This is ANY.RUN’s monthly update, where we keep you posted on our progress.
In November, we added new functionality that enables step-by-step analysis of script execution in ANY.RUN. We also introduced the capability to upload additional files to a virtual machine during active interactive sessions. This allows you to bring your own tooling, malware stages, or dependencies into active tasks.
Product updates
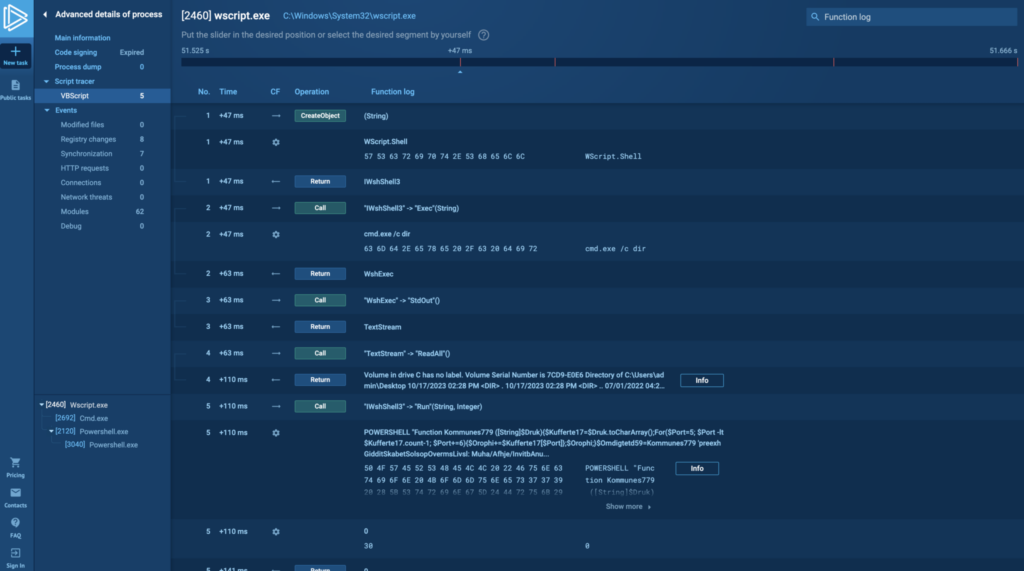
Script tracer
Tracer can help you deobfuscate the execution flow of scripting programs written in JScript, VB Script, VBA, and Macro 4.0. This feature works in all of our supported OS versions, from Windows 7 to Windows 11.
Read about Script tracer in more details
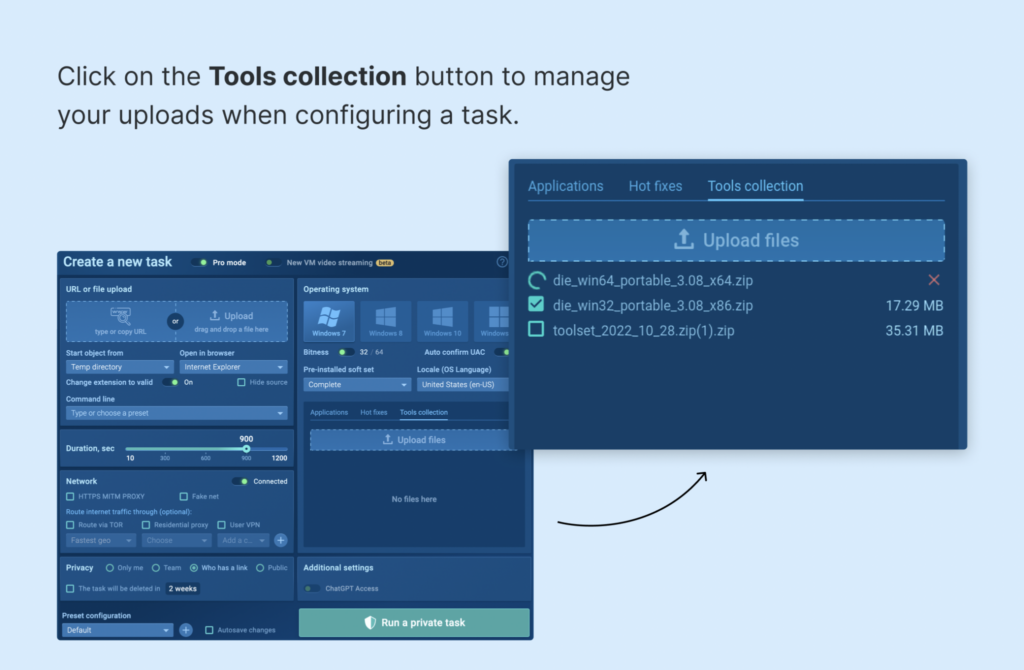
Uploading files into active tasks
You can now upload additional files to a VM, including while it is running. The sandbox allows for uploading a total of up to 500 MB of files. Hunter and Enterprise subscribers gain access to the Collection tab, where they can store their favorite files for quick and easy access.
Learn more about uploading files to running tasks in ANY.RUN
ANY.RUN Enterprise plan at a discount
Use promo: SANDBOXSAVER
New YARA
In November, we added YARA rules for new malware families:
- AlfaC2: Introduced YARA rules for this malware, which is based on the merged CHAOS framework.
- PureLogs: Added detection for this multifunctional stealer from the PureCode group. Notable for being packed with NetReactor.
- PureCrypter: Implemented rules for this multifunctional obfuscator-cryptor, also from the PureCode group, featuring a smart assembler cover.
- SheetRAT: Developed YARA rules for this malware, known to originate from Discord channels.
- GrMsk: Our analysts have named this new threat “GrMsk”. YARA rules have been formulated for its detection.
New signatures
We’ve also added multiple new Suricata rules. Here are some of the highlights:
- Phishing: New signatures for IPFSQuery, CapSeg, EvilProxy, and Tycoon. The first two phishing signatures (IPFSQuery, CapSeg) are codenames for as-yet-unknown phishing services.
- Loaders: Added detection for PureLoader, Talisman, and Smokeloader. The Pureloader signature relates to the activity of PureCrypter, specifically its module loading capabilities, as researched by ANY.RUN’s khr0x.
- Stealers: Updated with signatures for UmbralStealer, BlankGrabber, FtpFileStealer, Vidar, and GreedyStealer. The names FtpFileStealer and GreedyStealer were coined by ANY.RUN.
- Ransomware: Introduced signatures for CryptGh0st and CryptoLocker.
- Proxy: Now detecting Socks5Systemz.
- Backdoors: Enhanced detection for JinxV2DEV, Gh0stRat, and BrushaLoader. JinxV2DEV, a new backdoor, was identified through its unique user agent. BrushaLoader is a new version of the previously known backdoor (read its analysis from 2018 here).
- Tracer signatures: Enhanced script analysis capabilities with new signatures for using a tracer. This aids in understanding the activities within scripts more effectively.
Wrapping up
We’re continuing to work on and expand our sandbox capabilities. What feature would you most like to see, or what are you currently missing in your day-to-day work with ANY.RUN? Let us know in the comments below — we’d really appreciate your feedback.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
The post Release Notes: Script Tracer, Uploading Files Into Active Tasks, New Rules, and More appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Release Notes: Script Tracer, Extra File Uploads, and New Rules