SigmaHQ Rules Release Highlights — r2024–02–26
 https://github.com/SigmaHQ/sigma/releases/tag/r2024-02-26
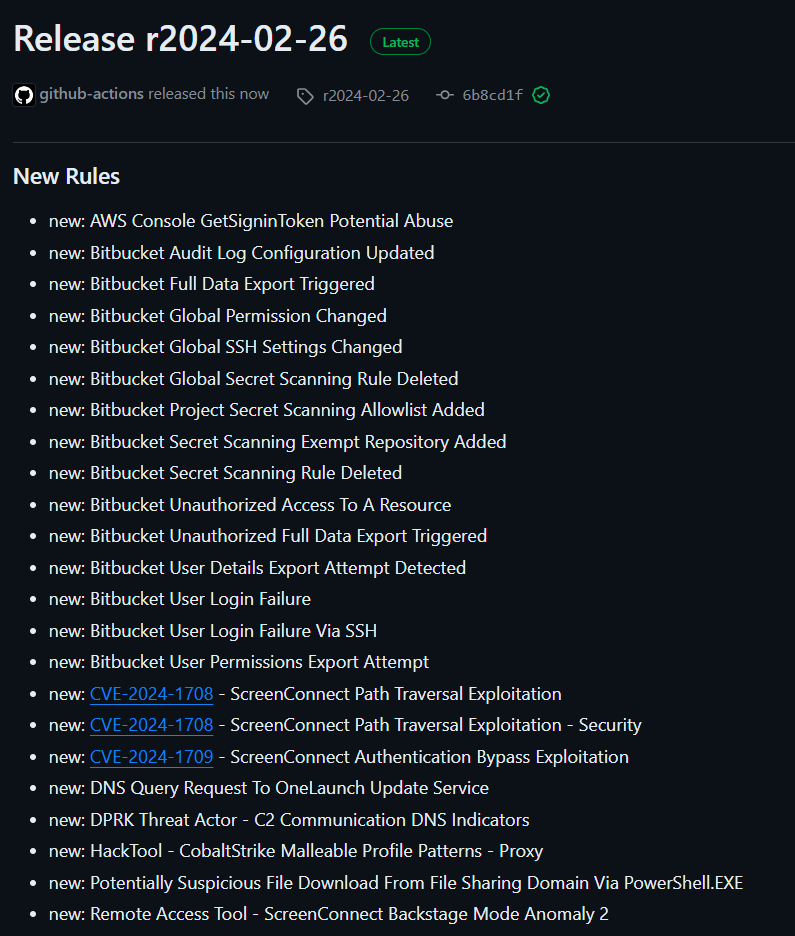
https://github.com/SigmaHQ/sigma/releases/tag/r2024-02-26Sigma Rule Packages for 26–02–2024 are released and available for download. This release saw the addition of 31 new rules, 16 rule updates by 9 contributors.
New Rules
Some highlights for the newer rules include new rules related to the ScreenConnect “Slash and Grab” exploit CVE-2024–1708 and CVE-2024–1709.
title: CVE-2024-1709 - ScreenConnect Authentication Bypass Exploitation
id: d27eabad-9068-401a-b0d6-9eac744d6e67
status: experimental
description: |
Detects GET requests to '/SetupWizard.aspx/[anythinghere]' that indicate exploitation of the ScreenConnect vulnerability CVE-2024-1709.
references:
- https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
- https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
- https://www.cve.org/CVERecord?id=CVE-2024-1709
author: Matt Anderson, Huntress
date: 2024/02/20
tags:
- attack.initial_access
- attack.persistence
- cve.2024.1709
logsource:
category: webserver
detection:
selection:
cs-uri-stem|contains: '/SetupWizard.aspx/'
condition: selection
falsepositives:
- Unknown
level: critical
title: CVE-2024-1708 - ScreenConnect Path Traversal Exploitation
id: 44d7af7e-88e6-4490-be11-55f7ff4d9fc1
related:
- id: 4c198a60-7d05-4daf-8bf7-4136fb6f5c62
type: similar
status: experimental
description: |
This detects file modifications to ASPX and ASHX files within the root of the App_Extensions directory, which is allowed by a ZipSlip vulnerability in versions prior to 23.9.8. This occurs during exploitation of CVE-2024-1708.
references:
- https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
- https://www.cve.org/CVERecord?id=CVE-2024-1709
- https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
author: Matt Anderson, Andrew Schwartz, Caleb Stewart, Huntress
date: 2024/02/21
tags:
- attack.persistence
- cve.2024.1708
logsource:
product: windows
category: file_event
detection:
selection:
Image|endswith: '\ScreenConnect.Service.exe'
TargetFilename|endswith:
- 'ScreenConnect\\App_Extensions\\*.ashx'
- 'ScreenConnect\\App_Extensions\\*.aspx'
filter_main_legit_extension:
TargetFilename|contains: 'ScreenConnect\App_Extensions\\*\\'
condition: selection and not 1 of filter_main_*
falsepositives:
- This will occur legitimately as well and will result in some benign activity.
level: medium
As well as generic rules for exploitation indicator of the ScreenConnect client and server.
title: Remote Access Tool - ScreenConnect Potential Suspicious Remote Command Execution
id: 7b582f1a-b318-4c6a-bf4e-66fe49bf55a5
related:
- id: d1a401ab-8c47-4e86-a7d8-2460b6a53e4a
type: derived
status: test
description: |
Detects potentially suspicious child processes launched via the ScreenConnect client service.
references:
- https://www.mandiant.com/resources/telegram-malware-iranian-espionage
- https://docs.connectwise.com/ConnectWise_Control_Documentation/Get_started/Host_client/View_menu/Backstage_mode
- https://www.huntress.com/blog/slashandgrab-screen-connect-post-exploitation-in-the-wild-cve-2024-1709-cve-2024-1708
author: Florian Roth (Nextron Systems), Nasreddine Bencherchali (Nextron Systems), @Kostastsale
date: 2022/02/25
modified: 2024/02/26
tags:
- attack.command_and_control
- attack.t1219
logsource:
product: windows
category: process_creation
detection:
selection:
ParentCommandLine|contains|all:
- ':\Windows\TEMP\ScreenConnect\'
- 'run.cmd'
Image|endswith:
- '\cmd.exe'
- '\curl.exe'
- '\powershell.exe'
- '\pwsh.exe'
- '\wevtutil.exe'
condition: selection
falsepositives:
- If the script being executed make use of any of the utilities mentioned in the detection then they should filtered out or allowed.
level: medium
title: Remote Access Tool - ScreenConnect Server Web Shell Execution
id: b19146a3-25d4-41b4-928b-1e2a92641b1b
status: experimental
description: Detects potential web shell execution from the ScreenConnect server process.
references:
- https://blackpointcyber.com/resources/blog/breaking-through-the-screen/
- https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
author: Jason Rathbun (Blackpoint Cyber)
date: 2024/02/26
tags:
- attack.initial_access
- attack.t1190
logsource:
product: windows
category: process_creation
detection:
selection:
ParentImage|endswith: '\ScreenConnect.Service.exe'
Image|endswith:
- '\cmd.exe'
- '\csc.exe'
condition: selection
falsepositives:
- Unlikely
level: high
Another major contribution this release was the addition of the first set of Bitbucket related rules based on Audit logs generated by Bitbucket. These include
- Full data export
- Global permission tampering
- Project scanning rules deletion
and much more
title: Bitbucket Full Data Export Triggered
id: 195e1b9d-bfc2-4ffa-ab4e-35aef69815f8
status: experimental
description: Detects when full data export is attempted.
references:
- https://confluence.atlassian.com/bitbucketserver/audit-log-events-776640423.html
- https://confluence.atlassian.com/adminjiraserver0811/importing-and-exporting-data-1019391889.html
author: Muhammad Faisal (@faisalusuf)
date: 2024/02/25
tags:
- attack.collection
- attack.t1213.003
logsource:
product: bitbucket
service: audit
definition: 'Requirements: "Advance" log level is required to receive these audit events.'
detection:
selection:
auditType.category: 'Data pipeline'
auditType.action: 'Full data export triggered'
condition: selection
falsepositives:
- Legitimate user activity.
level: high
title: Bitbucket Global Permission Changed
id: aac6c4f4-87c7-4961-96ac-c3fd3a42c310
status: experimental
description: Detects global permissions change activity.
references:
- https://confluence.atlassian.com/bitbucketserver/audit-log-events-776640423.html
- https://confluence.atlassian.com/bitbucketserver/global-permissions-776640369.html
author: Muhammad Faisal (@faisalusuf)
date: 2024/02/25
tags:
- attack.persistence
- attack.privilege_escalation
- attack.t1098
logsource:
product: bitbucket
service: audit
definition: 'Requirements: "Advance" log level is required to receive these audit events.'
detection:
selection:
auditType.category: 'Permissions'
auditType.action:
- 'Global permission remove request'
- 'Global permission removed'
- 'Global permission granted'
- 'Global permission requested'
condition: selection
falsepositives:
- Legitimate user activity.
level: medium
New Updates
A couple of the older rules have seen some improvements in coverage and metadata as well. Some examples include
New User-Agent to the APT UA hunting rule related to RedCurl APT
title: APT User Agent
id: 6ec820f2-e963-4801-9127-d8b2dce4d31b
status: test
description: Detects suspicious user agent strings used in APT malware in proxy logs
references:
- Internal Research
author: Florian Roth (Nextron Systems), Markus Neis
date: 2019/11/12
modified: 2024/02/15
tags:
- attack.command_and_control
- attack.t1071.001
logsource:
category: proxy
detection:
selection:
c-useragent:
# APT Related
- 'SJZJ (compatible; MSIE 6.0; Win32)' # APT Backspace
- 'Mozilla/5.0 (Windows NT 6.; WOW64; rv:20.0) Gecko/20100101 Firefox/20.0' # APT GrizzlySteppe - ChopStick - US CERT https://goo.gl/1DTHwi
- 'User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC' # Comment Crew Miniasp
- 'Mozilla/4.0 (compatible; MSIE 7.4; Win32;32-bit)' # Comment Crew Miniasp
- 'webclient' # Naikon APT
- 'Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-EN; rv:1.7.12) Gecko/200' # Naikon APT
- 'Mozilla/4.0 (compatible; MSI 6.0;' # SnowGlobe Babar - yes, it is cut
- 'Mozilla/5.0 (Windows NT 6.3; WOW64; rv:28.0) Gecko/20100101 Firefox/28.0' # Sofacy - Xtunnel
- 'Mozilla/5.0 (Windows NT 6.2; WOW64; rv:20.0) Gecko/20100101 Firefox/' # Sofacy - Xtunnel
- 'Mozilla/5.0 (Windows NT 6.; WOW64; rv:20.0) Gecko/20100101 Firefox/2' # Sofacy - Xtunnel
- 'Mozilla/4.0' # Derusbi backdoor ELF https://github.com/fideliscyber/indicators/tree/master/FTA-1021
- 'Netscape' # Unit78020 Malware
- 'Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-EN; rv:1.7.12) Gecko/20100719 Firefox/1.0.7' # Unit78020 Malware
- 'Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.2.13) Firefox/3.6.13 GTB7.1' # Winnti related
- 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)' # Winnti related
- 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NETCLR 2.0.50727)' # APT17
- 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.0; SV1)' # Bronze Butler - Daserf
- 'Mozilla/4.0 (compatible; MSIE 11.0; Windows NT 6.1; SV1)' # Bronze Butler - Daserf
- 'Mozilla/4.0 (compatible; MSIE 8.0; Win32)' # TSCookie https://app.any.run/tasks/0996b314-5133-491b-8d23-d431ffdec597
- 'Mozilla v5.1 (Windows NT 6.1; rv:6.0.1) Gecko/20100101 Firefox/6.0.1' # Delphi downloader https://www.welivesecurity.com/2018/04/24/sednit-update-analysis-zebrocy/
- 'Mozilla/6.1 (compatible; MSIE 9.0; Windows NT 5.3; Trident/5.0)' # VPNFilter https://blog.talosintelligence.com/2018/05/VPNFilter.html
- 'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.04506.30; .NET CLR 3.0.04506.648; InfoPath.1)' # Sofacy User-Agent https://researchcenter.paloaltonetworks.com/2018/06/unit42-sofacy-groups-parallel-attacks/
- 'Mozilla/5.0 (Windows NT 6.1; WOW64) WinHttp/1.6.3.8 (WinHTTP/5.1) like Gecko' # Sofacy User-Agent https://researchcenter.paloaltonetworks.com/2018/06/unit42-sofacy-groups-parallel-attacks/
- 'Mozilla v5.1 *' # Sofacy Zebrocy samples
- 'MSIE 8.0' # Sofacy Azzy Backdoor from https://www.hybrid-analysis.com/sample/a80e29c0757bee05338fd5c22a542d852ad86c477068e3eb4aacc1c3e59e2eef?environmentId=100
- 'Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E; InfoPath.2)' # https://www.fireeye.com/blog/threat-research/2018/07/microsoft-office-vulnerabilities-used-to-distribute-felixroot-backdoor.html
- 'Mozilla/4.0 (compatible; RMS)' # Attacks on industrial enterprises using RMS and TeamViewer https://goo.gl/GthvTw
- 'Mozilla/4.0 (compatible; MSIE 6.0; DynGate)' # Attacks on industrial enterprises using RMS and TeamViewer https://goo.gl/GthvTw
- 'O/9.27 (W; U; Z)' # Cmstar https://www.virustotal.com/#/file/e4328011bb2b04abc856ccd04404c9f95d67167f6c291d343e8ffa8aa2aa2099/details
- 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; Trident/5.0; Trident/5.0*' # KerrDown UA https://goo.gl/s2WU6o
- 'Mozilla/5.0 (Windows NT 9; *' # Suspicious 'Windows NT 9' user agent - used by APT33 malware in 2018
- 'hots scot' # Unknown iOS zero-day implant https://twitter.com/craiu/status/1176437994288484352?s=20
- 'Mozilla/5.0 (compatible; MSIE 10.0; Windows NT)' # https://blog.telsy.com/meeting-powerband-the-apt33-net-powerton-variant/
- 'Mozilla/5.0 (Windows NT 6.1; WOW64) Chrome/28.0.1500.95 Safari/537.36' # Hidden Cobra malware
- 'Mozilla/5.0 (Windows NT 6.2; Win32; rv:47.0)' # Strong Pity loader https://twitter.com/VK_Intel/status/1264185981118406657
- 'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1;' # Mustang Panda https://insights.oem.avira.com/new-wave-of-plugx-targets-hong-kong/
- 'Mozilla/5.0 (X11; Linux i686; rv:22.0) Firefox/22.0' # BackdoorDiplomacy https://www.welivesecurity.com/2021/06/10/backdoordiplomacy-upgrading-quarian-turian/
- 'Mozilla/5.0 Chrome/72.0.3626.109 Safari/537.36' # SideWalk malware used by Sparkling Goblin
- 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:FTS_06) Gecko/22.36.35.06 Firefox/2.0' # LitePower stager used by WRITE https://securelist.com/wirtes-campaign-in-the-middle-east-living-off-the-land-since-at-least-2019/105044/
- 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.5005.63 Safari/537.36 Edg/100.0.1185.39' # https://www.microsoft.com/security/blog/2022/09/29/zinc-weaponizing-open-source-software/
- 'Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; InfoPath.3; .NET4.0C; .NET4.0E)' # https://www.microsoft.com/security/blog/2022/09/29/zinc-weaponizing-open-source-software/
- 'Mozilla/4.0 (compatible; MSIE 9.0; Windows NT 10.0; .NET4.0C; .NET4.0E; Tablet PC 2.0)' # PlugX backdoor https://unit42.paloaltonetworks.com/thor-plugx-variant/
- 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246001' # RedCurl Downloader APT https://www.facct.ru/blog/redcurl-2024
condition: selection
fields:
- ClientIP
- c-uri
- c-useragent
falsepositives:
- Old browsers
level: high
Add commandline flag variation of / and - to Windows based rules such as
- Curl
- Chcp
- Cmdkey
And more.
Update and merging of rules that covered the potential abuse of the “RunHTMLApplication” export, in order to cover the newly reported Windows Defender bypass
title: Mshtml.DLL RunHTMLApplication Suspicious Usage
id: 4782eb5a-a513-4523-a0ac-f3082b26ac5c
related:
- id: 9f06447a-a33a-4cbe-a94f-a3f43184a7a3
type: obsoletes
- id: 73fcad2e-ff14-4c38-b11d-4172c8ac86c7
type: obsoletes
status: test
description: |
Detects execution of commands that leverage the "mshtml.dll" RunHTMLApplication export to run arbitrary code via different protocol handlers (vbscript, javascript, file, http...)
references:
- https://twitter.com/n1nj4sec/status/1421190238081277959
- https://hyp3rlinx.altervista.org/advisories/MICROSOFT_WINDOWS_DEFENDER_TROJAN.WIN32.POWESSERE.G_MITIGATION_BYPASS_PART2.txt
- http://hyp3rlinx.altervista.org/advisories/MICROSOFT_WINDOWS_DEFENDER_DETECTION_BYPASS.txt
author: Nasreddine Bencherchali (Nextron Systems), Florian Roth (Nextron Systems), Josh Nickels, frack113, Zaw Min Htun (ZETA)
date: 2022/08/14
modified: 2024/02/23
tags:
- attack.defense_evasion
- attack.execution
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine|contains|all:
- '\..\'
- 'mshtml'
CommandLine|contains:
- '#135'
- 'RunHTMLApplication'
condition: selection
falsepositives:
- Unlikely
level: high
Please check the full changelog on the release page below for the complete list of changes and additions.
Release Release r2024-02-26 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
SigmaHQ Rules Release Highlights — r2024–02–26 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2024–02–26 | by Nasreddine Bencherchali | Feb, 2024 | Sigma_HQ