SigmaHQ Rules Release Highlights — r2024–01–29
 https://github.com/SigmaHQ/sigma/releases/tag/r2024-01-29
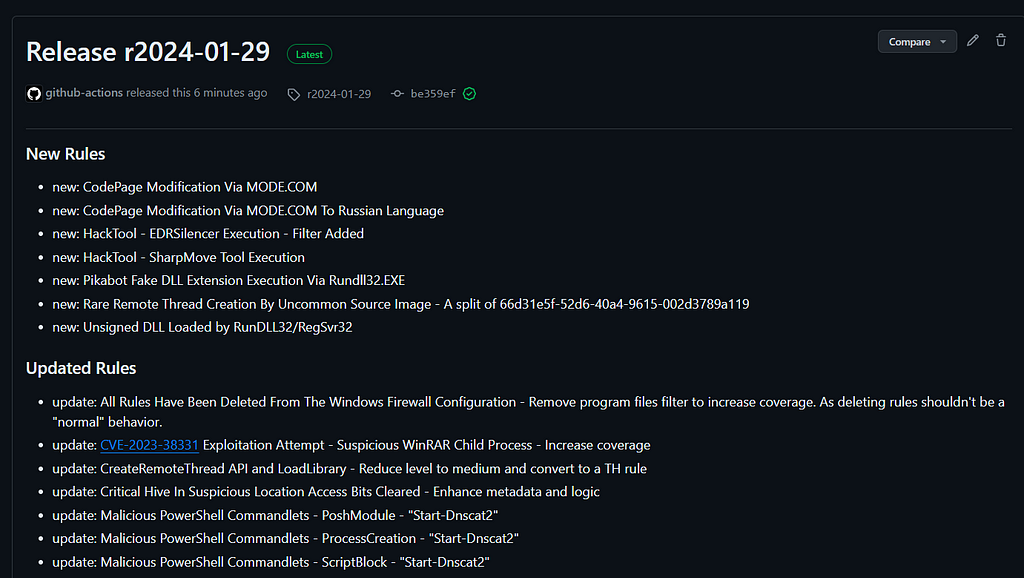
https://github.com/SigmaHQ/sigma/releases/tag/r2024-01-29Sigma Rule Packages for 29–01–2024 are released and available for download. This release saw the addition of 7 new rules, 30 rule updates and 11 rule fixes by 10+ contributors.
New Rules
Some highlights for the newer rules include new Pikabot rule to detect loading of DLL with uncommon extensions
title: Pikabot Fake DLL Extension Execution Via Rundll32.EXE
id: 1bf0ba65-9a39-42a2-9271-31d31bf2f0bf
status: experimental
description: |
Detects specific process tree behavior linked to "rundll32" executions, wherein the associated DLL lacks a common ".dll" extension, often signaling potential Pikabot activity.
references:
- https://github.com/pr0xylife/Pikabot
- https://tria.ge/231004-tp8k6sch9t/behavioral2
- https://www.virustotal.com/gui/file/56db0c4842a63234ab7fe2dda6eeb63aa7bb68f9a456985b519122f74dea37e2/behavior
- https://tria.ge/231212-r1bpgaefar/behavioral2
author: Swachchhanda Shrawan Poudel, Nasreddine Bencherchali (Nextron Systems)
date: 2024/01/26
tags:
- detection.emerging_threats
- attack.defense_evasion
- attack.execution
logsource:
product: windows
category: process_creation
detection:
selection:
ParentImage|endswith:
- '\cmd.exe'
- '\cscript.exe'
- '\mshta.exe'
- '\powershell.exe'
- '\pwsh.exe'
- '\regsvr32.exe'
- '\wscript.exe'
Image|endswith: '\rundll32.exe'
CommandLine|contains:
- ':\ProgramData\'
- ':\Users\Public\'
- ':\Windows\Installer\'
- '\AppData\Local\Temp\'
- '\AppData\Roaming\'
filter_main_known_extension:
- CommandLine|contains:
- '.cpl '
- '.cpl,'
- '.dll '
- '.dll,'
- '.inf '
- '.inf,'
- CommandLine|endswith:
- '.cpl'
- '.cpl"'
- '.dll'
- '.dll"'
- '.inf'
- '.inf"'
- ".cpl'"
- ".dll'"
- ".inf'"
condition: selection and not 1 of filter_main_*
falsepositives:
- Unknown
level: high
A couple of new rules to detect changing the CodePage to “Russian” or “Chinese” as seen used by malware in the wild using the “MODE.COM” utility.
title: CodePage Modification Via MODE.COM To Russian Language
id: 12fbff88-16b5-4b42-9754-cd001a789fb3
related:
- id: d48c5ffa-3b02-4c0f-9a9e-3c275650dd0e
type: derived
status: experimental
description: |
Detects a CodePage modification using the "mode.com" utility to Russian language.
This behavior has been used by threat actors behind Dharma ransomware.
references:
- https://learn.microsoft.com/en-us/windows/win32/intl/code-page-identifiers
- https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/mode
- https://strontic.github.io/xcyclopedia/library/mode.com-59D1ED51ACB8C3D50F1306FD75F20E99.html
- https://www.virustotal.com/gui/file/5e75ef02517afd6e8ba6462b19217dc4a5a574abb33d10eb0f2bab49d8d48c22/behavior
author: Joseliyo Sanchez, @Joseliyo_Jstnk
date: 2024/01/17
tags:
- attack.defense_evasion
- attack.t1036
logsource:
category: process_creation
product: windows
detection:
# VT Query: behavior:"mode con cp select=1251"
# VT Query: behavior:"mode con cp select=866"
selection_img:
- Image|endswith: '\mode.com'
- OriginalFileName: 'MODE.COM'
selection_cli:
CommandLine|contains|all:
- ' con '
- ' cp '
- ' select='
CommandLine|endswith:
- '=1251' # ANSI Cyrillic; Cyrillic (Windows) - Observed ITW by Dharma ransomware
- '=866' # OEM Russian; Cyrillic (DOS) - Observed ITW by other malware
condition: all of selection_*
falsepositives:
- Russian speaking people changing the CodePage
level: medium
2 new rules based on CLI flags, PE metadata and hardcoded settings for “EDRSilencer” and “SharpMove”.
title: HackTool - EDRSilencer Execution - Filter Added
id: 98054878-5eab-434c-85d4-72d4e5a3361b
status: experimental
description: |
Detects execution of EDRSilencer, a tool that abuses the Windows Filtering Platform (WFP) to block the outbound traffic of running EDR agents based on specific hardcoded filter names.
references:
- https://github.com/netero1010/EDRSilencer
author: Thodoris Polyzos (@SmoothDeploy)
date: 2024/01/29
tags:
- attack.defense_evasion
- attack.t1562
logsource:
category: windows_filtering_platform
product: windows
service: security
definition: 'Requirements: Audit Filtering Platform Policy Change needs to be enabled'
detection:
selection:
EventID:
- 5441
- 5447
FilterName|contains: 'Custom Outbound Filter'
condition: selection
falsepositives:
- Unknown
level: high
title: HackTool - SharpMove Tool Execution
id: 055fb54c-a8f4-4aee-bd44-f74cf30a0d9d
status: experimental
description: |
Detects the execution of SharpMove, a .NET utility performing multiple tasks such as "Task Creation", "SCM" query, VBScript execution using WMI via its PE metadata and command line options.
references:
- https://github.com/0xthirteen/SharpMove/
- https://pentestlab.blog/tag/sharpmove/
author: Luca Di Bartolomeo (CrimpSec)
date: 2024/01/29
tags:
- attack.lateral_movement
- attack.t1021.002
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\SharpMove.exe'
- OriginalFileName: SharpMove.exe
selection_cli_computer:
# In its current implementation the "computername" flag is required in all actions
CommandLine|contains: 'computername='
selection_cli_actions:
CommandLine|contains:
- 'action=create'
- 'action=dcom'
- 'action=executevbs'
- 'action=hijackdcom'
- 'action=modschtask'
- 'action=modsvc'
- 'action=query'
- 'action=scm'
- 'action=startservice'
- 'action=taskscheduler'
condition: selection_img or all of selection_cli_*
falsepositives:
- Unknown
level: high
New Updates
Many older rules have seen multiple improvements in coverage and metadata as well. Some examples include
Inreased coverage for the “Network Communication With Crypto Mining Pool” by adding additional pools.
title: Network Communication With Crypto Mining Pool
id: fa5b1358-b040-4403-9868-15f7d9ab6329
status: stable
description: Detects initiated network connections to crypto mining pools
references:
- https://www.poolwatch.io/coin/monero
- https://github.com/stamparm/maltrail/blob/3ea70459b9559134449423c0a7d8b965ac5c40ea/trails/static/suspicious/crypto_mining.txt
- https://www.virustotal.com/gui/search/behaviour_network%253A*.miningocean.org/files
author: Florian Roth (Nextron Systems), Nasreddine Bencherchali (Nextron Systems)
date: 2021/10/26
modified: 2024/01/19
tags:
- attack.impact
- attack.t1496
logsource:
category: network_connection
product: windows
detection:
selection:
DestinationHostname:
- 'alimabi.cn'
- 'ap.luckpool.net'
- 'bcn.pool.minergate.com'
- 'bcn.vip.pool.minergate.com'
- 'bohemianpool.com'
- 'ca-aipg.miningocean.org'
- 'ca-dynex.miningocean.org'
- 'ca-neurai.miningocean.org'
- 'ca-qrl.miningocean.org'
- 'ca-upx.miningocean.org'
- 'ca-zephyr.miningocean.org'
- 'ca.minexmr.com'
- 'ca.monero.herominers.com'
- 'cbd.monerpool.org'
- 'cbdv2.monerpool.org'
- 'cryptmonero.com'
- 'minemonero.gq'
- 'miner.ppxxmr.com'
- 'miner.rocks'
- 'minercircle.com'
- 'minergate.com'
- 'minerpool.pw'
- 'minerrocks.com'
- 'miners.pro'
- 'minerxmr.ru'
- 'minexmr.cn'
- 'minexmr.com'
- 'mining-help.ru'
- 'miningpoolhub.com'
- 'mixpools.org'
- 'moner.monerpool.org'
- 'moner1min.monerpool.org'
- 'monero-master.crypto-pool.fr'
- 'monero.crypto-pool.fr'
- 'monero.hashvault.pro'
- 'monero.herominers.com'
- 'monero.lindon-pool.win'
- 'monero.miners.pro'
- 'monero.riefly.id'
- 'monero.us.to'
- 'monerocean.stream'
- 'monerogb.com'
- 'monerohash.com'
...
- 'xx11m.monerpool.org'
- 'xx11mv2.monerpool.org'
- 'xxx.hex7e4.ru'
- 'zarabotaibitok.ru'
- 'zer0day.ru'
condition: selection
falsepositives:
- Unlikely
level: high
Enhanced logic of the rule using the “Kernel-General” provider with EventID 16. To detect utilities such as “QuarksPwDump” and similar that dump the registry.
The rules is using specific location by can and should be adapted to an environement.
title: Critical Hive In Suspicious Location Access Bits Cleared
id: 39f919f3-980b-4e6f-a975-8af7e507ef2b
related:
- id: 839dd1e8-eda8-4834-8145-01beeee33acd
type: obsoletes
status: test
description: |
Detects events from the Kernel-General ETW indicating that the access bits of a hive with a system like hive name located in the temp directory have been reset.
This occurs when an application tries to access a hive and the hive has not be recognized since the last 7 days (by default).
Registry hive dumping utilities such as QuarksPwDump were seen emitting this behavior.
references:
- https://github.com/nasbench/Misc-Research/blob/b20da2336de0f342d31ef4794959d28c8d3ba5ba/ETW/Microsoft-Windows-Kernel-General.md
author: Florian Roth (Nextron Systems)
date: 2017/05/15
modified: 2024/01/18
tags:
- attack.credential_access
- attack.t1003.002
logsource:
product: windows
service: system
detection:
selection:
EventID: 16
Provider_Name: Microsoft-Windows-Kernel-General
HiveName|contains:
- '\Temp\SAM'
- '\Temp\SECURITY'
condition: selection
falsepositives:
- Unknown
level: high
Re-work of the rule “Potential Dropper Script Execution Via WScript/CScript” to use more robust paths instead of generic one to reduce FP and still offer a good coverage by default.
title: Potential Dropper Script Execution Via WScript/CScript
id: cea72823-df4d-4567-950c-0b579eaf0846
related:
- id: 1e33157c-53b1-41ad-bbcc-780b80b58288
type: similar
status: deprecated
description: Detects wscript/cscript executions of scripts located in user directories
references:
- https://thedfirreport.com/2023/10/30/netsupport-intrusion-results-in-domain-compromise/
- https://redcanary.com/blog/gootloader/
author: Margaritis Dimitrios (idea), Florian Roth (Nextron Systems), oscd.community, Nasreddine Bencherchali (Nextron Systems)
date: 2019/01/16
modified: 2024/01/18
tags:
- attack.execution
- attack.t1059.005
- attack.t1059.007
logsource:
category: process_creation
product: windows
detection:
selection_exec:
Image|endswith:
- '\wscript.exe'
- '\cscript.exe'
selection_paths:
CommandLine|contains:
- ':\Temp\'
- ':\Tmp\'
- ':\Users\Public\'
- ':\Windows\Temp\'
- '\AppData\Local\Temp\'
selection_ext:
CommandLine|contains:
- '.js'
- '.jse'
- '.vba'
- '.vbe'
- '.vbs'
- '.wsf'
condition: all of selection_*
falsepositives:
- Some installers might generate a similar behavior. An initial baseline is required
level: medium
Fixes
This release includes a couple of false positives fixes and tuning of older rules to enhance their quality.
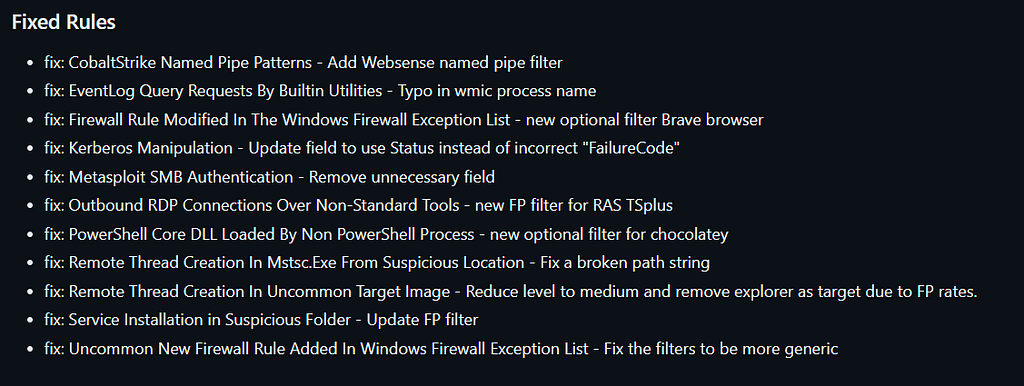
Please check the full changelog on the release page below for the complete list of changes and additions.
Release Release r2024-01-29 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
- @CrimpSec
- @frack113
- @jstnk9
- @nasbench
- @phantinuss
- @qasimqlf
- @slincoln-aiq
- @swachchhanda000
- @t-pol
- @tr0mb1r
- @xiangchen96
SigmaHQ Rules Release Highlights — r2024–01–29 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2024–01–29 | by Nasreddine Bencherchali | Jan, 2024 | Sigma_HQ