SigmaHQ Rules Release Highlights — r2023–11–20
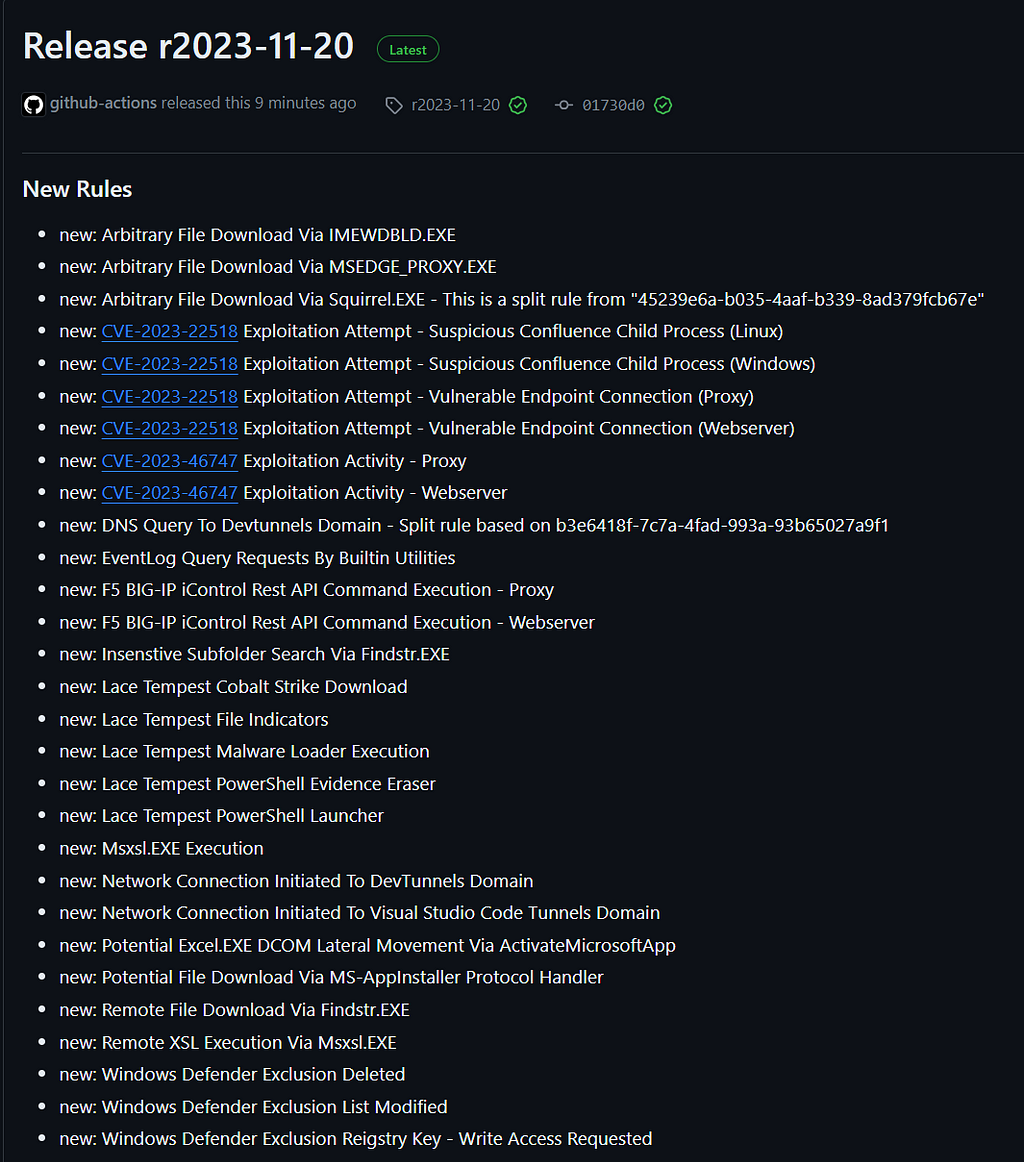 https://github.com/SigmaHQ/sigma/releases/tag/r2023-11-20
https://github.com/SigmaHQ/sigma/releases/tag/r2023-11-20Sigma Rule Packages for 20–11–2023 are released and available for download. This release saw the addition of 29 new rules, 44 rule updates and 11 rule fixes by 21+ contributors.
New Rules
Some highlights for the newer rules include, emerging threat detections for CVE-2023–22518 and CVE-2023–46747 exploitation attempts.
title: CVE-2023-22518 Exploitation Attempt - Suspicious Confluence Child Process (Windows)
id: 1ddaa9a4-eb0b-4398-a9fe-7b018f9e23db
related:
- id: f8987c03-4290-4c96-870f-55e75ee377f4
type: similar
status: experimental
description: |
Detects exploitation attempt of CVE-2023-22518 (Confluence Data Center / Confluence Server), where an attacker can exploit vulnerable endpoints to e.g. create admin accounts and execute arbitrary commands.
references:
- https://confluence.atlassian.com/security/cve-2023-22518-improper-authorization-vulnerability-in-confluence-data-center-and-server-1311473907.html
- https://www.huntress.com/blog/confluence-to-cerber-exploitation-of-cve-2023-22518-for-ransomware-deployment
- https://github.com/ForceFledgling/CVE-2023-22518
author: Andreas Braathen (mnemonic.io)
date: 2023/11/14
tags:
- detection.emerging_threats
- attack.execution
- attack.t1059
- attack.initial_access
- attack.t1190
- cve.2023.22518
logsource:
category: process_creation
product: windows
detection:
selection_parent:
ParentImage|endswith:
- '\tomcat8.exe'
- '\tomcat9.exe'
- '\tomcat10.exe'
ParentCommandLine|contains: 'confluence'
selection_child:
# Note: Only children associated with known campaigns
- Image|endswith:
- '\cmd.exe'
- '\powershell.exe'
- OriginalFileName:
- 'Cmd.Exe'
- 'PowerShell.EXE'
condition: all of selection_*
falsepositives:
- Unknown
level: medium
title: CVE-2023-46747 Exploitation Activity - Webserver
id: e9928831-ba14-42ea-a4bc-33d352b9929a
related:
- id: f195b2ff-e542-41bf-8d91-864fb81e5c20
type: similar
status: experimental
description: Detects exploitation activity of CVE-2023-46747 an unauthenticated remote code execution vulnerability in F5 BIG-IP.
references:
- https://github.com/AliBrTab/CVE-2023-46747-POC/tree/main
- https://github.com/0xorOne/nuclei-templates/blob/2fef4270ec6e5573d0a1732cb18bcfc4b1580a88/http/cves/2023/CVE-2023-46747.yaml
- https://mp.weixin.qq.com/s/wUoBy7ZiqJL2CUOMC-8Wdg
- https://www.praetorian.com/blog/refresh-compromising-f5-big-ip-with-request-smuggling-cve-2023-46747/
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/11/08
tags:
- attack.initial_access
- attack.t1190
- detection.emerging_threats
- cve.2023.46747
logsource:
category: webserver
definition: 'Requirements: The POST request body data must be collected in order to make use of this detection'
detection:
selection:
cs-method: 'POST'
cs-uri-stem|contains: '/mgmt/tm/util/bash'
keywords_hex:
'|all':
- '2f746d75692f436f6e74726f6c2f666f726d' # /tmui/Control/form
- '666f726d5f706167653d253266746d756925326673797374656d253266757365722532666372656174652e6a7370' # form_page=%2ftmui%2fsystem%2fuser%2fcreate.jsp
keywords_plain:
'|all':
- '/tmui/Control/form'
- 'form_page=%2ftmui%2fsystem%2fuser%2fcreate.jsp'
condition: selection and (keywords_hex or keywords_plain)
falsepositives:
- Unlikely
level: high
New detection for the threat actor Lace Tempest and their exploitation of the SysAid vulnerability.
title: Lace Tempest PowerShell Evidence Eraser
id: b377ddab-502d-4519-9e8c-5590033d2d70
status: experimental
description: |
Detects a PowerShell script used by Lace Tempest APT to erase evidence from victim servers by exploiting CVE-2023-47246 as reported by SysAid Team
references:
- https://www.sysaid.com/blog/service-desk/on-premise-software-security-vulnerability-notification
author: Nasreddine Bencherchali (Nextron Systems)
date: 2023/11/09
tags:
- attack.execution
- attack.t1059.001
- detection.emerging_threats
logsource:
product: windows
category: ps_script
definition: 'Requirements: Script Block Logging must be enabled'
detection:
selection:
ScriptBlockText|contains|all:
- 'cleanLL'
- 'usersfiles.war'
- 'Remove-Item -Path "$tomcat_dir'
- 'SysAidServer'
- 'sleep '
- 'while(1)'
condition: selection
falsepositives:
- Unlikely
level: high
We’ve also included new detection for the IMEWDBLDand MSEDGE_PROXY LOLBins being used for arbitrary download.
title: Arbitrary File Download Via IMEWDBLD.EXE
id: 863218bd-c7d0-4c52-80cd-0a96c09f54af
related:
- id: 8d7e392e-9b28-49e1-831d-5949c6281228
type: derived
status: experimental
description: Detects usage of "IMEWDBLD.exe" to download arbitrary files
references:
- https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1105/T1105.md#atomic-test-10---windows---powershell-download
- https://lolbas-project.github.io/lolbas/Binaries/IMEWDBLD/
author: Swachchhanda Shrawan Poudel
date: 2023/11/09
tags:
- attack.defense_evasion
- attack.execution
- attack.t1218
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\IMEWDBLD.exe'
- OriginalFileName: 'imewdbld.exe'
selection_cli:
CommandLine|contains:
- 'http://'
- 'https://'
condition: all of selection_*
falsepositives:
- Unknown
# Note: Please reduce this to medium if you find legitimate use case of this utility with a URL
level: high
As well as many others. Please check the full changelog in the release page.
New Updates
Many older rules have seen multiple improvements in coverage and metadata as well. Some examples include:
Increased coverage for all rules that are based on usage of the findstr utility to include find.exe as well. As was seen used by threats in the wild.
title: Security Tools Keyword Lookup Via Findstr.EXE
id: 4fe074b4-b833-4081-8f24-7dcfeca72b42
related:
- id: fe63010f-8823-4864-a96b-a7b4a0f7b929
type: derived
status: experimental
description: |
Detects execution of "findstr" to search for common names of security tools. Attackers often pipe the results of recon commands such as "tasklist" or "whoami" to "findstr" in order to filter out the results.
This detection focuses on the keywords that the attacker might use as a filter.
references:
- https://github.com/redcanaryco/atomic-red-team/blob/987e3ca988ae3cff4b9f6e388c139c05bf44bbb8/atomics/T1518.001/T1518.001.md#atomic-test-1---security-software-discovery
- https://www.microsoft.com/en-us/security/blog/2023/10/18/multiple-north-korean-threat-actors-exploiting-the-teamcity-cve-2023-42793-vulnerability/
- https://www.hhs.gov/sites/default/files/manage-engine-vulnerability-sector-alert-tlpclear.pdf
author: Nasreddine Bencherchali (Nextron Systems), frack113
date: 2023/10/20
modified: 2023/11/14
tags:
- attack.discovery
- attack.t1518.001
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith:
- '\find.exe'
- '\findstr.exe'
- OriginalFileName:
- 'FIND.EXE'
- 'FINDSTR.EXE'
selection_cli:
CommandLine|endswith:
# Note: Add additional keywords to increase and enhance coverage
# Note:
# We use the double quote variation because in cases of where the command is executed through cmd for example:
# cmd /c "tasklist | findstr virus"
# Logging utilties such as Sysmon would capture the end quote as part of findstr execution
- ' avira'
- ' avira"'
- ' cb'
- ' cb"'
- ' cylance'
- ' cylance"'
- ' defender'
- ' defender"'
- ' kaspersky'
- ' kaspersky"'
- ' kes'
- ' kes"'
- ' mc'
- ' mc"'
- ' sec'
- ' sec"'
- ' sentinel'
- ' sentinel"'
- ' symantec'
- ' symantec"'
- ' virus'
- ' virus"'
condition: all of selection_*
falsepositives:
- Unknown
level: medium
Enhanced logic of AD user enumeration rule to focus on access masks with “Read” properties only.
title: Potential AD User Enumeration From Non-Machine Account
id: ab6bffca-beff-4baa-af11-6733f296d57a
status: test
description: Detects read access to a domain user from a non-machine account
references:
- https://www.specterops.io/assets/resources/an_ace_up_the_sleeve.pdf
- http://www.stuffithoughtiknew.com/2019/02/detecting-bloodhound.html
- https://docs.microsoft.com/en-us/windows/win32/adschema/attributes-all # For further investigation of the accessed properties
- https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4662
author: Maxime Thiebaut (@0xThiebaut)
date: 2020/03/30
modified: 2022/11/08
tags:
- attack.discovery
- attack.t1087.002
logsource:
product: windows
service: security
definition: 'Requirements: The "Read all properties" permission on the user object needs to be audited for the "Everyone" principal'
detection:
selection:
EventID: 4662
# Using contains as the data commonly is structured as "%{bf967aba-0de6-11d0-a285-00aa003049e2}"
# The user class (https://docs.microsoft.com/en-us/windows/win32/adschema/c-user)
ObjectType|contains: 'bf967aba-0de6-11d0-a285-00aa003049e2'
AccessMask|endswith:
# Note: Since the Access Mask can have more than once permission we need to add all permutations that include the READ property
- '1?' # This covers all access masks that are 1 bytes or shorter and the "Read Property" itself
- '3?' # Read Property + Write Property
- '4?' # Read Property + Delete Tree
- '7?' # Read Property + Write Property + Delete Tree
- '9?' # Read Property + List Object
- 'B?' # Read Property + Write Property + List Object
- 'D?' # Read Property + Delete Tree + List Object
- 'F?' # Covers usage of all possible 2 bytes permissions with any or none of the single byte permissions
filter_main_machine_accounts:
SubjectUserName|endswith: '$' # Exclude machine accounts
filter_main_msql:
SubjectUserName|startswith: 'MSOL_' # https://docs.microsoft.com/en-us/azure/active-directory/hybrid/reference-connect-accounts-permissions#ad-ds-connector-account
condition: selection and not 1 of filter_main_*
falsepositives:
- Administrators configuring new users.
level: medium
Increased coverage for double extension rule by adding more extensions.
title: Suspicious Appended Extension
id: e3f673b3-65d1-4d80-9146-466f8b63fa99
status: experimental
description: Detects file renames where the target filename uses an uncommon double extension. Could indicate potential ransomware activity renaming files and adding a custom extension to the encrypted files, such as ".jpg.crypted", ".docx.locky", etc.
references:
- https://app.any.run/tasks/d66ead5a-faf4-4437-93aa-65785afaf9e5/
- https://blog.cyble.com/2022/08/10/onyx-ransomware-renames-its-leak-site-to-vsop/
author: frack113
date: 2022/07/16
modified: 2023/01/02
tags:
- attack.impact
- attack.t1486
logsource:
product: windows
category: file_rename
definition: 'Requirements: Microsoft-Windows-Kernel-File Provider with at least the KERNEL_FILE_KEYWORD_RENAME_SETLINK_PATH keyword'
detection:
selection:
SourceFilename|endswith:
- '.lnk'
- '.rtf'
- '.pst'
- '.docx'
- '.xlsx'
- '.jpg'
- '.jpeg'
- '.png'
- '.pdf'
TargetFilename|contains:
- '.lnk.'
- '.rtf.'
- '.pst.'
- '.docx.'
- '.xlsx.'
- '.jpg.'
- '.jpeg.'
- '.png.'
- '.pdf.'
filter_main_generic:
TargetFilename|endswith:
- '.tmp'
- '.bak'
- '.old'
- '.orig'
- '.backup'
- '.temp'
filter_optional_anaconda:
TargetFilename|startswith: 'C:\ProgramData\Anaconda3\'
TargetFilename|endswith: '.c~'
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
- Backup software
level: medium
Fixes
This release also saw a couple of false positives fixes and tuning of some rules. Such as new filters for Citrix and their logon Script they used in icast
title: Uncommon Userinit Child Process
id: 0a98a10c-685d-4ab0-bddc-b6bdd1d48458
related:
- id: 21d856f9-9281-4ded-9377-51a1a6e2a432
type: similar
status: test
description: Detects uncommon "userinit.exe" child processes, which could be a sign of uncommon shells or login scripts used for persistence.
references:
- https://cocomelonc.github.io/persistence/2022/12/09/malware-pers-20.html
- https://learn.microsoft.com/en-us/windows-server/administration/server-core/server-core-sconfig#powershell-is-the-default-shell-on-server-core
author: Tom Ueltschi (@c_APT_ure), Tim Shelton
date: 2019/01/12
modified: 2023/11/14
tags:
- attack.t1037.001
- attack.persistence
logsource:
category: process_creation
product: windows
detection:
selection:
ParentImage|endswith: '\userinit.exe'
filter_main_explorer:
Image|endswith: ':\WINDOWS\explorer.exe'
filter_optional_logonscripts:
CommandLine|contains:
- 'netlogon.bat'
- 'UsrLogon.cmd'
filter_optional_windows_core:
# Note: This filter is mandatory on Windows Core machines as the default shell spawned by "userinit" is "powershell.exe".
# https://learn.microsoft.com/en-us/windows-server/administration/server-core/server-core-sconfig#powershell-is-the-default-shell-on-server-core
CommandLine: 'PowerShell.exe'
filter_optional_proquota:
Image|endswith:
- ':\Windows\System32\proquota.exe'
- ':\Windows\SysWOW64\proquota.exe'
filter_optional_citrix:
Image|endswith:
# As reported by https://github.com/SigmaHQ/sigma/issues/4569
- ':\Program Files (x86)\Citrix\HDX\bin\cmstart.exe' # https://support.citrix.com/article/CTX983798/purpose-of-cmstart-command
- ':\Program Files (x86)\Citrix\HDX\bin\icast.exe' # https://support.citrix.com/article/CTX983798/purpose-of-cmstart-command
- ':\Program Files (x86)\Citrix\System32\icast.exe'
- ':\Program Files\Citrix\HDX\bin\cmstart.exe' # https://support.citrix.com/article/CTX983798/purpose-of-cmstart-command
- ':\Program Files\Citrix\HDX\bin\icast.exe' # https://support.citrix.com/article/CTX983798/purpose-of-cmstart-command
- ':\Program Files\Citrix\System32\icast.exe'
filter_optional_image_null:
Image: null
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
- Legitimate logon scripts or custom shells may trigger false positives. Apply additional filters accordingly.
level: high
Added another default location for GnuPG
title: Portable Gpg.EXE Execution
id: 77df53a5-1d78-4f32-bc5a-0e7465bd8f41
status: experimental
description: Detects the execution of "gpg.exe" from uncommon location. Often used by ransomware and loaders to decrypt/encrypt data.
references:
- https://www.trendmicro.com/vinfo/vn/threat-encyclopedia/malware/ransom.bat.zarlock.a
- https://securelist.com/locked-out/68960/
- https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1486/T1486.md
author: frack113, Nasreddine Bencherchali (Nextron Systems)
date: 2023/08/06
modified: 2023/11/10
tags:
- attack.impact
- attack.t1486
logsource:
category: process_creation
product: windows
detection:
selection:
- Image|endswith:
- '\gpg.exe'
- '\gpg2.exe'
- OriginalFileName: 'gpg.exe'
- Description: 'GnuPG’s OpenPGP tool'
filter_main_legit_location:
Image|contains:
- ':\Program Files (x86)\GNU\GnuPG\bin\'
- ':\Program Files (x86)\GnuPG VS-Desktop\'
- ':\Program Files (x86)\GnuPG\bin\'
- ':\Program Files (x86)\Gpg4win\bin\'
condition: selection and not 1 of filter_main_*
level: medium
New location added to the rule Files With System Process Name In Unsuspected Locations that covers Windows recovery folder $WinReAgent and other folders that enhance tuning of the rule.
filter_main_setuphost:
TargetFilename|contains: ':\$WINDOWS.~BT\'
Image|endswith: ':\$WINDOWS.~BT\Sources\SetupHost.exe'
filter_main_wbengine:
TargetFilename|endswith: '\RuntimeBroker.exe'
Image|endswith: ':\Windows\system32\wbengine.exe'
filter_main_svchost:
Image|endswith: ':\Windows\system32\svchost.exe'
TargetFilename|contains:
- ':\Windows\SoftwareDistribution\Download\'
- ':\Program Files\WindowsApps\'
filter_main_wuauclt:
Image|endswith: ':\Windows\System32\wuauclt.exe'
filter_main_explorer:
TargetFilename|endswith: ':\Windows\explorer.exe'
filter_main_msiexec:
# This filter handles system processes who are updated/installed using misexec.
Image|endswith: ':\WINDOWS\system32\msiexec.exe'
# Add more processes if you find them or simply filter msiexec on its own. If the list grows big
TargetFilename|endswith:
- ':\Program Files\PowerShell\7\pwsh.exe'
- ':\Program Files\PowerShell\7-preview\pwsh.exe'
filter_main_healtray:
TargetFilename|contains: ':\Windows\System32\SecurityHealth\'
TargetFilename|endswith: '\SecurityHealthSystray.exe'
Image|endswith: '\SecurityHealthSetup.exe'
filter_main_wuaucltcore:
Image|contains: ':\Windows\uus\'
Image|endswith: '\wuaucltcore.exe'
TargetFilename|contains: ':\$WinREAgent\'
You can check the full changelog on the release page below.
Release Release r2023-11-20 · SigmaHQ/sigma
Contributors
This release was possible thanks to the many Sigma community contributors. A big thanks goes to following people:
- @AaronS97
- @alwashali
- @celalettin-turgut
- @CrimpSec
- @deFr0ggy
- @frack113
- @fukusuket
- @longmdx
- @lsoumille
- @mezzofix
- @michaelpeacock
- @mtnmunuklu
- @nasbench
- @Neo23x0
- @netgrain
- @phantinuss
- @qasimqlf
- @rkmbaxed
- @swachchhanda000
- @ThureinOo
- @vj-codes
- @YamatoSecurity
SigmaHQ Rules Release Highlights — r2023–11–20 was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: SigmaHQ Rules Release Highlights — r2023–11–20 | by Nasreddine Bencherchali | Nov, 2023 | Sigma_HQ