Author: Kyunghee Kim, Jiho Kim and Huiseong Yang | S2W TALON
Last Modified: Apr 9, 2024
 Photo by Billy Huynh on Unsplash
Photo by Billy Huynh on UnsplashExecutive Summary
- In this report, S2W TALON examined the trends of ransomware groups active in 2023 identifying the operational characteristics of each group and describing them from 5 perspectives:
— Activity: The number of victim organizations uploaded to ransomware leak sites increased by 1.6 times in 2023 compared to 2022. 50% of the victim organizations uploaded to leak sites in 2023 were affected by the top 5 ransomware groups with high activity.
— Influence: The number of attacks on specific industries such as the non-profit sector and government increased. Also, ransomware groups that target big organizations with a particularly high percentage have been identified.
— Brand Continuity: 26 groups updated their ransomware versions during 2023. 18 ransomware groups were identified as having possibly rebranded by changing their brand names.
— Extensibility: Ransomware groups operate with a systematized division of roles for organizational operation and infrastructure expansion. They build their main infrastructure on the dark web.
— Vulnerability: At least 13 ransomware groups use vulnerabilities in their attacks. - S2W has set a total of 21 ransomware evaluation metrics by subdividing the above 5 perspectives, and the details of specific evaluation metrics can be found in Chapter 1. Additive Metric and Chapter 2. Subtractive Metric.
— Additive Metric: Activity, Influence, Brand Continuity, Extensibility, Vulnerability
— Subtractive Metric: Availability of decryption tools, Use of publicly available source code or builders, Whether internal resources were revealed, Whether the ransomware group’s infrastructure was taken down - Top 5 ransomware groups by risk score:
— Before applying Subtractive Metric: LockBit, BlackCat, CLOP, BlackBasta, Nokoyawa
— After applying Subtractive Metric: CLOP, BlackBasta, Nokoyawa, Qilin, BlackByte - The ransomware groups are clustered into 6 groups based on the risk score clustering results.
— Destructive, Self Management Expert, Offensive, Follower, Rookie, Enigma. - This report can be used to proactively identify the attack methods used by high-risk ransomware groups and prevent damage.
- The metrics can be further tailored to each organization’s specific interests and industry characteristics to assess which ransomware groups pose the greatest threat, and this is expected to aid in proactive attack prevention.
The analysis subjects of this report are ransomware groups with ransomware leak sites, victim organizations and organizations uploaded to the leak sites, and Extortion-type groups that only perform data exfiltration without using ransomware.
1. Ransomware Threatscape in 2023
- Throughout 2023, 4,245 organizations fell victim to ransomware attacks and had the fact that they were attacked posted on leak sites. This represents a 60% increase compared to 2022.
- In 2023, 72 ransomware groups were identified as operating leak sites where they exposed exfiltrated data. The 5 ransomware groups with the highest number of victimized organizations are as follows:
— LockBit(1,004), BlackCat(402), CLOP(374), PLAY(288), 8Base(203) - New ransomware groups can be categorized into those operating Leak sites and groups utilizing the source code or builder of existing ransomware groups.
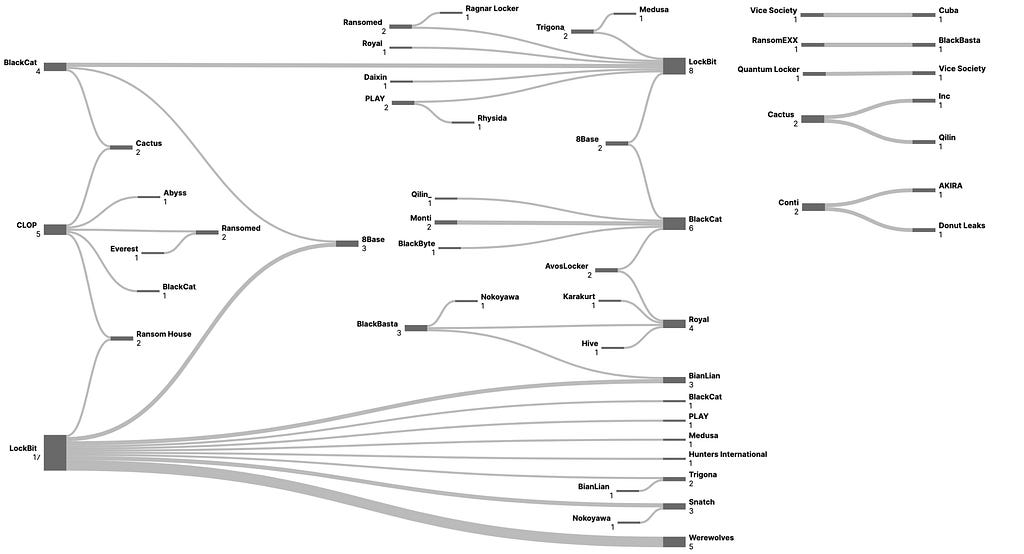
— During the second half of 2023, 18 new ransomware groups with Leak sites were discovered. Among them, 5 groups had their Leak site addresses changed, and 2 groups were confirmed to have ceased operations. - During 2023, a total of 57 duplicate victims were publicly disclosed.
— Among these, LockBit was identified as the group exhibiting the most proactive attack patterns against the same victims. - In 2023, the top 5 countries most affected by ransomware attacks were:
— Top 5 HQ: United States of America(2,049), United Kingdom(290), Canada(209), Germany(152), France(136)
— Ransomware groups tend to target countries with higher GDPs and a larger number of big organizations when considering the victim country’s economic power and the number of large organizations by country. - In 2023, the top 5 industries most affected by ransomware attacks were:
— Top 5 Industry: Manufacturing(746), Business Services(458), Retail(336), Construction(318), Education(246)
— The top 5 industries with the highest losses all fall within the high-revenue industries surveyed by BankRate in 2023, suggesting that ransomware groups tend to target industries with larger revenue streams. - A classification of organizations affected by ransomware in 2023 based on revenue revealed that small organizations suffered the most, followed by medium-sized enterprises and big organizations.
— Ransomware groups with a high success rate in targeting big organizations are assessed as likely to be collaborating with technically skilled Pentesters or Affiliates.
— Top 5 Ransomware groups with the most disclosed attacks against big organizations: CLOP(118), LockBit(58), BlackCat(40), BlackBasta(14), AKIRA(9) - Among the 72 ransomware groups active in 2023, at least 26 groups were observed to have updated and enhanced their ransomware versions.
— BlackCat was identified as the group with the most version updates. - A total of 18 ransomware groups were identified as having rebranded or showing potential for rebranding in 2023. The reasons for rebranding observed by S2W are as follows:
— Improve Brand Image, Evolve TTPs, Collaborate with others, Disbanding Group - Approximately 84% of active ransomware groups in 2023 operated leak sites on the dark web.
— There has been a recent increase in the use of social media platforms like Telegram and Clearnet domains. - At least 13 ransomware groups were identified as exploiting vulnerabilities throughout 2023.
- Of these groups, approximately 47% utilized remote code execution (RCE) vulnerabilities to gain internal access to corporate networks.
The detailed ransomware trends for the first and second half of 2023, as disclosed by S2W, can be found below.
- Story of H1 2023: Statistical Insights into Ransomware Trends and Impact on Victims
- Story of H1 2023: In-depth Examination of Notable Ransomware Groups and Key Issues
- Story of H2 2023: Statistical Insights into Ransomware Trends and Impact on Victims
- Story of H2 2023: In-depth Examination of Notable Ransomware Groups and Key Issues
2. Ransomware Risk Assessment
This chapter defines the risk assessment criteria developed by S2W for ransomware groups. These criteria are based on the quantitative and qualitative trends that emerged in 2023. We will also present the results of clustering ransomware groups with similar characteristics based on risk scores.
To evaluate ransomware groups, we developed risk metrics. Scores are assigned based on the severity of each metric, with higher scores indicating greater risk. Based on their total score, we then categorize ransomware groups into 4 risk levels. The detailed criteria for this categorization are shown in Table 1.
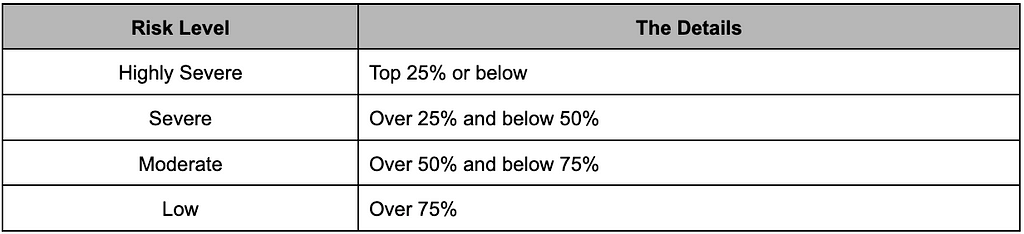 Table 1. Risk level classification criteria
Table 1. Risk level classification criteria2.1. Additive Metric
The metrics that increase the risk of a ransomware group are categorized into 5 perspectives: Activity, Influence, Brand Continuity, Extensibility, and Vulnerability.
2.1.1. Activity
The risk of ransomware groups was assessed based on their activity levels on leak sites, identifying duplicate victims targeted by multiple groups and the types of groups that uploaded duplicate targets. The detailed metrics are presented in Table 2.
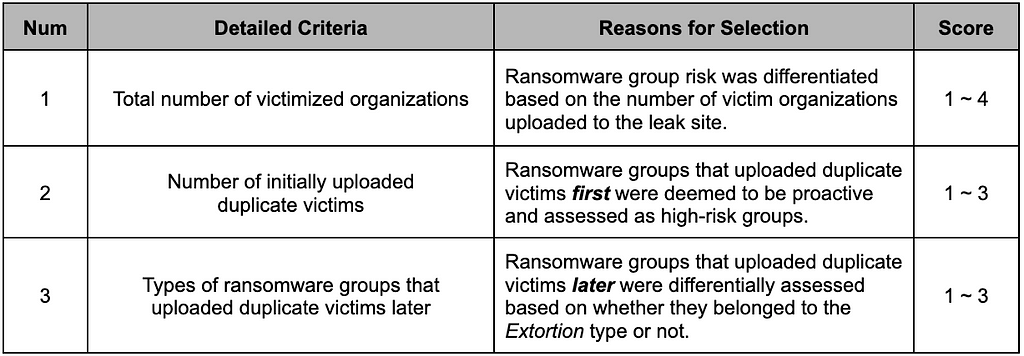 Table 2. Activity Metric
Table 2. Activity Metric2.1.2. Influence
We analyzed the damage status by industry group and enterprise size of the affected organizations to evaluate the impact of the ransomware group on specific industries. Additionally, the proficiency of each group was evaluated based on the number of successful attacks against big organizations. These factors were combined to create the “Influence” metric, as detailed in Table 3.
S2W defined critical industries as non-profit organizations (Education, Medical, Welfare, Culture, Environmental Organizations) and Government agencies
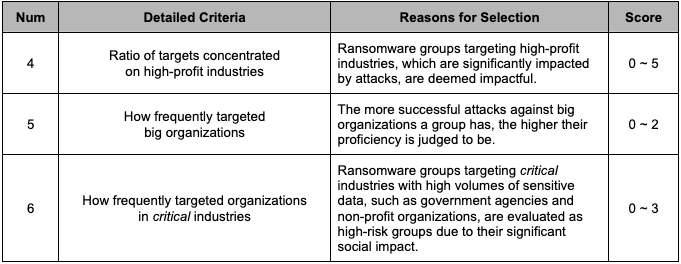 Table 3. Influence Metric
Table 3. Influence Metric2.1.3. Brand Continuity
We assessed the risk level of ransomware groups with the “Brand Continuity” metric such as ransomware binary updates, expansion of the target environment, rebranding history, and active period. The detailed criteria are shown in Table 4.
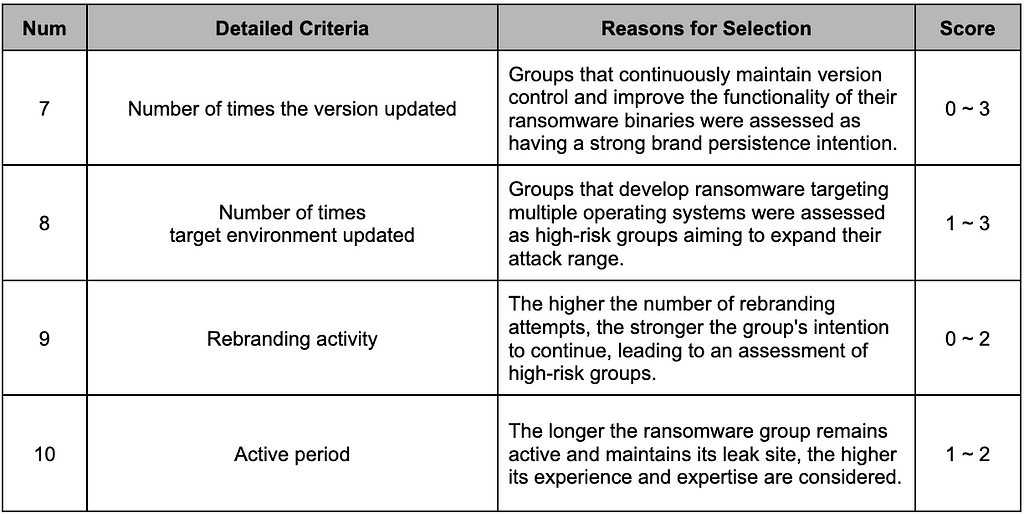 Table 4. Brand Continuity Metric
Table 4. Brand Continuity Metric2.1.4. Extensibility
To evaluate the “Extensibility” of ransomware groups, we analyzed their activities and infrastructure on the dark web, considering their collaboration with various groups. It also includes how they use their own tools and if they keep up the infrastructure for effective attacks and managing victims. The detailed criteria are presented in Table 5.
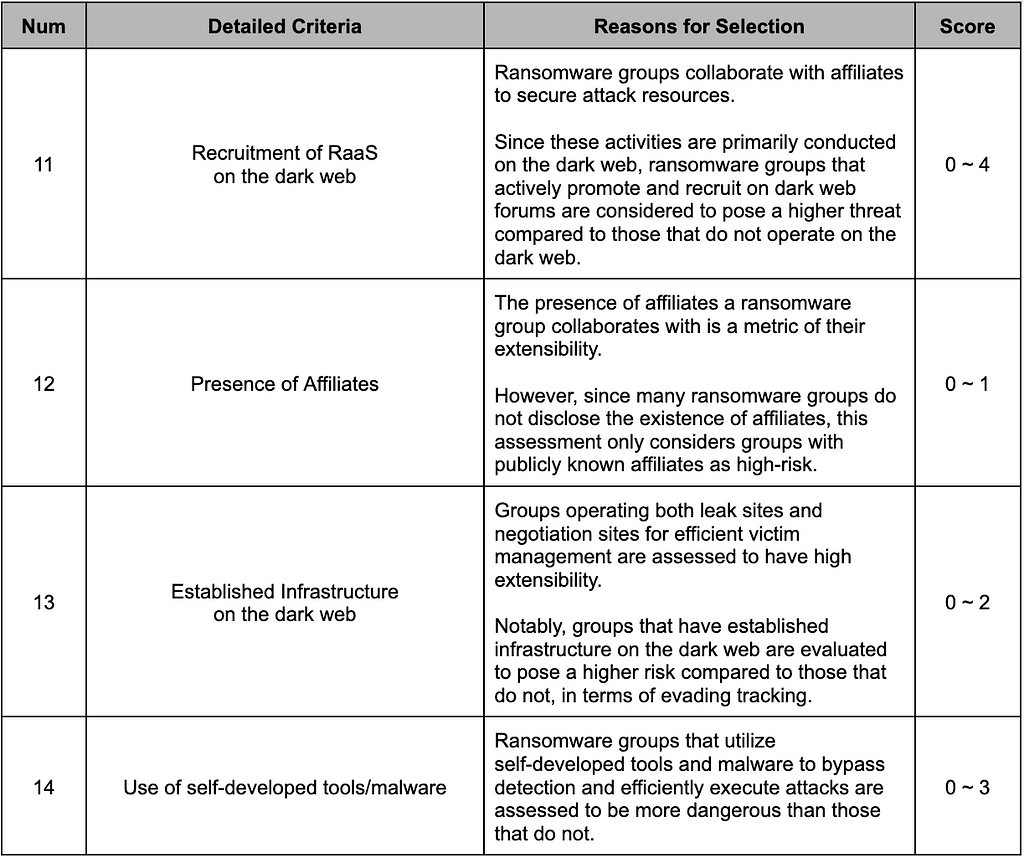 Table 5. Extensibility Metric
Table 5. Extensibility Metric2.1.5. Vulnerability
The risk of ransomware groups was assessed based on their vulnerability exploitation capabilities and the impact of the vulnerabilities they exploited, using the “Vulnerability” metric. The detailed criteria are shown in Table 6.
EPSS(Exploit Prediction Scoring System) is a data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild.
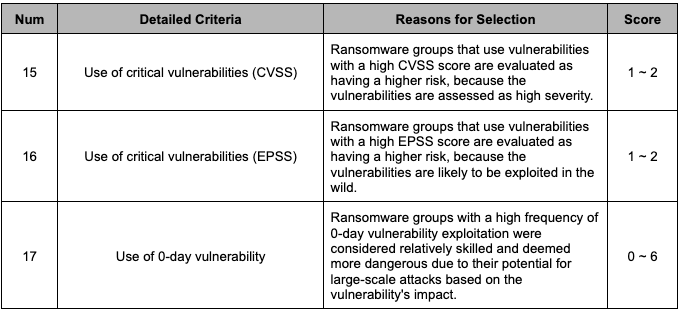 Table 6. Vulnerability Metric
Table 6. Vulnerability Metric2.2. Subtractive Metric
In contrast to the aforementioned Additive Metric, there exist metrics that lower the risk posed by ransomware groups. These specific criteria are detailed in Table 7.
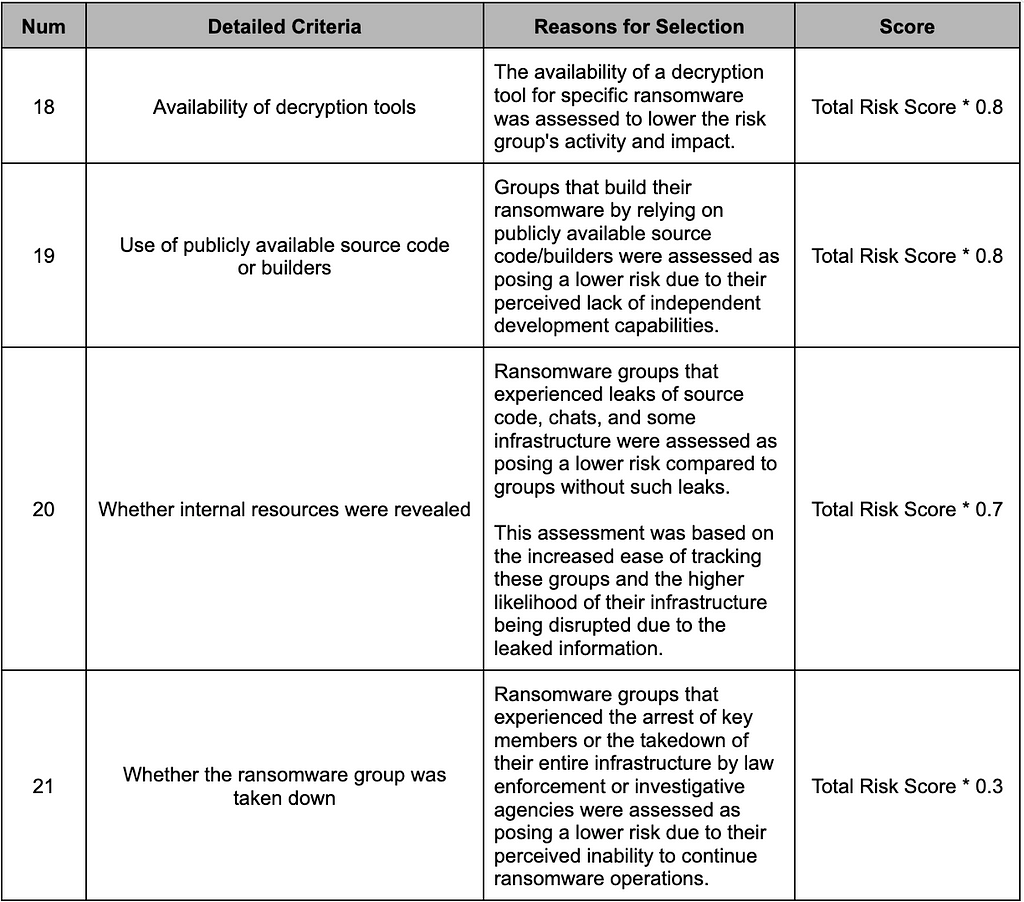 Table 7. Subtractive Metric
Table 7. Subtractive Metric2.3. Evaluation of Ransomware Groups’ Risk Level
To determine the impact the subtractive metrics have on measuring the risk of ransomware groups, S2W divided the risk of ransomware groups according to whether the subtractive metric was applied or not.
2.3.1. Risk measurement results before applying subtractive metrics
The top 5 ransomware groups with the highest scores without applying subtractive metrics were LockBit, BlackCat, CLOP, BlackBasta, and Nokoyawa.
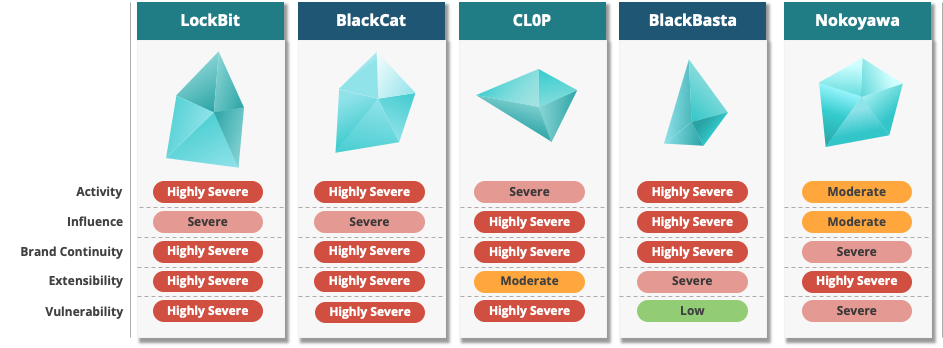 Figure 1. Top 5 groups with the highest combined risk metric values (before applying the subtractive metrics)
Figure 1. Top 5 groups with the highest combined risk metric values (before applying the subtractive metrics)The LockBit group, which had the highest total score, was classified as Highly Severe for all metrics except the Influence metric, which was classified as Severe.
According to the Affiliate Rules mentioned on their leak site, the LockBit group is prohibited from attacking industries categorized as “Critical Infrastructure,” which suggests that the group’s influence in this particular industry may be relatively small compared to other groups.
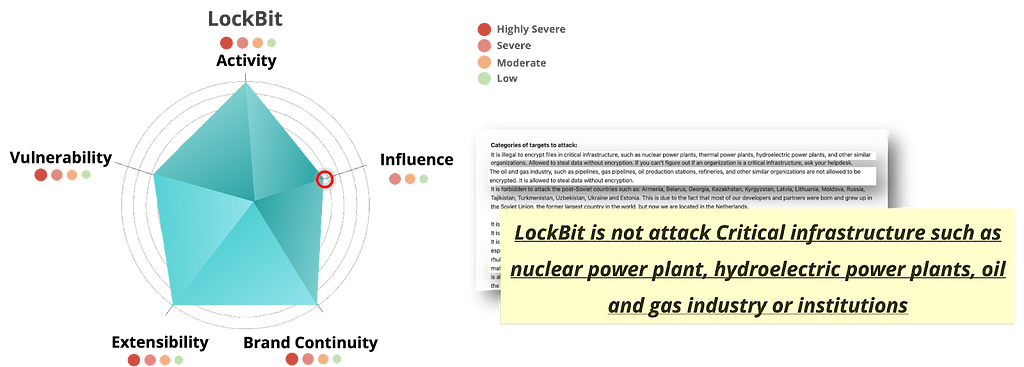 Figure 2. LockBit Group’s risk assessment results
Figure 2. LockBit Group’s risk assessment resultsLike LockBit, the BlackCat group was classified as severe only in the Influence metric and highly severe in all other metrics.
In Particular, the BlackCat scored very high in the Activity metric. To increase the likelihood that victims would pay the ransom, the group employed blackmail tactics that leveraged the U.S. Securities and Exchange Commission’s (SEC) rule that requires data disclosure on a specific form (1.05 of Form 8-K) within 4 business days about a cyberattack.
It is highly unusual for a ransomware group to abuse policy and publicly pressure a victim organization on a leak-site, suggesting that the BlackCat group is a very clever and sophisticated group of strategists.
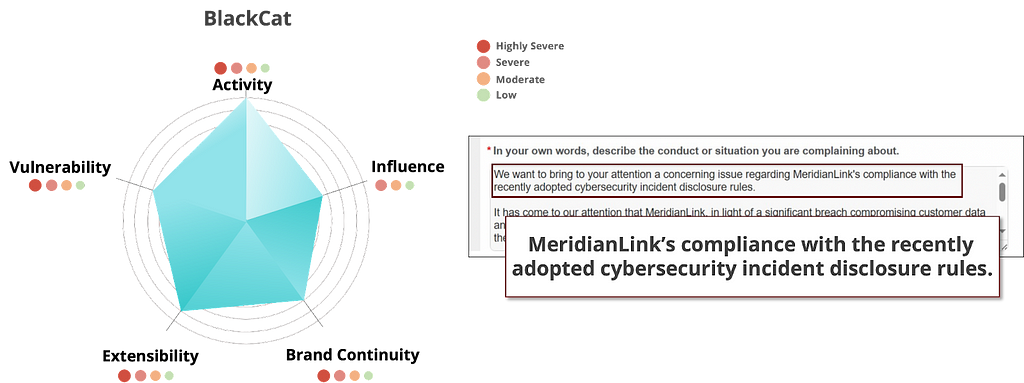 Figure 3. BlackCat Group risk assessment results
Figure 3. BlackCat Group risk assessment resultsThe CLOP group was categorized as highly severe in the Influence, Brand Continuity, and Vulnerability metrics and severe in the Activity metric.
In particular, the CLOP group has a history of exploiting various high-impact 0-day vulnerabilities and tends to generate a large number of victims in a short period of time after exploiting the vulnerability, followed by a relatively low level of activity on its leak sites during other periods.
This raises the possibility that the CLOP group spends time developing 0-day vulnerabilities. However, the CLOP group has no strong presence on the dark web or Telegram, so the extensibility metric is Moderate.
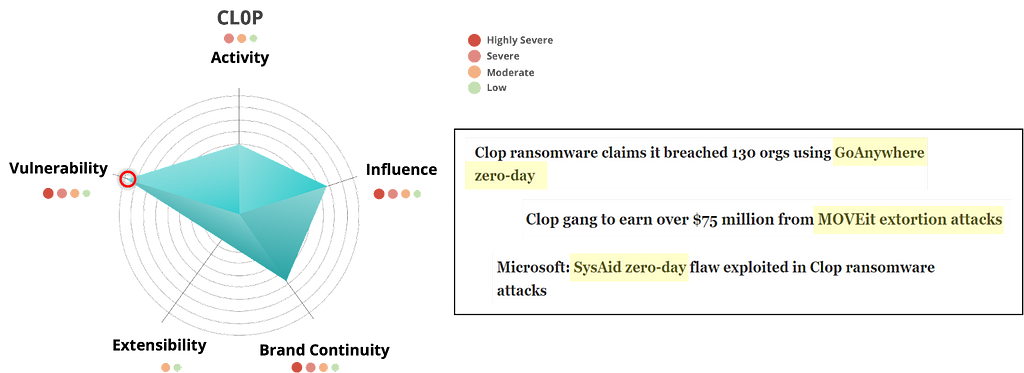 Figure 4. CLOP group risk assessment results
Figure 4. CLOP group risk assessment resultsThe BlackBasta group has a Low vulnerability metric due to the lack of 0-day vulnerabilities or exploits against products with large numbers of users.
However, the group has a high percentage of attacks against big organizations and major industries, which suggests that the BlackBasta group may have highly skilled pen-testers who can infiltrate the internal networks of big organizations or may be working with affiliates.
The Nokoyawa group is one of the groups that scored strongly on the vulnerability metric, but it also scored highly on the extensibility metric and was categorized as Highly Severe because its operators are active on the dark web and have publicly listed affiliates.
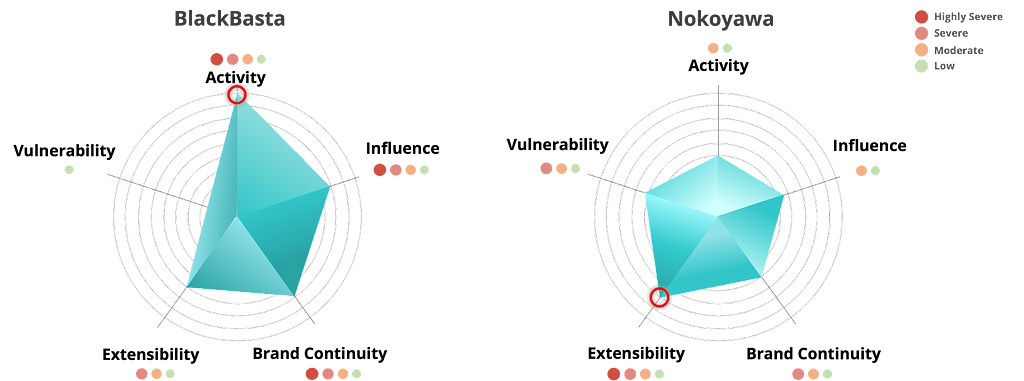 Figure 5. Risk assessment results of BlackBasta and Nokoyawa Group
Figure 5. Risk assessment results of BlackBasta and Nokoyawa Group2.3.2. Risk measurement results after applying subtractive metrics
After applying the subtractive metrics, the LockBit and BlackCat groups, which were in the top 5 groups with the highest scores, were downgraded due to the deduction of points for infrastructure breaches, and the Qilin and BlackByte groups were newly ranked in the top 5 groups.
Figure 6 shows the risk levels of each of the top 5 groups, as redefined after the subtractive metrics are applied.
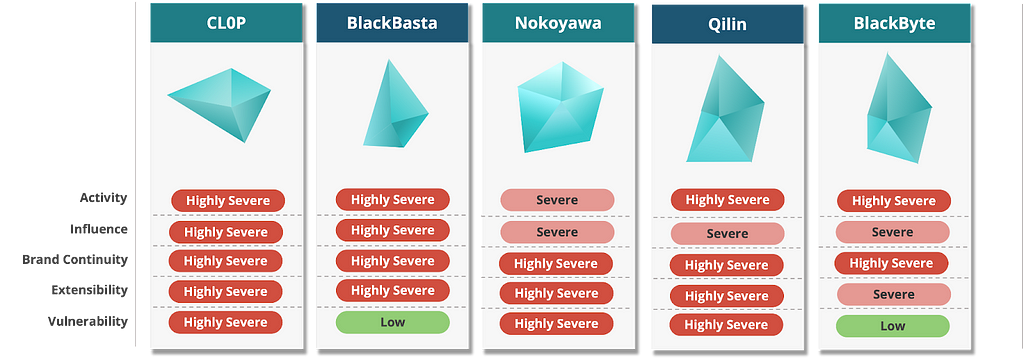 Figure 6. Top 5 groups with high risk metric sum values (after applying subtractive metrics)
Figure 6. Top 5 groups with high risk metric sum values (after applying subtractive metrics)Of the original top 5 groups, CLOP, BlackBasta, and Nokoyawa did not have any deduction factors, so they remained in the top group even after the subtractive metric was applied.
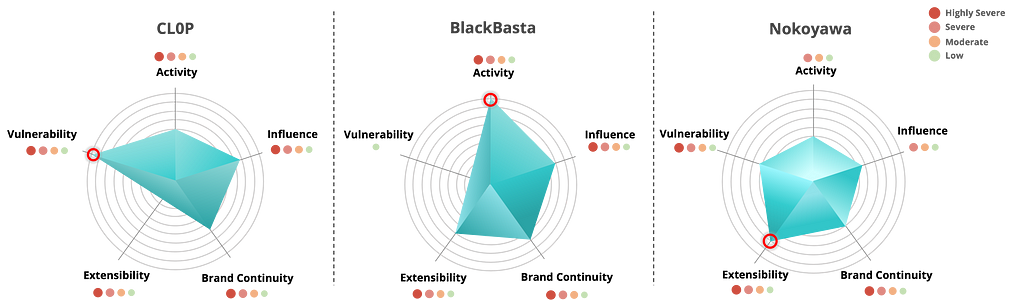 Figure 7. Top 3 groups with the highest combined risk metric values (after applying subtractive metrics)
Figure 7. Top 3 groups with the highest combined risk metric values (after applying subtractive metrics)Qilin Group scored Highly Severe in the Extensibility and Brand Continuity metrics. To maintain brand continuity, they are actively promoting their RaaS program on the dark web and using ransomware that targets Linux operating systems in addition to Windows.
 Figure 8. Qilin Group risk assessment results
Figure 8. Qilin Group risk assessment resultsThe BlackByte group performs strongly on activity volume and brand continuity metrics, especially given that the group has been updating versions of its ransomware and improving its functionality using different programming languages such as C#, C++, and the Go language since its first discovery in July 2021 until December 2023.
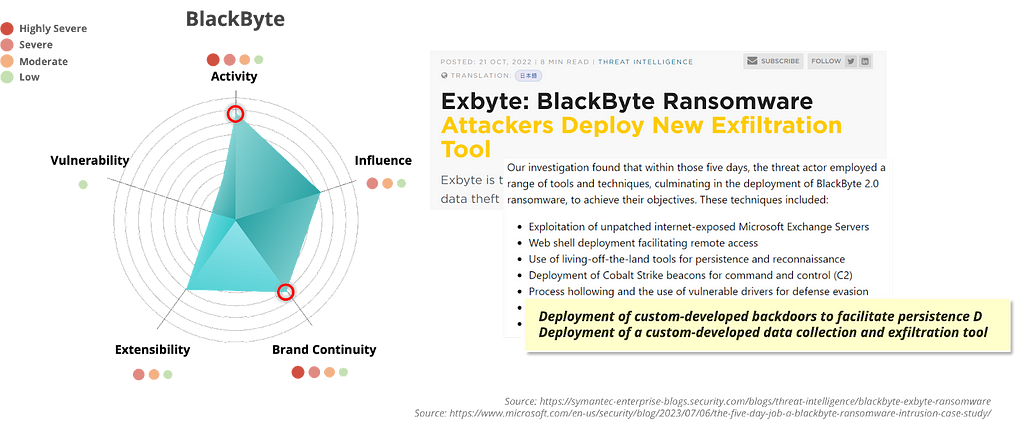 Figure 9. BlackByte Group’s Risk Assessment Results
Figure 9. BlackByte Group’s Risk Assessment ResultsWhile the above is a risk assessment of each group based on ransomware group activities in 2023, there was a major issue with the LockBit group in February 2024 when some of their infrastructure was taken down.
When we calculated the score based on the activity in 2023 before this event, the combined risk metric for the LockBit group was 38.7 out of 50, which is very high. However, after the infrastructure take-down issue in 2024 was factored into the risk measure, the total score decreased to 27.07.
The scoring scheme presented in this report allows us to quantitatively measure the risk of ransomware groups by reflecting changing metrics.
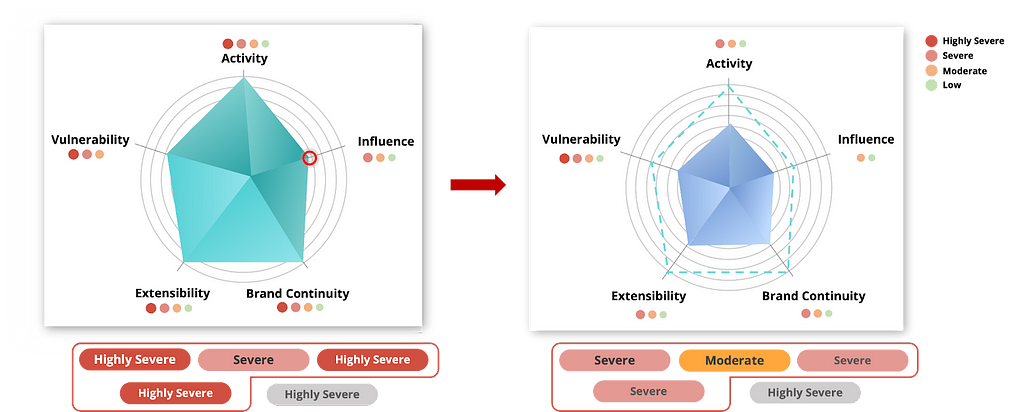 Figure 10. Change in score for the LockBit group’s infrastructure take-down issue.
Figure 10. Change in score for the LockBit group’s infrastructure take-down issue.2.4. Risk-based clustering of groups active in 2023
In addition to measuring the risk of each ransomware group, S2W also worked on clustering ransomware groups with similar characteristics based on the scoring results.
2.4.1. Clustering Ransomware Groups
The Hierarchical Clustering technique based on Ward Distance was used in this process, and the schematic process is shown in Figure 11.
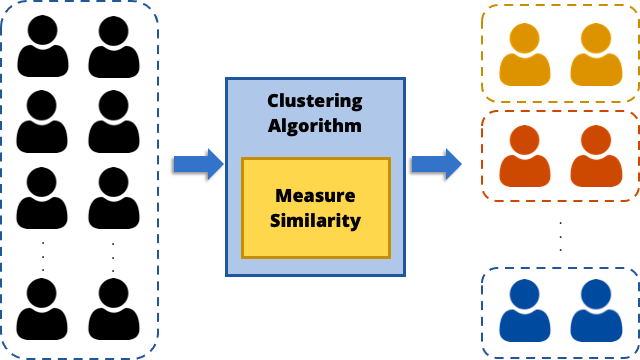 Figure 11. Clustering process
Figure 11. Clustering processUsing the risk metric values of the different ransomware groups, the hierarchical clustering technique was used to evaluate the similarity between each group, and the groups with high similarity were clustered together.
As a result of this clustering process, the 72 ransomware groups were divided into 6 clusters, as shown in Figure 12, and S2W named each cluster Enigma, Follower Group, Rookie Group, Self-Management Expert Group, Destructive Group, and Offensive Group.
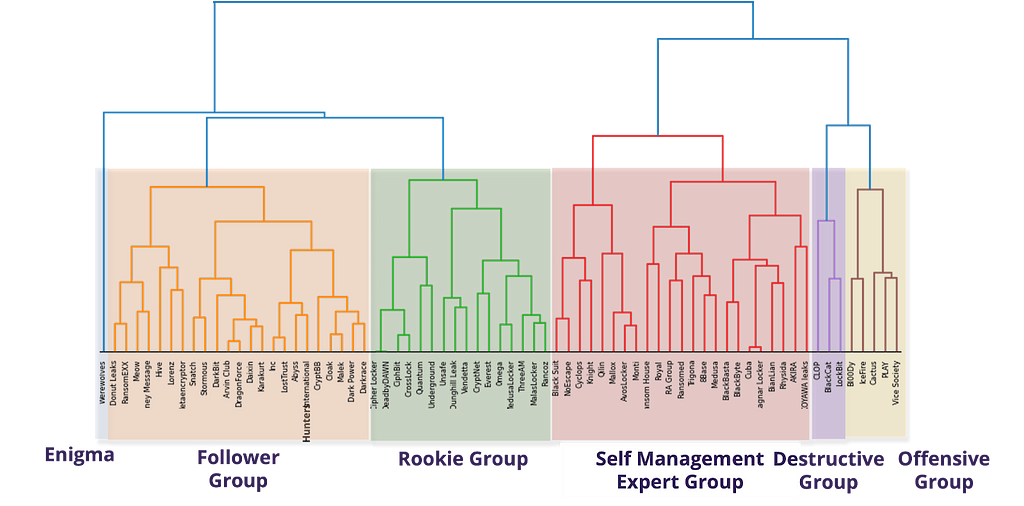 Figure 12. Clustering results of ransomware groups
Figure 12. Clustering results of ransomware groupsWhen the sum of the risk metrics separated the 6 clusters, the Destructive Group ranked highest, while the Rookie Group ranked low in all metrics.
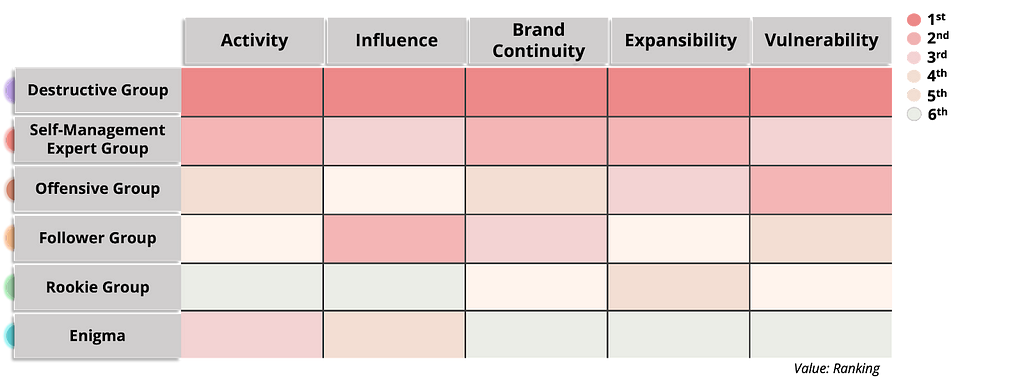 Figure 13. Cluster ranking based on the sum value of risk metrics
Figure 13. Cluster ranking based on the sum value of risk metrics2.4.2. Analysis of Each Clusters
Destructive Group
The Destructive Group, with the highest scores across all metrics, consists exclusively of ransomware groups that have been active for more than 3 years and include CLOP, BlackCat, and LockBit. These are also the ransomware groups that uploaded the most victims to the leak site in 2023, with each group scoring at the Highly Severe level.
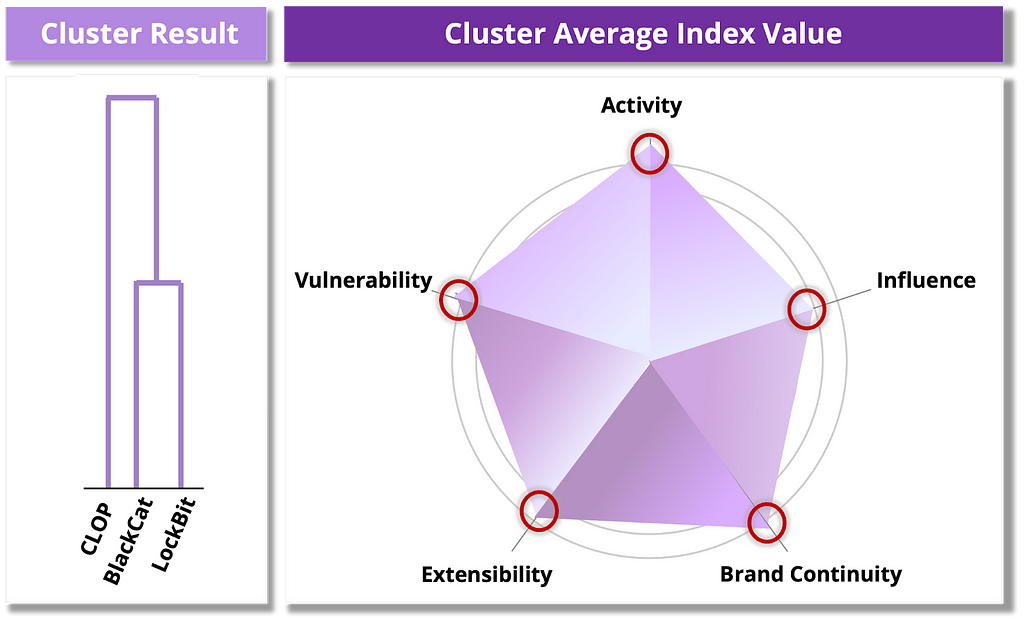 Figure 14. Risk assessment results for the Destructive Group
Figure 14. Risk assessment results for the Destructive GroupSelf Management Expert Group
The Self Management Expert Group consists of 23 strong ransomware groups in the Activity, Extensibility, and Brand Continuity metrics. These groups are characterized by a strong presence on the dark web and various infrastructures besides the dark web, such as Twitter and Telegram. With the exception of the Vulnerability metric, the Self Management Expert Group scores well across all metrics, suggesting it has a high potential to become a Destructive Group.
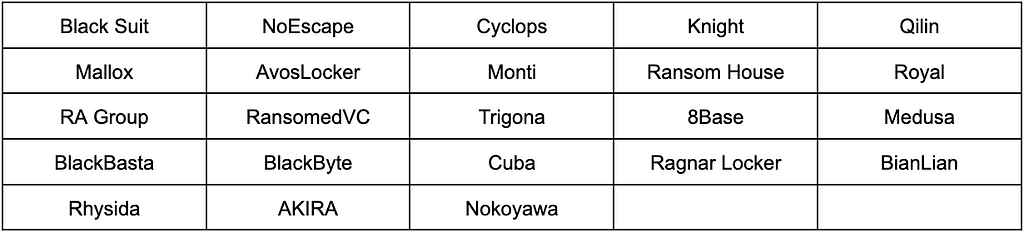 Table 8. Ransomware groups in the Self-Management Expert Group
Table 8. Ransomware groups in the Self-Management Expert Group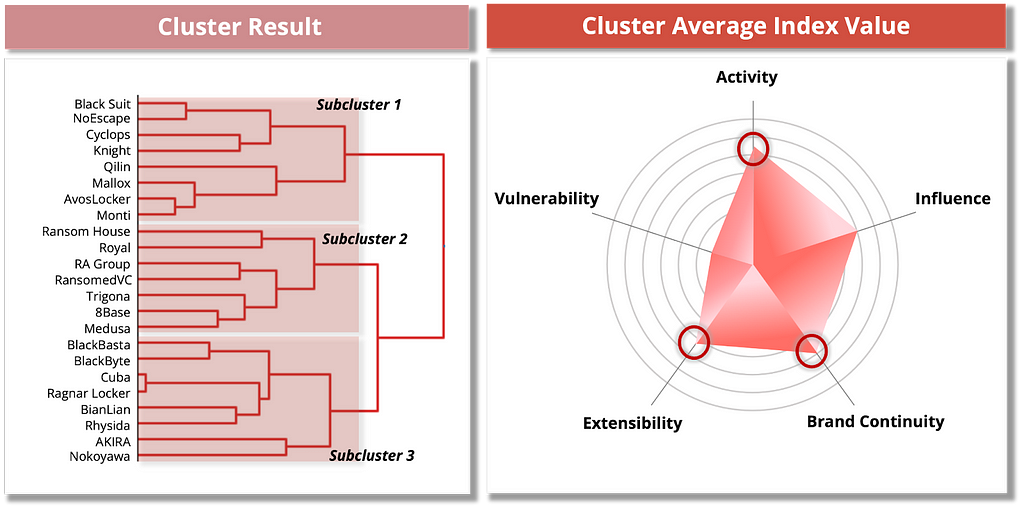 Figure 15. Risk Measure Results of the Self-Management Expert Group
Figure 15. Risk Measure Results of the Self-Management Expert GroupWe further divided the Self Management Expert cluster into subclusters by examining the groups that clustered first with similar overall numbers. We subsequently analyzed them as depicted in Figure 16. An interesting finding is that ransomware groups that are rebranding or have been previously associated tend to be in the same subcluster.
- Rebranding Groups: Royal — BlackSuit / Cyclops — Knight
- Existing Association with Conti: BlackBasta, BlackByte, AKIRA
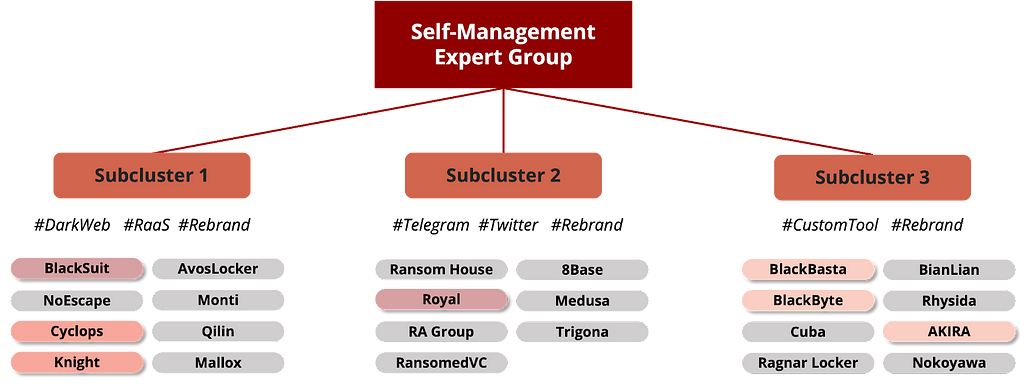 Figure 16. Ransomware groups with known associations (Self Management Expert Group)
Figure 16. Ransomware groups with known associations (Self Management Expert Group)Offensive Group
The Offensive Group consists of 5 ransomware groups and shows strength in the Vulnerability metric compared to the other clusters. All ransomware groups in this cluster have a CVSS score of 8.0 or higher, and at least one exploit with an EPSS score of 80% or higher during 2023.
 Table 9. Ransomware groups in the Offensive Group
Table 9. Ransomware groups in the Offensive Group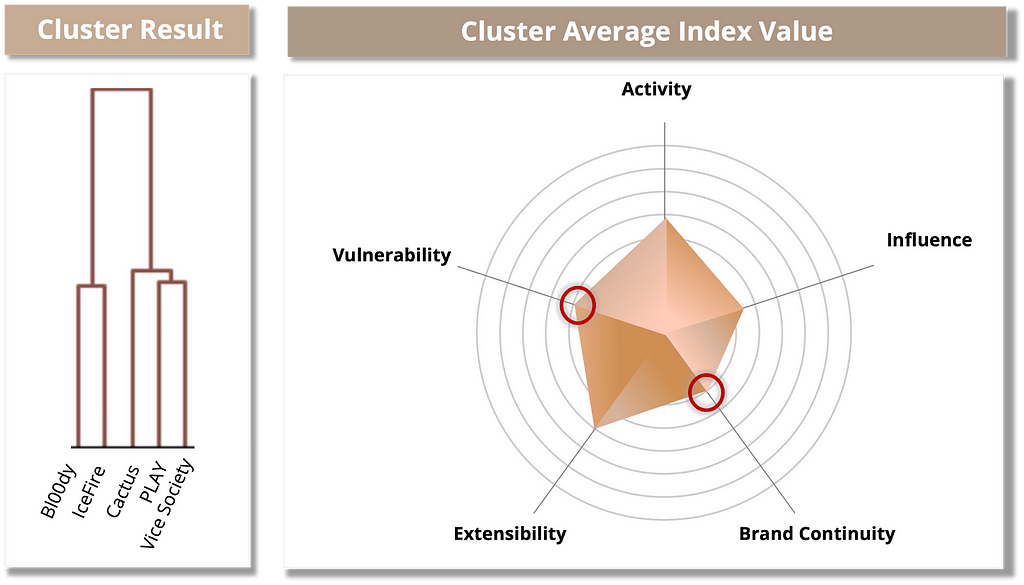 Figure 17. Risk assessment results for the Offensive Group
Figure 17. Risk assessment results for the Offensive GroupFollower Group
The Follower Group consists of 13 ransomware groups. This cluster has a relatively low score in the Activity metric but is strong in the Influence metric due to the high percentage of uploaded victims targeting big organizations and major industries. Furthermore, it was found that the Follower Group includes Extortion-type groups that, instead of using ransomware, primarily resort to data exfiltration to extort affected companies.
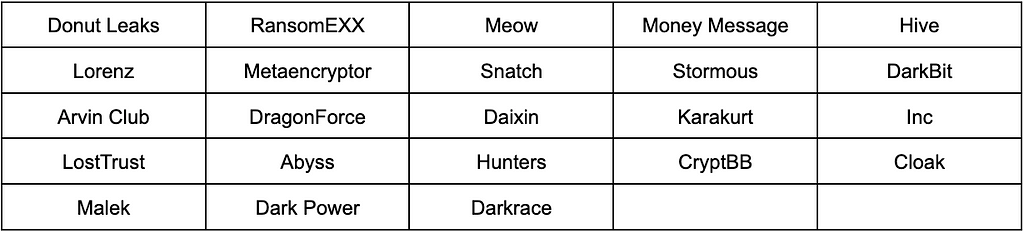 Table 10. Ransomware groups in the Follower Group
Table 10. Ransomware groups in the Follower Group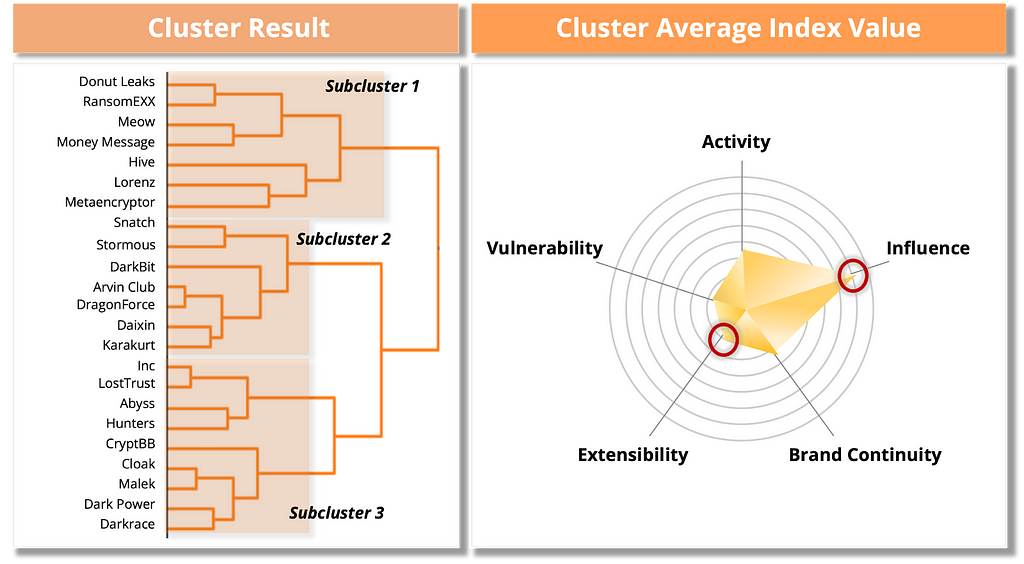 Figure 18. Risk assessment results of the Follower Group
Figure 18. Risk assessment results of the Follower GroupLike the Self Management Expert cluster, the Follower cluster shows similar overall numbers, which led us to separate the first clustered group into subclusters, shown in Figure 19. Ransomware groups with rebranding relationships were also found in the Follower Group.
- Rebranding Groups: Hive-Hunters / LostTrust — Metaencryptor
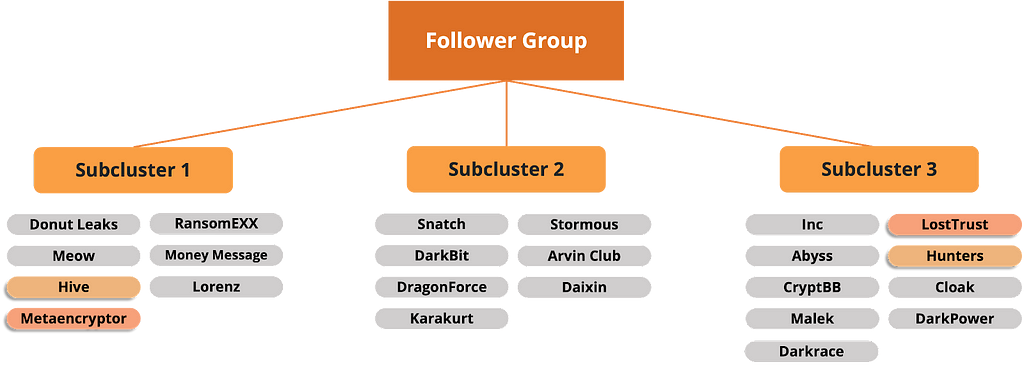 Figure 19. Ransomware groups with known associations (Follower Group)
Figure 19. Ransomware groups with known associations (Follower Group)Rookie Group
The Rookie Group consists of ransomware groups that have been active for a year or less. Some groups have shown little activity on the dark web and leak sites. Everest and CryptNet, identified on dark web forums, score relatively high on Extensibility, but the other ransomware groups do not stand out across all metrics and are considered a potentially dangerous cluster.
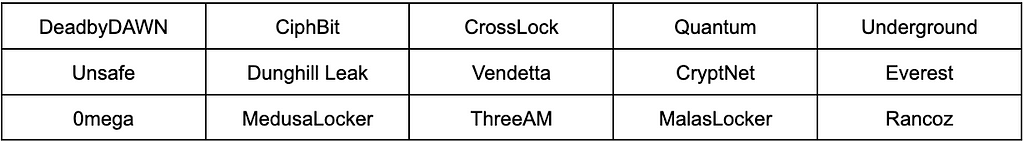 Table 11. Ransomware groups in the Rookie Group
Table 11. Ransomware groups in the Rookie Group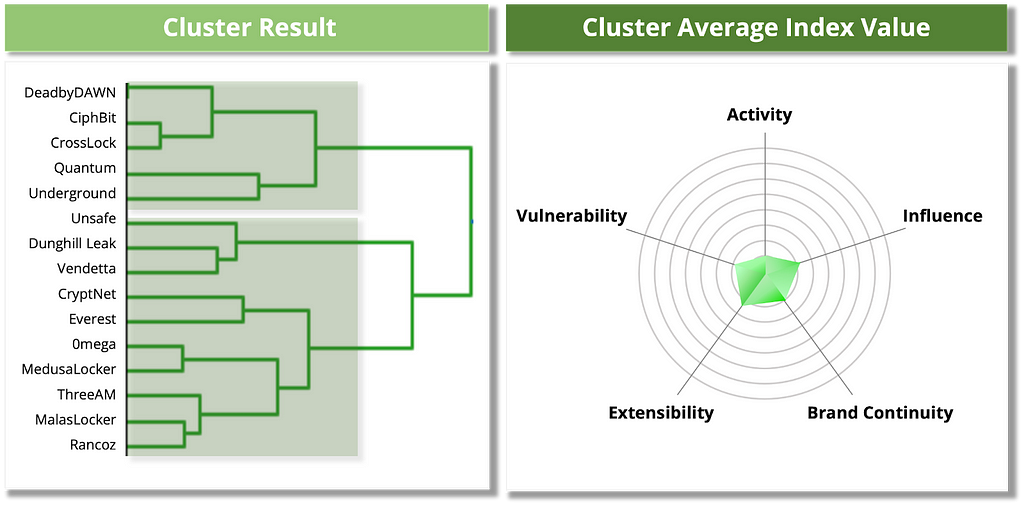 Figure 20. Risk assessment results for the Rookie Group
Figure 20. Risk assessment results for the Rookie GroupEnigma
Finally, Enigma is a cluster composed solely of the Werewolves group, which is unique in its own right. Discovered in the second half of 2023, the Werewolves group has no activity on the dark web, and its leak sites are only deployed on Clearnet. Furthermore, many of the uploaded victims were identified as having a history of uploading from the LockBit group, and unusually, the group uploaded compromises against Russian organizations.
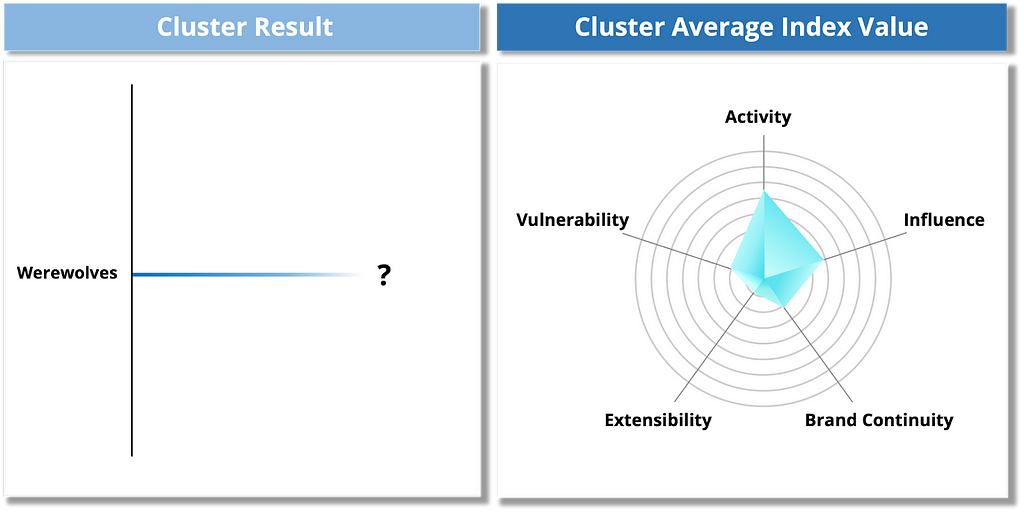 Figure 21. Risk assessment results for Enigma Group
Figure 21. Risk assessment results for Enigma GroupTo determine the most threatening ransomware groups in 2023, we considered both the risk of each ransomware and the clustering results. From the ransomware groups belonging to the top 2 clusters, the Destructive Group and the Self Management Expert Group, we selected the top 3 ransomware groups per group with the highest combined risk metrics.
Figure 22 shows the selected groups. LockBit and BlackCat, even with the subtractive metric applied, still ranked in the top 10 in the combined risk metrics of the ransomware groups, proving that they are still influential ransomware.
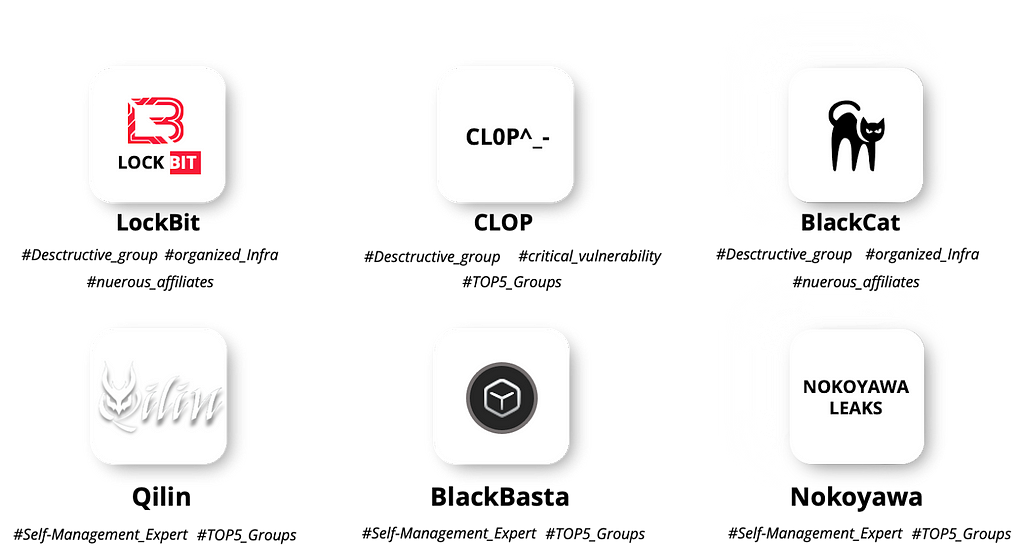 Figure 22. Ransomware groups with the highest risk levels in 2023
Figure 22. Ransomware groups with the highest risk levels in 2023Using this risk scoring scheme, we quantitatively measure the risk of each ransomware group and cluster ransomware with similar characteristics to identify the ransomware groups that pose the greatest threat. The risk scoring system presented in this report is expected to enable rapid and quantitative risk assessment in the future, even as new ransomware groups emerge and their activities change.
Conclusion
1. Results of risk measurement by ransomware group
- We measured the risk of each ransomware group according to the 21 metrics we developed.
- Before applying the subtractive metrics, The top 5 groups with the highest risk levels were as follows.
— Top 5 Groups: LockBit, BlackCat, CLOP, BlackBasta, Nokoyawa - After applying the subtractive metric, the risk of ransomware groups was reassessed, and The top 5 groups were
— Top 5 Groups: CLOP, BlackBasta, Nokoyawa, Qilin, BlackByte
2. Ransomware group clustering results
- We clustered ransomware groups with common characteristics based on the sum of the risk metrics of each ransomware group, and the characteristics of each cluster were as follows
— Destructive Group: The cluster with the highest level of risk across all 5 additive metrics.
— Self Management Expert Group: Clusters active on the dark web and leveraging various infrastructures, including Telegram and Twitter.
— Offensive Group: Clusters with a history of exploiting high-impact vulnerabilities throughout 2023.
— Follower Group: Clusters characterized by a high proportion of targets in large organizations and high-profit industries, including Extortion-type groups to blackmail victims through data breaches.
— Rookie Group: Clusters that have been active for less than a year and have a low activity level on leak sites, indicating a potential risk level.
— Enigma: A cluster independently organized by the Werewolves group and characterized by infrastructure built on Clearnet that targets Russian organizations.
3. Takeaway
- This report can help you proactively recognize the attack methods used by high-risk ransomware groups so you can respond and prevent damage.
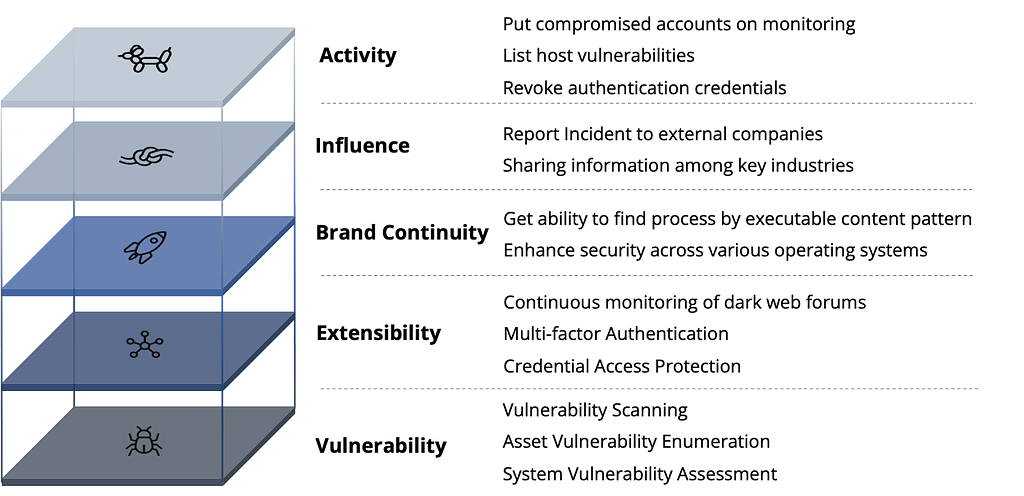
- Mitigations provided by the MITRE Framework, D3FEND, and RE&CT were used to suggest countermeasures for each metric that increases the risk of ransomware groups. Details of the mitigations for each metric are attached in the Appendix. B.
- In the future, the metrics can be adjusted according to the industry and characteristics of each organization to assess which ransomware groups are the most threatening and help prevent attacks in advance.
Appendix. A
Mitigation for metrics that increase the risk of ransomware groups
Appendix. B
Identified duplicate victims uploaded in 2023
Ransomware Resurgence: A Deep Dive into 2023’s Threatscape and Risk Assessment was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Ransomware Resurgence: A Deep Dive into 2023’s Threatscape and Risk Assessment | by S2W | S2W BLOG | Apr, 2024 | Medium