Welcome to ANY.RUN’s monthly update series, where we share what the team has been working on this past month.
In January, we expanded ANY.RUN’s capabilities, with the support of Linux, improved phishing coverage, detected new threats like Bitter-wmRAT and MustangPanda-Toneshell, introduced over 17 new signatures, including Linux ones, and added multiple new Yara rules.
New features
Linux
We’ve expanded our capabilities to include support for analyzing Linux-based malware. Now, you can research malware samples targeting Linux right in your browser!
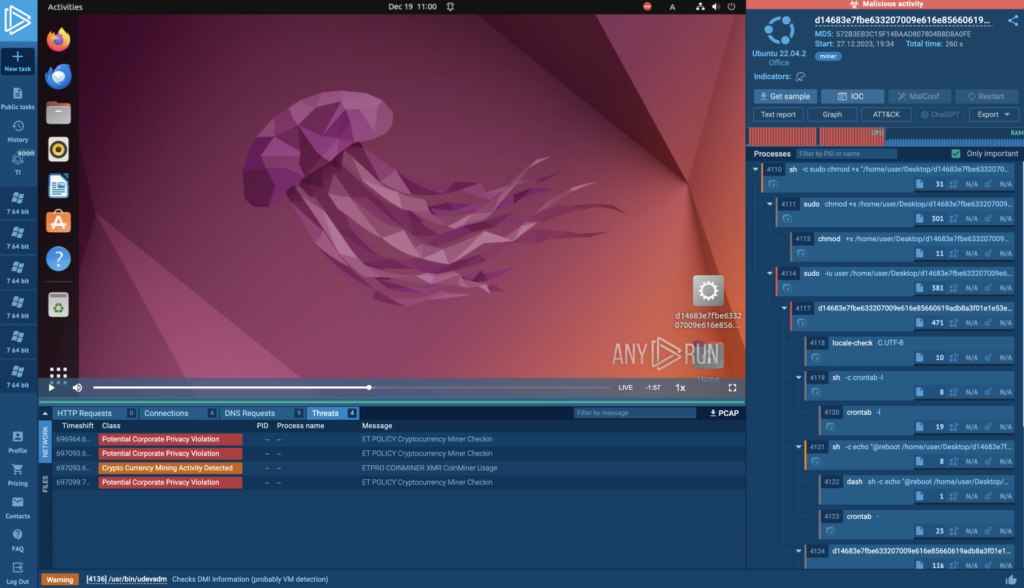 Linux VM running in ANY.RUN — a miner is detected on Linux
Linux VM running in ANY.RUN — a miner is detected on Linux
This is a significant step for ANY.RUN as we extend our interactive analysis capabilities to the Linux platform, specifically Ubuntu 22.04.2. Our service offers real-time monitoring of suspicious activities and provides access to IOCs even before task completion. Additionally, you will receive detailed reports like MITTRE ATT&CK Matrix, Process Graph, and IOCs Report to help you extract actionable information quickly.
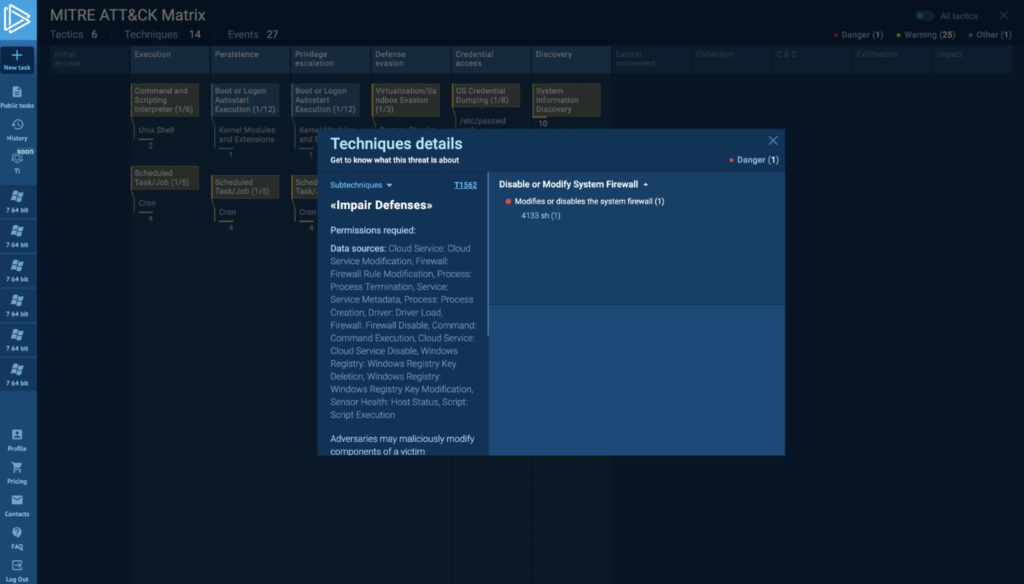 MITRE ATT&CK Matrix is available for Linux tasks in ANY.RUN
MITRE ATT&CK Matrix is available for Linux tasks in ANY.RUN
Read about introduction of Linux support to ANY.RUN
Ready to analyze Linux-based malware in ANY.RUN? Get started today
Register for free
Improved phishing coverage
In January, we enhanced our network detection capabilities by introducing new phishing rules. These rules not only include specific domains, but also domain correlations but also address the RDGA threat associated with MageCart. We gave particular attention to monitoring the Caffeine phishing kit.
New threats detected in January
We’ve detected the actions of two backdoors used by APT groups. The first one is associated with Bitter-wmRAT. The second one is linked to MustangPanda-Toneshell.
Additionally, we’ve identified a new remote access tool called RadX. Learn more about it here
New Signatures and Yara Rules
We have introduced 17 new signatures for our production system, along with approximately 14 new Linux signatures. We have also added a Yara rule for BazaLoader, which we’ve shared with the community in our GitHub repository here— feel free to use it for your own work.
Other updated and added rules include:
- BazaLoader
- GCleaner
- Xeno-RAT backdoor
- Zima and Rust miners.
We’ve also shared detection rules with The ET community, including ZharkBot, RadX, and Xeno-RAT.
In addition, we’ve added detection for the CoinSurf proxy, and our new rules proved effective in detecting the Lumma Stealer, even when it attempts to hide under TLS encryption.
Easily analyze emerging malware with ANY.RUN cloud malware sandbox
Register for freeVarious fixes
We’ve implemented multiple fixes, including one related to BazaLoader and another for RADX. Issues with SystemBC Yara and the extractor were resolved. We’ve also implemented fixes for PrivateLoader and GCleaner, regarding their detection and C2 extraction.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
The post Release Notes: Linux Support, New Signatures, and Coverage of Emerging Threats appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Release Notes: Linux, Signatures, and Coverage of New Threats