Author: Sunhyung Shim, Jaehak Oh | S2W Marketing
 Photo by Koukichi Takahashi on Unsplash
Photo by Koukichi Takahashi on UnsplashExecutive Summary
- S2W data analysis reveals a significant uptick in cyberattacks targeting Japanese businesses and government agencies from January to October of this year. Notably, there has been a substantial increase in activities related to Japanese data trading on dark web hacking forums and Telegram, particularly in Distributed Denial of Service (DDOS) attacks against major government agencies and corporations.

Darkweb Hacking Forum
- An analysis of dark web hacking forum posts indicates a 58.2% increase in cybercrime targeting Japan compared to the same period last year, surpassing the global average increase by 18 percentage points.
- The most affected industries, in descending order, are Japan’s key sectors:
“Electronics manufacturing”, “Gaming”, and “Automotive”. - Notably, the “Electronics manufacturing” and “Gaming industries” have incurred substantial losses. SONY recently suffered a ransomware attack, leading to data leakage subsequently traded on multiple hacking forums. Additionally, numerous posts regarding internal data breaches at NINTENDO have surfaced.
Ransomware
- Ransomware attacks on Japanese businesses and government agencies have experienced a marginal decline in comparison to the prior year. Nonetheless, this decline is consistent with global trends, and significant corporations remain susceptible to attacks.
- The most affected sector has been the “Manufacturing” industry, constituting roughly 62% of the incidents. This figure surpasses the global average by approximately 37% and the Asian average by about 24%.
Telegram
- In the current year, Japan has witnessed a substantial increase in cyberattacks, with a notable 1,000% rise in messages referencing Japan compared to the previous year.
- These cybercrimes predominantly involve the theft and dissemination of personal information, along with frequent incidents of cyberattacks targeting government agencies and businesses, encompassing DDoS attacks and website infiltration attempts.
→ The responsible entities are often known as “hacktivists” active on platforms like Telegram. They primarily focus on launching cyberattacks against nations that oppose their political beliefs, resulting in significant damage, including site shutdowns and defacement, for major Japanese government agencies and businesses this year.
Darkweb Hacking Forum Analysis
Distribution of affected industries / Comparison with neighboring countries
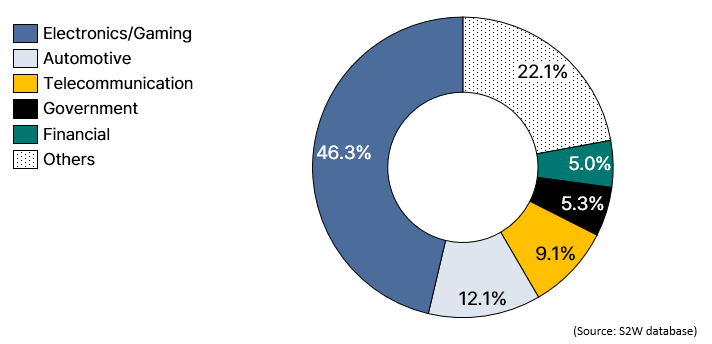 Distribution of affected industries within Japan
Distribution of affected industries within Japan- A recent analysis of postings on hacking forums related to data breaches involving Japanese businesses has revealed that prominent Japanese industries such as “Electronics manufacturing”, “Gaming”, and “Automotive” have suffered a significant number of data leakage incidents.
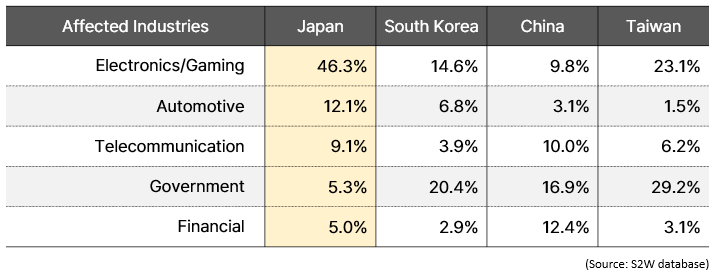
- Even when compared to data from neighboring countries, the data leakage incidents in Japanese “Electronics manufacturing” companies, “Gaming” companies, and “Automotive” companies stand out as notably higher.
Electronic Manufacturer: SONY
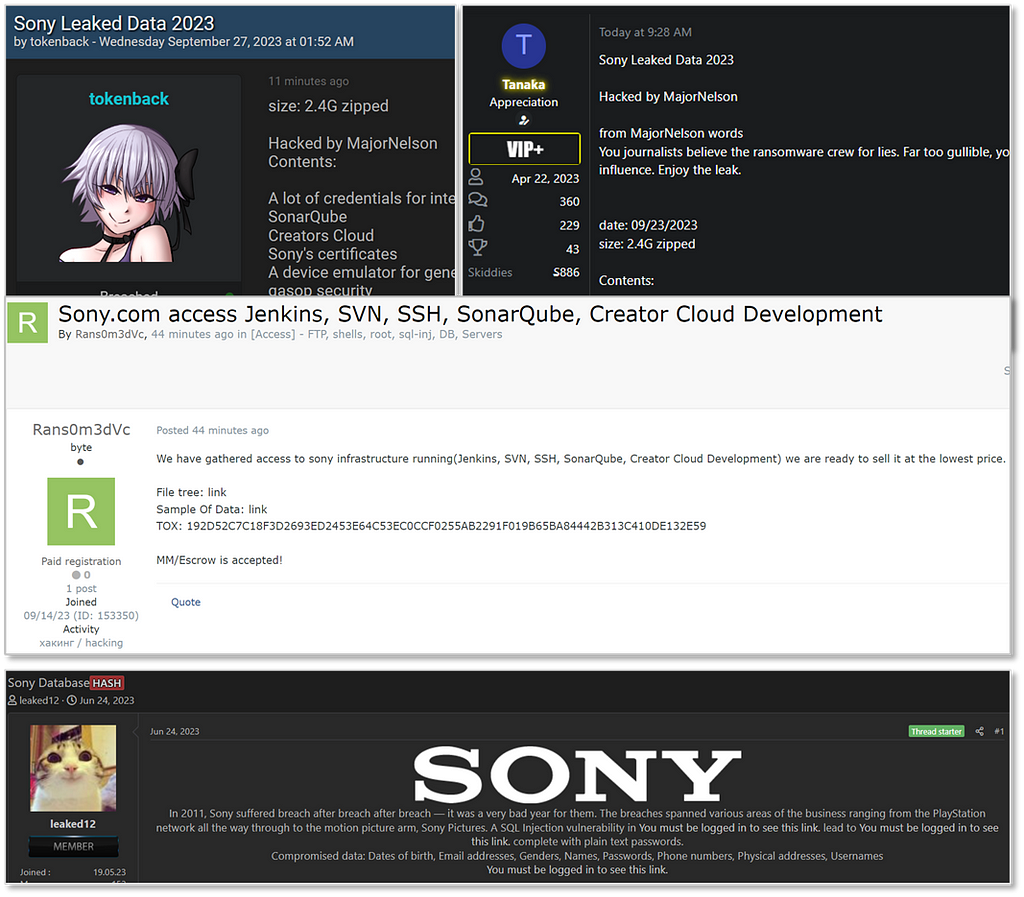 SONY Breach on Darkweb hacking forums
SONY Breach on Darkweb hacking forums- SONY’s internal database has suffered multiple breaches, and data from it is being traded on various dark web hacking forums.
→ Instances of internal network access credentials being leaked include SONY’s Jenkins, SVN, and SSH, which were offered for sale on a Russian hacking forum known as XSS.
→ There have been incidents of internal document leaks, including platform source code and internal documents, which were sold on the global hacking forum, BreachFourms.
→ Ransomware incidents resulting in internal document leaks occurred in June and September of this year, attributed to different ransomware groups.
Gaming Industry: NINTENDO
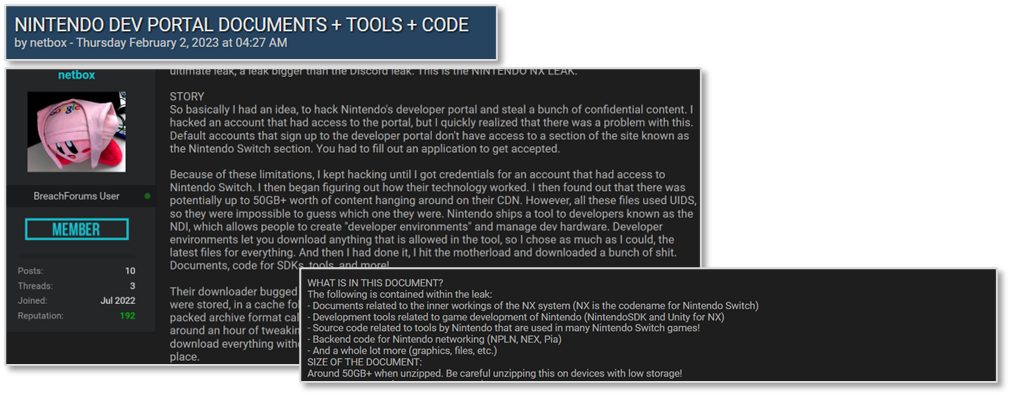 NINTENDO Breach on Darkweb hacking forums
NINTENDO Breach on Darkweb hacking forums- In February of the past year, data related to the portable gaming console ‘NINTENDO SWITCH’ by NINTENDO was freely posted on a global hacking forum.
- The leaked data, which amounted to approximately 50GB, included source code, game development tools, graphic files, and various internal documents of the affected company.
- The threat actor admitted to seizing the developer accounts of the affected company and gaining access to the developer portal to extract internal data.
Automotive Industry: TOYOTA
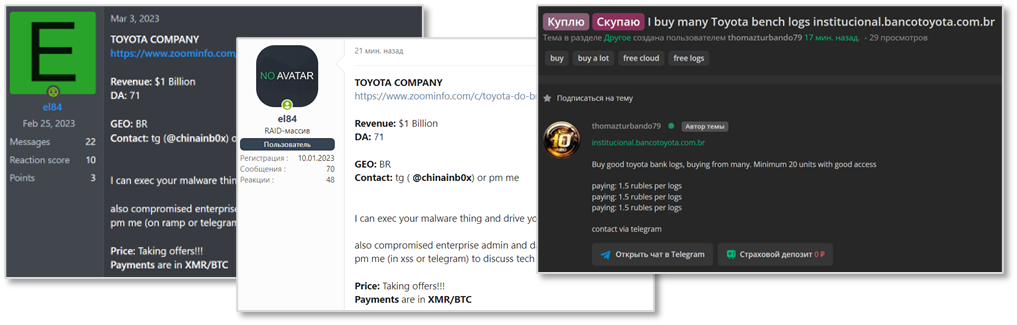 TOYOTA Breach on Darkweb Hacking Forum
TOYOTA Breach on Darkweb Hacking Forum- In March of last year, postings offering internal network access credentials for TOYOTA’s Brazilian branch were made on two dark web hacking forums, namely RAMP and XSS, both under the username ‘el84.’ This threat actor, operating as an ‘IAB’ (Initial Access Broker), is known for selling corporate accounts compromised by ransomware gangs on various hacking forums.
- In July, a user on a dark web hacking forum was observed seeking to purchase logs for accessing the internal network of ‘BANCO TOYOTA,’ a company providing services, including loans and leases to customers purchasing TOYOTA vehicles.
Ransomware Analysis
Ransomware damage comparision with neighboring countries
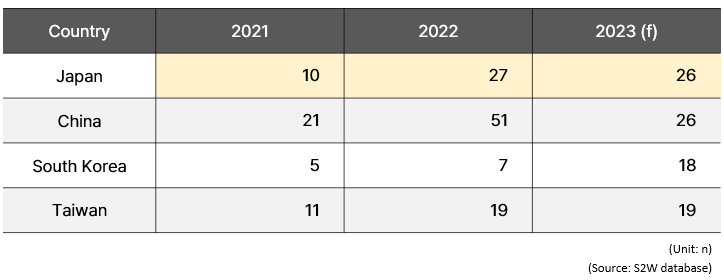
- Recently, the activities of ransomware gangs have seen a modest overall decrease compared to the previous year. However, attacks on major global corporations and government agencies persist, and ransomware attacks targeting Japan continue to be observed.
- This year, ransomware incidents affecting Japanese businesses and institutions have shown a higher level of activity in comparison to neighboring countries.
Analysis of affected industries and gang’s activity share
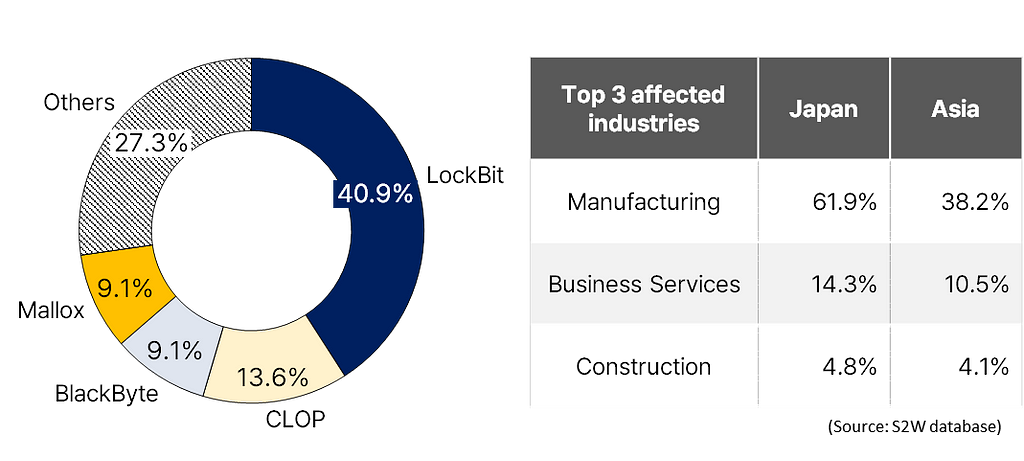
- The ransomware gang that has inflicted the most significant ransomware damage in Japan is ‘LockBit.’

Ransomware attack: SONY
June) CLOP attacks SONY
- ’SONY’ has experienced ransomware incidents along with ‘PWC’ and ‘EY.’ These incidents were attributed to the exploitation of the ‘MOVEit’ vulnerability by the ‘CLOP’ ransomware group.
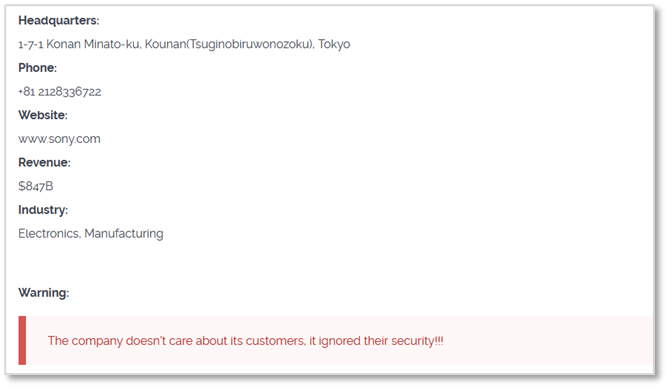 CLOP’s operating Darkweb blog
CLOP’s operating Darkweb blogSeptember) RansomedVC attacks SONY
- A new gang called ‘RansomedVC’ has compromised data from ‘SONY’ and uploaded it to a dark web ransomware blog.
- Just hours before the ransomware group posted the data, a user with a highly similar ID to the ransomware group’s name, ‘Rans0m3dVc,’ was observed on the dark web hacking forum ‘Exploit.’ This user was selling various sources that could provide access to the internal networks of targeted companies (refer to Figure 1 for details).
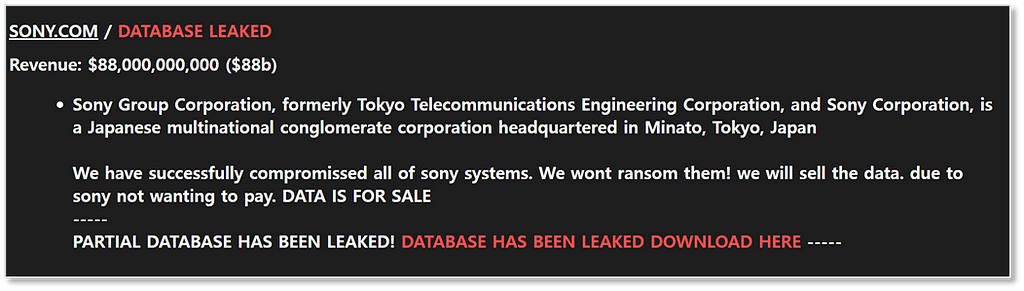
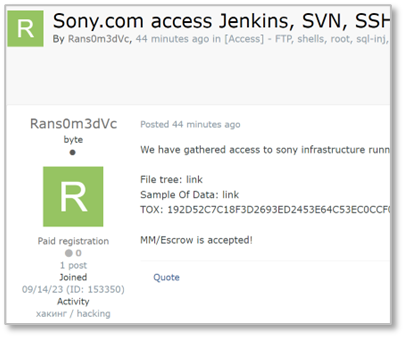 (Left) RansomedVC operating Darkweb blog / (Right) Figure 1
(Left) RansomedVC operating Darkweb blog / (Right) Figure 1Ransomware attack: YKK
June) LockBit attacks YKK
- The U.S. branch of the Japanese clothing zipper manufacturer ‘YKK’ fell victim to a cyberattack by the ransomware group ‘LockBit.’
- The ransomware group only uploaded the name of the affected company, ‘YKK,’ to their list and did not publicly share any samples.
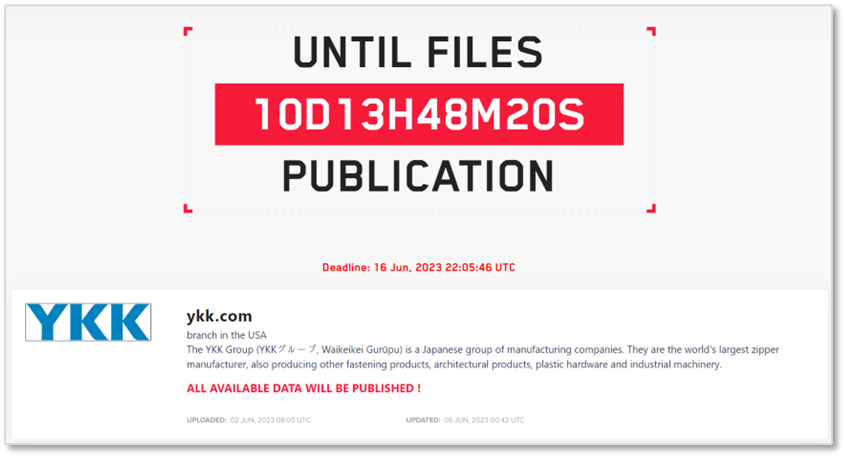 LockBit’s operating Darkweb blog
LockBit’s operating Darkweb blogRansomware attack: SEIKO
August) Alphv/BlackCat attacks SEIKO
- The ‘Seiko Group’ experienced a ransomware attack from the ‘Alphv/BlackCat’ ransomware group, resulting in the leakage of internal data.
- The gang uploaded samples, including credentials for accessing the victim company’s internal domain and internal document screenshots.
- The victim company’s official website contains posts related to this hacking incident. According to the content of the posts, an unauthorized intrusion into Seiko’s internal domain was confirmed in July, and in August, a post indicated that internal assets were stolen through this breach.
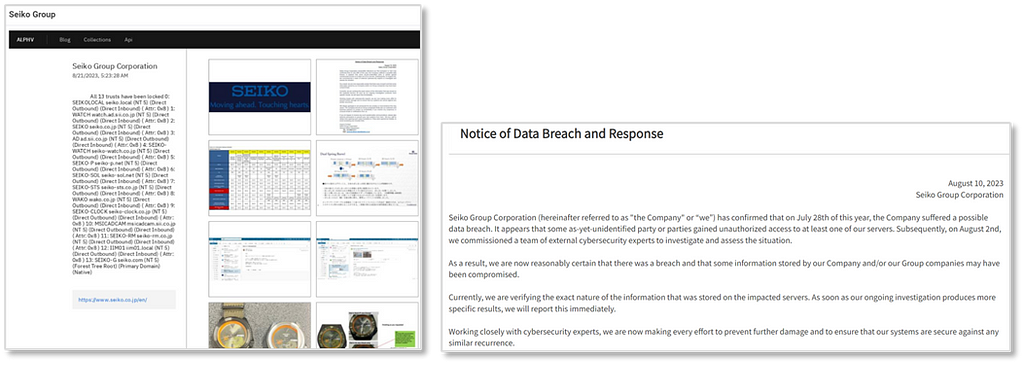 Alphv/BlackCat’s operating Darkweb blog
Alphv/BlackCat’s operating Darkweb blogTelegram Analysis
Cyber Threat content targeting Japan in Telegram Channels
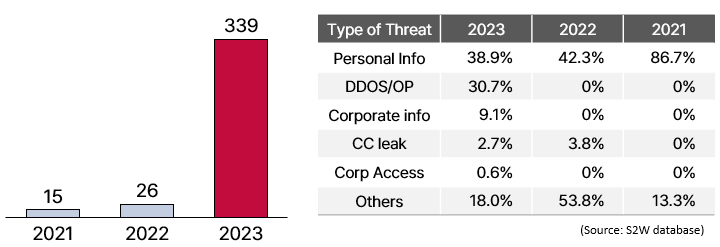 (Left) Yearly trend targeting Japan / (Right) Type of threat targeting Japan
(Left) Yearly trend targeting Japan / (Right) Type of threat targeting Japan- This year, there has been a significant surge in cyber threat messages targeting Japan within Telegram, with a predominant focus on exposing the personal information of Japanese citizens.
- Threat-actor collectives active on Telegram have shown a new pattern of hacking attempts (DDoS/OP) against Japanese businesses and government agencies this year. The volume of these attempts has notably increased, and the content of each message often contains highly risky elements.
Messages sharing/selling personal information and corporate data
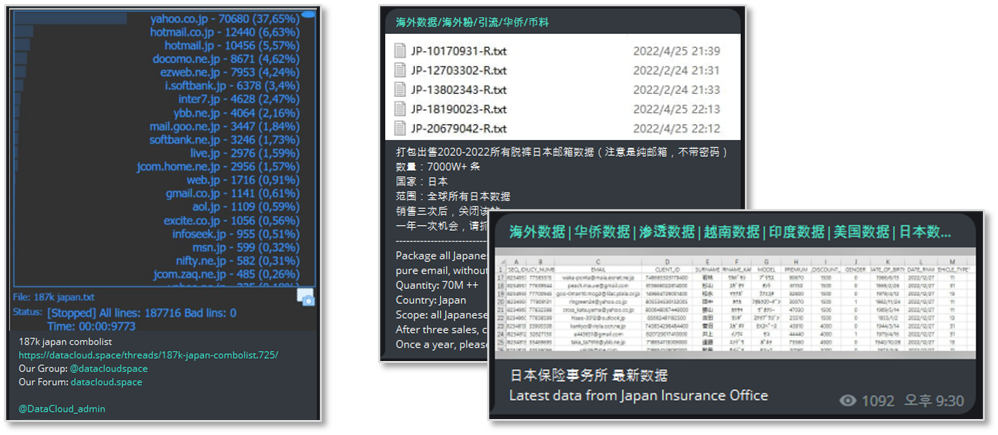 Messages targeting Japanese citizens and corporate information
Messages targeting Japanese citizens and corporate information- A significant portion of personal information leaks in Japan comprises “Combolists,” which are typically available for direct download on Telegram channels or through separate URLs.
Emergence of DDOS/OP attacks
- The Emergence of Hacktivist Groups Targeting Japan
→ Hacktivist groups, combining “hack” and “activist,” conduct cyberattacks against countries opposing their political beliefs, often using “OP” (Operation) as a keyword when targeting specific nations.
- Instances of Hacktivism Targeting Japan
→ In February this year, the Russian-based ‘NoName057(16)’ hacktivist group launched DDOS attacks against Japanese government agencies, financial institutions, gaming companies, and electronics manufacturers in response to Japan’s support for Ukraine during the Russian-Ukraine war.
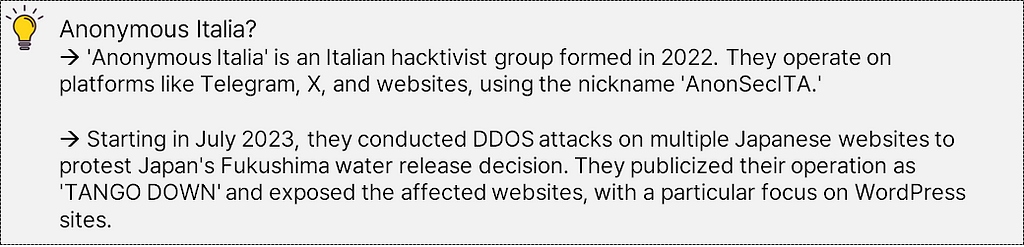
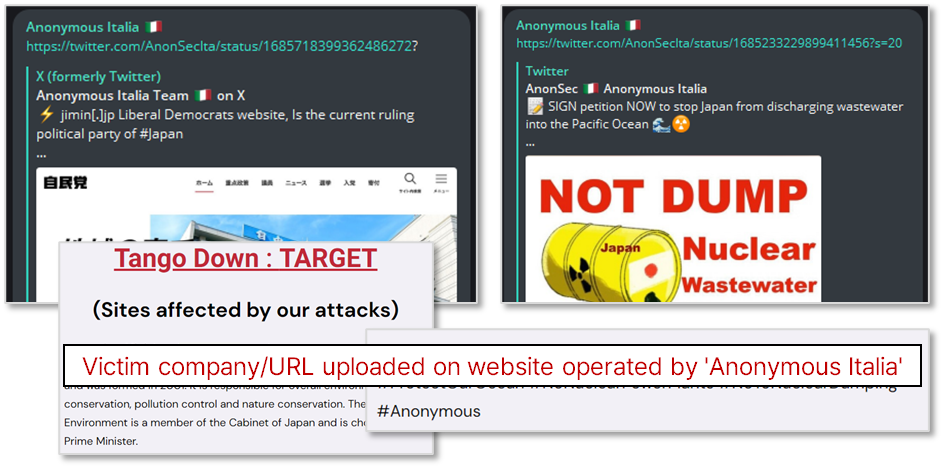
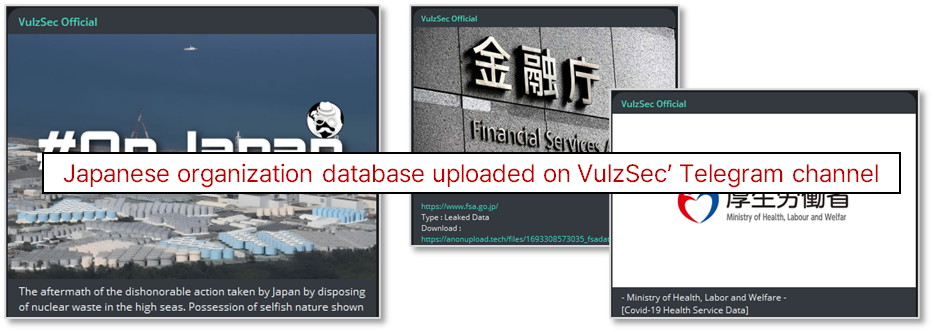
→ Groups like ‘Anonymous Italia’ and ‘VulzSec Official’ carried out DDOS attacks on Japanese business websites and government agencies to protest Japan’s decision to release Fukushima-contaminated water, sharing stolen data from major institutions.
→ Other hacktivist groups, such as ‘Hacktivist of Garuda’ and ‘Ganosec Team,’ supported these views by sharing messages from ‘Anonymous Italia’ and ‘VulzSec Official’ on their Telegram channels.
Monthly trends in DDOS/OP cyberattacks
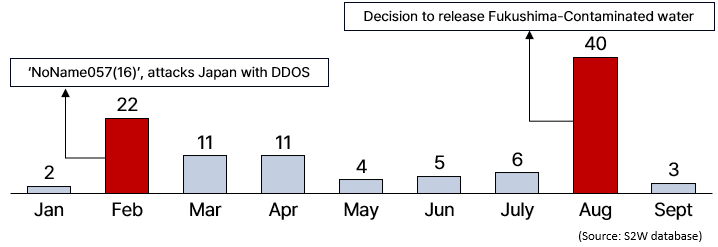 Monthly trends targeting Japan with DDOS/OP cyberattacks
Monthly trends targeting Japan with DDOS/OP cyberattacksJan) Japan expressed support for Ukraine during the Russo-Ukraine war
- January 27th, the Japanese Prime Minister’s office expressed support for Ukraine via ‘X’ (formerly known as Twitter).
- February 13th, the group ‘NoName057(16)’ launched its first Distributed Denial of Service (DDOS) attack on Japan.
Aug) Decision to release contaminated water from Fukushima
- ’Anonymous Italia’ initiated DDOS attacks opposing the decision to release contaminated water in late July. In August, ‘VulzSec,’ ‘Hacktivist of Garuda,’ and others joined in these DDOS attacks.
Threat Actors operating on Telegram
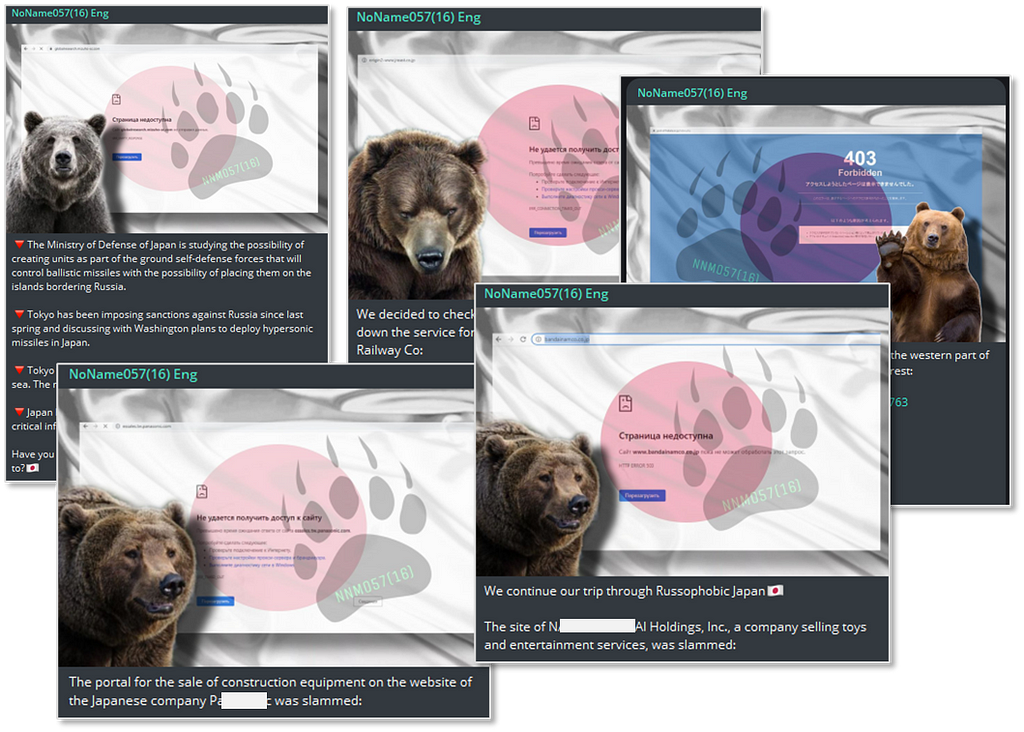
Threat Actor: NoName057(16)

- ‘NoName057(16)’ has carried out highly disruptive DDoS attacks on the websites of the Japanese electronics manufacturer ‘PANASONIC’ and the major gaming company ‘BANDAI NAMCO,’ rendering them inoperable.
- Additionally, ‘NoName057(16)’ has conducted cyberattacks on railway reservation websites and the website for Hakata Station.
Threat Actor: Anonymous Italia
Threat Actor: VulzSec
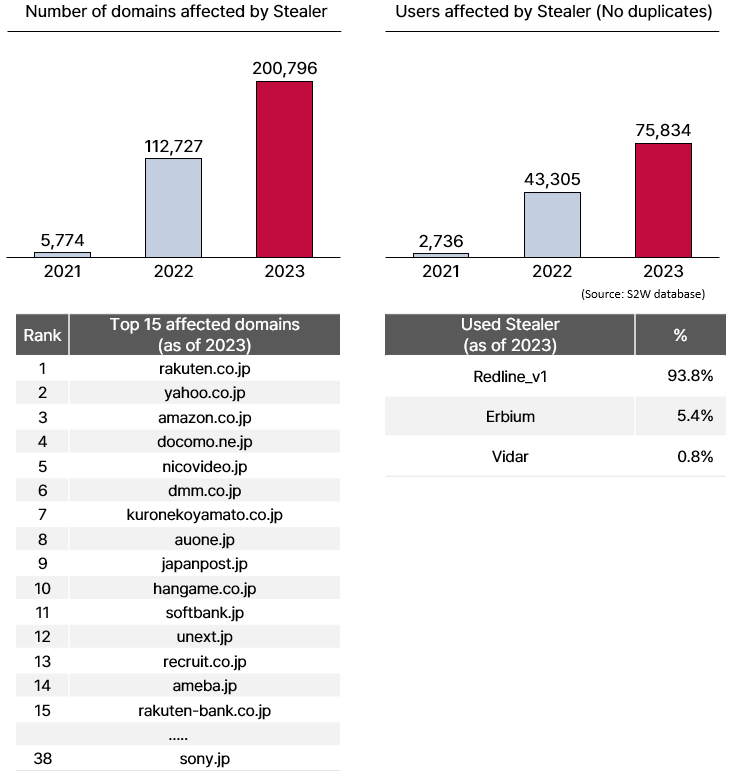
[Appendix] Credential Leak by Stealer
[Regional Analysis_OCTOBER] Dark Web Cyber-attacks targeting Japan (English ver.) was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: [Regional Analysis_OCTOBER] Dark Web Cyber-attacks targeting Japan (English ver.) | by S2W | S2W BLOG | Medium