SigmaHQ Rules Release Highlights — r2023–12–04
 https://github.com/SigmaHQ/sigma/releases/tag/r2023-12-04
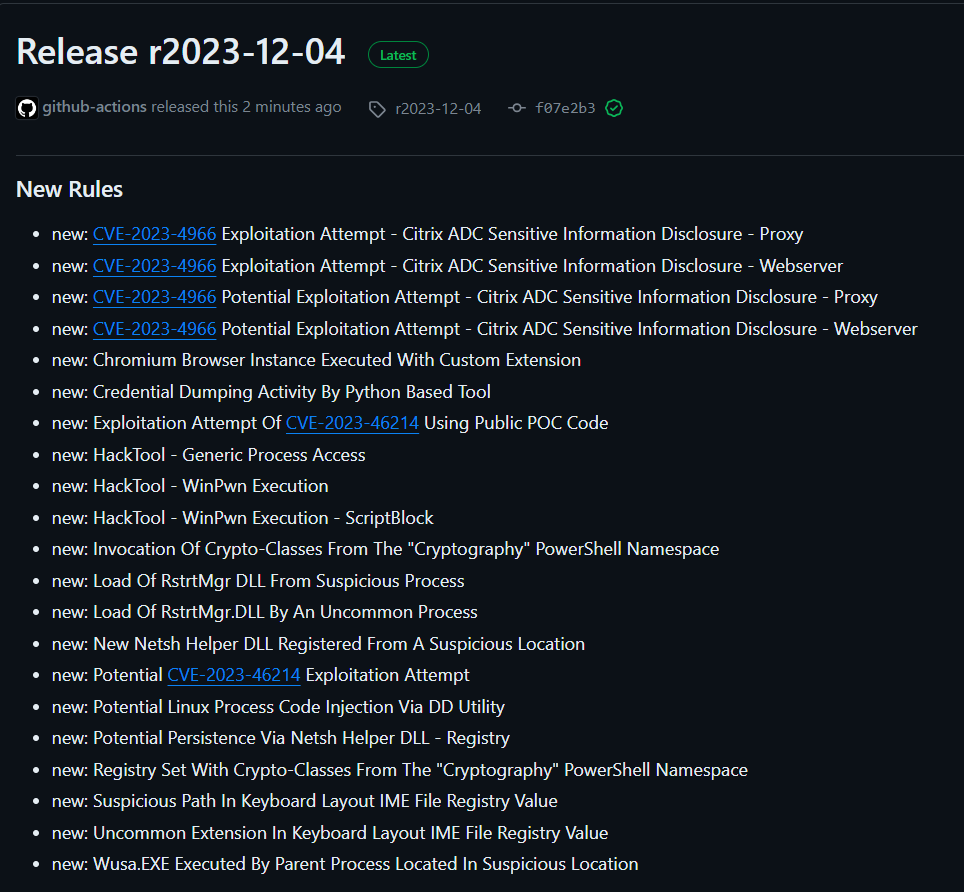
https://github.com/SigmaHQ/sigma/releases/tag/r2023-12-04Sigma Rule Packages for 04–12–2023 are released and available for download. This release saw the addition of 21 new rules, 29 rule updates and 5 rule fixes by 15+ contributors.
New Rules
Some highlights for the newer rules include, a new detection for potential abuse of the “RstrtMgr” DLL by uncommon or suspicious processes
title: Load Of RstrtMgr.DLL By An Uncommon Process
id: 3669afd2-9891-4534-a626-e5cf03810a61
related:
- id: b48492dc-c5ef-4572-8dff-32bc241c15c8
type: derived
status: experimental
description: |
Detects the load of RstrtMgr DLL (Restart Manager) by an uncommon process.
This library has been used during ransomware campaigns to kill processes that would prevent file encryption by locking them (e.g. Conti ransomware, Cactus ransomware). It has also recently been seen used by the BiBi wiper for Windows.
It could also be used for anti-analysis purposes by shut downing specific processes.
references:
- https://www.crowdstrike.com/blog/windows-restart-manager-part-1/
- https://www.crowdstrike.com/blog/windows-restart-manager-part-2/
- https://www.swascan.com/cactus-ransomware-malware-analysis/
- https://taiwan.postsen.com/business/88601/Hamas-hackers-use-data-destruction-software-BiBi-which-consumes-a-lot-of-processor-resources-to-wipe-Windows-computer-data--iThome.html
author: Luc Génaux
date: 2023/11/28
tags:
- attack.impact
- attack.defense_evasion
- attack.t1486
- attack.t1562.001
logsource:
category: image_load
product: windows
detection:
selection:
- ImageLoaded|endswith: '\RstrtMgr.dll'
- OriginalFileName: 'RstrtMgr.dll'
filter_main_generic:
Image|contains:
- ':\$WINDOWS.~BT\'
- ':\$WinREAgent\'
- ':\Program Files (x86)\'
- ':\Program Files\'
- ':\ProgramData\'
- ':\Windows\explorer.exe'
- ':\Windows\SoftwareDistribution\'
- ':\Windows\SysNative\'
- ':\Windows\System32\'
- ':\Windows\SysWOW64\'
- ':\Windows\WinSxS\'
- ':\WUDownloadCache\'
filter_main_user_software_installations:
Image|contains|all:
- ':\Users\'
- '\AppData\Local\Temp\is-'
- '.tmp\'
Image|endswith: '.tmp'
filter_main_admin_software_installations:
Image|contains: ':\Windows\Temp\'
condition: selection and not 1 of filter_main_*
falsepositives:
- Other legitimate Windows processes not currently listed
- Processes related to software installation
level: low
A new detection focusing on the usage of the linux “dd” utility to potentially overwrite the memory map of a process, indicating “Process Injection”.
title: Potential Linux Process Code Injection Via DD Utility
id: 4cad6c64-d6df-42d6-8dae-eb78defdc415
status: experimental
description: Detects the injection of code by overwriting the memory map of a Linux process using the "dd" Linux command.
references:
- https://www.aon.com/cyber-solutions/aon_cyber_labs/linux-based-inter-process-code-injection-without-ptrace2/
- https://github.com/AonCyberLabs/Cexigua/blob/34d338620afae4c6335ba8d8d499e1d7d3d5d7b5/overwrite.sh
author: Joseph Kamau
date: 2023/12/01
tags:
- attack.defense_evasion
- attack.t1055.009
logsource:
product: linux
category: process_creation
detection:
selection:
Image|endswith: '/dd'
CommandLine|contains|all:
- 'of='
- '/proc/'
- '/mem'
condition: selection
falsepositives:
- Unknown
level: medium
Another new detection focusing on potential DLL sideloading via IME registry key.
title: Suspicious Path In Keyboard Layout IME File Registry Value
id: 9d8f9bb8-01af-4e15-a3a2-349071530530
related:
- id: b888e3f2-224d-4435-b00b-9dd66e9ea1f1
type: derived
status: experimental
description: |
Detects usage of Windows Input Method Editor (IME) keyboard layout feature, which allows an attacker to load a DLL into the process after sending the WM_INPUTLANGCHANGEREQUEST message.
Before doing this, the client needs to register the DLL in a special registry key that is assumed to implement this keyboard layout. This registry key should store a value named "Ime File" with a DLL path.
IMEs are essential for languages that have more characters than can be represented on a standard keyboard, such as Chinese, Japanese, and Korean.
references:
- https://www.linkedin.com/pulse/guntior-story-advanced-bootkit-doesnt-rely-windows-disk-baranov-wue8e/
author: X__Junior (Nextron Systems)
date: 2023/11/21
tags:
- attack.defense_evasion
- attack.t1562.001
logsource:
product: windows
category: registry_set
detection:
selection_registry:
TargetObject|contains|all:
- '\Control\Keyboard Layouts\'
- 'Ime File'
selection_folders_1:
Details|contains:
- ':\Perflogs\'
- ':\Users\Public\'
- ':\Windows\Temp\'
- '\AppData\Local\Temp\'
- '\AppData\Roaming\'
- '\Temporary Internet'
selection_folders_2:
- Details|contains|all:
- ':\Users\'
- '\Favorites\'
- Details|contains|all:
- ':\Users\'
- '\Favourites\'
- Details|contains|all:
- ':\Users\'
- '\Contacts\'
condition: selection_registry and 1 of selection_folders_*
falsepositives:
- Unknown
level: high
As well as many others. Please check the full changelog in the release page.
New Updates
Many older rules have seen multiple improvements in coverage and metadata as well. Some examples include:
Rename, metadata and logic enhancements to all rules leveraging the process_access log source. Including a reduced level for many to set FP expectations correctly.
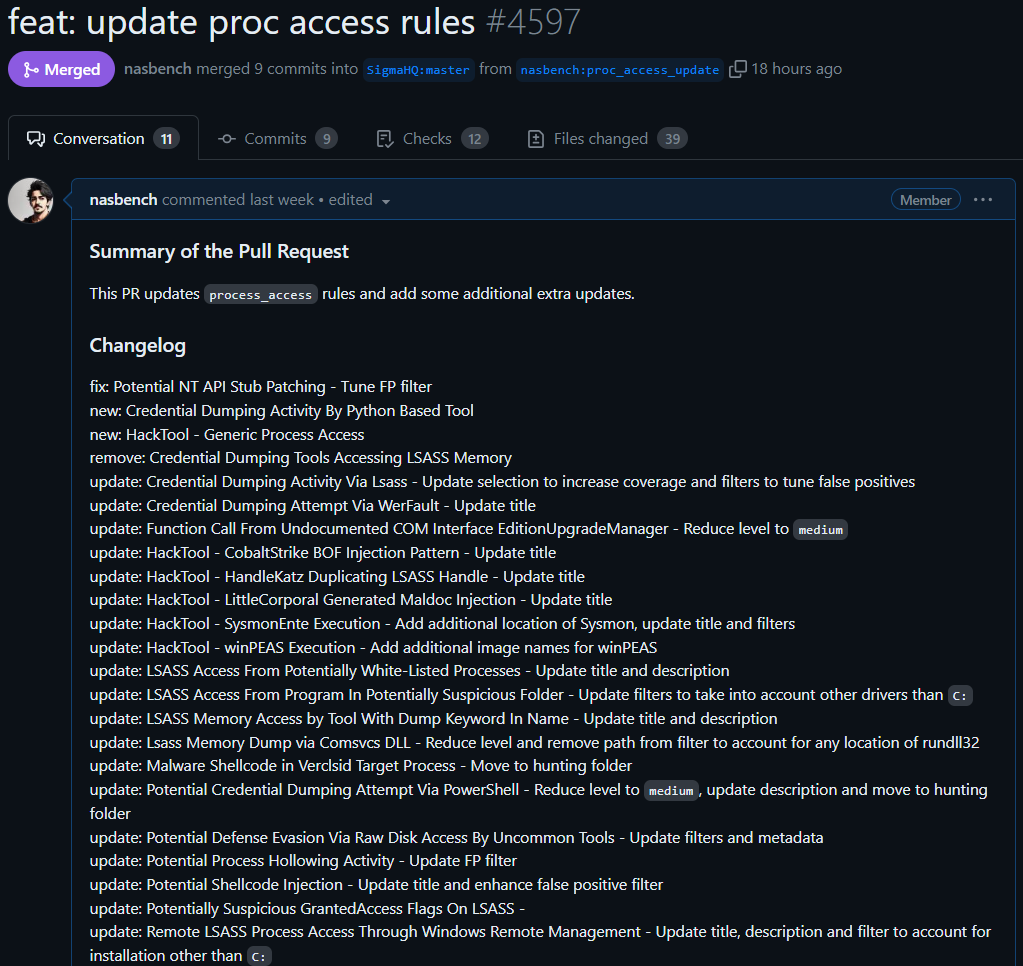 https://github.com/SigmaHQ/sigma/pull/4597
https://github.com/SigmaHQ/sigma/pull/4597Increase coverage for the rule focusing on COR CLR profiler persistence technique.
title: Enabling COR Profiler Environment Variables
id: ad89044a-8f49-4673-9a55-cbd88a1b374f
status: test
description: Detects .NET Framework CLR and .NET Core CLR "cor_enable_profiling" and "cor_profiler" variables being set and configured.
references:
- https://twitter.com/jamieantisocial/status/1304520651248668673
- https://www.slideshare.net/JamieWilliams130/started-from-the-bottom-exploiting-data-sources-to-uncover-attck-behaviors
- https://www.sans.org/cyber-security-summit/archives
- https://learn.microsoft.com/en-us/dotnet/core/runtime-config/debugging-profiling
author: Jose Rodriguez (@Cyb3rPandaH), OTR (Open Threat Research), Jimmy Bayne (@bohops)
date: 2020/09/10
modified: 2023/11/24
tags:
- attack.persistence
- attack.privilege_escalation
- attack.defense_evasion
- attack.t1574.012
logsource:
category: registry_set
product: windows
detection:
selection_1:
TargetObject|endswith:
- '\COR_ENABLE_PROFILING'
- '\COR_PROFILER'
- '\CORECLR_ENABLE_PROFILING'
selection_2:
TargetObject|contains: '\CORECLR_PROFILER_PATH'
condition: 1 of selection_*
level: medium
Increase coverage for rule looking for IP lookup service requests by adding
- db-ip.com
- api.bigdatacloud.net
- ipapi.co
title: Suspicious DNS Query for IP Lookup Service APIs
id: ec82e2a5-81ea-4211-a1f8-37a0286df2c2
status: test
description: Detects DNS queries for IP lookup services such as "api.ipify.org" originating from a non browser process.
references:
- https://www.binarydefense.com/analysis-of-hancitor-when-boring-begets-beacon
- https://twitter.com/neonprimetime/status/1436376497980428318
- https://www.trendmicro.com/en_us/research/23/e/managed-xdr-investigation-of-ducktail-in-trend-micro-vision-one.html
author: Brandon George (blog post), Thomas Patzke
date: 2021/07/08
modified: 2023/11/29
tags:
- attack.reconnaissance
- attack.t1590
logsource:
product: windows
category: dns_query
detection:
selection:
QueryName|contains:
- 'api.2ip.ua'
- 'api.bigdatacloud.net'
- 'api.ipify.org'
- 'bot.whatismyipaddress.com'
- 'canireachthe.net'
- 'checkip.amazonaws.com'
- 'checkip.dyndns.org'
- 'curlmyip.com'
- 'db-ip.com'
- 'edns.ip-api.com'
- 'eth0.me'
- 'freegeoip.app'
- 'geoipy.com'
- 'getip.pro'
- 'icanhazip.com'
- 'ident.me'
- 'ifconfig.io'
- 'ifconfig.me'
- 'ipapi.co'
- 'ip-api.com'
- 'ip.anysrc.net'
- 'ip.tyk.nu'
- 'ipaddressworld.com'
- 'ipecho.net'
- 'ipinfo.io'
- 'ipof.in'
- 'ipv4.icanhazip.com'
- 'ipv4bot.whatismyipaddress.com'
- 'ipwho.is'
- 'l2.io'
- 'myexternalip.com'
- 'wgetip.com'
- 'whatismyip.akamai.com'
- 'wtfismyip.com'
filter_optional_brave:
Image|endswith: '\brave.exe'
filter_optional_chrome:
Image:
- 'C:\Program Files\Google\Chrome\Application\chrome.exe'
- 'C:\Program Files (x86)\Google\Chrome\Application\chrome.exe'
filter_optional_firefox:
Image:
- 'C:\Program Files\Mozilla Firefox\firefox.exe'
- 'C:\Program Files (x86)\Mozilla Firefox\firefox.exe'
filter_optional_ie:
Image:
- 'C:\Program Files (x86)\Internet Explorer\iexplore.exe'
- 'C:\Program Files\Internet Explorer\iexplore.exe'
filter_optional_maxthon:
Image|endswith: '\maxthon.exe'
filter_optional_edge_1:
- Image|startswith: 'C:\Program Files (x86)\Microsoft\EdgeWebView\Application\'
- Image|endswith: '\WindowsApps\MicrosoftEdge.exe'
- Image:
- 'C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe'
- 'C:\Program Files\Microsoft\Edge\Application\msedge.exe'
filter_optional_edge_2:
Image|startswith:
- 'C:\Program Files (x86)\Microsoft\EdgeCore\'
- 'C:\Program Files\Microsoft\EdgeCore\'
Image|endswith:
- '\msedge.exe'
- '\msedgewebview2.exe'
filter_optional_opera:
Image|endswith: '\opera.exe'
filter_optional_safari:
Image|endswith: '\safari.exe'
filter_optional_seamonkey:
Image|endswith: '\seamonkey.exe'
filter_optional_vivaldi:
Image|endswith: '\vivaldi.exe'
filter_optional_whale:
Image|endswith: '\whale.exe'
condition: selection and not 1 of filter_optional_*
falsepositives:
- Legitimate usage of IP lookup services such as ipify API
level: medium
Fixes
This release also saw a couple of false positives fixes and tuning of some rules, check out the main repo for the full list.
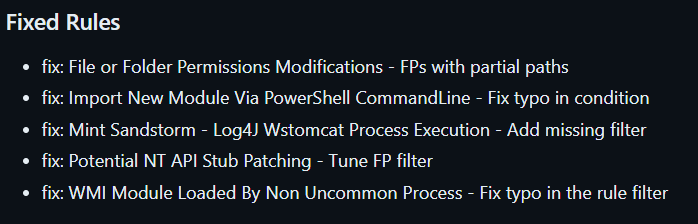
You can check the full changelog on the release page below.
Release Release r2023-12-04 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
- @0x616c6578
- @AaronHoffmannRL
- @bohops
- @EzLucky
- @frack113
- @himynamesdave
- @joshnck
- @nasbench
- @netgrain
- @phantinuss
- @qasimqlf
- @skaynum
- @StevenD33
- @swachchhanda000
- @ts-lbf
- @X-Junior
SigmaHQ Rules Release Highlights — r2023–12–04 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2023–12–04 | by Nasreddine Bencherchali | Dec, 2023 | Sigma_HQ