SigmaHQ Rules Release Highlights — r2024–01–15
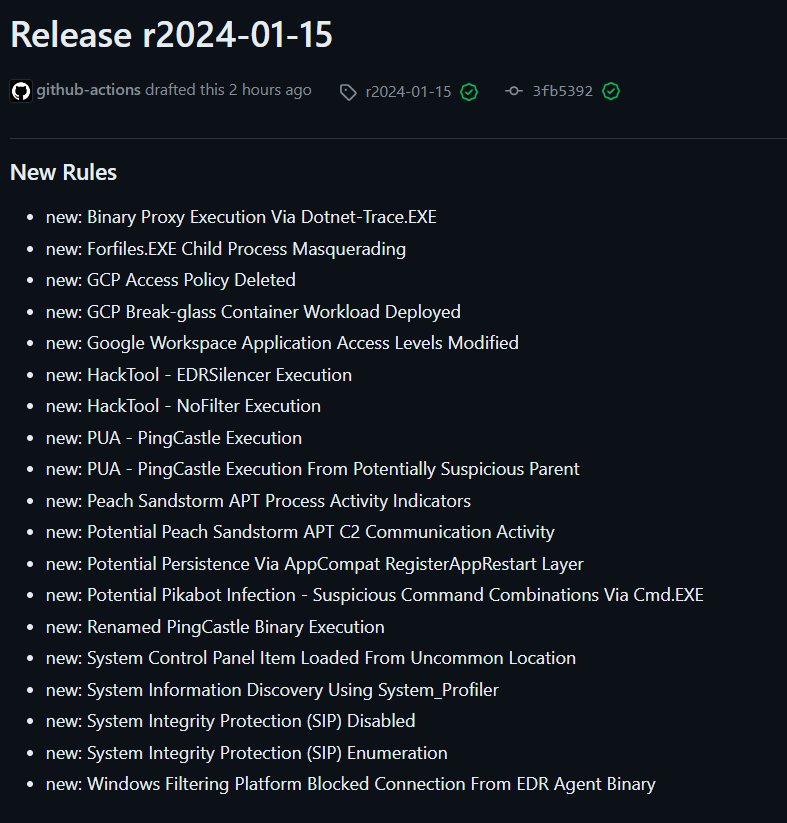 https://github.com/SigmaHQ/sigma/releases/tag/r2024-01-15
https://github.com/SigmaHQ/sigma/releases/tag/r2024-01-15Sigma Rule Packages for 15–01–2024 are released and available for download. This release saw the addition of 19 new rules, 17 rule updates and 5 rule fixes by 18+ contributors.
New Rules
Some highlights for the newer rules include, a detection covering a new LOLbin “Dotnet-Trace.EXE” reported by bohops
title: Binary Proxy Execution Via Dotnet-Trace.EXE
id: 9257c05b-4a4a-48e5-a670-b7b073cf401b
status: experimental
description: Detects commandline arguments for executing a child process via dotnet-trace.exe
references:
- https://twitter.com/bohops/status/1740022869198037480
author: Jimmy Bayne (@bohops)
date: 2024/01/02
tags:
- attack.execution
- attack.defense_evasion
- attack.t1218
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\dotnet-trace.exe'
- OriginalFileName: 'dotnet-trace.dll'
selection_cli:
CommandLine|contains|all:
- '-- '
- 'collect'
condition: all of selection_*
falsepositives:
- Legitimate usage of the utility in order to debug and trace a program.
level: medium
A new detection covering a new persistence reported by nasbench that make use of the “Register Application Restart” compatibility feature.
title: Potential Persistence Via AppCompat RegisterAppRestart Layer
id: b86852fb-4c77-48f9-8519-eb1b2c308b59
status: experimental
description: |
Detects the setting of the REGISTERAPPRESTART compatibility layer on an application.
This compatibility layer allows an application to register for restart using the "RegisterApplicationRestart" API.
This can be potentially abused as a persistence mechanism.
references:
- https://github.com/nasbench/Misc-Research/blob/d114d6a5e0a437d3818e492ef9864367152543e7/Other/Persistence-Via-RegisterAppRestart-Shim.md
author: Nasreddine Bencherchali (Nextron Systems)
date: 2024/01/01
tags:
- attack.persistence
- attack.t1546.011
logsource:
category: registry_set
product: windows
detection:
selection:
TargetObject|contains: '\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers\'
Details|contains: 'REGISTERAPPRESTART'
condition: selection
falsepositives:
- Legitimate applications making use of this feature for compatibility reasons
level: medium
Another new detection that leverages the “Windows Filtering Platform” event log that focus on finding block events of known EDR processes, covers a technique used by tools like EDRSilencer and EDRNoiseMaker.
title: Windows Filtering Platform Blocked Connection From EDR Agent Binary
id: bacf58c6-e199-4040-a94f-95dea0f1e45a
status: experimental
description: |
Detects a Windows Filtering Platform (WFP) blocked connection event involving common Endpoint Detection and Response (EDR) agents.
Adversaries may use WFP filters to prevent Endpoint Detection and Response (EDR) agents from reporting security events.
references:
- https://github.com/netero1010/EDRSilencer
- https://github.com/amjcyber/EDRNoiseMaker
- https://ghoulsec.medium.com/misc-series-4-forensics-on-edrsilencer-events-428b20b3f983
author: '@gott_cyber'
date: 2024/01/08
tags:
- attack.defense_evasion
- attack.t1562
logsource:
product: windows
service: security
definition: 'Requirements: Audit Filtering Platform Connection needs to be enabled'
detection:
selection:
EventID: 5157
Application|endswith:
- '\AmSvc.exe' # Cybereason
- '\cb.exe' # Carbon Black EDR
- '\CETASvc.exe' # TrendMicro Apex One
- '\CNTAoSMgr.exe' # TrendMicro Apex One
- '\CrAmTray.exe' # Cybereason
- '\CrsSvc.exe' # Cybereason
- '\CSFalconContainer.exe' # CrowdStrike Falcon
- '\CSFalconService.exe' # CrowdStrike Falcon
- '\CybereasonAV.exe' # Cybereason
- '\CylanceSvc.exe' # Cylance
- '\cyserver.exe' # Palo Alto Networks Traps/Cortex XDR
- '\CyveraService.exe' # Palo Alto Networks Traps/Cortex XDR
- '\CyvrFsFlt.exe' # Palo Alto Networks Traps/Cortex XDR
- '\EIConnector.exe' # ESET Inspect
- '\elastic-agent.exe' # Elastic EDR
- '\elastic-endpoint.exe' # Elastic EDR
- '\EndpointBasecamp.exe' # TrendMicro Apex One
- '\ExecutionPreventionSvc.exe' # Cybereason
- '\filebeat.exe' # Elastic EDR
- '\fortiedr.exe' # FortiEDR
- '\hmpalert.exe' # Sophos EDR
- '\hurukai.exe' # Harfanglab EDR
- '\LogProcessorService.exe' # SentinelOne
- '\mcsagent.exe' # Sophos EDR
- '\mcsclient.exe' # Sophos EDR
- '\MsMpEng.exe' # Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- '\MsSense.exe' # Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- '\Ntrtscan.exe' # TrendMicro Apex One
- '\PccNTMon.exe' # TrendMicro Apex One
- '\QualysAgent.exe' # Qualys EDR
- '\RepMgr.exe' # Carbon Black Cloud
- '\RepUtils.exe' # Carbon Black Cloud
- '\RepUx.exe' # Carbon Black Cloud
- '\RepWAV.exe' # Carbon Black Cloud
- '\RepWSC.exe' # Carbon Black Cloud
- '\sedservice.exe' # Sophos EDR
- '\SenseCncProxy.exe' # Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- '\SenseIR.exe' # Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- '\SenseNdr.exe' # Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- '\SenseSampleUploader.exe' # Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- '\SentinelAgent.exe' # SentinelOne
- '\SentinelAgentWorker.exe' # SentinelOne
- '\SentinelBrowserNativeHost.exe' # SentinelOne
- '\SentinelHelperService.exe' # SentinelOne
- '\SentinelServiceHost.exe' # SentinelOne
- '\SentinelStaticEngine.exe' # SentinelOne
- '\SentinelStaticEngineScanner.exe' # SentinelOne
- '\sfc.exe' # Cisco Secure Endpoint (Formerly Cisco AMP)
- '\sophos ui.exe' # Sophos EDR
- '\sophosfilescanner.exe' # Sophos EDR
- '\sophosfs.exe' # Sophos EDR
- '\sophoshealth.exe' # Sophos EDR
- '\sophosips.exe' # Sophos EDR
- '\sophosLivequeryservice.exe' # Sophos EDR
- '\sophosnetfilter.exe' # Sophos EDR
- '\sophosntpservice.exe' # Sophos EDR
- '\sophososquery.exe' # Sophos EDR
- '\sspservice.exe' # Sophos EDR
- '\TaniumClient.exe' # Tanium
- '\TaniumCX.exe' # Tanium
- '\TaniumDetectEngine.exe' # Tanium
- '\TMBMSRV.exe' # TrendMicro Apex One
- '\TmCCSF.exe' # TrendMicro Apex One
- '\TmListen.exe' # TrendMicro Apex One
- '\TmWSCSvc.exe' # TrendMicro Apex One
- '\Traps.exe' # Palo Alto Networks Traps/Cortex XDR
- '\winlogbeat.exe' # Elastic EDR
- '\WSCommunicator.exe' # TrendMicro Apex One
- '\xagt.exe' # Trellix EDR
condition: selection
falsepositives:
- Unlikely
level: high
Two other new detection covering Peach Sandstorm activity as reported by MSFT
title: Peach Sandstorm APT Process Activity Indicators
id: 2e7bbd54-2f26-476e-b4a1-ba5f1a012614
status: experimental
description: Detects process creation activity related to Peach Sandstorm APT
references:
- https://twitter.com/MsftSecIntel/status/1737895710169628824
- https://www.virustotal.com/gui/file/364275326bbfc4a3b89233dabdaf3230a3d149ab774678342a40644ad9f8d614/details
author: X__Junior (Nextron Systems)
date: 2024/01/15
tags:
- attack.execution
- detection.emerging_threats
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine|contains: 'QP''s\*(58vaP!tF4'
condition: selection
falsepositives:
- Unlikely
level: high
title: Potential Peach Sandstorm APT C2 Communication Activity
id: b8225208-81d0-4715-a822-12bcdd583e0f
status: experimental
description: Detects potential C2 communication activity related to Peach Sandstorm APT
references:
- https://twitter.com/MsftSecIntel/status/1737895710169628824
- https://www.virustotal.com/gui/file/364275326bbfc4a3b89233dabdaf3230a3d149ab774678342a40644ad9f8d614/details
author: X__Junior (Nextron Systems)
date: 2024/01/15
tags:
- attack.command_and_control
- detection.emerging_threats
logsource:
category: proxy
detection:
selection:
cs-method: 'GET'
c-uri|endswith:
- '/api/Core/Command/Init'
- '/api/Core/Command/Restart'
condition: selection
falsepositives:
- Unknown
level: medium
And a couple of IOC based rules to detect recent hacktool releases such as EDRSilencer and NoFilter
title: HackTool - NoFilter Execution
id: 7b14c76a-c602-4ae6-9717-eff868153fc0
status: experimental
description: |
Detects execution of NoFilter, a tool for abusing the Windows Filtering Platform for privilege escalation via hardcoded policy name indicators
references:
- https://github.com/deepinstinct/NoFilter/blob/121d215ab130c5e8e3ad45a7e7fcd56f4de97b4d/NoFilter/Consts.cpp
- https://github.com/deepinstinct/NoFilter
- https://www.deepinstinct.com/blog/nofilter-abusing-windows-filtering-platform-for-privilege-escalation
- https://x.com/_st0pp3r_/status/1742203752361128162?s=20
author: Stamatis Chatzimangou (st0pp3r)
date: 2024/01/05
tags:
- attack.privilege_escalation
- attack.t1134
- attack.t1134.001
logsource:
product: windows
service: security
definition: 'Requirements: Audit Filtering Platform Policy Change needs to be enabled'
detection:
selection_5447:
EventID: 5447
FilterName|contains: 'RonPolicy'
selection_5449:
EventID: 5449
ProviderContextName|contains: 'RonPolicy'
condition: 1 of selection_*
falsepositives:
- Unknown
level: high
New Updates
Many older rules have seen multiple improvements in coverage and metadata as well. Some examples include
Additional Imphash values have been added to the IOC based rule to detect different default/pre-compiled hacktool binaries
title: Hacktool Execution - Imphash
id: 24e3e58a-646b-4b50-adef-02ef935b9fc8
status: test
description: Detects the execution of different Windows based hacktools via their import hash (imphash) even if the files have been renamed
references:
- Internal Research
author: Florian Roth (Nextron Systems)
date: 2022/03/04
modified: 2024/01/15
tags:
- attack.credential_access
- attack.t1588.002
- attack.t1003
logsource:
category: process_creation
product: windows
detection:
selection:
- Imphash:
- bcca3c247b619dcd13c8cdff5f123932 # PetitPotam
- 3a19059bd7688cb88e70005f18efc439 # PetitPotam
- bf6223a49e45d99094406777eb6004ba # PetitPotam
- 23867a89c2b8fc733be6cf5ef902f2d1 # JuicyPotato
- a37ff327f8d48e8a4d2f757e1b6e70bc # JuicyPotato
- f9a28c458284584a93b14216308d31bd # JuicyPotatoNG
- 6118619783fc175bc7ebecff0769b46e # RoguePotato
- 959a83047e80ab68b368fdb3f4c6e4ea # RoguePotato
- 563233bfa169acc7892451f71ad5850a # RoguePotato
- 87575cb7a0e0700eb37f2e3668671a08 # RoguePotato
- 13f08707f759af6003837a150a371ba1 # Pwdump
- 1781f06048a7e58b323f0b9259be798b # Pwdump
- 233f85f2d4bc9d6521a6caae11a1e7f5 # Pwdump
- 24af2584cbf4d60bbe5c6d1b31b3be6d # Pwdump
- 632969ddf6dbf4e0f53424b75e4b91f2 # Pwdump
- 713c29b396b907ed71a72482759ed757 # Pwdump
- 749a7bb1f0b4c4455949c0b2bf7f9e9f # Pwdump
- 8628b2608957a6b0c6330ac3de28ce2e # Pwdump
- 8b114550386e31895dfab371e741123d # Pwdump
- 94cb940a1a6b65bed4d5a8f849ce9793 # PwDumpX
- 9d68781980370e00e0bd939ee5e6c141 # Pwdump
- b18a1401ff8f444056d29450fbc0a6ce # Pwdump
- cb567f9498452721d77a451374955f5f # Pwdump
- 730073214094cd328547bf1f72289752 # Htran
- 17b461a082950fc6332228572138b80c # Cobalt Strike beacons
- dc25ee78e2ef4d36faa0badf1e7461c9 # Cobalt Strike beacons
- 819b19d53ca6736448f9325a85736792 # Cobalt Strike beacons
- 829da329ce140d873b4a8bde2cbfaa7e # Cobalt Strike beacons
- c547f2e66061a8dffb6f5a3ff63c0a74 # PPLDump
- 0588081ab0e63ba785938467e1b10cca # PPLDump
- 0d9ec08bac6c07d9987dfd0f1506587c # NanoDump
- bc129092b71c89b4d4c8cdf8ea590b29 # NanoDump
- 4da924cf622d039d58bce71cdf05d242 # NanoDump
- e7a3a5c377e2d29324093377d7db1c66 # NanoDump
- 9a9dbec5c62f0380b4fa5fd31deffedf # NanoDump
- af8a3976ad71e5d5fdfb67ddb8dadfce # NanoDump
- 0c477898bbf137bbd6f2a54e3b805ff4 # NanoDump
- 0ca9f02b537bcea20d4ea5eb1a9fe338 # NanoDump
- 3ab3655e5a14d4eefc547f4781bf7f9e # NanoDump
- e6f9d5152da699934b30daab206471f6 # NanoDump
- 3ad59991ccf1d67339b319b15a41b35d # NanoDump
- ffdd59e0318b85a3e480874d9796d872 # NanoDump
- 0cf479628d7cc1ea25ec7998a92f5051 # NanoDump
- 07a2d4dcbd6cb2c6a45e6b101f0b6d51 # NanoDump
- d6d0f80386e1380d05cb78e871bc72b1 # NanoDump
- 38d9e015591bbfd4929e0d0f47fa0055 # HandleKatz
- 0e2216679ca6e1094d63322e3412d650 # HandleKatz
- ada161bf41b8e5e9132858cb54cab5fb # DripLoader
- 2a1bc4913cd5ecb0434df07cb675b798 # DripLoader
- 11083e75553baae21dc89ce8f9a195e4 # DripLoader
- a23d29c9e566f2fa8ffbb79267f5df80 # DripLoader
- 4a07f944a83e8a7c2525efa35dd30e2f # CreateMiniDump
- 767637c23bb42cd5d7397cf58b0be688 # UACMe Akagi
- 14c4e4c72ba075e9069ee67f39188ad8 # UACMe Akagi
- 3c782813d4afce07bbfc5a9772acdbdc # UACMe Akagi
- 7d010c6bb6a3726f327f7e239166d127 # UACMe Akagi
- 89159ba4dd04e4ce5559f132a9964eb3 # UACMe Akagi
- 6f33f4a5fc42b8cec7314947bd13f30f # UACMe Akagi
- 5834ed4291bdeb928270428ebbaf7604 # UACMe Akagi
- 5a8a8a43f25485e7ee1b201edcbc7a38 # UACMe Akagi
- dc7d30b90b2d8abf664fbed2b1b59894 # UACMe Akagi
- 41923ea1f824fe63ea5beb84db7a3e74 # UACMe Akagi
- 3de09703c8e79ed2ca3f01074719906b # UACMe Akagi
- a53a02b997935fd8eedcb5f7abab9b9f # WCE
- e96a73c7bf33a464c510ede582318bf2 # WCE
- 32089b8851bbf8bc2d014e9f37288c83 # Sliver Stagers
- 09D278F9DE118EF09163C6140255C690 # Dumpert
- 03866661686829d806989e2fc5a72606 # Dumpert
- e57401fbdadcd4571ff385ab82bd5d6d # Dumpert
- 84B763C45C0E4A3E7CA5548C710DB4EE # SysmonEnte
- 19584675d94829987952432e018d5056 # SysmonQuiet
- 330768a4f172e10acb6287b87289d83b # ShaprEvtMute Hook
- 885c99ccfbe77d1cbfcb9c4e7c1a3313 # Forkatz
- 22a22bc9e4e0d2f189f1ea01748816ac # PPLKiller
- 7fa30e6bb7e8e8a69155636e50bf1b28 # PPLKiller
- 96df3a3731912449521f6f8d183279b1 # Backstab
- 7e6cf3ff4576581271ac8a313b2aab46 # Backstab
- 51791678f351c03a0eb4e2a7b05c6e17 # Backstab
- 25ce42b079282632708fc846129e98a5 # Forensia
- 021bcca20ba3381b11bdde26b4e62f20 # EDRSandBlast
- 59223b5f52d8799d38e0754855cbdf42 # EDRSandBlast
- 81e75d8f1d276c156653d3d8813e4a43 # EDRSandBlast
- 17244e8b6b8227e57fe709ccad421420 # EDRSandBlast
- 5b76da3acdedc8a5cdf23a798b5936b4 # EDRSandBlast
- cb2b65bb77d995cc1c0e5df1c860133c # EDRSandBlast
- 40445337761d80cf465136fafb1f63e6 # EDRSandBlast
- 8a790f401b29fa87bc1e56f7272b3aa6 # EDRSilencer
- Hashes|contains: # Sysmon field hashes contains all types
- IMPHASH=BCCA3C247B619DCD13C8CDFF5F123932 # PetitPotam
- IMPHASH=3A19059BD7688CB88E70005F18EFC439 # PetitPotam
- IMPHASH=bf6223a49e45d99094406777eb6004ba # PetitPotam
- IMPHASH=23867A89C2B8FC733BE6CF5EF902F2D1 # JuicyPotato
- IMPHASH=A37FF327F8D48E8A4D2F757E1B6E70BC # JuicyPotato
- IMPHASH=F9A28C458284584A93B14216308D31BD # JuicyPotatoNG
- IMPHASH=6118619783FC175BC7EBECFF0769B46E # RoguePotato
- IMPHASH=959A83047E80AB68B368FDB3F4C6E4EA # RoguePotato
- IMPHASH=563233BFA169ACC7892451F71AD5850A # RoguePotato
- IMPHASH=87575CB7A0E0700EB37F2E3668671A08 # RoguePotato
- IMPHASH=13F08707F759AF6003837A150A371BA1 # Pwdump
- IMPHASH=1781F06048A7E58B323F0B9259BE798B # Pwdump
- IMPHASH=233F85F2D4BC9D6521A6CAAE11A1E7F5 # Pwdump
- IMPHASH=24AF2584CBF4D60BBE5C6D1B31B3BE6D # Pwdump
- IMPHASH=632969DDF6DBF4E0F53424B75E4B91F2 # Pwdump
- IMPHASH=713C29B396B907ED71A72482759ED757 # Pwdump
- IMPHASH=749A7BB1F0B4C4455949C0B2BF7F9E9F # Pwdump
- IMPHASH=8628B2608957A6B0C6330AC3DE28CE2E # Pwdump
- IMPHASH=8B114550386E31895DFAB371E741123D # Pwdump
- IMPHASH=94CB940A1A6B65BED4D5A8F849CE9793 # PwDumpX
- IMPHASH=9D68781980370E00E0BD939EE5E6C141 # Pwdump
- IMPHASH=B18A1401FF8F444056D29450FBC0A6CE # Pwdump
- IMPHASH=CB567F9498452721D77A451374955F5F # Pwdump
- IMPHASH=730073214094CD328547BF1F72289752 # Htran
- IMPHASH=17B461A082950FC6332228572138B80C # Cobalt Strike beacons
- IMPHASH=DC25EE78E2EF4D36FAA0BADF1E7461C9 # Cobalt Strike beacons
- IMPHASH=819B19D53CA6736448F9325A85736792 # Cobalt Strike beacons
- IMPHASH=829DA329CE140D873B4A8BDE2CBFAA7E # Cobalt Strike beacons
- IMPHASH=C547F2E66061A8DFFB6F5A3FF63C0A74 # PPLDump
- IMPHASH=0588081AB0E63BA785938467E1B10CCA # PPLDump
- IMPHASH=0D9EC08BAC6C07D9987DFD0F1506587C # NanoDump
- IMPHASH=BC129092B71C89B4D4C8CDF8EA590B29 # NanoDump
- IMPHASH=4DA924CF622D039D58BCE71CDF05D242 # NanoDump
- IMPHASH=E7A3A5C377E2D29324093377D7DB1C66 # NanoDump
- IMPHASH=9A9DBEC5C62F0380B4FA5FD31DEFFEDF # NanoDump
- IMPHASH=AF8A3976AD71E5D5FDFB67DDB8DADFCE # NanoDump
- IMPHASH=0C477898BBF137BBD6F2A54E3B805FF4 # NanoDump
- IMPHASH=0CA9F02B537BCEA20D4EA5EB1A9FE338 # NanoDump
- IMPHASH=3AB3655E5A14D4EEFC547F4781BF7F9E # NanoDump
- IMPHASH=E6F9D5152DA699934B30DAAB206471F6 # NanoDump
- IMPHASH=3AD59991CCF1D67339B319B15A41B35D # NanoDump
- IMPHASH=FFDD59E0318B85A3E480874D9796D872 # NanoDump
- IMPHASH=0CF479628D7CC1EA25EC7998A92F5051 # NanoDump
- IMPHASH=07A2D4DCBD6CB2C6A45E6B101F0B6D51 # NanoDump
- IMPHASH=D6D0F80386E1380D05CB78E871BC72B1 # NanoDump
- IMPHASH=38D9E015591BBFD4929E0D0F47FA0055 # HandleKatz
- IMPHASH=0E2216679CA6E1094D63322E3412D650 # HandleKatz
- IMPHASH=ADA161BF41B8E5E9132858CB54CAB5FB # DripLoader
- IMPHASH=2A1BC4913CD5ECB0434DF07CB675B798 # DripLoader
- IMPHASH=11083E75553BAAE21DC89CE8F9A195E4 # DripLoader
- IMPHASH=A23D29C9E566F2FA8FFBB79267F5DF80 # DripLoader
- IMPHASH=4A07F944A83E8A7C2525EFA35DD30E2F # CreateMiniDump
- IMPHASH=767637C23BB42CD5D7397CF58B0BE688 # UACMe Akagi
- IMPHASH=14C4E4C72BA075E9069EE67F39188AD8 # UACMe Akagi
- IMPHASH=3C782813D4AFCE07BBFC5A9772ACDBDC # UACMe Akagi
- IMPHASH=7D010C6BB6A3726F327F7E239166D127 # UACMe Akagi
- IMPHASH=89159BA4DD04E4CE5559F132A9964EB3 # UACMe Akagi
- IMPHASH=6F33F4A5FC42B8CEC7314947BD13F30F # UACMe Akagi
- IMPHASH=5834ED4291BDEB928270428EBBAF7604 # UACMe Akagi
- IMPHASH=5A8A8A43F25485E7EE1B201EDCBC7A38 # UACMe Akagi
- IMPHASH=DC7D30B90B2D8ABF664FBED2B1B59894 # UACMe Akagi
- IMPHASH=41923EA1F824FE63EA5BEB84DB7A3E74 # UACMe Akagi
- IMPHASH=3DE09703C8E79ED2CA3F01074719906B # UACMe Akagi
- IMPHASH=A53A02B997935FD8EEDCB5F7ABAB9B9F # WCE
- IMPHASH=E96A73C7BF33A464C510EDE582318BF2 # WCE
- IMPHASH=32089B8851BBF8BC2D014E9F37288C83 # Sliver Stagers
- IMPHASH=09D278F9DE118EF09163C6140255C690 # Dumpert
- IMPHASH=03866661686829d806989e2fc5a72606 # Dumpert
- IMPHASH=e57401fbdadcd4571ff385ab82bd5d6d # Dumpert
- IMPHASH=84B763C45C0E4A3E7CA5548C710DB4EE # SysmonEnte
- IMPHASH=19584675D94829987952432E018D5056 # SysmonQuiet
- IMPHASH=330768A4F172E10ACB6287B87289D83B # ShaprEvtMute Hook
- IMPHASH=885C99CCFBE77D1CBFCB9C4E7C1A3313 # Forkatz
- IMPHASH=22A22BC9E4E0D2F189F1EA01748816AC # PPLKiller
- IMPHASH=7FA30E6BB7E8E8A69155636E50BF1B28 # PPLKiller
- IMPHASH=96DF3A3731912449521F6F8D183279B1 # Backstab
- IMPHASH=7E6CF3FF4576581271AC8A313B2AAB46 # Backstab
- IMPHASH=51791678F351C03A0EB4E2A7B05C6E17 # Backstab
- IMPHASH=25CE42B079282632708FC846129E98A5 # Forensia
- IMPHASH=021BCCA20BA3381B11BDDE26B4E62F20 # EDRSandBlast
- IMPHASH=59223B5F52D8799D38E0754855CBDF42 # EDRSandBlast
- IMPHASH=81E75D8F1D276C156653D3D8813E4A43 # EDRSandBlast
- IMPHASH=17244E8B6B8227E57FE709CCAD421420 # EDRSandBlast
- IMPHASH=5B76DA3ACDEDC8A5CDF23A798B5936B4 # EDRSandBlast
- IMPHASH=CB2B65BB77D995CC1C0E5DF1C860133C # EDRSandBlast
- IMPHASH=40445337761D80CF465136FAFB1F63E6 # EDRSandBlast
- IMPHASH=8A790F401B29FA87BC1E56F7272B3AA6 # EDRSilencer
condition: selection
falsepositives:
- Legitimate use of one of these tools
level: critical
Inreased coverage of the “Hypervisor Enforced Code Integrity Disabled” rule by adding additional values that include change via group policy and older windows key/value.
title: Hypervisor Enforced Code Integrity Disabled
id: 8b7273a4-ba5d-4d8a-b04f-11f2900d043a
status: experimental
description: Detects changes to the HypervisorEnforcedCodeIntegrity registry key and the "Enabled" value being set to 0 in order to disable the Hypervisor Enforced Code Integrity feature. This allows an attacker to load unsigned and untrusted code to be run in the kernel
references:
- https://www.welivesecurity.com/2023/03/01/blacklotus-uefi-bootkit-myth-confirmed/
- https://github.com/redcanaryco/atomic-red-team/blob/04e487c1828d76df3e834621f4f893ea756d5232/atomics/T1562.001/T1562.001.md#atomic-test-43---disable-hypervisor-enforced-code-integrity-hvci
author: Nasreddine Bencherchali (Nextron Systems), Anish Bogati
date: 2023/03/14
modified: 2024/01/10
tags:
- attack.defense_evasion
- attack.t1562.001
logsource:
category: registry_set
product: windows
detection:
selection:
EventType: SetValue
TargetObject|endswith:
- '\Microsoft\Windows\DeviceGuard\HypervisorEnforcedCodeIntegrity'
- '\Control\DeviceGuard\HypervisorEnforcedCodeIntegrity'
- '\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity\Enabled'
Details: 'DWORD (0x00000000)'
condition: selection
falsepositives:
- Unknown
level: high
New Cmdlets added to increase coverage of the rule “Tamper Windows Defender”.
title: Tamper Windows Defender - ScriptBlockLogging
id: 14c71865-6cd3-44ae-adaa-1db923fae5f2
related:
- id: ec19ebab-72dc-40e1-9728-4c0b805d722c
type: derived
status: experimental
description: Detects PowerShell scripts attempting to disable scheduled scanning and other parts of Windows Defender ATP or set default actions to allow.
references:
- https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1562.001/T1562.001.md
- https://docs.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps
- https://bidouillesecurity.com/disable-windows-defender-in-powershell/
author: frack113, elhoim, Tim Shelton (fps, alias support), Swachchhanda Shrawan Poudel, Nasreddine Bencherchali (Nextron Systems)
date: 2022/01/16
modified: 2024/01/02
tags:
- attack.defense_evasion
- attack.t1562.001
logsource:
product: windows
category: ps_script
definition: 'Requirements: Script Block Logging must be enabled'
detection:
selection_options_disabling_preference:
ScriptBlockText|contains: 'Set-MpPreference'
selection_options_disabling_function:
ScriptBlockText|contains:
- '-dbaf $true'
- '-dbaf 1'
- '-dbm $true'
- '-dbm 1'
- '-dips $true'
- '-dips 1'
- '-DisableArchiveScanning $true'
- '-DisableArchiveScanning 1'
- '-DisableBehaviorMonitoring $true'
- '-DisableBehaviorMonitoring 1'
- '-DisableBlockAtFirstSeen $true'
- '-DisableBlockAtFirstSeen 1'
- '-DisableCatchupFullScan $true'
- '-DisableCatchupFullScan 1'
- '-DisableCatchupQuickScan $true'
- '-DisableCatchupQuickScan 1'
- '-DisableIntrusionPreventionSystem $true'
- '-DisableIntrusionPreventionSystem 1'
- '-DisableIOAVProtection $true'
- '-DisableIOAVProtection 1'
- '-DisableRealtimeMonitoring $true'
- '-DisableRealtimeMonitoring 1'
- '-DisableRemovableDriveScanning $true'
- '-DisableRemovableDriveScanning 1'
- '-DisableScanningMappedNetworkDrivesForFullScan $true'
- '-DisableScanningMappedNetworkDrivesForFullScan 1'
- '-DisableScanningNetworkFiles $true'
- '-DisableScanningNetworkFiles 1'
- '-DisableScriptScanning $true'
- '-DisableScriptScanning 1'
- '-MAPSReporting $false'
- '-MAPSReporting 0'
- '-drdsc $true'
- '-drdsc 1'
- '-drtm $true'
- '-drtm 1'
- '-dscrptsc $true'
- '-dscrptsc 1'
- '-dsmndf $true'
- '-dsmndf 1'
- '-dsnf $true'
- '-dsnf 1'
- '-dss $true'
- '-dss 1'
selection_other_default_actions_allow:
ScriptBlockText|contains: 'Set-MpPreference'
selection_other_default_actions_func:
ScriptBlockText|contains:
- 'HighThreatDefaultAction Allow'
- 'htdefac Allow'
- 'LowThreatDefaultAction Allow'
- 'ltdefac Allow'
- 'ModerateThreatDefaultAction Allow'
- 'mtdefac Allow'
- 'SevereThreatDefaultAction Allow'
- 'stdefac Allow'
condition: all of selection_options_disabling_* or all of selection_other_default_actions_*
falsepositives:
- Legitimate PowerShell scripts that disable Windows Defender for troubleshooting purposes. Must be investigated.
level: high
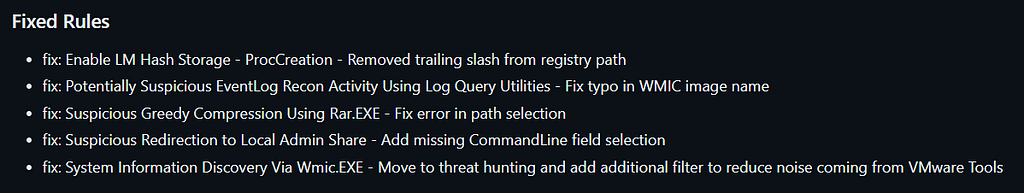
Fixes
This release includes a couple of false positives fixes and tuning of older rules to enhance their quality.
Please check the full changelog on the release page below for the complete list of changes and additions.
Release Release r2024-01-15 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
- @ahouspan
- @bohops
- @danielgottt
- @frack113
- @joshnck
- @jstnk9
- @meiliumeiliu
- @MrSeccubus
- @nasbench
- @Neo23x0
- @phantinuss
- @qasimqlf
- @slincoln-aiq
- @st0pp3r
- @tr0mb1r
- @Tuutaans
- @X-Junior
- @zestsg
SigmaHQ Rules Release Highlights — r2024–01–15 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2024–01–15 | by Nasreddine Bencherchali | Jan, 2024 | Sigma_HQ