SigmaHQ Rules Release Highlights — r2024–02–12
 https://github.com/SigmaHQ/sigma/releases/tag/r2024-02-12
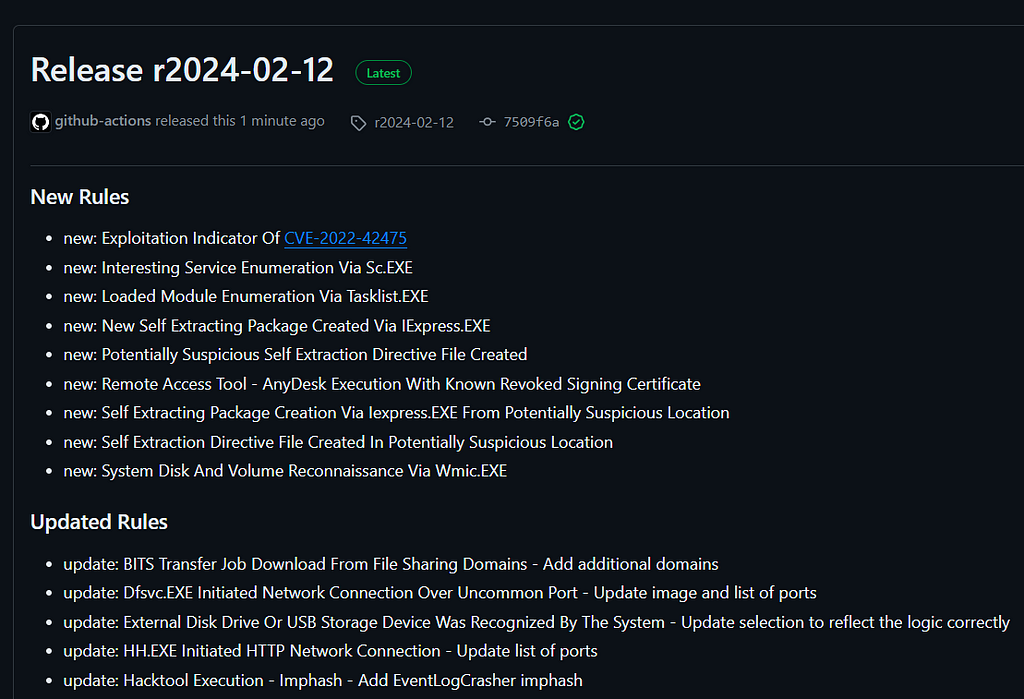
https://github.com/SigmaHQ/sigma/releases/tag/r2024-02-12Sigma Rule Packages for 12–02–2024 are released and available for download. This release saw the addition of 9 new rules, 23 rule updates and 9 rule fixes by 12+ contributors.
New Rules
Some highlights for the newer rules include new rules related to IExpress usage as seen in the wild. Threat actors deployed self extracting directories in order to create binaries and cab file via IExpress
title: Self Extracting Package Creation Via Iexpress.EXE From Potentially Suspicious Location
id: b2b048b0-7857-4380-b0fb-d3f0ab820b71
status: experimental
description: |
Detects the use of iexpress.exe to create binaries via Self Extraction Directive (SED) files located in potentially suspicious locations.
This behavior has been observed in-the-wild by different threat actors.
references:
- https://strontic.github.io/xcyclopedia/library/iexpress.exe-D594B2A33EFAFD0EABF09E3FDC05FCEA.html
- https://en.wikipedia.org/wiki/IExpress
- https://decoded.avast.io/janvojtesek/raspberry-robins-roshtyak-a-little-lesson-in-trickery/
- https://www.virustotal.com/gui/file/602f4ae507fa8de57ada079adff25a6c2a899bd25cd092d0af7e62cdb619c93c/behavior
author: Joseliyo Sanchez, @Joseliyo_Jstnk, Nasreddine Bencherchali (Nextron Systems)
date: 2024/02/05
tags:
- attack.execution
- attack.t1218
logsource:
category: process_creation
product: windows
detection:
# VT Query: behavior_processes:"iexpress.exe" and behavior_processes:"/n /q /m" and behavior_processes:"*.sed*" and p:5+
selection_img:
- Image|endswith: '\iexpress.exe'
- OriginalFileName: 'IEXPRESS.exe'
selection_cli:
CommandLine|contains: ' /n '
selection_paths:
CommandLine|contains:
# Note: Add more uncommon paths that fit your organizational needs.
- ':\ProgramData\'
- ':\Temp\'
- ':\Windows\System32\Tasks\'
- ':\Windows\Tasks\'
- ':\Windows\Temp\'
- '\AppData\Local\Temp\'
condition: all of selection_*
falsepositives:
- Administrators building packages using iexpress.exe
level: high
Threat actors were also seen creating these “.sed” files as executables and dropping them in uncommon locations.
title: Potentially Suspicious Self Extraction Directive File Created
id: ab90dab8-c7da-4010-9193-563528cfa347
related:
- id: 760e75d8-c3b5-409b-a9bf-6130b4c4603f
type: derived
status: experimental
description: |
Detects the creation of a binary file with the ".sed" extension. The ".sed" extension stand for Self Extraction Directive files.
These files are used by the "iexpress.exe" utility in order to create self extracting packages.
Attackers were seen abusing this utility and creating PE files with embedded ".sed" entries.
Usually ".sed" files are simple ini files and not PE binaries.
references:
- https://strontic.github.io/xcyclopedia/library/iexpress.exe-D594B2A33EFAFD0EABF09E3FDC05FCEA.html
- https://en.wikipedia.org/wiki/IExpress
- https://www.virustotal.com/gui/file/602f4ae507fa8de57ada079adff25a6c2a899bd25cd092d0af7e62cdb619c93c/behavior
author: Joseliyo Sanchez, @Joseliyo_Jstnk
date: 2024/02/05
tags:
- attack.execution
- attack.t1218
logsource:
product: windows
category: file_executable_detected
detection:
selection:
TargetFilename|endswith: '.sed'
condition: selection
falsepositives:
- Unknown
level: medium
title: Self Extraction Directive File Created In Potentially Suspicious Location
id: 760e75d8-c3b5-409b-a9bf-6130b4c4603f
related:
- id: ab90dab8-c7da-4010-9193-563528cfa347
type: derived
status: experimental
description: |
Detects the creation of Self Extraction Directive files (.sed) in a potentially suspicious location.
These files are used by the "iexpress.exe" utility in order to create self extracting packages.
Attackers were seen abusing this utility and creating PE files with embedded ".sed" entries.
references:
- https://strontic.github.io/xcyclopedia/library/iexpress.exe-D594B2A33EFAFD0EABF09E3FDC05FCEA.html
- https://en.wikipedia.org/wiki/IExpress
- https://www.virustotal.com/gui/file/602f4ae507fa8de57ada079adff25a6c2a899bd25cd092d0af7e62cdb619c93c/behavior
author: Joseliyo Sanchez, @Joseliyo_Jstnk
date: 2024/02/05
tags:
- attack.execution
- attack.t1218
logsource:
category: file_event
product: windows
detection:
selection:
TargetFilename|contains:
- ':\ProgramData\'
- ':\Temp\'
- ':\Windows\System32\Tasks\'
- ':\Windows\Tasks\'
- ':\Windows\Temp\'
- '\AppData\Local\Temp\'
TargetFilename|endswith: '.sed'
condition: selection
falsepositives:
- Unknown
level: medium
Other rules include, using WMIC to query disk information
title: System Disk And Volume Reconnaissance Via Wmic.EXE
id: c79da740-5030-45ec-a2e0-479e824a562c
related:
- id: d85ecdd7-b855-4e6e-af59-d9c78b5b861e
type: similar
status: experimental
description: |
An adversary might use WMI to discover information about the system, such as the volume name, size,
free space, and other disk information. This can be done using the `wmic` command-line utility and has been
observed being used by threat actors such as Volt Typhoon.
references:
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-144a
- https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/wmic
author: Stephen Lincoln `@slincoln-aiq`(AttackIQ)
date: 2024/02/02
tags:
- attack.execution
- attack.discovery
- attack.t1047
- attack.t1082
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\WMIC.exe'
- OriginalFileName: 'wmic.exe'
selection_cli:
CommandLine|contains:
- 'volume'
- 'path win32_logicaldisk'
condition: all of selection_*
falsepositives:
- Unknown
level: medium
And querying a module via tasklist to inspect which process is hosting a specific module (DLL, EXE)
title: Loaded Module Enumeration Via Tasklist.EXE
id: 34275eb8-fa19-436b-b959-3d9ecd53fa1f
status: experimental
description: |
Detects the enumeration of a specific DLL or EXE being used by a binary via "tasklist.exe".
This is often used by attackers in order to find the specific process identifier (PID) that is using the DLL in question.
In order to dump the process memory or perform other nefarious actions.
references:
- https://www.n00py.io/2021/05/dumping-plaintext-rdp-credentials-from-svchost-exe/
- https://pentestlab.blog/tag/svchost/
author: Swachchhanda Shrawan Poudel
date: 2024/02/12
tags:
- attack.t1003
logsource:
product: windows
category: process_creation
detection:
selection_img:
- Image|endswith: '\tasklist.exe'
- OriginalFileName: 'tasklist.exe'
selection_flags:
CommandLine|contains:
- '/m'
- '-m'
selection_module:
# Note: add other interesting modules or binaries
CommandLine|contains: 'rdpcorets.dll'
condition: all of selection_*
falsepositives:
- Unknown
level: medium
New Updates
Many older rules have seen multiple improvements in coverage and metadata as well. Some examples include
Increased coverage for rules using file sharing domains as detection logic to include the following
- onrender[.]com
- glitch[.]me
- supabase[.]co
title: Suspicious DNS Query for IP Lookup Service APIs
id: ec82e2a5-81ea-4211-a1f8-37a0286df2c2
status: test
description: Detects DNS queries for IP lookup services such as "api.ipify.org" originating from a non browser process.
references:
- https://www.binarydefense.com/analysis-of-hancitor-when-boring-begets-beacon
- https://twitter.com/neonprimetime/status/1436376497980428318
- https://www.trendmicro.com/en_us/research/23/e/managed-xdr-investigation-of-ducktail-in-trend-micro-vision-one.html
author: Brandon George (blog post), Thomas Patzke
date: 2021/07/08
modified: 2024/02/08
tags:
- attack.reconnaissance
- attack.t1590
logsource:
product: windows
category: dns_query
detection:
selection:
QueryName|contains:
- 'api.2ip.ua'
- 'api.bigdatacloud.net'
- 'api.ipify.org'
- 'bot.whatismyipaddress.com'
- 'canireachthe.net'
- 'checkip.amazonaws.com'
- 'checkip.dyndns.org'
- 'curlmyip.com'
- 'db-ip.com'
- 'edns.ip-api.com'
- 'eth0.me'
- 'freegeoip.app'
- 'geoipy.com'
- 'getip.pro'
- 'icanhazip.com'
- 'ident.me'
- 'ifconfig.io'
- 'ifconfig.me'
- 'ip-api.com'
- 'ip.anysrc.net'
- 'ip.tyk.nu'
- 'ipaddressworld.com'
- 'ipapi.co'
- 'ipconfig.io'
- 'ipecho.net'
- 'ipinfo.io'
- 'ipof.in'
- 'ipv4.icanhazip.com'
- 'ipv4bot.whatismyipaddress.com'
- 'ipwho.is'
- 'l2.io'
- 'myexternalip.com'
- 'wgetip.com'
- 'whatismyip.akamai.com'
- 'wtfismyip.com'
filter_optional_brave:
Image|endswith: '\brave.exe'
filter_optional_chrome:
Image:
- 'C:\Program Files\Google\Chrome\Application\chrome.exe'
- 'C:\Program Files (x86)\Google\Chrome\Application\chrome.exe'
filter_optional_firefox:
Image:
- 'C:\Program Files\Mozilla Firefox\firefox.exe'
- 'C:\Program Files (x86)\Mozilla Firefox\firefox.exe'
filter_optional_ie:
Image:
- 'C:\Program Files (x86)\Internet Explorer\iexplore.exe'
- 'C:\Program Files\Internet Explorer\iexplore.exe'
filter_optional_maxthon:
Image|endswith: '\maxthon.exe'
filter_optional_edge_1:
- Image|startswith: 'C:\Program Files (x86)\Microsoft\EdgeWebView\Application\'
- Image|endswith: '\WindowsApps\MicrosoftEdge.exe'
- Image:
- 'C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe'
- 'C:\Program Files\Microsoft\Edge\Application\msedge.exe'
filter_optional_edge_2:
Image|startswith:
- 'C:\Program Files (x86)\Microsoft\EdgeCore\'
- 'C:\Program Files\Microsoft\EdgeCore\'
Image|endswith:
- '\msedge.exe'
- '\msedgewebview2.exe'
filter_optional_opera:
Image|endswith: '\opera.exe'
filter_optional_safari:
Image|endswith: '\safari.exe'
filter_optional_seamonkey:
Image|endswith: '\seamonkey.exe'
filter_optional_vivaldi:
Image|endswith: '\vivaldi.exe'
filter_optional_whale:
Image|endswith: '\whale.exe'
condition: selection and not 1 of filter_optional_*
falsepositives:
- Legitimate usage of IP lookup services such as ipify API
level: medium
Enhanced coverage of multiple rules that are using the network logs. A couple of example include.
- Limiting or increasing destination ports.
- Address specific images by limiting paths
title: Dfsvc.EXE Initiated Network Connection Over Uncommon Port
id: 4c5fba4a-9ef6-4f16-823d-606246054741
status: experimental
description: Detects an initiated network connection over uncommon ports from "dfsvc.exe". A utility used to handled ClickOnce applications.
references:
- https://posts.specterops.io/less-smartscreen-more-caffeine-ab-using-clickonce-for-trusted-code-execution-1446ea8051c5
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/06/12
modified: 2024/01/31
tags:
- attack.execution
- attack.t1203
logsource:
category: network_connection
product: windows
detection:
selection:
Image|contains: ':\Windows\Microsoft.NET\'
Image|endswith: '\dfsvc.exe'
Initiated: 'true'
filter_main_known_ports:
DestinationPort:
- 80
- 443
filter_optional_dns_ipv6:
# Based on VT. More than 140 binaries made communication over DNS
DestinationIsIpv6: 'true'
DestinationPort: 53
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
- Unknown
level: high
title: Msiexec.EXE Initiated Network Connection Over HTTP
id: 8e5e38e4-5350-4c0b-895a-e872ce0dd54f
status: test
description: |
Detects an initiated network connection by "Msiexec.exe" over port 80 or 443.
Adversaries might abuse "msiexec.exe" to install and execute remotely hosted packages.
references:
- https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/msiexec
- https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1218.007/T1218.007.md
author: frack113
date: 2022/01/16
modified: 2024/02/01
tags:
- attack.defense_evasion
- attack.t1218.007
logsource:
category: network_connection
product: windows
detection:
selection:
Initiated: 'true'
Image|endswith: '\msiexec.exe'
DestinationPort:
- 80
- 443
condition: selection
falsepositives:
- Some rare installers were seen communicating with external servers for additional information. While its a very rare occurrence in some environments an initial baseline might be required.
level: high
title: HH.EXE Initiated HTTP Network Connection
id: 468a8cea-2920-4909-a593-0cbe1d96674a
related:
- id: f57c58b3-ee69-4ef5-9041-455bf39aaa89
type: derived
status: test
description: |
Detects a network connection initiated by the "hh.exe" process to HTTP destination ports, which could indicate the execution/download of remotely hosted .chm files.
references:
- https://www.splunk.com/en_us/blog/security/follina-for-protocol-handlers.html
- https://github.com/redcanaryco/atomic-red-team/blob/1cf4dd51f83dcb0ebe6ade902d6157ad2dbc6ac8/atomics/T1218.001/T1218.001.md
author: Nasreddine Bencherchali (Nextron Systems)
date: 2022/10/05
tags:
- attack.defense_evasion
- attack.t1218.001
- detection.threat_hunting
logsource:
category: network_connection
product: windows
detection:
selection:
Image|endswith: '\hh.exe'
Initiated: 'true'
DestinationPort:
- 80
- 443
condition: selection
falsepositives:
- False positive is expected from launching "hh.exe" for the first time on a machine in a while or simply from help files containing reference to external sources. Best correlate this with process creation and file events.
level: medium
Fixes
This release includes a couple of false positives fixes and tuning of older rules to enhance their quality.
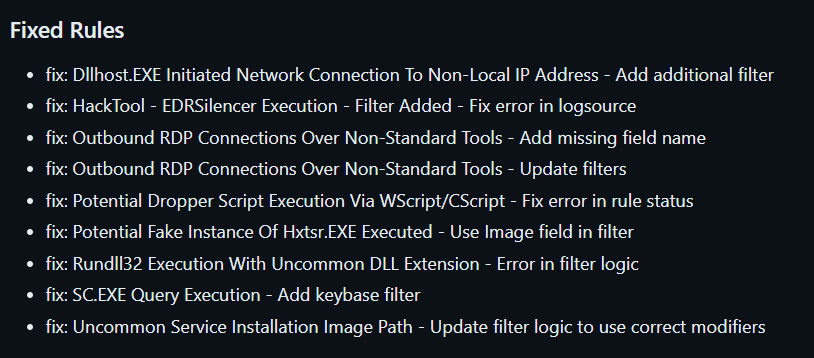
Please check the full changelog on the release page below for the complete list of changes and additions.
Release Release r2024-02-12 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
- @douglasrose75
- @frack113
- @jstnk9
- @nasbench
- @Neo23x0
- @omaramin17
- @phantinuss
- @prashanthpulisetti
- @qasimqlf
- @slincoln-aiq
- @swachchhanda000
- @xiangchen96
- @X-Junior
SigmaHQ Rules Release Highlights — r2024–02–12 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2024–02–12 | by Nasreddine Bencherchali | Feb, 2024 | Sigma_HQ