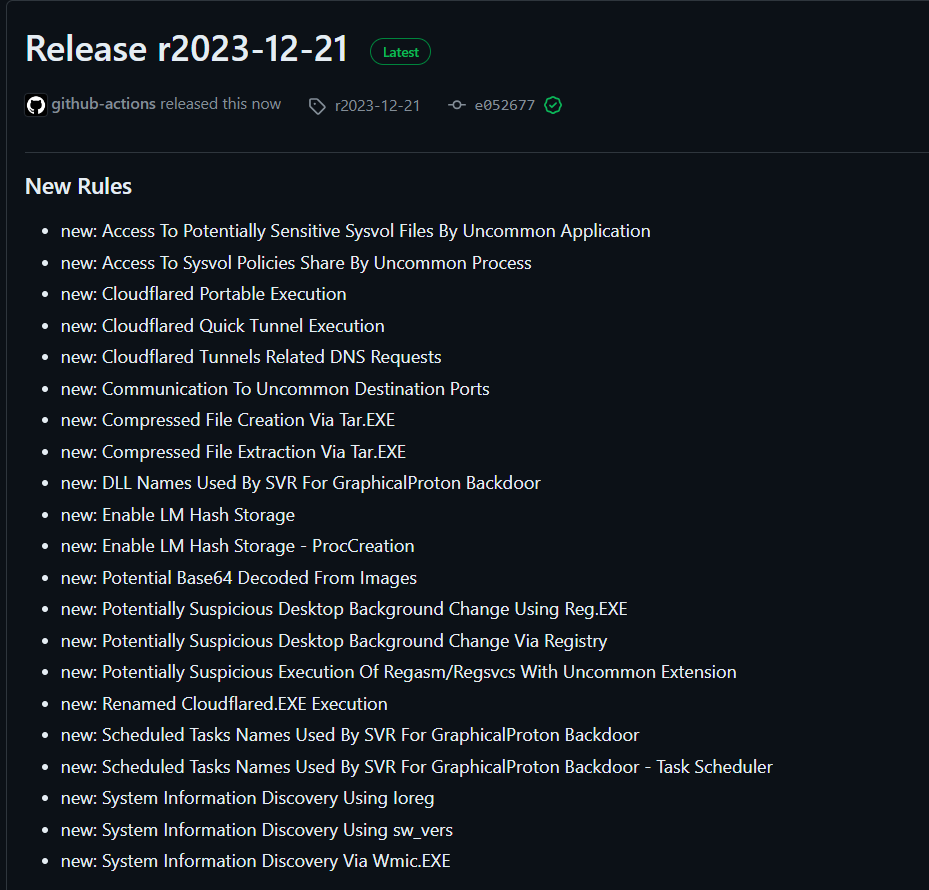
SigmaHQ Rules Release Highlights — r2023–12–21
 https://github.com/SigmaHQ/sigma/releases/tag/r2023-12-21
https://github.com/SigmaHQ/sigma/releases/tag/r2023-12-21Sigma Rule Packages for 21–12–2023 are released and available for download. This release saw the addition of 21 new rules, 55 rule updates and 30 rule fixes by 17+ contributors.
New Rules
Some highlights for the newer rules include, new detections for Cloudflared a tunneling tool by cloudflare covering additional flags, renamed versions and DNS requests.
title: Cloudflared Portable Execution
id: fadb84f0-4e84-4f6d-a1ce-9ef2bffb6ccd
status: experimental
description: |
Detects the execution of the "cloudflared" binary from a non standard location.
references:
- https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/do-more-with-tunnels/trycloudflare/
- https://github.com/cloudflare/cloudflared
- https://www.intrinsec.com/akira_ransomware/
- https://www.guidepointsecurity.com/blog/tunnel-vision-cloudflared-abused-in-the-wild/
- https://github.com/cloudflare/cloudflared/releases
author: Nasreddine Bencherchali (Nextron Systems)
tags:
- attack.command_and_control
- attack.t1090.001
date: 2023/12/20
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\cloudflared.exe'
filter_main_admin_location:
Image|contains:
- ':\Program Files (x86)\cloudflared\'
- ':\Program Files\cloudflared\'
condition: selection and not 1 of filter_main_*
falsepositives:
- Legitimate usage of Cloudflared portable versions
level: medium
title: Cloudflared Tunnels Related DNS Requests
id: a1d9eec5-33b2-4177-8d24-27fe754d0812
status: experimental
description: Detects DNS query requests to Cloudflared tunnels domains.
references:
- https://www.guidepointsecurity.com/blog/tunnel-vision-cloudflared-abused-in-the-wild/
- Internal Research
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/12/20
tags:
- attack.command_and_control
- attack.t1071.001
logsource:
category: dns_query
product: windows
detection:
selection:
QueryName|endswith:
- '.v2.argotunnel.com'
- 'protocol-v2.argotunnel.com'
- 'trycloudflare.com'
- 'update.argotunnel.com'
condition: selection
falsepositives:
- Legitimate use of cloudflare tunnels will also trigger this.
level: medium
title: Cloudflared Quick Tunnel Execution
id: 222129f7-f4dc-4568-b0d2-22440a9639ba
related:
- id: 7050bba1-1aed-454e-8f73-3f46f09ce56a
type: similar
- id: 9a019ffc-3580-4c9d-8d87-079f7e8d3fd4
type: similar
status: experimental
description: |
Detects creation of an ad-hoc Cloudflare Quick Tunnel, which can be used to tunnel local services such as HTTP, RDP, SSH and SMB.
The free TryCloudflare Quick Tunnel will generate a random subdomain on trycloudflare[.]com, following a call to api[.]trycloudflare[.]com.
The tool has been observed in use by threat groups including Akira ransomware.
references:
- https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/do-more-with-tunnels/trycloudflare/
- https://github.com/cloudflare/cloudflared
- https://www.intrinsec.com/akira_ransomware/
- https://www.guidepointsecurity.com/blog/tunnel-vision-cloudflared-abused-in-the-wild/
author: Sajid Nawaz Khan
tags:
- attack.command_and_control
- attack.t1090.001
date: 2023/12/20
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith:
- '\cloudflared.exe'
- '\cloudflared-windows-386.exe'
- '\cloudflared-windows-amd64.exe'
- Hashes|contains:
- 'SHA256=2fb6c04c4f95fb8d158af94c137f90ac820716deaf88d8ebec956254e046cb29'
- 'SHA256=b3d21940a10fdef5e415ad70331ce257c24fe3bcf7722262302e0421791f87e8'
- 'SHA256=1fbd8362b2d2d2e6a5750ae3db69cd1815e6c1d31da48a98b796450971a8e039'
- 'SHA256=0409c9b12f9d0eda86e461ed9bdabeefb00172b26322079681a0bdf48e68dc28'
- 'SHA256=7cfb411d04bac42ef93d1f0c93c0a481e38c6f4612b97ae89d4702595988edc7'
- 'SHA256=5b3c2d846ab162dc6bc595cce3a49de5731afde5d6060be7066d21b013a28373'
- 'SHA256=ce95df7f69664c3df19b76028e115931919a71517b776da7b42d353e2ff4a670'
- 'SHA256=1293525a19cfe3bc8296b62fbfe19f083632ed644a1c18c10b045a1d3030d81a'
- 'SHA256=af2b9161cfcb654b16408cd6b098afe9d1fb61a037d18d7090a119d4c0c8e0f0'
- 'SHA256=39ddceb56a15798826a5fc4892fa2b474c444bb4d7a8bf2fa95e41cab10fa7a1'
- 'SHA256=ccd11f2328023a0e7929e845d5b6e7bc783fb4650d65faef3ae090239d4bbce2'
- 'SHA256=b6e5c5d2567ae8c69cc012ebcae30e6c9b5359d64a58d17ba75ec89f8bce71ac'
- 'SHA256=f813484ea441404f18caad96f28138e8aaf0cb256163c09c2ab8a3acab87f69f'
- 'SHA256=fc4a0802ab9c7409b892ca00636bec61e2acfc911bccfdeb9978b8ab5a2f828d'
- 'SHA256=083150724b49604c8765c1ba19541fa260b133be0acb0647fcd936d81f054499'
- 'SHA256=44303d6572956f28a0f2e4b188934fb9874f2584f5c81fa431a463cfbf28083b'
- 'SHA256=5d38c46032a58e28ae5f7d174d8761ec3d64d186677f3ec53af5f51afb9bfd2f'
- 'SHA256=e1e70fa42059911bc6685fafef957f9a73fc66f214d0704a9b932683a5204032'
- 'SHA256=c01356092a365b84f84f0e66870bd1a05ba3feb53cafd973fa5fea2534bee234'
- 'SHA256=b3f9c06151e30ee43d39e788a79cd918a314f24e04fe87f3de8272a2057b624f'
- 'SHA256=cd81b2792f0739f473c31c9cb7cf2313154bfa28b839975802b90e8790bb5058'
- 'SHA256=9ec7e6c8e1bfd883663d8d9d62c9e4f9ae373b731407181e32491b27a7218a2c'
- 'SHA256=c2cfd23fdc6c0e1b1ffa0e545cbe556f18d11b362b4a89ba0713f6ab01c4827f'
- 'SHA256=53f8adbd76c0eb16f5e43cadde422474d8a06f9c8f959389c1930042ad8beaa5'
- 'SHA256=648c8d2f8001c113d2986dd00b7bbd181593d462bef73522cee212c4f71f95b3'
- 'SHA256=ae047e2095e46c3f9c518b2be67ec753f4f0aad23b261a361fcb6144dcdb63b4'
- 'SHA256=3153d2baa462978dd22ab33d1c2274ecc88c200225d6a3327f98d5b752d08f5c'
- 'SHA256=f49cde976e628012c9db73e1c8d76081944ecf2297cdafeb78bb13290da274c4'
- 'SHA256=d2513e58bb03ccc83affde685c6ef987924c37ce6707d8e9857e2524b0d7e90f'
- 'SHA256=bb67c7623ba92fe64ffd9816b8d5b3b1ea3013960a30bd4cf6e295b3eb5b1bad'
- 'SHA256=b34b3c3a91e3165d1481f0b3ec23eab93a1cfba94345a6cbfe5b18ddbd48eac7'
- 'SHA256=f7848034e010d55f15e474ca998f96391e320ff29b00cfcc4c5e536529703e75'
- 'SHA256=b6fc9493778cbe3bfc062d73f5cc604bc0ff058bc5e5dc6aac87f3a4008b54b6'
- 'SHA256=f5c5e962577e2293c4ad10603816dce7cc273585969615fbf4e4bfa9eaff1688'
- 'SHA256=d14c52d9220b606f428a8fe9f7c108b0d6f14cf71e7384749e98e6a95962e68f'
- 'SHA256=d3a0e1a79158f3985cd49607ebe0cdfcc49cb9af96b8f43aefd0cdfe2f22e663'
- 'SHA256=2fbbfc8299537ff80cadf9d0e27c223fe0ccb9052bf9d8763ad717bbfa521c77'
- 'SHA256=19074674c6fbdaa573b3081745e5e26144fdf7a086d14e0e220d1814f1f13078'
# Note:
# Accounts for the cloudflared binaries being renamed
# `tunnel` is optional, but has been included to reduce the possibility of parameter collision when not observed with known binary names
selection_param:
- CommandLine|contains|all:
- '-url'
- 'tunnel'
- CommandLine|contains:
- '.exe -url'
- '.exe --url'
selection_other:
CommandLine|contains|all:
- '-url'
- '-no-autoupdate'
condition: (selection_img and selection_param) or selection_other
falsepositives:
- Legitimate usage of Cloudflare Quick Tunnel
level: medium
New rules covering some of the tradecraft used by the SVR / Cozy Bear, courtesy of CISA
title: Scheduled Tasks Names Used By SVR For GraphicalProton Backdoor - Task Scheduler
id: 2bfc1373-0220-4fbd-8b10-33ddafd2a142
related:
- id: 8fa65166-f463-4fd2-ad4f-1436133c52e1 # Security-Audting Eventlog
type: similar
status: experimental
description: Hunts for known SVR-specific scheduled task names
author: CISA
references:
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-347a
date: 2023/12/18
tags:
- attack.persistence
logsource:
product: windows
service: taskscheduler
definition: 'Requirements: The "Microsoft-Windows-TaskScheduler/Operational" is disabled by default and needs to be enabled in order for this detection to trigger'
detection:
selection:
EventID:
- 129 # Task Created
- 140 # Task Updated
- 141 # Task Deleted
TaskName:
- '\defender'
- '\Microsoft\DefenderService'
- '\Microsoft\Windows\Application Experience\StartupAppTaskCheck'
- '\Microsoft\Windows\Application Experience\StartupAppTaskCkeck'
- '\Microsoft\Windows\ATPUpd'
- '\Microsoft\Windows\Data Integrity Scan\Data Integrity Update'
- '\Microsoft\Windows\DefenderUPDService'
- '\Microsoft\Windows\IISUpdateService'
- '\Microsoft\Windows\Speech\SpeechModelInstallTask'
- '\Microsoft\Windows\WiMSDFS'
- '\Microsoft\Windows\Windows Defender\Defender Update Service'
- '\Microsoft\Windows\Windows Defender\Service Update'
- '\Microsoft\Windows\Windows Error Reporting\CheckReporting'
- '\Microsoft\Windows\Windows Error Reporting\SubmitReporting'
- '\Microsoft\Windows\Windows Filtering Platform\BfeOnServiceStart'
- '\Microsoft\Windows\WindowsDefenderService'
- '\Microsoft\Windows\WindowsDefenderService2'
- '\Microsoft\Windows\WindowsUpdate\Scheduled AutoCheck'
- '\Microsoft\Windows\WindowsUpdate\Scheduled Check'
- '\WindowUpdate'
condition: selection
falsepositives:
- Unknown
level: high
New mac os rules covering potential information discovery using utilities such as “ioreg” and “sw_vers”.
title: System Information Discovery Using Ioreg
id: 2d5e7a8b-f484-4a24-945d-7f0efd52eab0
status: experimental
description: |
Detects the use of "ioreg" which will show I/O Kit registry information.
This process is used for system information discovery.
It has been observed in-the-wild by calling this process directly or using bash and grep to look for specific strings.
references:
- https://www.virustotal.com/gui/file/0373d78db6c3c0f6f6dcc409821bf89e1ad8c165d6f95c5c80ecdce2219627d7/behavior
- https://www.virustotal.com/gui/file/4ffdc72d1ff1ee8228e31691020fc275afd1baee5a985403a71ca8c7bd36e2e4/behavior
- https://www.virustotal.com/gui/file/5907d59ec1303cfb5c0a0f4aaca3efc0830707d86c732ba6b9e842b5730b95dc/behavior
author: Joseliyo Sanchez, @Joseliyo_Jstnk
date: 2023/12/20
tags:
- attack.discovery
- attack.t1082
logsource:
product: macos
category: process_creation
detection:
# Examples:
# /bin/bash /bin/sh -c ioreg -l | grep -e 'VirtualBox' -e 'Oracle' -e 'VMware' -e 'Parallels' | wc -l
# /usr/sbin/ioreg ioreg -rd1 -w0 -c AppleAHCIDiskDriver
# /bin/bash /bin/sh -c ioreg -l | grep -e 'USB Vendor Name'
selection_img:
- Image|endswith: '/ioreg'
- CommandLine|contains|all:
- 'ioreg'
- '-l'
selection_cmd:
CommandLine|contains:
- 'AppleAHCIDiskDriver'
- 'Oracle'
- 'Parallels'
- 'USB Vendor Name'
- 'VirtualBox'
- 'VMware'
condition: all of selection_*
falsepositives:
- Legitimate administrative activities
level: medium
title: System Information Discovery Using sw_vers
id: 5de06a6f-673a-4fc0-8d48-bcfe3837b033
status: experimental
description: Detects the use of "sw_vers" for system information discovery
references:
- https://www.virustotal.com/gui/file/d3fa64f63563fe958b75238742d1e473800cb5f49f5cb79d38d4aa3c93709026/behavior
- https://www.virustotal.com/gui/file/03b71eaceadea05bc0eea5cddecaa05f245126d6b16cfcd0f3ba0442ac58dab3/behavior
- https://ss64.com/osx/sw_vers.html
author: Joseliyo Sanchez, @Joseliyo_Jstnk
date: 2023/12/20
tags:
- attack.discovery
- attack.t1082
logsource:
product: macos
category: process_creation
detection:
# VT Query: 'behavior_processes:"sw_vers" and (behavior_processes:"-productVersion" or behavior_processes:"-productName" or behavior_processes:"-buildVersion") tag:dmg p:5+'
selection_image:
Image|endswith: '/sw_vers'
selection_options:
CommandLine|contains:
- '-buildVersion'
- '-productName'
- '-productVersion'
condition: all of selection_*
falsepositives:
- Legitimate administrative activities
level: medium
As well as a new version for hunting potential WMIC discovery queries
title: System Information Discovery Via Wmic.EXE
id: d85ecdd7-b855-4e6e-af59-d9c78b5b861e
related:
- id: 9d5a1274-922a-49d0-87f3-8c653483b909
type: derived
status: experimental
description: |
Detects the use of the WMI command-line (WMIC) utility to identify and display various system information,
including OS, CPU, GPU, disk drive names, memory capacity, display resolution, baseboard, BIOS,
and GPU driver products/versions.
references:
- https://github.com/redcanaryco/atomic-red-team/blob/a2ccd19c37d0278b4ffa8583add3cf52060a5418/atomics/T1082/T1082.md#atomic-test-25---system-information-discovery-with-wmic
- https://nwgat.ninja/getting-system-information-with-wmic-on-windows/
- https://blog.sekoia.io/aurora-a-rising-stealer-flying-under-the-radar
- https://blog.cyble.com/2023/01/18/aurora-a-stealer-using-shapeshifting-tactics/
- https://app.any.run/tasks/a6aa0057-82ec-451f-8f99-55650ca537da/
- https://www.virustotal.com/gui/file/d6f6bc10ae0e634ed4301d584f61418cee18e5d58ad9af72f8aa552dc4aaeca3/behavior
author: Joseliyo Sanchez, @Joseliyo_Jstnk
date: 2023/12/19
tags:
- attack.discovery
- attack.t1082
logsource:
category: process_creation
product: windows
detection:
selection_wmic:
- Description: 'WMI Commandline Utility'
- OriginalFileName: 'wmic.exe'
- Image|endswith: '\WMIC.exe'
selection_get:
CommandLine|contains: 'get'
selection_classes:
CommandLine|contains:
- 'baseboard'
- 'bios'
- 'cpu'
- 'diskdrive'
- 'logicaldisk'
- 'memphysical'
- 'os'
- 'path'
- 'startup'
- 'win32_videocontroller'
selection_attributes:
CommandLine|contains:
- 'caption'
- 'command'
- 'driverversion'
- 'maxcapacity'
- 'name'
- 'osarchitecture'
- 'product'
- 'size'
- 'smbiosbiosversion'
- 'version'
- 'videomodedescription'
condition: all of selection_*
falsepositives:
- Unknown
# Note: Might be upgraded to medium after some time
level: low
As well as many others. Please check the full changelog in the release page.
New Updates
Many older rules have seen multiple improvements in coverage and metadata as well. Some examples include:
Enhanced list for uncommon DLL extensions rule
title: Rundll32 Execution With Uncommon DLL Extension
id: c3a99af4-35a9-4668-879e-c09aeb4f2bdf
status: experimental
description: Detects the execution of rundll32 with a command line that doesn't contain a common extension
references:
- https://twitter.com/mrd0x/status/1481630810495139841?s=12
author: Tim Shelton, Florian Roth (Nextron Systems), Yassine Oukessou
date: 2022/01/13
modified: 2023/12/13
tags:
- attack.defense_evasion
- attack.t1218.011
logsource:
category: process_creation
product: windows
detection:
selection:
- Image|endswith: '\rundll32.exe'
- OriginalFileName: 'RUNDLL32.EXE'
filter_main_null:
CommandLine: null
filter_main_empty:
CommandLine: ''
filter_main_known_extension:
CommandLine|contains:
- '.cpl'
- '.dll'
- '.inf'
filter_main_localserver:
CommandLine|contains: ' -localserver '
filter_main_zzzzInvokeManagedCustomActionOutOfProc:
CommandLine|contains|all:
- 'C:\Windows\Installer\MSI'
- '.tmp'
- 'zzzzInvokeManagedCustomActionOutOfProc'
condition: selection and not 1 of filter_main_*
falsepositives:
- Unknown
level: medium
An update to the powershell rule covering potential compression cmdlet usage from temp locations
title: Zip A Folder With PowerShell For Staging In Temp - PowerShell Script
id: b7a3c9a3-09ea-4934-8864-6a32cacd98d9 # PowerShell Script
related:
- id: 71ff406e-b633-4989-96ec-bc49d825a412 # PowerShell Classic
type: similar
- id: daf7eb81-35fd-410d-9d7a-657837e602bb # PowerShell Module
type: similar
- id: 85a8e5ba-bd03-4bfb-bbfa-a4409a8f8b98 # Process Creation
type: similar
status: test
description: |
Detects PowerShell scripts that make use of the "Compress-Archive" Cmdlet in order to compress folders and files where the output is stored in a potentially suspicious location that is used often by malware for exfiltration.
An adversary might compress data (e.g., sensitive documents) that is collected prior to exfiltration in order to make it portable and minimize the amount of data sent over the network.
references:
- https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1074.001/T1074.001.md
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-347a
author: Nasreddine Bencherchali (Nextron Systems), frack113
date: 2021/07/20
modified: 2023/12/18
tags:
- attack.collection
- attack.t1074.001
logsource:
product: windows
category: ps_script
definition: 'Requirements: Script Block Logging must be enabled'
detection:
selection:
ScriptBlockText|contains:
- 'Compress-Archive -Path*-DestinationPath $env:TEMP'
- 'Compress-Archive -Path*-DestinationPath*\AppData\Local\Temp\'
- 'Compress-Archive -Path*-DestinationPath*:\Windows\Temp\'
condition: selection
falsepositives:
- Unknown
level: medium
As well as many update to the level of rules to set expectation according to FP found in the wild. Check out the full changelog for a complete list.
Fixes
This release focused a lot on false positives fixes and tuning of older rules to enhance the quality.
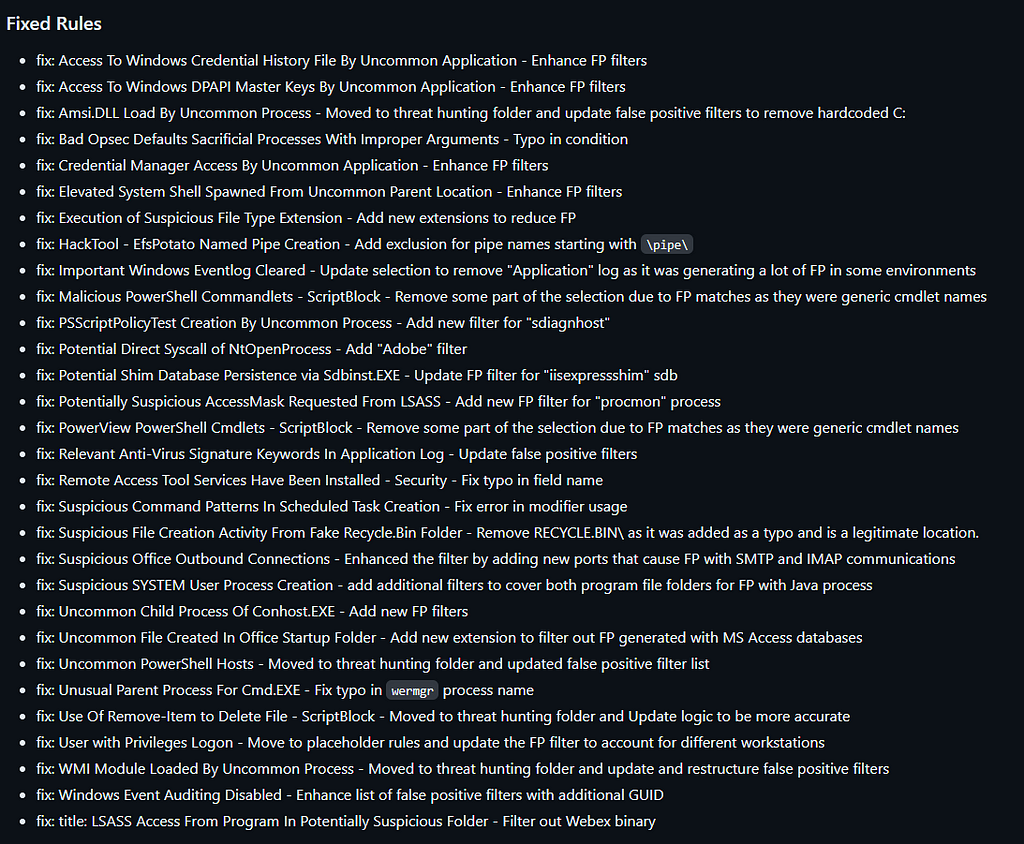
You can check the full changelog on the release page below.
Release Release r2023-12-21 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
- @AaronS97
- @AdmU3
- @Blackmore-Robert
- @celalettin-turgut
- @frack113
- @GtUGtHGtNDtEUaE
- @jstnk9
- @mcdave2k1
- @mostafa
- @nasbench
- @phantinuss
- @qasimqlf
- @ruppde
- @slincoln-aiq
- @ssnkhan
- @swachchhanda000
- @tr0mb1r
- @X-Junior
SigmaHQ Rules Release Highlights — r2023–12–21 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2023–12–21 | by Nasreddine Bencherchali | Dec, 2023 | Sigma_HQ