TLDR: Highlights of Intezer’s Autonomous SOC solution for Microsoft Defender for Endpoint
- Auto resolve alerts that Intezer identifies as false positives, based on your pre-defined classifications.
- Reduced response time for critical security investigations.
- Simplified IOC and rule extraction for incident remediation and threat hunting.
- Automatically conduct deep endpoint forensics and memory analysis for each alert.
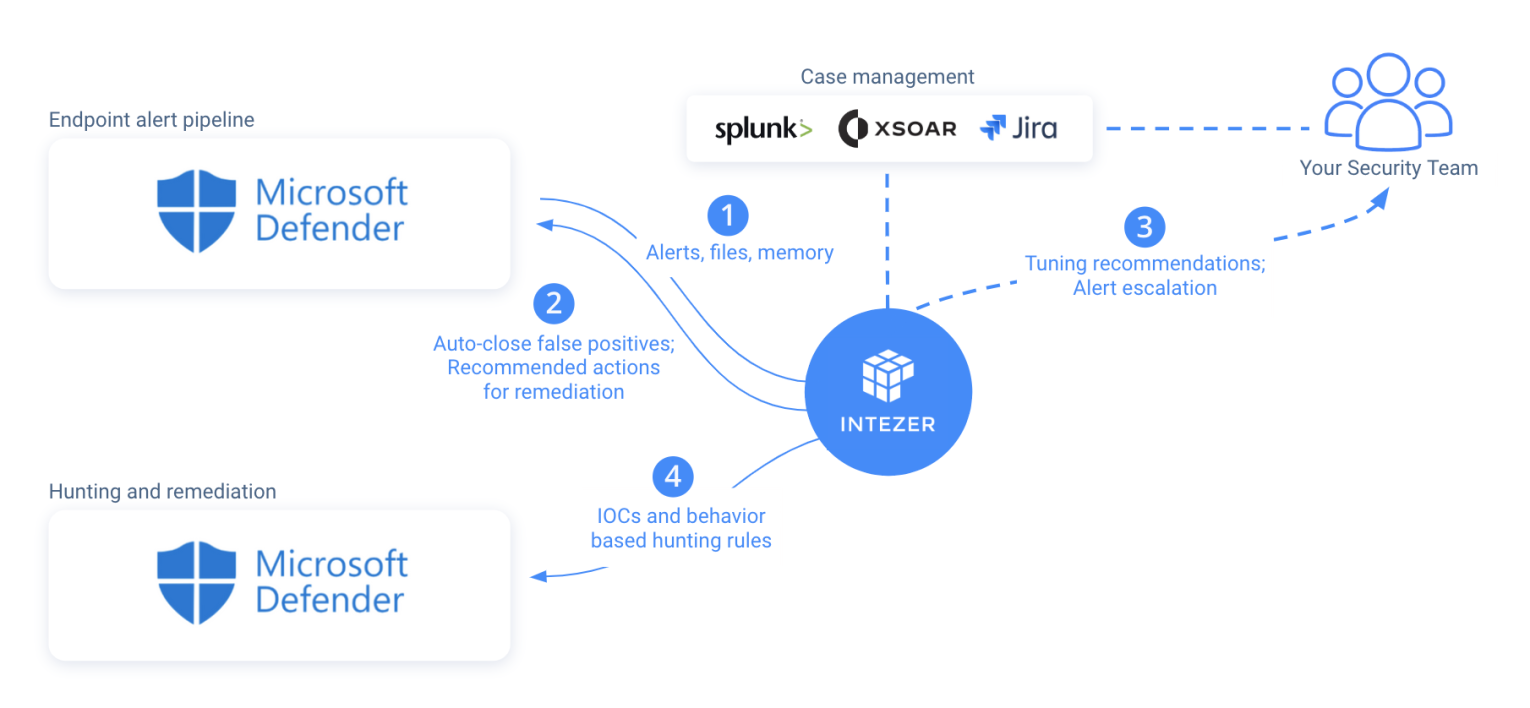 How Intezer works with Microsoft Defender for Endpoint.
How Intezer works with Microsoft Defender for Endpoint.
Automating SOC Triage and Investigations with Defender
Intezer’s Autonomous SOC solution now supports Microsoft Defender for Endpoint, enabling security teams to automatically triage incidents and get deep endpoint forensics. As Microsoft Defender is a leading endpoint security solution providing prevention, detection, and response across all major OSs, this allows more security teams to leverage autonomous SOC technology in their environments.
So how does Intezer work with Microsoft Defender? When an endpoint incident is created in Microsoft Defender, artifacts are automatically collected by Intezer for deep analysis and investigation down to the code level. Intezer can then auto-resolve alerts it confirms as false positives. All analysis results get sent to the Microsoft Defender console for transparency, so it’s easy to review what led to Intezer’s verdict. Confirmed threats get deeply investigated by Intezer and escalated, quickly giving you additional context, classification, and threat hunting detection opportunities.
An ongoing challenge for SOC teams is trying to keep up with a tedious, never-ending stream of alerts to triage. In today’s reality, security teams can spend a large amount of their valuable time on confirming alerts instead of investigating real incidents (or paying a big chunk of their budget to outsource some tasks).
By replacing manual processes with machine-speed detection and deep analysis, security teams can respond to incidents with greater speed and confidence. Connecting Intezer with endpoint security tools in your alert triage workflow allows you to automate more tasks and make sure your team can quickly identify and focus on the most critical threats.
Intezer for Microsoft Defender Benefits
- Automate alert triage for time savings and a unified workflow.
- Auto remediate false positives identified by Intezer’s analysis: based on your settings for Microsoft Defender alerts, Intezer updates the Classification to “False Positive” and updates the Status to “Resolved.”
- Get additional context for scanned artifacts including attribution, malware families, indicators of compromise (IOC), and TTPs mapped to MITRE ATT&CK®.
- Hunt for traces of advanced in-memory threats such as fileless and packed malware, malicious code injections, or any unrecognized code by running Intezer’s Live Endpoint Scanner from your Microsoft Defender console.
- Out-of-the-box detection content for threat hunting provides immediate time-to-value.
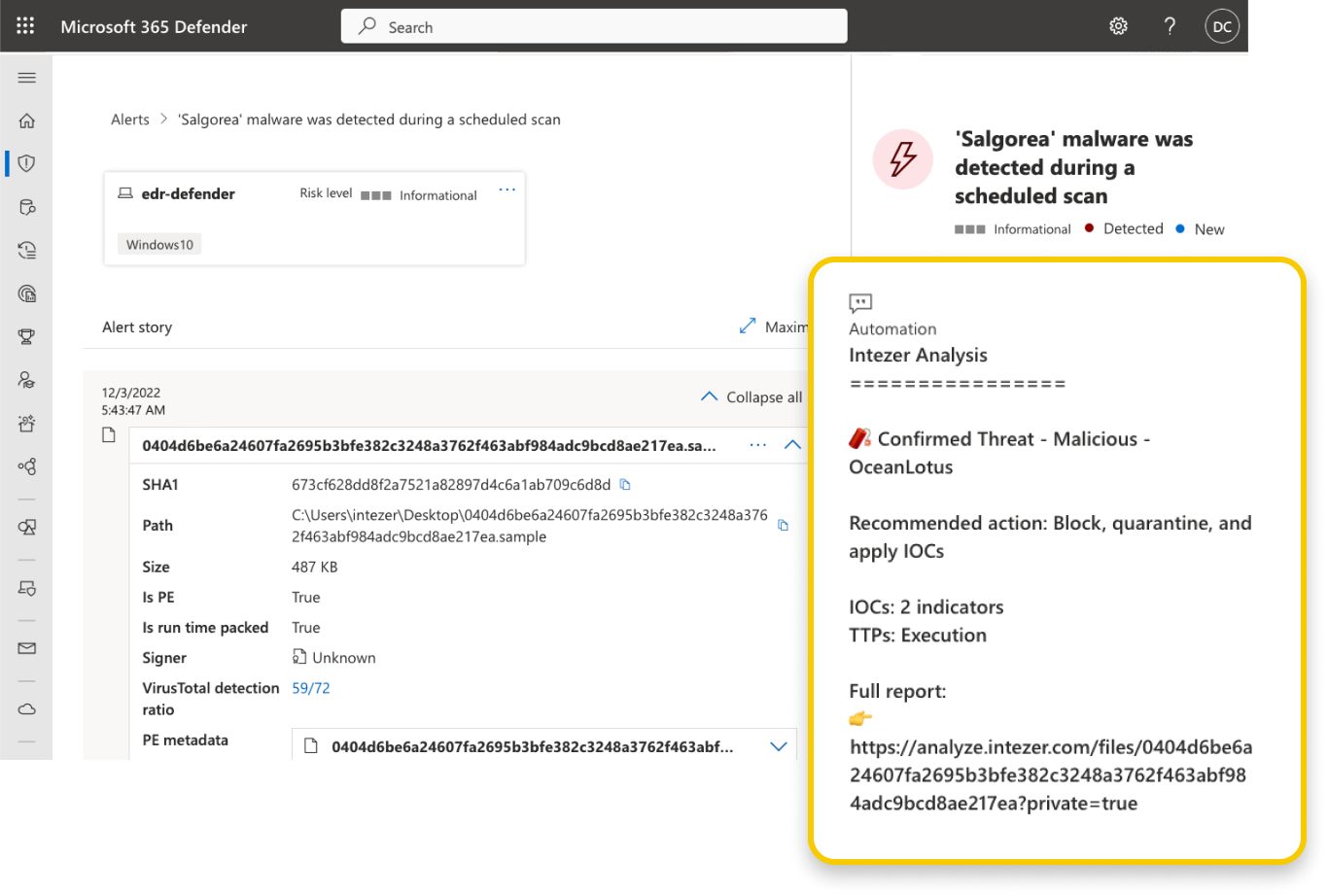 Illustration of Intezer’s analysis results for an individual alert in Defender.
Illustration of Intezer’s analysis results for an individual alert in Defender.
How It Works with Your Incident Response Processes
Here we’ll look at how Intezer’s Autonomous SOC solution works, as shown above, step-by-step during the process of triage and incident response.
- Microsoft Defender detects malicious activity on an endpoint and creates an incident.
- Intezer is alerted to the incident and uses Microsoft Defender to retrieve the artifact from the endpoint for analysis. The artifact is sent to Intezer for analysis.
- Intezer enriches the incident in Microsoft Defender with an analysis link, context, verdict, and threat family information.
- Intezer takes action to auto-remediate alerts that it confirms as false positives after analysis.
- Users can dive into the linked Intezer analysis report to identify additional IOCs and create threat hunting queries for confirmed threats.
- Additional indicators can be added to Microsoft Defender’s blocklist or in a custom detection rule to alert and perform an automated response next time those indicators are seen.
- Autonomously respond to threats in Microsoft Defender by killing, quarantining, remediating, or rolling back the effects of the malicious code.
- Scan a suspicious endpoint or proactively hunt for traces of advanced in-memory threats (such as fileless and packed malware, malicious code injections, or any unrecognized code) by launching Intezer’s live Endpoint Scanner from inside Microsoft Defender.
- Content for threat hunting can be extracted from Intezer and used with Microsoft Defender to search for additional indicators across the environment.
Solution Use Cases
- Alert Triage – With automated analysis of every alert, analysts are able to confirm if an alert is a true positive that warrants escalation and use Intezer’s investigation results to respond quickly. This can supplement your team or replace expensive managed detections and response providers that provide outsourced SOC services.
- Deep Endpoint Forensics – Launching Intezer’s Endpoint Scanner from Microsoft Defender allows teams to quickly get forensics evidence, without requiring advanced skills or a lot of time. This remotely downloads a lightweight executable to the suspicious endpoint (or all endpoints in an environment), executes the scan, and logs the resulting analysis as a report in Intezer for incident responders.
“Too many teams face challenges hiring and retaining skilled security professionals, but they can feel empowered by introducing more automation into their workflows for alert triage, response, and threat hunting with Intezer’s integration that combines seamlessly with CrowdStrike’s platform.”
— Itai Tevet, CEO and Founder, Intezer
Reducing Alert Fatigue for SOC/IR Teams to Improve MTTR
The deluge of alerts from security tooling and the tedious nature of the Tier 1 analyst position makes burnout one of the leading contributors to the shortage of security talent.
SOC teams are increasingly looking to automation to handle repetitive tasks required for triage and incident response (or avoid the high price of outsourced managed detection and response providers). When security teams are overwhelmed with alerts, reliant on expensive outsourced providers, or experiencing alert fatigue, then integrating automation into an alert triage process is key to reducing the mean time to respond (MTTR) for incidents. This smart use of automation allows SOC teams to focus their limited resources on the highest impact and most critical incidents, increasing throughput and reducing the time to respond.
Not an Intezer customer yet? Book a demo to talk with us and see how Intezer for Microsoft Defender could help your SOC team.
If you are an Intezer customer, login and then use “Connect Sources” to enter your Microsoft Defender API key and start triaging alerts with Intezer.
The post Scaling your SOC with Microsoft Defender + Intezer appeared first on Intezer.
Article Link: Scaling your SOC with Microsoft Defender + Intezer - Intezer