The ASEC analysis team recently discovered that a Linux malware developed with Shc has been installing a CoinMiner. It is presumed that after successful authentication through a dictionary attack on inadequately managed Linux SSH servers, various malware were installed on the target system. Among those installed were the Shc downloader, XMRig CoinMiner installed through the former, and DDoS IRC Bot, developed with Perl.
1. Shc (Shell Script Compiler)
Shc is an abbreviation for Shell Script Compiler and is responsible for converting Bash shell scripts into an ELF (Executable and Linkable Format).
 Figure 1. Overview of General Shell Script Compiler
Figure 1. Overview of General Shell Script CompilerBash is a basic shell offered in the Linux operating system, and commands supported by the Bash shell can be compiled in script format. This means that the commands to be executed by users can be written as scripts, and because of this, syntaxes such as conditional and looping statements are provided. The Bash shell can be compared to the Command Prompt in Windows, with the Bash shell script files corresponding to Windows batch scripts.
Additionally, just like how Linux has Shc that converts Bash shell scripts into executable ELF file formats, Windows has the bat2exe utility that converts batch scripts into executable EXE file formats. In Windows environments, threat actors use bat2exe to convert malicious batch scripts to executables before distributing them in order to bypass file detection of security software such as anti-malware products. It is likely that the reason threat actors do not distribute the bash shell scripts as is but rather convert them to ELF before distributing them is to evade file detection as they do in Windows environments.
The Shc data section contains the original Bash shell script encoded with the Alleged RC4 algorithm. When it is executed afterward, the same ARC4 algorithm is used to decode the original script, and the decoded script commands are executed.
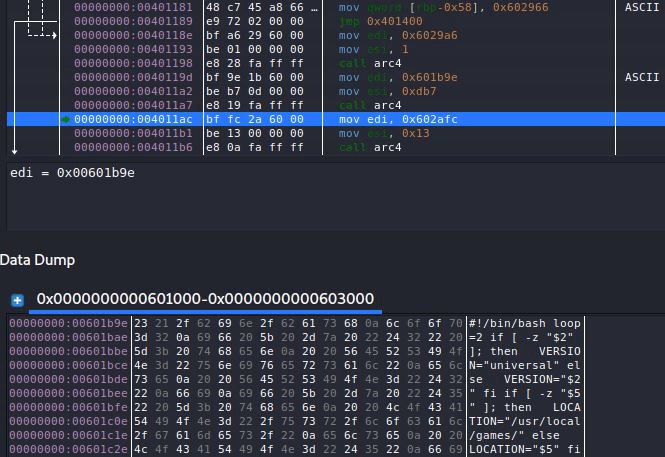 Figure 2. Decoding routine using the ARC4 algorithm
Figure 2. Decoding routine using the ARC4 algorithm
2. Shc Downloader
The following is a decoded Bash shell script of Shc malware reported by a client company that suffered an infiltration attack. It downloads and runs files from external sources, and based on the fact that XMRig CoinMiner is downloaded and installed from the currently available address, it is assumed to be a CoinMiner downloader..
 Figure 3. A portion of the decoded Bash shell script’s routine
Figure 3. A portion of the decoded Bash shell script’s routineAdditionally, this malware has the characteristic of infecting systems alongside DDoS IRC Bot malware developed with Perl, and this point will be discussed in more detail further on. These DDoS IRC Bots have been continuously installed during the past years on Linux servers with inappropriate account information and still continued to this day. The threat actors attempt dictionary attacks on SSH servers after a scanning process, and if this process is successful, various malware such as Perl IRC Bot is installed on the target system. Other malware include XMRig, SSH Scanner and various IRC Bot malware.
Analysis of the reported malware revealed that a “run” file for execution didn’t exist and instead required multiple arguments, which limits our analysis with this sample only.
| Argument # | Feature |
|---|---|
| 1 | The download URL and the name of the file to be downloaded |
| 2 | Version (The “universal” string by default) |
| 3 | The name of the PID file to be created |
| 4 | The Socks5 host name |
| 5 | The path where the installation process will occur (“/Usr/local/games/” by default) |
| 6 | Additional download URLs |
| 7 | Additional commands |
While the ASEC analysis team was tracking related malware, the team found a similar form of Shc Downloader Malware uploaded on VirusTotal. Assuming that such types of malware were all uploaded to VirusTotal from Korea, it seems that attacks generally target systems in Korea.
The malware found on VirusTotal has a much simpler structure in comparison to the type covered above, requiring no additional arguments and having a complete URL as the download address.
 Figure 4. Bash shell script extracted from the similar file
Figure 4. Bash shell script extracted from the similar file
3. XMRig CoinMiner
The Shc downloader malware is responsible for downloading a compressed file from an external source to the path, “/usr/local/games/” and executing the “run” file. The compressed file currently available for download includes not only the XMRig CoinMiner malware but also a config.json with the mining pool URL and the “run” script.
 Figure 5. Downloaded compressed file
Figure 5. Downloaded compressed file Figure 6. config.json file
Figure 6. config.json fileAs the config.json file containing the configuration data exists in the same path, the configuration does not need to be transmitted when XMRig is executed. However, examining the “run” script shown below reveals that it transmits slightly different configuration data to config.json before executing XMRig.
 Figure 7. The “run” script that executes XMRig
Figure 7. The “run” script that executes XMRig
4. DDoS IRC Bot
Aside from installing a CoinMiner on the infected system, the threat actor installs an IRC bot that can perform a DDoS attack by receiving commands. This DDoS IRC Bot has the characteristic of being developed with Perl, and as the name suggests, it uses the IRC protocol in communications with the C&C server.
Both malware strains are similar in form, and while one of them currently cannot connect to the C&C server (IRC server), the other can. Even if a connection can be established, entering the channel is unavailable, and this is presumed to be because the password has been changed from “ddosit” to another value. Additionally, a URL is included in the message that is displayed after channel entry is denied. A compressed file can be downloaded from this URL, and this file contains XMRig from above.
 Figure 8. The process of connecting to the IRC server and attempting to enter the channel
Figure 8. The process of connecting to the IRC server and attempting to enter the channelNext is the configuration data which includes the IRC server address, port number, “#xmr” (IRC channel name to enter), and the password “@” required for entry into the channel. For reference, DDoS IRC Bot performs additional tasks to verify the threat actor; the username of the user that entered the channel must be one of the four usernames shown below and the host address must be “qwerty”.
 Figure 9. Configuration data of DDoS Perl IRC Bot
Figure 9. Configuration data of DDoS Perl IRC BotIf the above conditions are met, it deems the user to be the threat actor and performs the received commands. This bot supports not only DDoS attacks such as TCP Flood, UDP Flood, and HTTP Flood but various other features including command execution, reverse shell, port scanning, and log deletion. The following is a screenshot taken not by the actual threat actor’s command but during a test process. It shows the process of DDoS IRC Bot sending the list of commands to the #xmr channel when the “!u @commands” command is entered to bring up the list of available commands.
 Figure 10. Following commands transmitted from the IRC server
Figure 10. Following commands transmitted from the IRC server
Conclusion
Typical attacks that target Linux SSH servers include brute force attacks and dictionary attacks on systems where account credentials are poorly managed. Because of this, administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the Linux server from brute force attacks and dictionary attacks, and update to the latest patch to prevent vulnerability attacks.
Administrators should also use security programs such as firewalls for servers accessible from outside to restrict access by attackers. Finally, V3 should be updated to the latest version so that malware infection can be prevented.
File Detection
– Downloader/Linux.Agent.13360 (2022.12.21.00)
– Downloader/Linux.Agent.13256 (2022.12.25.03)
– Downloader/Linux.Agent.13392 (2022.12.25.03)
– Shellbot/Perl.Generic.S1118 (2020.02.19.07)
– Linux/CoinMiner.Gen2 (2019.07.31.08)
– CoinMiner/Text.Config (2022.12.26.03)
– Trojan/Shell.Agent.SC185400 (2022.12.26.03)
– Trojan/Shell.Agent.SC185401 (2022.12.26.03)
IOC
MD5
– c13e7e87e800a970df4d113d60e75ab4: Shc Downloader (kermine)
– 1f0e5f4736a567a631946a0d9878fad7 : Shc Downloader (VirusTotal)
– 6fa237ce385dc9495246bc4498b64c2d : Shc Downloader (VirusTotal)
– 7650957bf7d798b284ea01a732ad07a5 : Perl DDoS IRC Bot (botcarternew)
– 077279a2ae5b1bc89540a1293fa807f1 : Perl DDoS IRC Bot (.ubuntu)
– 497bec45d865b2a9165699433c64816c : XMRig (s)
– c1e65d481af4e6d4bad74cca4e8737cb : XMRig (xmrig)
– 48e5ce77980d52c68a7bbfd091756036 : XMRig (.system3d)
– 16b7ef9cbc89ccc08f5fcd80e473c169 : XMRig Configuration File (config.json)
– a2fd0f3e18259d0bba9ebbf910e925c4 : XMRig Configuration File (config.json)
– a2c7c9e3b468e7e02e882066b05c55c3 : Launcher Script (run)
– c15ed837bd367fd4f66562b57b8fb57c ” Launcher Script (.b4nd1d0)
C&C URL
– 64.227.112[.]247:80 – Perl DDoS IRC Bot
– 157.230.116[.]194:80 – Perl DDoS IRC Bot
Download URL
– hxxp://172.105.211[.]21/
– hxxp://172.105.211[.]21/xmrig
– hxxp://172.105.211[.]21/snunewa.tar
– hxxp://167.172.103[.]111/
– hxxp://172.104.170[.]240/
– hxxp://172.104.170[.]240/snunewa.tar
– hxxp://wget.hostname[.]help/
– hxxp://wget.hostname[.]help/driver.zip
– hxxp://pateu.freevar[.]com/xmrminer2.tgz
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Shc Linux Malware Installing CoinMiner appeared first on ASEC BLOG.
Article Link: Shc Linux Malware Installing CoinMiner - ASEC BLOG