SigmaHQ Rules Release Highlights — r2024–03–26
 https://github.com/SigmaHQ/sigma/releases/tag/r2024-03-26
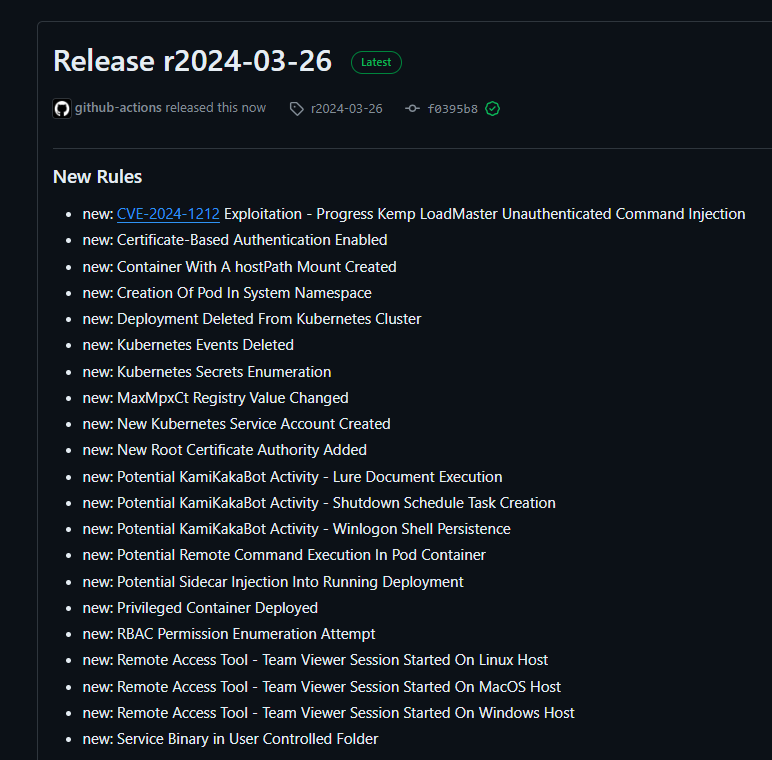
https://github.com/SigmaHQ/sigma/releases/tag/r2024-03-26Sigma Rule Packages for 26–03–2024 are released and available for download. This release saw the addition of 21 new rules, 64 rule updates and 5 rule fixes by 9 contributors.
New Rules
Some highlights for the newer rules include rule for CVE-2024–1212 a “Progress Kemp LoadMaster Unauthenticated Command Injection”
title: CVE-2024-1212 Exploitation - Progress Kemp LoadMaster Unauthenticated Command Injection
id: eafb8bd5-7605-4bfe-a9ec-0442bc151f15
status: experimental
description: |
Detects potential exploitation of CVE-2024-1709 an unauthenticated command injection in Progress Kemp LoadMaster.
It looks for GET requests to '/access/set' API with the parameters 'param=enableapi' and 'value=1' as well as an "Authorization" header with a base64 encoded value with an uncommon character.
references:
- https://github.com/RhinoSecurityLabs/CVEs/blob/15cf4d86c83daa57b59eaa2542a0ed47ad3dc32d/CVE-2024-1212/CVE-2024-1212.py
- https://rhinosecuritylabs.com/research/cve-2024-1212unauthenticated-command-injection-in-progress-kemp-loadmaster/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2024/03/20
tags:
- attack.initial_access
- cve.2024.1212
logsource:
category: webserver
detection:
selection_path:
cs-method: 'GET'
cs-uri-stem|contains|all:
- '/access/set'
- 'param=enableapi'
- 'value=1'
selection_keywords:
- 'Basic Jz'
- 'Basic c7'
- 'Basic nO'
- "Basic ';"
condition: all of selection_*
falsepositives:
- Unlikely
level: high
New set of rules covering activity related to KamiKakaBot.
title: Potential KamiKakaBot Activity - Lure Document Execution
id: 24474469-bd80-46cc-9e08-9fbe81bfaaca
status: experimental
description: |
Detects the execution of a Word document via the WinWord Start Menu shortcut.
This behavior was observed being used by KamiKakaBot samples in order to initiate the 2nd stage of the infection.
references:
- https://www.nextron-systems.com/2024/03/22/unveiling-kamikakabot-malware-analysis/
author: Nasreddine Bencherchali (Nextron Systems), X__Junior (Nextron Systems)
date: 2024/03/22
tags:
- attack.execution
- attack.t1059
- detection.emerging_threats
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\cmd.exe'
CommandLine|contains|all:
- '/c '
- '.lnk ~'
- 'Start Menu\Programs\Word'
CommandLine|endswith: '.doc'
condition: selection
falsepositives:
- Unknown
level: medium
title: Potential KamiKakaBot Activity - Shutdown Schedule Task Creation
id: fe9e8ba9-4419-41e6-a574-bd9f7b3af961
status: experimental
description: |
Detects the creation of a schedule task that runs weekly and execute the "shutdown /l /f" command.
This behavior was observed being used by KamiKakaBot samples in order to achieve persistence on a system.
references:
- https://www.nextron-systems.com/2024/03/22/unveiling-kamikakabot-malware-analysis/
- https://tria.ge/240123-rapteaahhr/behavioral1
author: Nasreddine Bencherchali (Nextron Systems), X__Junior (Nextron Systems)
date: 2024/03/22
tags:
- attack.persistence
- detection.emerging_threats
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\schtasks.exe'
CommandLine|contains|all:
- ' /create '
- 'shutdown /l /f'
- 'WEEKLY'
filter_main_system_user:
User|contains: # covers many language settings
- 'AUTHORI'
- 'AUTORI'
condition: selection and not 1 of filter_main_*
falsepositives:
- Unknown
level: medium
A new set of rules leveraging native Kubernetes logs.
title: Potential Remote Command Execution In Pod Container
id: a1b0ca4e-7835-413e-8471-3ff2b8a66be6
status: experimental
description: |
Detects attempts to execute remote commands, within a Pod's container using e.g. the "kubectl exec" command.
references:
- https://microsoft.github.io/Threat-Matrix-for-Kubernetes/techniques/Exec%20into%20container/
author: Leo Tsaousis (@laripping)
date: 2024/03/26
tags:
- attack.t1609
logsource:
category: application
product: kubernetes
service: audit
detection:
selection:
verb: 'create'
objectRef.resource: 'pods'
objectRef.subresource: 'exec'
condition: selection
falsepositives:
- Legitimate debugging activity. Investigate the identity performing the requests and their authorization.
level: medium
title: Privileged Container Deployed
id: c5cd1b20-36bb-488d-8c05-486be3d0cb97
status: experimental
description: |
Detects the creation of a "privileged" container, an action which could be indicative of a threat actor mounting a container breakout attacks.
A privileged container is a container that can access the host with all of the root capabilities of the host machine. This allows it to view, interact and modify processes, network operations, IPC calls, the file system, mount points, SELinux configurations etc. as the root user on the host.
Various versions of "privileged" containers can be specified, e.g. by setting the securityContext.privileged flag in the resource specification, setting non-standard Linux capabilities, or configuring the hostNetwork/hostPID fields
references:
- https://microsoft.github.io/Threat-Matrix-for-Kubernetes/techniques/Privileged%20container/
- https://docs.aws.amazon.com/guardduty/latest/ug/guardduty_finding-types-kubernetes.html#privilegeescalation-kubernetes-privilegedcontainer
- https://www.elastic.co/guide/en/security/current/kubernetes-pod-created-with-hostnetwork.html
- https://www.elastic.co/guide/en/security/current/kubernetes-container-created-with-excessive-linux-capabilities.html
author: Leo Tsaousis (@laripping)
date: 2024/03/26
tags:
- attack.t1611
logsource:
category: application
product: kubernetes
service: audit
detection:
selection:
verb: 'create'
objectRef.resource: 'pods'
capabilities: '*' # Note: Add the "exists" when it's implemented in SigmaHQ/Aurora
condition: selection
falsepositives:
- Unknown
level: low
New Updates
Some older rules have seen improvements in coverage and metadata as well.
The first big set of update is related to enhancing the registry rule so that they don’t use the hard coded “HKLM”, “HKCU” or similar prefixes.
The reason behind such an update is that not all logging utilities use that notation. And depending on how you use the rule either in a SIEM or doing registry parsing for DFIR related tasks. The output might change.
To account for this, we dropped the prefixes where possible.
title: New PortProxy Registry Entry Added
id: a54f842a-3713-4b45-8c84-5f136fdebd3c
status: test
description: Detects the modification of the PortProxy registry key which is used for port forwarding.
references:
- https://www.fireeye.com/blog/threat-research/2019/01/bypassing-network-restrictions-through-rdp-tunneling.html
- https://adepts.of0x.cc/netsh-portproxy-code/
- https://www.dfirnotes.net/portproxy_detection/
author: Andreas Hunkeler (@Karneades)
date: 2021/06/22
modified: 2024/03/25
tags:
- attack.lateral_movement
- attack.defense_evasion
- attack.command_and_control
- attack.t1090
logsource:
category: registry_event
product: windows
detection:
selection:
# Example: HKLM\System\CurrentControlSet\Services\PortProxy\v4tov4\tcp\0.0.0.0/1337
TargetObject|contains: '\Services\PortProxy\v4tov4\tcp\'
condition: selection
falsepositives:
- WSL2 network bridge PowerShell script used for WSL/Kubernetes/Docker (e.g. https://github.com/microsoft/WSL/issues/4150#issuecomment-504209723)
- Synergy Software KVM (https://symless.com/synergy)
level: medium
Another set of update include the migration of rules to use the “windash” modifier. This modifier tells the sigma converter utility to use both permutation of a commandline flag.
For example many utilities accept both CLI flags with “/” (slash) and “-” (dash). This modifier abstracts this idea and let the user only care about one.
title: Potential Reconnaissance For Cached Credentials Via Cmdkey.EXE
id: 07f8bdc2-c9b3-472a-9817-5a670b872f53
status: test
description: Detects usage of cmdkey to look for cached credentials on the system
references:
- https://www.peew.pw/blog/2017/11/26/exploring-cmdkey-an-edge-case-for-privilege-escalation
- https://technet.microsoft.com/en-us/library/cc754243(v=ws.11).aspx
- https://github.com/redcanaryco/atomic-red-team/blob/b27a3cb25025161d49ac861cb216db68c46a3537/atomics/T1003.005/T1003.005.md#atomic-test-1---cached-credential-dump-via-cmdkey
author: jmallette, Florian Roth (Nextron Systems), Nasreddine Bencherchali (Nextron Systems)
date: 2019/01/16
modified: 2024/03/05
tags:
- attack.credential_access
- attack.t1003.005
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\cmdkey.exe'
- OriginalFileName: 'cmdkey.exe'
selection_cli:
CommandLine|contains|windash: ' -l'
condition: all of selection*
fields:
- CommandLine
- ParentCommandLine
- User
falsepositives:
- Legitimate administrative tasks
level: high
We also migrated all rules that make use of the CIDR notation in their logic. To use the “cidr” modifier. Which allows rule authors to write IP ranges in CIDR format.
title: Dllhost.EXE Initiated Network Connection To Non-Local IP Address
id: cfed2f44-16df-4bf3-833a-79405198b277
status: test
description: |
Detects dllhost initiating a network connection to a non-local IP address.
Aside from Microsoft own IP range that needs to be excluded. Network communication from Dllhost will depend entirely on the hosted DLL.
An initial baseline is recommended before deployment.
references:
- https://redcanary.com/blog/child-processes/
- https://nasbench.medium.com/what-is-the-dllhost-exe-process-actually-running-ef9fe4c19c08
author: bartblaze
date: 2020/07/13
modified: 2024/03/12
tags:
- attack.defense_evasion
- attack.t1218
- attack.execution
- attack.t1559.001
logsource:
category: network_connection
product: windows
detection:
selection:
Image|endswith: '\dllhost.exe'
Initiated: 'true'
filter_main_local_ranges:
DestinationIp|cidr:
- '::1/128' # IPv6 loopback
- '10.0.0.0/8'
- '127.0.0.0/8'
- '172.16.0.0/12'
- '192.168.0.0/16'
- '169.254.0.0/16'
- 'fc00::/7' # IPv6 private addresses
- 'fe80::/10' # IPv6 link-local addresses
filter_main_msrange:
DestinationIp|cidr:
- '20.184.0.0/13' # Microsoft Corporation
- '20.192.0.0/10' # Microsoft Corporation
- '23.72.0.0/13' # Akamai International B.V.
- '51.10.0.0/15' # Microsoft Corporation
- '51.103.0.0/16' # Microsoft Corporation
- '51.104.0.0/15' # Microsoft Corporation
- '52.224.0.0/11' # Microsoft Corporation
- '204.79.197.0/24' # Microsoft Corporation'
condition: selection and not 1 of filter_main_*
falsepositives:
- Communication to other corporate systems that use IP addresses from public address spaces
level: medium
Multiple rules also saw update to their logic in order to increase coverage. A couple of example include.
New domains added for the rule “Suspicious DNS Query for IP Lookup Service APIs”.
title: Suspicious DNS Query for IP Lookup Service APIs
id: ec82e2a5-81ea-4211-a1f8-37a0286df2c2
status: test
description: Detects DNS queries for IP lookup services such as "api.ipify.org" originating from a non browser process.
references:
- https://www.binarydefense.com/analysis-of-hancitor-when-boring-begets-beacon
- https://twitter.com/neonprimetime/status/1436376497980428318
- https://www.trendmicro.com/en_us/research/23/e/managed-xdr-investigation-of-ducktail-in-trend-micro-vision-one.html
author: Brandon George (blog post), Thomas Patzke
date: 2021/07/08
modified: 2024/03/22
tags:
- attack.reconnaissance
- attack.t1590
logsource:
product: windows
category: dns_query
detection:
selection:
- QueryName:
- 'www.ip.cn'
- 'l2.io'
- QueryName|contains:
- 'api.2ip.ua'
- 'api.bigdatacloud.net'
- 'api.ipify.org'
- 'bot.whatismyipaddress.com'
- 'canireachthe.net'
- 'checkip.amazonaws.com'
- 'checkip.dyndns.org'
- 'curlmyip.com'
- 'db-ip.com'
- 'edns.ip-api.com'
- 'eth0.me'
- 'freegeoip.app'
- 'geoipy.com'
- 'getip.pro'
- 'icanhazip.com'
- 'ident.me'
- 'ifconfig.io'
- 'ifconfig.me'
- 'ip-api.com'
- 'ip.360.cn'
- 'ip.anysrc.net'
- 'ip.taobao.com'
- 'ip.tyk.nu'
- 'ipaddressworld.com'
- 'ipapi.co'
- 'ipconfig.io'
- 'ipecho.net'
- 'ipinfo.io'
- 'ipip.net'
- 'ipof.in'
- 'ipv4.icanhazip.com'
- 'ipv4bot.whatismyipaddress.com'
- 'ipv6-test.com'
- 'ipwho.is'
- 'jsonip.com'
- 'myexternalip.com'
- 'seeip.org'
- 'wgetip.com'
- 'whatismyip.akamai.com'
- 'whois.pconline.com.cn'
- 'wtfismyip.com'
filter_optional_brave:
Image|endswith: '\brave.exe'
filter_optional_chrome:
Image:
- 'C:\Program Files\Google\Chrome\Application\chrome.exe'
- 'C:\Program Files (x86)\Google\Chrome\Application\chrome.exe'
filter_optional_firefox:
Image:
- 'C:\Program Files\Mozilla Firefox\firefox.exe'
- 'C:\Program Files (x86)\Mozilla Firefox\firefox.exe'
filter_optional_ie:
Image:
- 'C:\Program Files (x86)\Internet Explorer\iexplore.exe'
- 'C:\Program Files\Internet Explorer\iexplore.exe'
filter_optional_maxthon:
Image|endswith: '\maxthon.exe'
filter_optional_edge_1:
- Image|startswith: 'C:\Program Files (x86)\Microsoft\EdgeWebView\Application\'
- Image|endswith: '\WindowsApps\MicrosoftEdge.exe'
- Image:
- 'C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe'
- 'C:\Program Files\Microsoft\Edge\Application\msedge.exe'
filter_optional_edge_2:
Image|startswith:
- 'C:\Program Files (x86)\Microsoft\EdgeCore\'
- 'C:\Program Files\Microsoft\EdgeCore\'
Image|endswith:
- '\msedge.exe'
- '\msedgewebview2.exe'
filter_optional_opera:
Image|endswith: '\opera.exe'
filter_optional_safari:
Image|endswith: '\safari.exe'
filter_optional_seamonkey:
Image|endswith: '\seamonkey.exe'
filter_optional_vivaldi:
Image|endswith: '\vivaldi.exe'
filter_optional_whale:
Image|endswith: '\whale.exe'
condition: selection and not 1 of filter_optional_*
falsepositives:
- Legitimate usage of IP lookup services such as ipify API
level: medium
Enhanced logic for “Potentially Suspicious CMD Shell Output Redirect”
title: Potentially Suspicious CMD Shell Output Redirect
id: 8e0bb260-d4b2-4fff-bb8d-3f82118e6892
related:
- id: aa2efee7-34dd-446e-8a37-40790a66efd7
type: derived
- id: 4f4eaa9f-5ad4-410c-a4be-bc6132b0175a
type: similar
status: experimental
description: |
Detects inline Windows shell commands redirecting output via the ">" symbol to a suspicious location.
This technique is sometimes used by malicious actors in order to redirect the output of reconnaissance commands such as "hostname" and "dir" to files for future exfiltration.
references:
- https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2022/07/12
modified: 2024/03/19
tags:
- attack.defense_evasion
- attack.t1218
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\cmd.exe'
- OriginalFileName: 'Cmd.Exe'
selection_cli_1:
CommandLine|contains:
# Note: Add more suspicious locations as you find them
# Note: The space from the start is missing to cover append operations ">>"
# Note: We use the "?" to account for both a single and a double quote
# Note: If you want to account for more spaces which is still a valid bypass option. Use a regex with "\s"
- '>?%APPDATA%\'
- '>?%TEMP%\'
- '>?%TMP%\'
- '>?%USERPROFILE%\'
- '>?C:\ProgramData\'
- '>?C:\Temp\'
- '>?C:\Users\Public\'
- '>?C:\Windows\Temp\'
selection_cli_2:
CommandLine|contains:
- ' >'
- '">'
- "'>"
CommandLine|contains|all:
- 'C:\Users\'
- '\AppData\Local\'
condition: selection_img and 1 of selection_cli_*
falsepositives:
- Legitimate admin or third party scripts used for diagnostic collection might generate some false positives
level: medium
Fixes
This release includes a couple of false positives fixes and tuning of older rules to enhance their quality.
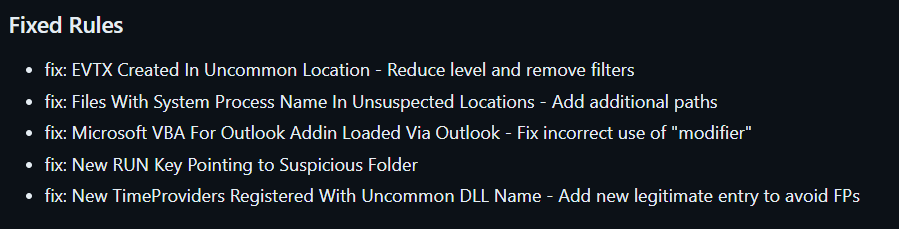
Please check the full change-log on the release page below for the complete list of changes and additions.
Release Release r2024-03-26 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
SigmaHQ Rules Release Highlights — r2024–03–26 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2024–03–26 | by Nasreddine Bencherchali | Mar, 2024 | Sigma_HQ