One of the developers’ most frequently used tools in software development is undoubtedly Postman. But what exactly are API and Postman, and how significant is their role in the software development process?
In today’s digital era, APIs (Application Programming Interfaces) have become fundamental components of software projects. An API is, in simple terms, an interface that allows one application to access the functions or data of another application or module. This interface enables different applications to easily interact with each other and share data.
For instance, a weather application uses a specific API to retrieve data from a weather service and presents this information to the user. Another example can be seen in social media platforms. These platforms use APIs to allow users to share or like posts. APIs increase efficiency in software development and provide purpose-specific integration between different systems. This enables developers to work more quickly and effectively.
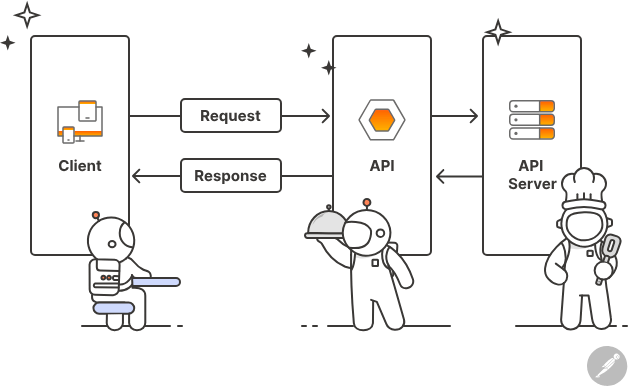 API Workflow
API Workflow
Postman is a platform that simplifies and facilitates testing and integration by making it easy to organize complex API requests. However, mistakes made while using this powerful tool can sometimes lead to unexpected risks.
Our research at the SOCRadar Threat Research team thoroughly examined workspaces created by or for over 200 randomly selected organizations. We found some containing the organizations’ confidential data. This investigation focuses on sensitive information inadvertently shared by organizations and individuals. This information includes security vulnerabilities and data that could lead to breaches and other risks. Our research methodology sheds light on how such mistakes are made, their consequences, and, most importantly, how to protect against these risks.
Postman’s role in software development and the common errors in its usage have been analyzed. Additionally, information has been provided on avoiding these mistakes and ensuring a more secure API development and testing process.
Common Mistakes and Risks in APIs
Cybersecurity Awareness is critical for the safe use and management of tools. Today, even organizations with high cybersecurity investments can be hacked, often due to end-user errors, highlighting the human factor. Even if you enhance your organization’s security with the strongest cybersecurity products, minor mistakes authorized personnel make can lead to irreversible problems. At this point, the complexity and length of the password or account access key become irrelevant.
Before looking at past critical cybersecurity incidents caused by APIs, we will provide brief information about two types of vulnerabilities that classify API weaknesses: BFLA (Broken Function Level Authorization) and BOLA (Broken Object Level Authorization), both of which are commonly encountered in API security. If you need more information you can read API Security from OWASP.
BFLA (Broken Function Level Authorization): This vulnerability stems from an application’s failure to appropriately distinguish between different user roles or authorization levels. In the case of BFLA, users might gain access to or be able to use functions, especially at the administrator level, without having the necessary permissions. For example, an ordinary user can perform operations that only an administrator or a specially authorized user can do, which is an instance of this vulnerability.
BOLA (Broken Object Level Authorization): BOLA is a security flaw arising from improper handling of object-level authorization in APIs. This can lead to unauthorized users accessing objects (such as database records or files) that should be protected via the API. BOLA poses a significant risk, particularly when users should only have access to their data. For instance, a user accessing another user’s personal information or account details indicates a BOLA vulnerability.
We have categorized API-related cyber incidents into “Incidents Arising from Access Information Leaks” and “Incidents Arising from API Vulnerabilities.”
Incidents Arising from Access Information Leaks
Credential leaks involve the accidental exposure of sensitive information such as API keys, tokens, or passwords, often leading to unauthorized access and data breaches.
The 2022 Dropbox security breach occurred as a result of a phishing campaign. This campaign targeted Dropbox employees, redirecting them to a fake website where their credentials were compromised. The attackers used these credentials to gain unauthorized access to Dropbox’s source code repositories on GitHub.
This breach highlights the importance of companies adopting layered security measures to secure internal and external API accesses. Such breaches can cause serious harm by allowing access to a company’s internal resources and sensitive data. In this incident, the threat actors did not directly misuse the APIs. However, according to the published report, they could have accessed all APIs and potentially leaked corporate and customer data using the access information.
Additionally, research by the IAM company Corsha revealed that many organizations manage a large list of API identities. 64% of the participating companies reported containing over 250 API credentials in their networks, while 3% managed over 1,000. These figures highlight the complexity and vulnerability to human error in managing API credentials.
Incidents Arising from API Vulnerabilities
API vulnerabilities encompass security weaknesses inherent in the API itself. These vulnerabilities range from inadequate authentication measures to security configuration errors and Common Vulnerabilities and Exposures (CVEs). Some high-profile incidents in 2022 have demonstrated the devastating impact of such vulnerabilities:
Texas Department of Insurance Leak (2022): In this data breach of an insurance company, a web service application mistakenly allowed unauthorized access to parts of the application that were supposed to be access-controlled, exposing 1.8 million user accounts. This incident has been classified as a Broken Function Level Authorization (BFLA) breach.
Twitter API Leak (2022): The Twitter API leakexposed the Personal Identifiable Information (PII) of 5.4 million user accounts. Since the underlying issue was insecure data, this is categorized as a Broken Object Level Authorization (BOLA) breach.
Beetle Eye Leak(2022): In 2022, an online marketing platform experienced a significant security breach. This breach exposed the Personal Identifiable Information (PII) of 7 million customer accounts. The cause of the security breach was an unsecured and unencrypted Amazon Web Services (AWS) S3 Bucket containing the customer database, which is considered a Broken Object Level Authorization (BOLA) violation.
These incidents underscore the diversity of API vulnerabilities, ranging from authentication failures to security misconfigurations and third-party integrations. This diversity highlights the need for comprehensive security measures, including robust authentication protocols and configurations.
What Data Can Be Accidentally Shared in Postman?
Before we get into the research findings, let’s classify some types of sensitive data that can be accidentally shared while using Postman.
 Postman – an API platform for building and using APIs
Postman – an API platform for building and using APIs
API Keys and Credentials: Postman often uses authentication information such as special keys or tokens for interacting with APIs. Accidentally sharing this information can lead to unauthorized access to the API and data leaks.
Sensitive Personal Information: APIs tested via Postman may contain users’ personal information. Suppose this information is inadvertently included in shared requests or responses. In that case, it can lead to privacy violations and breaches of data protection laws.
Internal Network Information and Infrastructure Details: Information related to company internal networks and system configurations can be included in API requests. Leaking this kind of information can expose security vulnerabilities and invite cyberattacks.
Test Data and Script Codes: Developers may use unique data sets and script codes for API testing. Accidentally sharing these data and script codes can lead to the exposure of business processes and testing methodologies.
Perhaps the most critical role in ensuring cybersecurity for an organization falls on the human factor. Especially for developers, a culture of cybersecurity is vital. Intriguing findings have been obtained in our research to identify the risks posed by APIs to organizations.
For the research, the domain names of 218 organizations were queried and examined using Postman’s search feature. Although we encountered numerous Postman collections containing sensitive data during the queries, the focus was solely on identifying APIs of companies with many employees/customers. We did not limit our research scope to lists like Fortune, as we knew that companies with many integrations could have a significant number of APIs, making them susceptible to oversight.
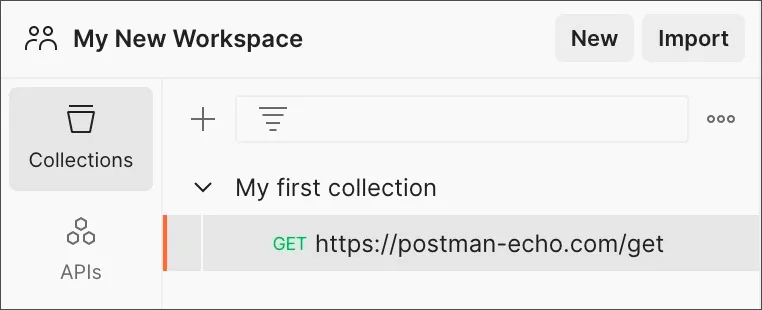 Postman Collections
Postman Collections
Postman API Collection Research by the Numbers
We investigated 218 companies and encountered API collections containing sensitive information from 17 different companies across 12 countries from 5 different continents (North America (2), South America (3), Asia (4), Europe (1), Africa (1), Oceania (1)). Typically, the collections where we found these findings also contained more related API collections within their associated workspaces.
Note: All findings mentioned below include at least one API token or authentication key. The identified findings have been communicated to the relevant organizations by SOCRadar. Nearly all organizations have taken necessary actions to close the collections or remove sensitive information.
Therefore, encountering an interface like the one below is inevitable if you were to search in Postman.
 Workspace Not Found
Workspace Not Found
Oil Company
Various APIs with different functions were found in an oil company’s Postman collection. One was the HubSpot API, a marketing, sales, and customer relationship management software.
Within the collection, it was observed that customer data could be compromised due to an overlooked API key in prepared requests. Other APIs related to payment services, tax services, etc., were also found. If misused, this situation could seriously jeopardize customer data security, leading to financial losses and damage to the company’s reputation. Screenshots related to the findings are as follows.
 HubSpot Overlooked Postman API Key
HubSpot Overlooked Postman API Key
Business Process and Technology Consulting Services Company
We identified a Postman workspace belonging to a company that provides various technology and business consulting services such as cloud infrastructure, application management, and software development. The findings included integrations in Hubspot, Sharepoint, SMS service, Telecommunications Integration, CRM (Customer Relationship Management), etc.
Threat actors could potentially misuse the openly left API tokens and connection keys, leading to severe disruptions in public services, data security breaches, and damage to systems dependent on these services. This could reduce the efficiency of public services and harm the organization’s reliability and reputation.
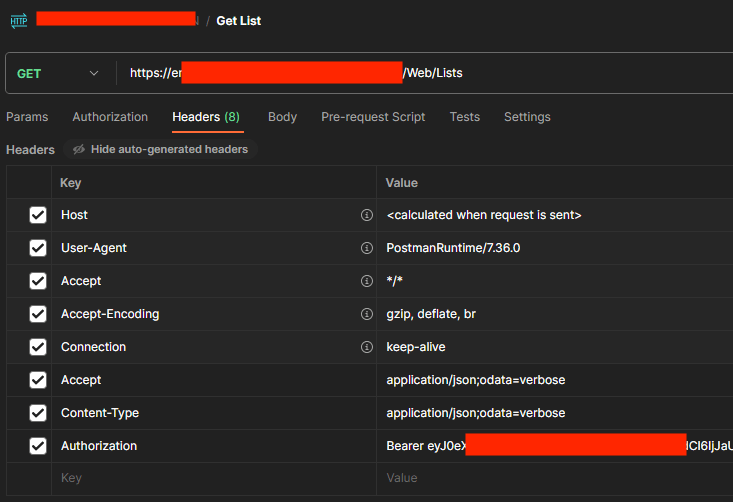
 Overlooked Postman API Keys
Overlooked Postman API Keys
Professional Accounting Firm and Cloud-Based Solutions Company
From a simple search, we came across a Postman collection within a workspace jointly used by two large firms in their field. These firms have a considerable global customer base.
A workspace that we believe belongs to these firms was found. Our assumption is based on the workspace’s name, a combination of both firms’ names. As we did not test the requests in the collections and could not verify the responses, we cannot provide definitive information about the firms.
The company’s workspace includes an API request (Token Retrieval) for a cloud-based document and email management platform containing a forgotten authorization token. This token could lead to security vulnerabilities, such as unauthorized access and manipulation of documents and records. If seized by malicious parties, it could endanger data privacy and harm the service providers’ reputation.
 Suspected Big Firm’s Workspace API
Suspected Big Firm’s Workspace API
Insurance Company Providing Risk Management Solutions
We discovered a Postman API collection from a global insurance firm offering risk management solutions. This collection contained a token API request to secure access, an initiation planning request for setting up payment plans for financial products, and a transfer request to manage policy ownership changes. This collection is designed to streamline processes in the financial and insurance sectors, enhancing automation and efficiency in the company’s operations.
Misuse of this API collection could lead to severe risks, such as security breaches of access, manipulation of payment plans, and wrongful or unauthorized policy ownership transfers. Such risks could cause financial losses and negatively affect customer trust and the company’s reputation. The security of these sensitive transactions in insurance and financial services is vital for protecting customers and the company.
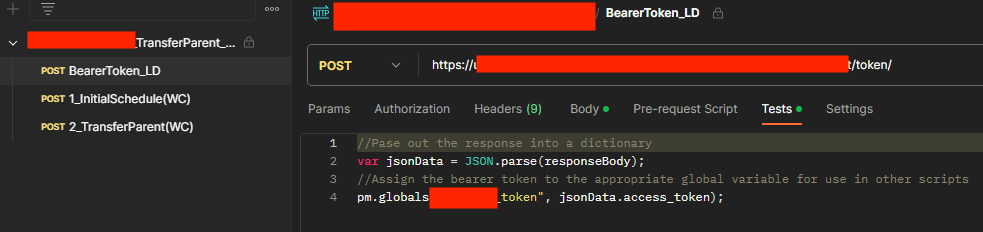 Postman API Collection Token API Request to Secure Access
Postman API Collection Token API Request to Secure Access
Professional Language Service Provider
The Postman API collection of a company providing professional language services to the private sector offers operational capabilities such as subscription management and file uploading while presenting potential risks for misuse by threat actors. Variables and usernames/passwords in subscription verification requests of web services could permit unauthorized access to sensitive data. If exploited, this could lead to the manipulation or theft of original content or project data. Robust security measures are crucial to protect these APIs from malicious activities.
Ensuring the security of this API collection, particularly regarding sensitive information and copyrighted content in language services and translation projects, is critical for maintaining the company’s customer trust and reputation. Therefore, proactive measures and continuous security audits are necessary to mitigate these risks. We also hope that in 2024, passwords like “Password1$” will no longer be in use.
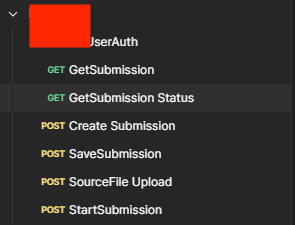 Capabilities in the Collection
Capabilities in the Collection
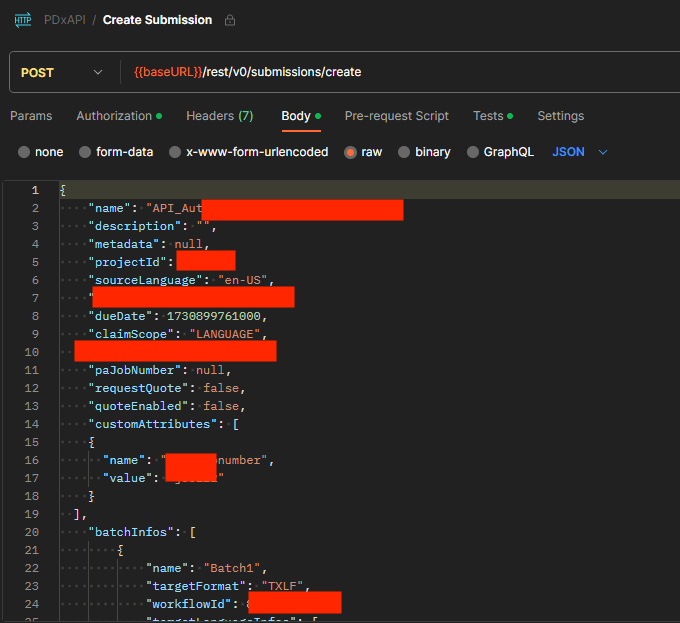 Variables Seen in a Submission Creation
Variables Seen in a Submission Creation
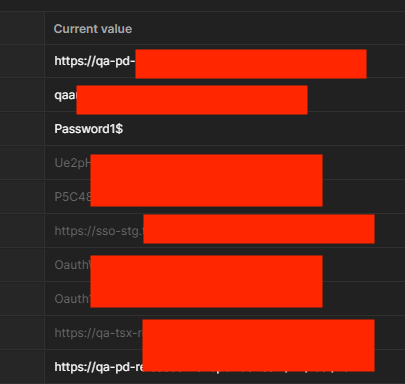 The Weak Password “Password1$”
The Weak Password “Password1$”
Global Banking Institution
The Postman collection of a globally operating bank contains API requests related to the maintenance of financial services. These requests include health checks of various environments (Development, Quality Assurance, Production), filtering logs, and managing inactive sessions. These APIs may be used in banking operations for system health monitoring, log analysis, and session management. This structure suggests focusing on system reliability and security in the banking context.
Misuse of these APIs could jeopardize the stability and security of banking systems. For example, manipulating log analyses could prevent the detection of security breaches; improper management of inactive sessions could lead to unauthorized access. Such risks could result in financial losses and raise customer security and privacy concerns. Hence, securing these APIs and their continuous monitoring are very important in the banking sector. Details related to the collection have been added.
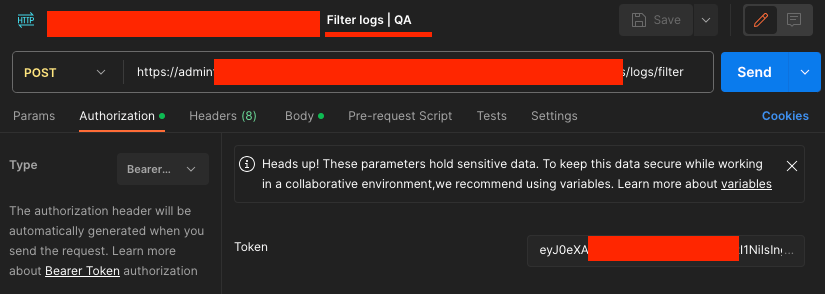 Details of the Collection of a Globally Operating Bank – 1
Details of the Collection of a Globally Operating Bank – 1
 Details of the Collection of a Globally Operating Bank – 2
Details of the Collection of a Globally Operating Bank – 2
In addition to the findings listed above, other collections belonging to critical institutions like banks, GSM operators, and government portals were also found. However, further details have not been provided as the research aimed to expose risks.
Recommendations for a More Secure API Development Environment
API security, particularly in platforms like Postman, is a critical issue that demands serious attention due to the potential for accidental exposure of sensitive data. Below are some general recommendations, best practices, awareness brought by the research, and steps to be taken in this context.
General Recommendations and Best Practices
- Automatically scanning all API requests for sensitive data can prevent accidental disclosures. This should include personal, financial, and other confidential information.
- Limiting who can access APIs and when can reduce unauthorized access. Role-based access controls and least-privilege access policies are effective in this regard.
- Using firewalls to monitor API traffic and block suspicious activities is vital in preventing attacks.
- Regular security audits and penetration testing effectively identify and rectify potential vulnerabilities.
- Encrypting and masking sensitive data ensures information protection, even in data breaches.
- Educating employees about security and increasing their awareness about the importance of protecting sensitive data is necessary.
Research Findings
Our SOCRadar Threat Research team’s investigation has highlighted often overlooked security vulnerabilities and risks in platforms like Postman. Future steps include:
- Updating API security policies.
- Integrating cybersecurity monitoring systems.
- Engaging professional Threat Intelligence services.
- Adopting a security-focused approach in development processes.
Recommended Security Protocols to Prevent Leaks
- Integrating security scans into CI/CD pipelines can detect vulnerabilities in the early stages of code development.
- Local or well-configured API management tools enhance security by allowing centralized management and monitoring of APIs.
- Preparing incident response plans for quick and effective action in potential breach situations is crucial.
Recommendations for Postman
Postman is continuously working to enhance the security of APIs. In this context, steps such as auditing the security of APIs, providing tools to users for quickly implementing security best practices, and offering educational materials to prevent security breaches are being taken. Additionally, continuously updating and improving the platform’s security settings is critical in ensuring user safety.
 Postman Workspace Settings
Postman Workspace Settings
In conclusion, ensuring API security in platforms like Postman, protecting sensitive data, and preventing accidental disclosures require an integrated approach beyond a single step. This involves a comprehensive strategic cybersecurity approach, including technological solutions and the human factor.
Security Measures with SOCRadar for API Security
SOCRadar Extended Threat Intelligence specializes in services within the realms of External Attack Surface Management (EASM), Digital Risk Protection (DRPS), and Cyber Threat Intelligence (CTI).
 SOCRadar Alarm: Sensitive Secret Data Exposure on Open-Source API Repository
SOCRadar Alarm: Sensitive Secret Data Exposure on Open-Source API Repository
As a SOCRadar client, you can enhance the security of your API processes in the following ways:
SOCRadar offers specialized services for detecting user credentials and data leaks. This can assist in identifying sensitive data that is accidentally published on platforms like Postman.
Continuous monitoring of the clear web, dark web, and deep web is necessary to detect potential cyber threats. SOCRadar provides its clients with detailed monitoring services in this area.
Protecting accounts of users with high privileges and monitoring the cybersecurity incidents of organizations in your supply chain are crucial for API security. SOCRadar offers solutions that include such protective measures.
The effective use of threat intelligence and the automation of incident response processes through SOCRadar’s integrations enhance API security.
The solutions SOCRadar provides offer a comprehensive approach to API security and are particularly helpful in identifying sensitive data accidentally published on platforms like Postman. Integrating such solutions is important in creating a more secure working environment.
The post Sensitive Information in APIs and Secure Usage of Postman appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: https://socradar.io/sensitive-information-in-apis-and-secure-usage-of-postman/
