 Digital threats are more numerous today than they were years ago. Illustrating this fact, Kaspersky Lab’s in-lab detection technologies identified 360,000 new threats each day in 2017. That figure is 11.5 percent more than 2016, and it represents the second year in a row where the number of malicious files identified each day by the security firm increased.
Digital threats are more numerous today than they were years ago. Illustrating this fact, Kaspersky Lab’s in-lab detection technologies identified 360,000 new threats each day in 2017. That figure is 11.5 percent more than 2016, and it represents the second year in a row where the number of malicious files identified each day by the security firm increased.
At the same time, there are some categories of digital threats around today that weren’t there a decade ago. These include malware like Remsec whose modular design enables bad actors to tailor their malicious activity to each infected machine. There are also fileless threats that target a computer’s memory, not its hard drive, by using applications like PowerShell and Windows Management Interface (WMI).
IT specialist Gary Stevens said that digital attackers have a clear motivation for switching to more sophisticated threats like fileless malware. As he wrote for The State of Security:
The reason sophisticated cyber criminals have shifted their focus away from popular malware strategies like brute force automated login attempts or sneaky spear phishing schemes is simple: traditional antivirus and anti-malware security aren’t even looking where these fileless malware attacks are going. They aren’t designed to stop this kind of thing. The AV suite on your computer is trained to sniff out trouble when one thing happens – a file is written. Does that mean traditional AV suites are useless in detecting this new type of computer takeover? Yep, that’s exactly what it means.
The Golden Triangle of Information Security
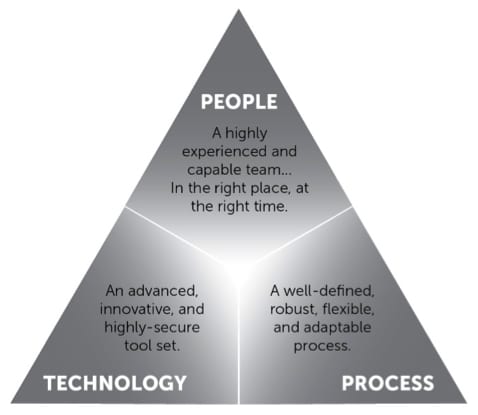 Fortunately, organizations aren’t powerless to protect themselves. They can defend against today’s increasingly numerous and diverse digital threats by strengthening their information security programs. To do that, they must look to the Golden Triangle, a model that divides an effective information security program into three equal parts.
Fortunately, organizations aren’t powerless to protect themselves. They can defend against today’s increasingly numerous and diverse digital threats by strengthening their information security programs. To do that, they must look to the Golden Triangle, a model that divides an effective information security program into three equal parts.
People
Organizations need to hire trained personnel who possess skill sets that are essential to the functioning of a robust security program. Per CIO, one of the most important skill sets is expertise with basic security tools that are commonly found in an enterprise setting. Knowledge surrounding security analysis and project management are also extremely valuable.
It’s not always easy for organizations to find candidates with these skills sets, however. This difficulty has produced a hiring shortfall in the industry, with Gartner finding that more than a third (35 percent) of organizations don’t have a security expert on staff. The skills gap isn’t expected to improve anytime soon, either. According to Cybersecurity Ventures, there will be 3.5 million unfilled digital security jobs by 2021. To remedy this situation, IBM recommends that organizations look within to satisfy their hiring needs and create their own professional development programs.
Process
Besides having qualified people in place, organizations need to have processes focused on the right information security measures. Gartner recommends six processes in particular:
- Security Governance – The system by which organizations direct their information security risk management strategy.
- Policy Management – Ongoing work to align the organization’s information security policy with its business requirements.
- Awareness and Education – Programs for training the workforce about digital threats and building a positive organizational security culture.
- Identity and Access Management – Controls that help ensure the right people in an organization have the appropriate level of access to IT assets and data.
- Vulnerability Management – A framework that’s useful for identifying known vulnerabilities, assessing their risk, and prioritizing their mitigation.
- Incident Response – The procedures that are necessary for IT security teams to triage potential threats and take action when necessary.
The level of maturity reflected in these processes is unachievable without organizations merging their security processes with their business processes and priorities.
Technology
Having the right technology in place brings an information security program together. There are lots of tools in the toolbox that skilled infosec pros can use to implement an organization’s security processes. But where is a business to start?
The most important aspect of technology is knowing that there is no one solution that can fulfill every purpose and process. Security is a team sport, so the most effective approach is to use multiple technologies in tandem. It’s even better when these technologies have been designed to work together and draw upon one another’s strengths.
Introducing Tripwire Malware Detection
In the spirit of such teamwork, Lastline signed an original equipment manufacturer (OEM) agreement with Tripwire Inc. This agreement laid the groundwork for Tripwire Malware Detection, a solution where Lastline’s technology is directly incorporated into Tripwire Enterprise. As Tripwire’s flagship secure configuration management suite, Tripwire Enterprise helps maintain the integrity of customers’ IT systems by establishing a secure configuration baseline and monitoring for changes.
This isn’t the first time that Lastline and Tripwire have come together. The two companies agreed to have Tripwire Enterprise integrate the Lastline Breach Detection Platform in 2014. Under this arrangement, Tripwire Enterprise continually monitored for and captured system and file change data. If and when it discovered a suspicious, unknown threat, Tripwire Enterprise sent that information to Lastline Breach Detection Platform, which identifies advanced and previously unknown threats designed to evade first-generation sandboxes and traditional security systems. Lastline then used this data to update its threat intelligence database and to help flag malicious binaries detected by Tripwire Enterprise, thereby aiding security teams in their incident response efforts.
Tripwire Malware Detection builds on this relationship by deepening the complementary relationship between Tripwire Enterprise and Lastline’s solutions. For example, Lastline now helps Tripwire Enterprise protect against failures and ensures availability by providing high fidelity visibility into malicious campaigns that target critical infrastructure. It also aids Tripwire Enterprise in its detection of changes and vulnerabilities by supplying threat insights and correlation of malicious activity targeting these changes or vulnerabilities. Finally, Lastline helps Tripwire Enterprise customers audit evidence reporting to reduce workload and maintain compliance by delivering highly accurate and forensically backed attack chain evidence of malicious traffic targeting an organization’s infrastructure.
Stop Malware With Tripwire and Lastline
As an example of how Tripwire Malware Detection works using Tripwire Enterprise and Lastline, say a Tripwire admin receives an alert about a potentially malicious file detected within one of the monitored assets. They use Tripwire Enterprise to figure out where and when the changes took place. Simultaneously, they use Lastline to gain complete visibility into the activity displayed when spun up into the cloud sandbox environment. If the file is found to be malicious, the admin can then delete the file without it affecting the organization’s critical servers.
Other types of solutions scan at scheduled intervals and require signature updates at each endpoint. Not Tripwire Malware Detection. This tool activates whenever there’s a change, with Lastline’s technology facilitating the quick detection of known threats and zero-days alike. Tripwire Malware Detection saves time and money; Tripwire Enterprise and Lastline work side-by-side, so there’s no need to install another solution or train security pros on how to use it.
An organization’s security program is only as strong as its individual parts. Fortunately, companies can target one element of their security program’s Golden Triangle with greater focus and investment to strengthen their security posture overall. That’s the story with Tripwire Malware Detection. Organizations can use this technology to improve the efficiency of their limited staff in implementing their security processes, thereby elevating their digital security.
For more information about how Lastline works in Tripwire Malware Detection, click here.
The post Security as a Team Sport: Working Together to Stop Malware in Its Tracks appeared first on Lastline.
Article Link: Threat Intelligence Archives - Network and Security Virtualization - VMware