Gain Complete Visibility and Eliminate Network Blind Spots in AWS Cloud
AWS’ inaugural security event re:Inforce is finally here. Moreover, this event marks the launch of yet another exciting new feature from AWS: VPC Traffic Mirroring. This feature provides a non-intrusive way to enable network visibility into your AWS deployments without requiring significant design changes to virtual network architecture.
Equally exciting, Palo Alto Networks has built an integration of its VM-Series Virtualized Next-Generation Firewall with AWS traffic mirroring capability. The VM-Series is the industry-leading virtualized firewall protecting your applications and data with next-generation security features that deliver superior visibility, precise control, and threat prevention at the application level.
The VM-Series has supported AWS cloud since 2014 with inline security protections for application workloads running in the cloud. According to Mukesh Gupta, vice president of Product Management at Palo Alto Networks, “Enterprises require consistent security in the cloud without sacrificing deployment flexibility and choice. Along with inline threat prevention capabilities, the integration of the VM-Series with the newly announced AWS traffic mirroring capability gives organizations a choice to deploy the firewall out-of-band for application visibility and advanced threat detection in AWS cloud.”
The VM-Series on AWS deployed out of band now supports two critical security outcomes in AWS cloud:
- Granular visibility into application traffic and detection of network-borne threats through inspection of mirrored traffic.
- Rapid detection and response against advanced attacks using an AI-driven approach, such as Cortex by Palo Alto Networks.
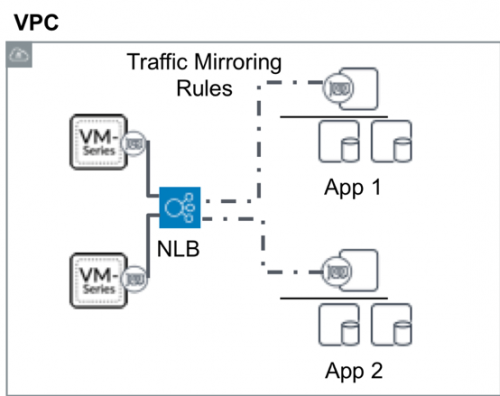
Application visibility and threat detection
The VM-Series on AWS can analyze, filter, and process the raw data available through the AWS traffic mirroring capability within AWS cloud and provide contextually rich application, content, and threat information. The need for extracting data out of AWS cloud for further processing is eliminated, saving cost and providing deep insight into network traffic. Based on this more in-depth inspection, customers can choose to enable alerts for a wide range of security issues, for example:
- High priority security alerts: Attacks for known exploits, for example, an attempt to exploit CVE-2017-5638 for Apache Struts-based web servers running in AWS. Primarily, the VM-Series is serving as an intrusion detection system (IDS).
- Traffic to inappropriate, malicious destinations and command-and-control systems: detect if the source/destination is inappropriate or malicious, whether there are geoblocking restrictions to be met, or if there is bitcoin traffic or an SSH session to a known command-and-control (C2) domain.
Based on the visibility and detection (in logs), you can filter for events, and enable alerts and actions that can trigger remediation using Action-Oriented log forwarding using HTTP(S). This provides a webhook to create a ticket in a service desk system or a security orchestration and response tool, such as Demisto, or launch an AWS Lambda function, which can quarantine by shutting down the instance or lock down the Security Group.
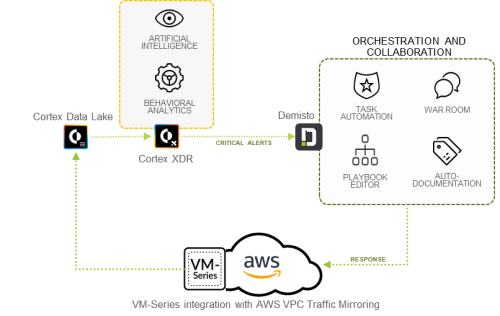
Rapid detection and response against advanced attacks
The VM-Series firewall supports enhanced application logging, which converts raw packet data from AWS mirrored network traffic into context-aware network activity information for storage in Palo Alto Networks cloud services, including Cortex Data Lake. Security applications, such as Cortex XDR, can start analyzing the rich data collected, using analytics and machine learning to detect stealthy attacks and expedite security investigations accurately. Identified threats can be mitigated through automated response from Demisto and other security orchestration and response tools.
To learn more, we encourage you to follow these links:
- AWS Traffic Mirroring blog documentation
- VM-Series in AWS Marketplace
- GitHub repository with sample VM-Series configuration for traffic mirroring
- VXLAN Tunnel Content Inspection feature in PAN-OS 9.0
- Log Filtering in PAN-OS
- Action-Oriented Log Forwarding Using HTTP(S)
- Learn more about the VM-Series for inline use cases (datasheet with performance information)
- Learn more about the VM-Series on AWS
- What’s new in PAN-OS 9.0
The post See the Unseen in AWS Mirrored Traffic With the VM-Series appeared first on Palo Alto Networks Blog.
![]()
Article Link: http://feedproxy.google.com/~r/PaloAltoNetworks/~3/hVgqHbalwxo/