Welcome to ANY.RUN’s monthly update series, where we share what the team has been working on this past month.
In December, ANY.RUN introduced Automated Interactivity using Machine Learning. New YARA rules were added for malware families such as W4SP Stealer, Klippr, OriginBotnet, DarkGate, and IcedId. Suricata signatures were updated, adding detection for AxileStealer, Vidar, AlbumStealer and more.
New features
Automated interactivity (ML)
ANY.RUN can now intelligently mimic human actions during task execution. Think of it as an advanced auto-clicker — the new feature uses Machine Learning to detect and sort buttons based on their importance, always choosing options that move the task forward. This includes navigating through setup forms or getting past captchas.
For API tasks, this feature is always on and will kick in when manual input is needed — such as to bypass a CAPTCHA on phishing site. This drastically increases detection rate of samples that use advanced evasion tactics.
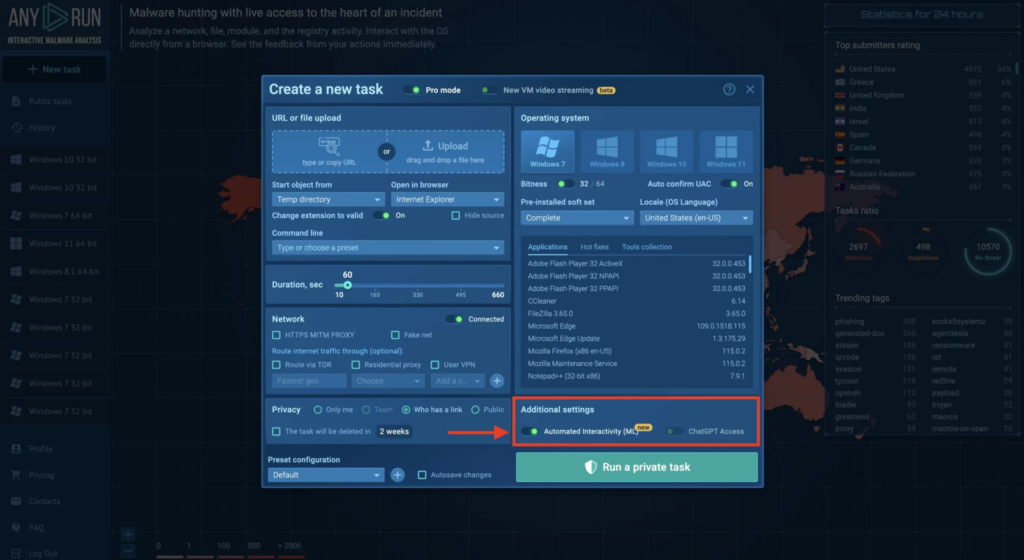
Via the interface, the feature is disabled by default. When enabled, tasks can now run autonomously in the background, letting you focus elsewhere. And if you ever want to jump back in, you have the flexibility to take over and guide the task to completion manually.
Read about automated interactivity in more details
Expanded Suricata rules
ANY.RUN already utilizes Suricata for network rules detection. We’re now broadening the scope of information displayed to the user when a detection occurs. Now, you’ll be able to see which specific rule was triggered, identify the traffic segment affected, detail the relevant fields, and often, even see the rule itself within the interface.
This will allow you to understand each detection better and apply our rules in your own detection processes and incident investigations.
New YARA Rules
We’ve added 3 new signatures to detect various activities within the task. Our latest YARA rules cover these malware families:
- W4SP Stealer
- Klippr
- OriginBotnet
- DarkGate
- IcedId
Easily analyze emerging malware with ANY.RUN cloud malware sandbox
Register for freeNew Rules and updates: December overview
We’ve also added multiple new Suricata signatures. Here’s the breakdown:
- Stealers: This month, we’ve added detection for AxileStealer, an updated version of Vidar, and AlbumStealer.
- Backdoors: ANY.RUN now detects Gh0stRat‘s encrypted dll which can be hidden within jpeg files.
- Phishing: Added detection of a new chain of suspicious activities.
- Loaders: Updated a signature for DarkGate, which altered its activities following our recent Twitter post on its new techniques. Also added are Pikabot and QakBot, which we also covered on Twitter.
- Proxy: Now detecting GoProxy.
- Ransomware: Added detection for DirCrypt
Tell us about your experience using ANY.RUN
We’re always improving and growing our sandbox features. If there’s anything specific, you’d like us to add, or something you’re missing in your daily tasks with ANY.RUN, we’d love to hear your thoughts in the comments below.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
The post Release Notes: Automated Interactivity (ML), New YARA Rules, and Network Signatures appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: https://any.run/cybersecurity-blog/release-notes-december-2023/