Author: HuiSeong Yang, HyeongJun Kim, SeungHo Lee
Last Modified : Oct 11, 2024
 Photo by Nickolas Nikolic on Unsplash
Photo by Nickolas Nikolic on UnsplashExecutive Summary
This report analyzes ransomware group activities in the first half of 2024 (from January 1 to June 30, 2024). The analysis focuses on ransomware groups operating Leak sites and the companies and institutions uploaded to these sites.
During the first half of 2024, a total of 75 ransomware groups posted information on the infection of 2,260 companies on their Leak sites, marking an increase of 445 affected companies compared to the same period last year. Notably, May saw a 73% increase compared to the same period in 2023, mainly due to the increased activity of LockBit, driven by Operation CRONOS.
- When classifying the companies attacked by ransomware groups based on revenue-based company classifications defined by Gartner, large enterprises accounted for 4% of the total, a decrease from 9.1% in the second half of last year, indicating a lower targeting rate for large corporations.
- When categorizing ransomware victims by country, the United States experienced the highest number of attacks. The U.S. also saw the most significant increase in ransomware incidents compared to 2023, while Türkiye saw the largest decrease in the number of attacks.
- By industry, the Manufacturing sector was the most heavily affected in the first half of 2024. The sector has experienced growth due to increased infrastructure investments and the strengthening of the Semiconductor industry in the U.S., along with the adoption of advanced technologies such as smart factories. This growing sector has thus become a prime target for ransomware attacks.
A total of 51 new ransomware groups were active during the first half of the year, with the largest number of new groups emerging in April, when 16 new groups were identified. These new groups utilized a variety of channels, including the dark web, Telegram, X(formerly Twitter), and clearnet. Some groups were observed using or customizing existing ransomware by purchasing or using leaked source codes and builders from other groups.
Ransomware groups have been actively recruiting through dark web forums and Telegram channels, with a 41.7% increase in recruitment posts compared to the second half of 2023. The number of recruitment posts and comments peaked in March and June 2024, which may be linked to a temporary decrease in ransomware attacks during those months.
Ransomware-related issues in the first half of 2024 were categorized into Version Control, Revealed Connections, Affiliates, Attack Techniques, Activity in Telegram and DDW, and Duplicated Victims.
- Version Control: Version updates were observed in three ransomware families — LockBit, Cerber, and TargetCompany. These updates included changes in programming languages and attempts to target different operating systems.
- Revealed Connections: Several connections were identified between existing and new ransomware groups based on similarities in infrastructure and ransomware code.
- Affiliates: IAB and pentester activities continued among RaaS operators. Some affiliates were identified or migrated to other groups as a result of Operation CRONOS.
- Attack Techniques: Ransomware groups exploited 1-day vulnerabilities in unpatched environments, while Black Basta leveraged 0-day vulnerabilities in its ransomware attacks.
- Activities in DDW & Telegram: Numerous ransomware groups, such as Kryptina and Ransomhub, posted RaaS advertisements on the dark web and Telegram. Large RaaS groups like BlackCat and LockBit had their accounts banned from dark web forums.
- Duplicated Victims: There were 54 cases of duplicated victims. BlackCat led in uploading the first instance of duplicated victims (10 cases), while LockBit had the highest number of secondary uploads (12 cases).
Based on the findings, the S2W Threat Intelligence Center developed an evaluation metric to assess the risk level of ransomware groups based on Activity, Influence, Brand Continuity, Extensibility, and Vulnerability. As a result, the top 5 most dangerous ransomware groups in the first half of 2024 were Black Basta, BlackSuit, Qilin, Ransomhub, and PLAY.
1. Overall Activities of Ransomware Groups in H1 2024
1.1 Activities of Ransomware Groups
In the first half of 2024, we observed 2,260 organizations that ransomware groups victimized. This is a 24.5% increase from the 1,815 organizations impacted by ransomware attacks in the first half of 2023. Figure 1 shows that, when broken down by month from January through June, ransomware activities were more frequent in the first half of 2024 than in the first half of 2023 in all months except March and June. The average number of affected organizations per month increased by 149. Notably, May saw an increase of approximately 73% compared to May in 2023, which we attribute to an increase in activity by LockBit, following the group regaining its infrastructure after it was seized during Operation CRONOS.
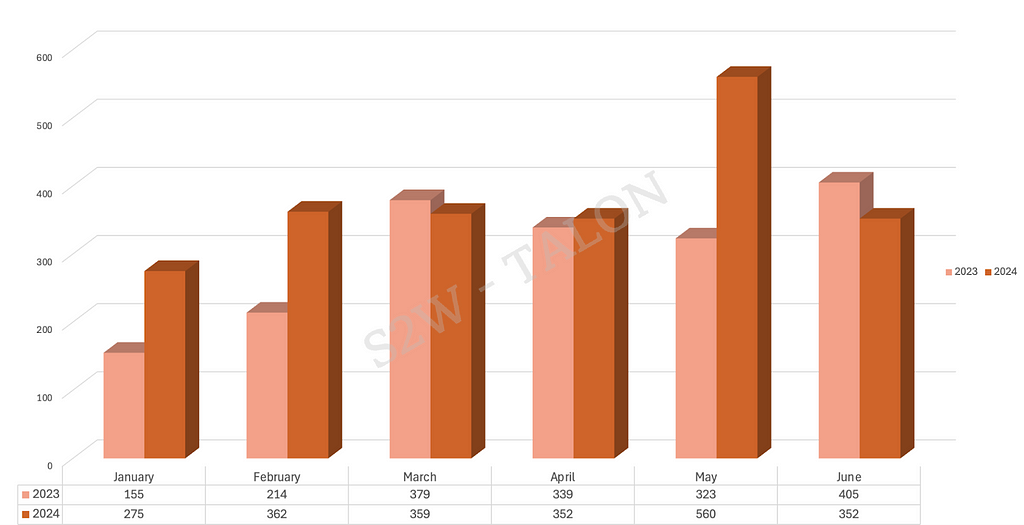 Figure 1. Monthly attack volume in H1 2024 compared to H1 2023
Figure 1. Monthly attack volume in H1 2024 compared to H1 2023Based on our analysis of ransomware groups operating leak sites, we found 75 active ransomware groups in the first half of 2024, with each group attacking an average of about 29 organizations. The top 10 most active ransomware groups accounted for 64.5% of all ransomware attacks in this period, as detailed in Table 1 and Figure 2.
The top 10 ransomware groups by volume attacked an average of 146 organizations in the first half of the year. In comparison, the 66 ransomware groups outside of the top 10 attacked an average of approximately 12 organizations. The attack volume of the top 10 ransomware groups is about 12.2 times higher than the average attack volume of the groups that did not make the top 10, indicating a significant disparity. The spike in the total number of victimized organizations across ransomware groups in the first half of 2024 can be attributed to increased activity from LockBit, as well as a rise in the number of new ransomware groups, with 16 more groups compared to the first half of 2023. Specifically, LockBit’s total ransomware attacks in May 2024 reached 180, higher than any other ransomware group in the first half of 2024, including the second-highest group, PLAY. LockBit’s attacks in the first half of 2024 were about three times higher than those of the PLAY group, highlighting LockBit’s notable activity. For information on new ransomware groups in the first half of 2024, refer to Section 2.1.1.
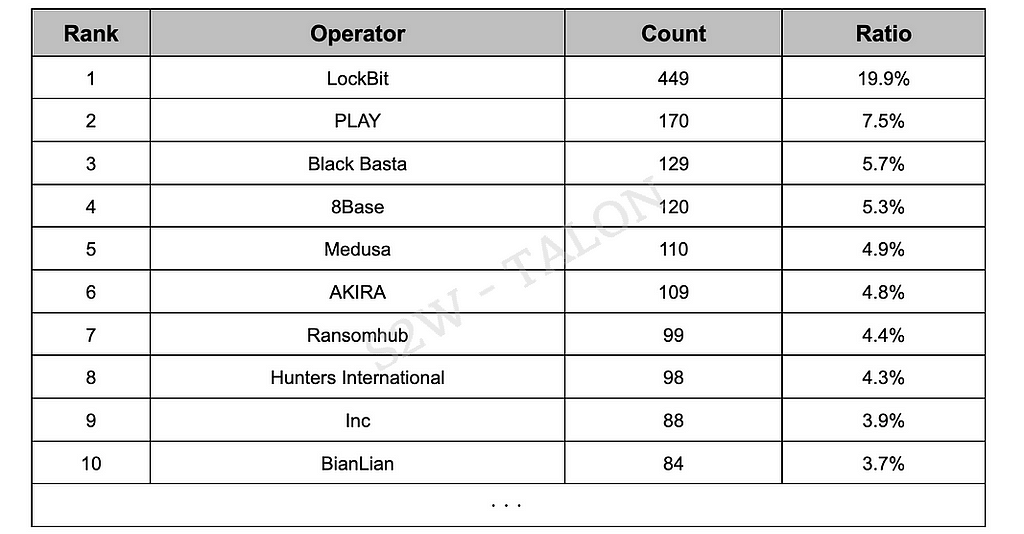 Table 1. Top 10 Ransomware Group Attacks
Table 1. Top 10 Ransomware Group Attacks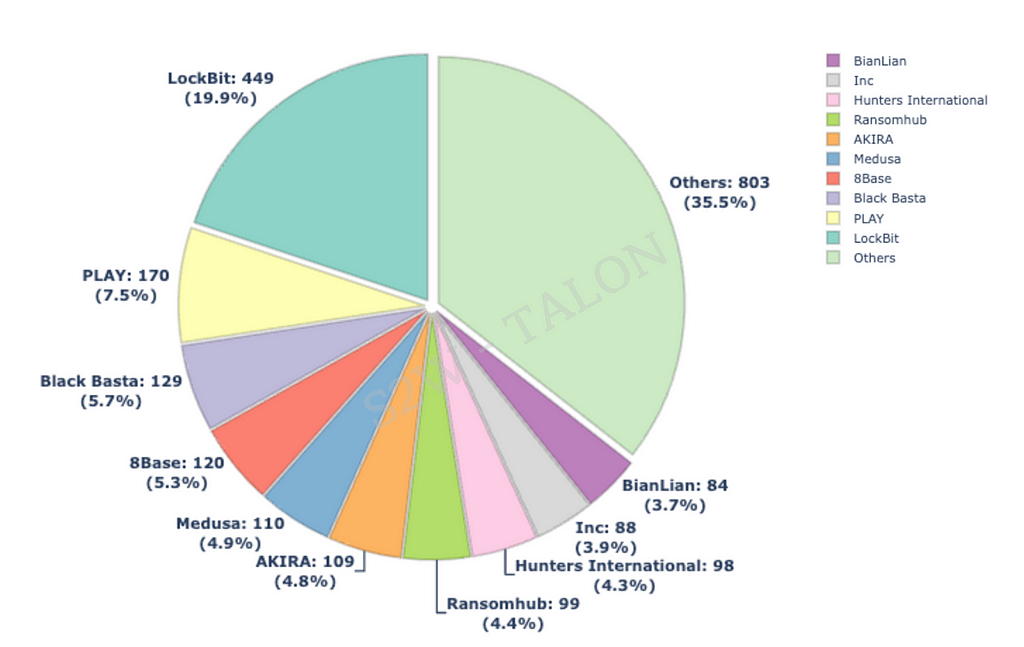 Figure 2. Ransomware group attack volume graph for the first half of 2024.
Figure 2. Ransomware group attack volume graph for the first half of 2024.1.2 Targeted Victim Country
The top 10 countries victimized by ransomware account for 81.1% of all victimized countries. These top 10 include five countries in Europe, three in the Americas, one in Oceania, and one in Asia, indicating that Europe and the Americas are the most frequently targeted by ransomware. Compared to 2023, the Netherlands was less often affected, while India, the only Asian country in the top 10, saw an increase in ransomware attacks. All 10 countries rank within the top 15 or lower in GDP, indicating that ransomware attacks in the first half of 2024 disproportionately targeted countries with higher economic power. This trend shows a strong correlation between a country’s GDP and the number of organizations affected, as noted in our H2 2023 Ransomware Trends and Statistics report. Among these countries, the U.S. accounted for over half (51.8%) of all ransomware victims in the first half of 2024. This can be attributed to the U.S.’s status as a high-value economic target, with a large concentration of businesses and government organizations more likely to pay the ransoms demanded by attackers.
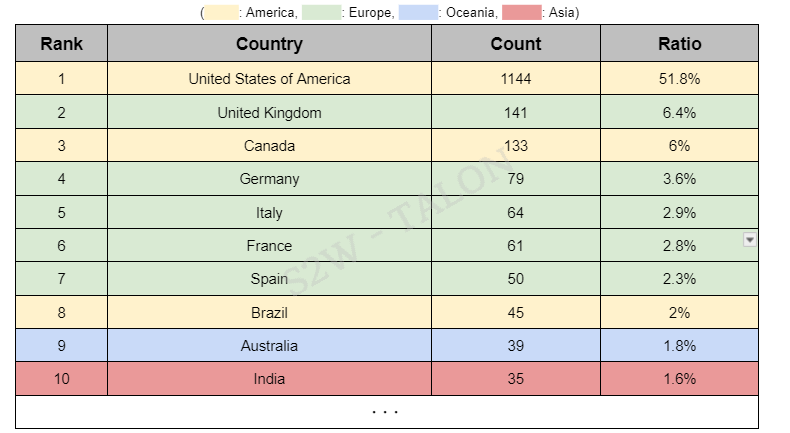 Table 2. Top 10 Ransomware Affected Countries
Table 2. Top 10 Ransomware Affected Countries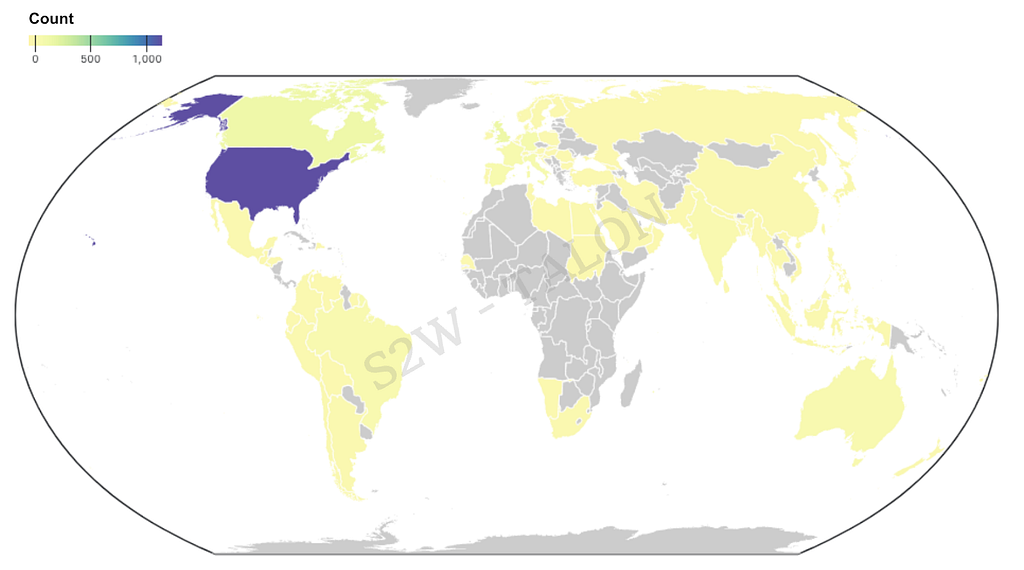 Figure 3. Map of Ransomware Affected Countries Graph
Figure 3. Map of Ransomware Affected Countries Graph1.3 Targeted Victim Industry
The top 10 victim industries accounted for 75.2% of all victim industries, which is similar to the second half of 2023 overall. However, in the first half of 2024, the Transportation industry, which was not previously in the top 10, appeared. Additionally, the Construction industry became the second most affected industry, up from fourth place in the second half of 2023, while the Education industry dropped about 0.6%, moving from fifth to tenth place in the top 10. The most affected industry remained the same as in 2023, accounting for 20.5% of all affected organizations, an increase of approximately 3.8% year-over-year. A detailed breakdown of ransomware-affected industries year-over-year can be found in Section 2.1.3.
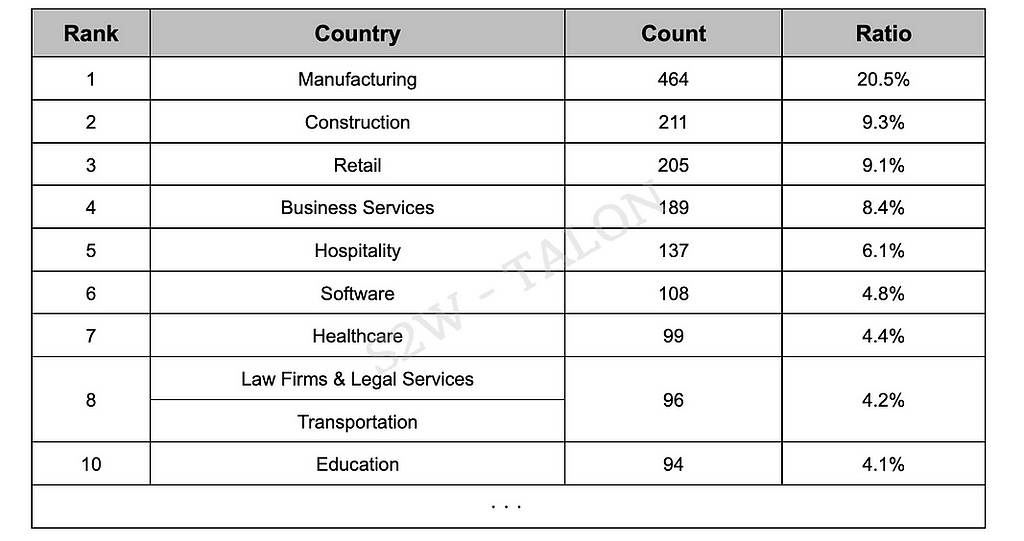 Table 3. Top 10 Ransomware Victim Industries
Table 3. Top 10 Ransomware Victim Industries2. Detailed Analysis of Ransomware Activities
2.1 Statistical Insight
2.1.1. New Ransomware Group
S2W tracked 51 new ransomware groups and variants in the first half of 2024, with an average of approximately 8 new groups discovered monthly. The number of new ransomware groups emerging in the first half of 2024 increased by seven compared to the second half of 2023. April saw the highest number of new ransomware groups in the first half of 2024, with 16 new groups emerging.
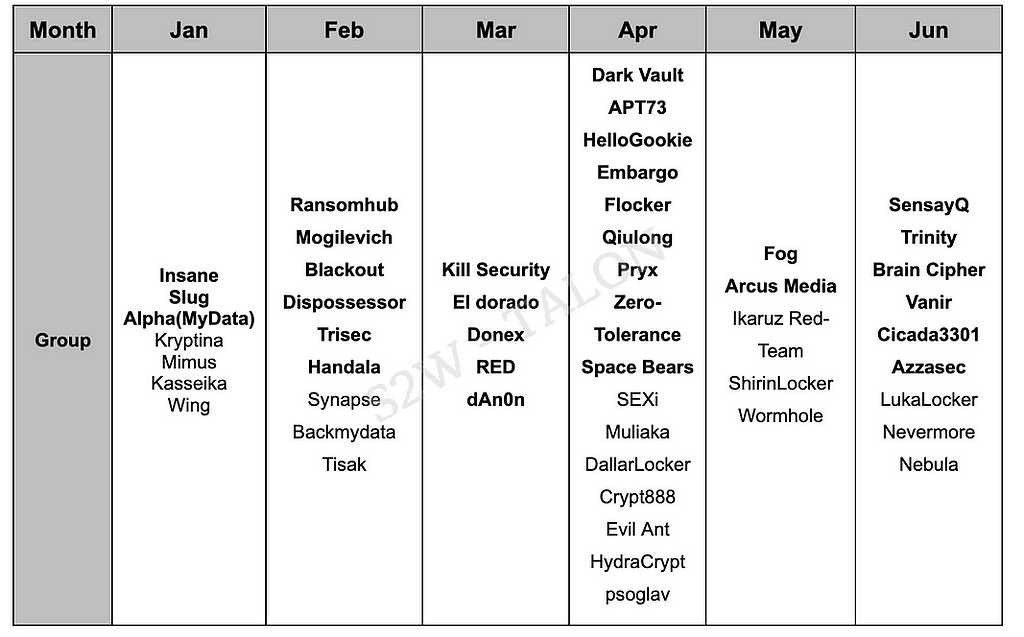 Table 4. New Ransomware Groups in the First Half of 2024 (Bold: Groups with Leak sites)
Table 4. New Ransomware Groups in the First Half of 2024 (Bold: Groups with Leak sites)This section provides a more detailed analysis of the newly active ransomware groups in the first half of the year, distinguishing between groups operating Leak sites and groups categorized by ransomware family.
New Ransomware Groups Operating Leak Sites
S2W has continuously tracked ransomware groups operating Leak sites. Compared to the second half of 2023, the number of newly discovered ransomware groups operating Leak sites increased, and the number of groups either changing addresses or going offline also rose.
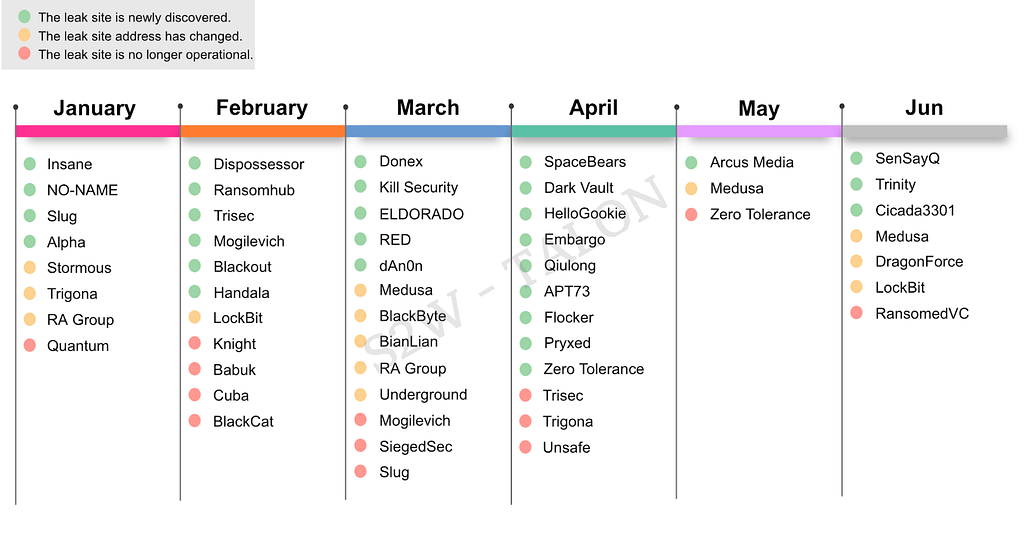 Figure 4. Status Changes of Leak Sites in the First Half of 2024
Figure 4. Status Changes of Leak Sites in the First Half of 202428 new Leak sites were discovered during the first half of 2024. Among them, groups such as APT73, DarkVault, Blackout, Kill Security, Flocker, Handala, Pryxed, and Insane were found to be operating both new and existing Leak sites, often adding new types of Leak sites on platforms such as Telegram, X(formerly Twitter), and Clearnet.
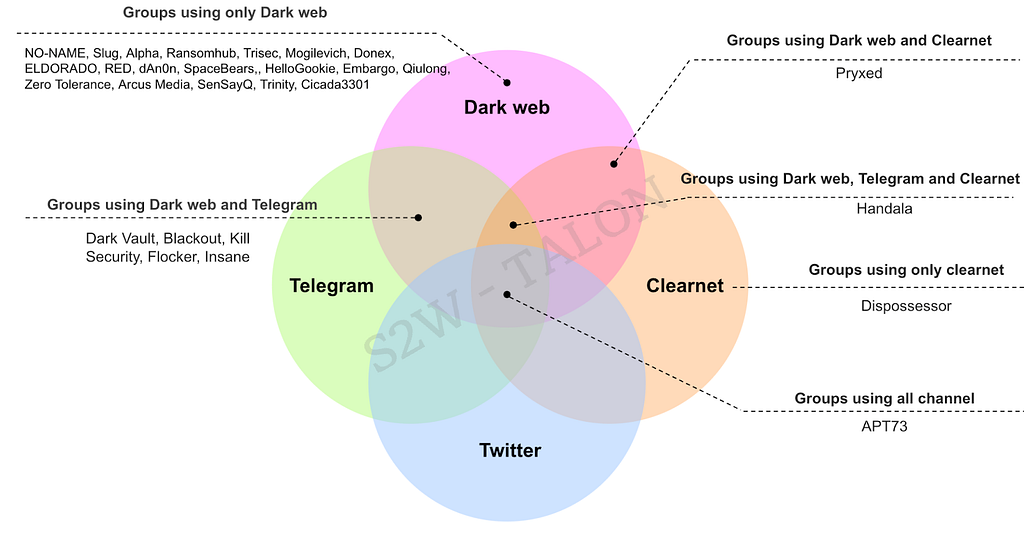 Figure 5. Channel Usage by Ransomware Groups with New Leak Sites
Figure 5. Channel Usage by Ransomware Groups with New Leak SitesOn the other hand, several groups experienced changes in their Leak sites. 9 groups changed their Leak site addresses, and 13 ceased operations.
- Groups that changed Leak site addresses (9): Stormous, Trigona, RA Group, LockBit, Medusa, BlackByte, BianLian, Underground, DragonForce
- Groups that ceased operations (13): Quantum, Knight, Babuk, Cuba, BlackCat, Mogilevich, SiegedSec, Slug, Trisec, Trigona, Unsafe, Zero Tolerance, RansomedVC
For example, LockBit’s Leak site was seized in February and May due to Operation CRONOS, leading to a halt in operations. BlackCat ceased operations in February 2024 following a scam incident. Additionally, Knight stopped operations in February 2024, selling its ransomware source code on forums and no longer maintaining its Leak site.
New Ransomware Groups Based on Ransomware Family
While some ransomware groups develop their ransomware, others either purchase the source code of other ransomware groups or use leaked source codes and builders to customize or reuse existing ransomware. Among the new ransomware groups that emerged in the first half of 2024, four groups were identified as having utilized builders or leaked source codes from other groups. Notably, several LockBit family variants were discovered during this period.
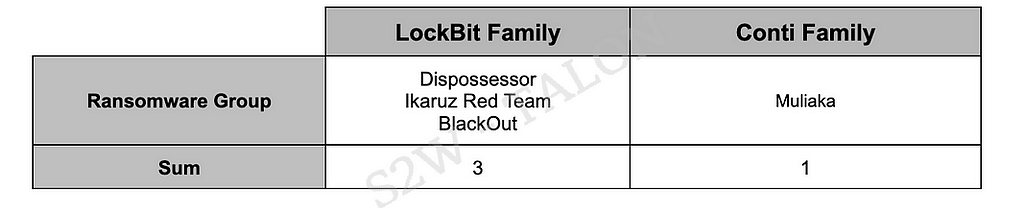 Table 5. Ransomware Groups Categorized by Ransomware Family
Table 5. Ransomware Groups Categorized by Ransomware Family- LockBit Family: Ransomware from the LockBit family refers to ransomware created using the LockBit 3.0/Black builder, which a developer leaked in September 2022.
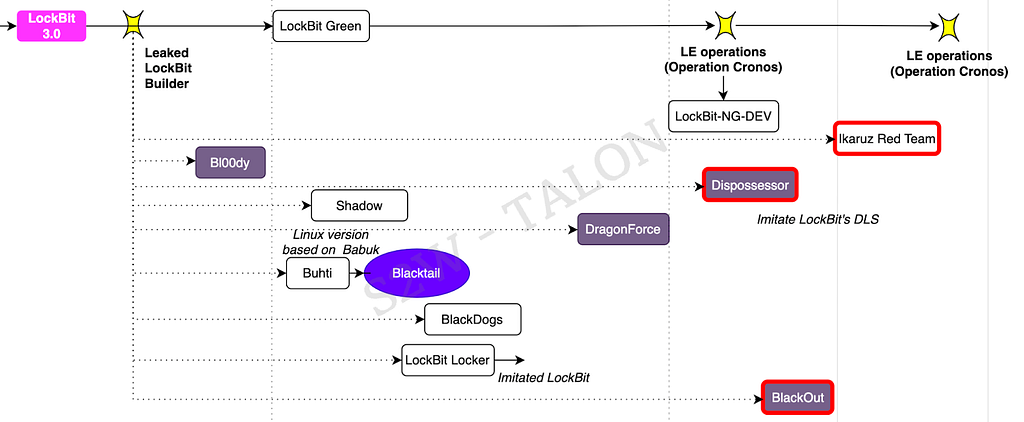 Figure 6. LockBit Family
Figure 6. LockBit Family- Conti Family: This term refers to ransomware developed using leaked source code from the Conti ransomware or derived from subgroups of Conti (e.g., Black Basta, BlackByte, Royal).
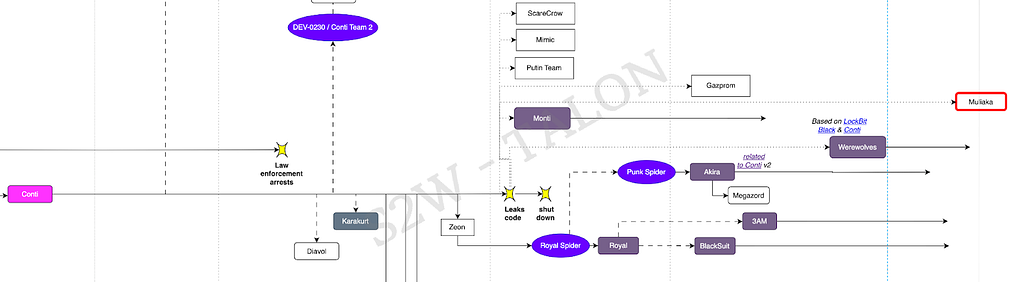 Figure 7. Conti Family
Figure 7. Conti Family2.1.2. Detailed Statistical Insight of Ransomware Group
There were 56 ransomware attacks against government organizations in the first half of 2024, accounting for approximately 1.3% of all ransomware attacks, one fewer than in the second half of 2023. While H1 2024 saw an 82.8% increase in ransomware victims, attacks on government organizations appear to have declined. Specifically, 19 government organizations were impacted, targeted by 22 ransomware groups, with LockBit being the most active and responsible for 11 attacks. The top eight affected countries were the U.S., Spain, Canada, the U.K., India, France, Brazil, and Germany, with the U.S. having the highest number of victims at 25, an increase of two compared to the second half of 2023. Government organizations in 11 other countries were also affected, though these are not included in the victimization statistics.
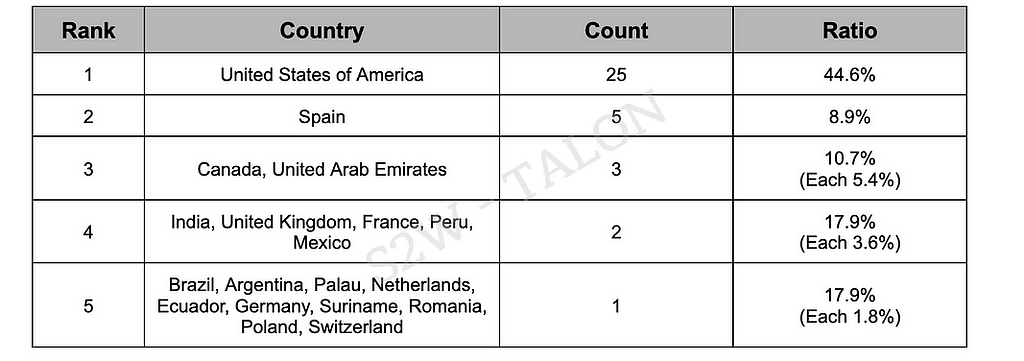 Table 6. Countries Affected by Ransomware Government Organizations
Table 6. Countries Affected by Ransomware Government Organizations32 ransomware groups targeted large enterprises, representing 42.6% of all ransomware groups. Among the top 10 groups, all except BianLian targeted large enterprises. LockBit focused on 25 out of 464 attacks on large enterprises, while Hunter International targeted large enterprises in 11 out of 98 attacks. Both 8Base and PLAY had relatively low percentages of attacks on large enterprises, at 2.5% and 1.2%, respectively. The CLOP group, which had targeted large enterprises the most in the second half of 2023, did not attack any large enterprises in the first half of 2024, and its overall attack volume decreased by 91.2%. This decline is likely due to the group’s reduced impact after the vulnerabilities they exploited in the second half of 2023 were patched.
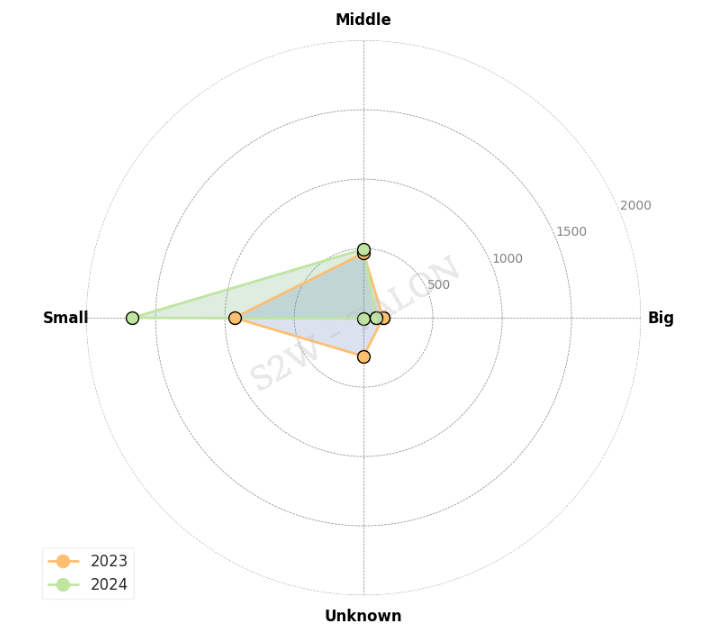 Figure 8. Categorizing companies by revenue in 2023 and the first half of 2024 Radar Chart
Figure 8. Categorizing companies by revenue in 2023 and the first half of 2024 Radar Chart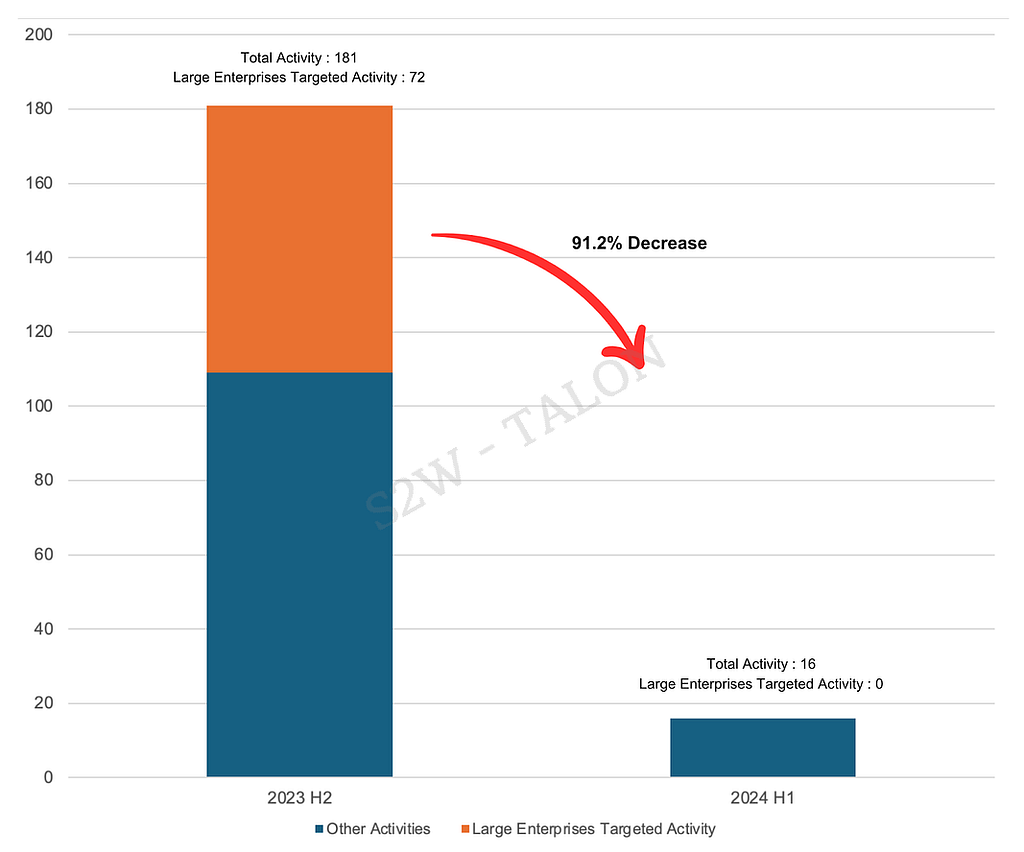 Figure 9. Ratio of CLOP group activity in H2 2023 vs. H1 2024
Figure 9. Ratio of CLOP group activity in H2 2023 vs. H1 2024The RaaS and Freelance boards on the RAMP forum, where ransomware groups are active, saw a 41.7% increase in posts recruiting pen-testers or RaaS members compared to the second half of 2023. The boards were particularly active in March and June 2024, coinciding with a ransomware attack volume decrease. This increase in job postings during these periods correlates with fluctuations in ransomware attack volume and should be monitored continuously to help predict future attack trends.
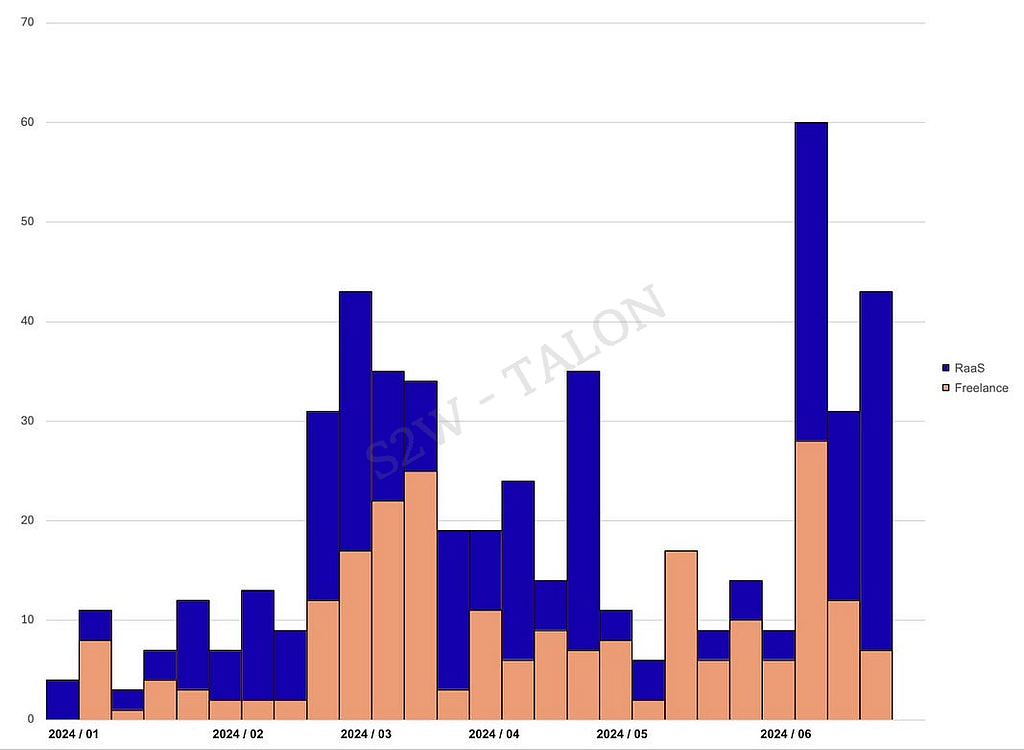 Figure 10. Total count of posts and comments in the RAMP forum Freelance and RaaS boards in the first half of 2024
Figure 10. Total count of posts and comments in the RAMP forum Freelance and RaaS boards in the first half of 2024We also analyzed mentions of the keywords “Ransomware” and “Affiliate” on the deep web, dark web, and Telegram during the first half of 2024. We found that Telegram had 96.1% more mentions than the deep web and dark web combined. Notably, the keyword “Affiliate” was mentioned more frequently than “Ransomware” on Telegram, indicating that ransomware groups are increasingly using Telegram as their primary platform for activity. The higher occurrence of the keyword “Affiliate” suggests that ransomware is increasingly being offered as a service.
2.1.3. Compared with H1 last year
The country with the most significant increase in ransomware victims in the first half of 2024 was Canada, and five of the top 10 countries with the most significant increase in victims were located in Europe, making Europe the continent with the most significant rise in ransomware activity. Canada, the United Kingdom, Italy, Germany, Spain, and Brazil took the top six spots, suggesting a broad increase in ransomware activity across multiple countries rather than focusing on any specific country or organization. In the Middle East, Israel and the United Arab Emirates were among the countries that experienced an increase in ransomware attacks, with the UAE appearing for the first time. This rise may be linked to the region's political tensions and GDP growth. On the other hand, the country with the most significant decrease in ransomware victimization was Türkiye, and Asia dominated the top 10 list of countries with the most significant decreases, with five Asian countries represented.
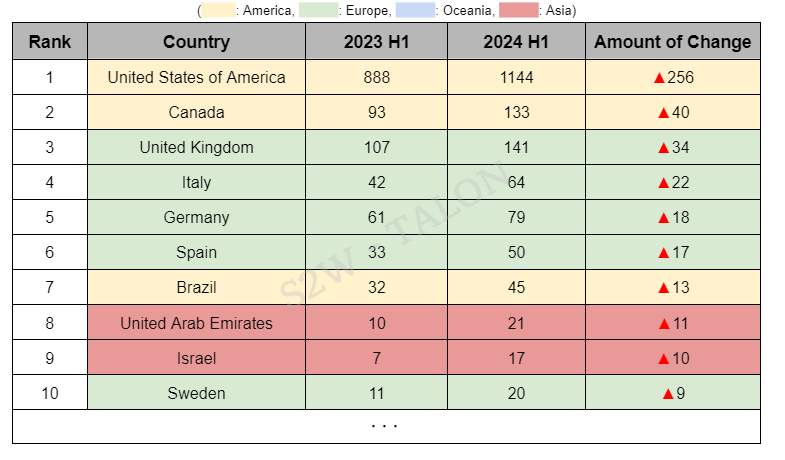 Table 8. Top 10 Countries with the Most Increased Ransomware Attacks
Table 8. Top 10 Countries with the Most Increased Ransomware Attacks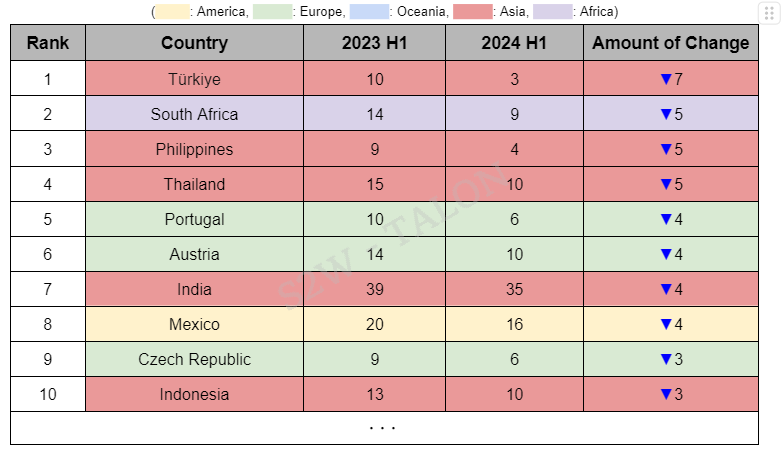 Table 9. Top 10 Countries with the Most Reduced Ransomware Attacks
Table 9. Top 10 Countries with the Most Reduced Ransomware Attacks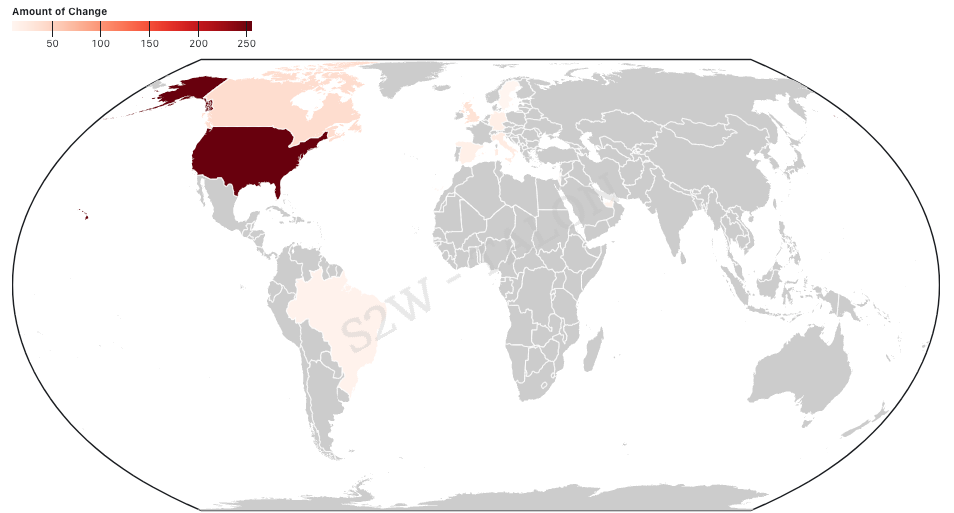 Figure 11. Graph of the Top 10 Countries with the Most Increased Ransomware Attacks
Figure 11. Graph of the Top 10 Countries with the Most Increased Ransomware Attacks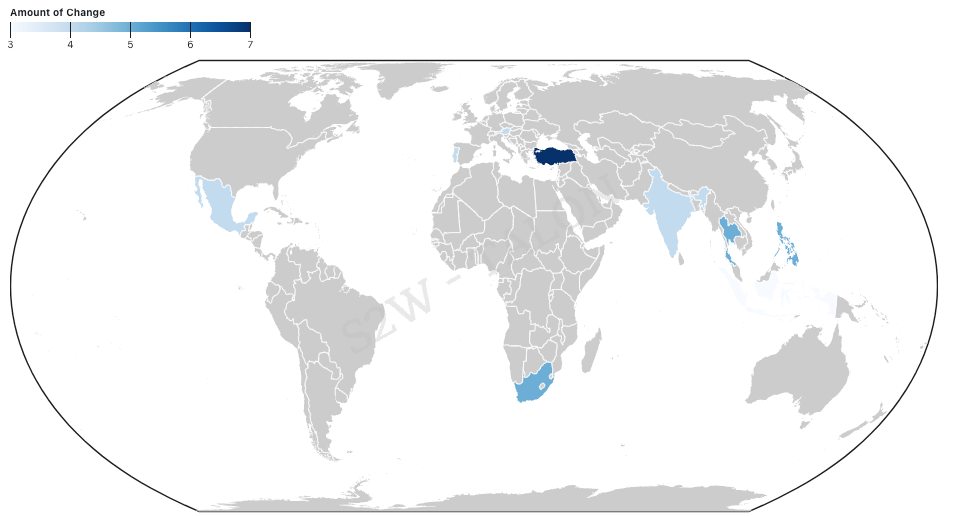 Figure 12. Graph of the Top 10 Countries with the Most Reduced Ransomware Attacks
Figure 12. Graph of the Top 10 Countries with the Most Reduced Ransomware AttacksThe industries that experienced the largest increase in ransomware victims were Manufacturing, Hospitality, and Construction, with Manufacturing seeing the highest rise at 117 incidents. This is likely due to the expansion of these sectors, driven by infrastructure investments and the adoption of advanced technology in the U.S., as well as the post-COVID-19 recovery in travel and tourism, which has contributed to the surge in ransomware attacks. Ransomware groups typically target highly profitable industries, making these growing sectors prime targets. As the Manufacturing, Hospitality, and Retail industries continue to expand by adopting AI and digital technologies, they are likely to face increasing ransomware threats.
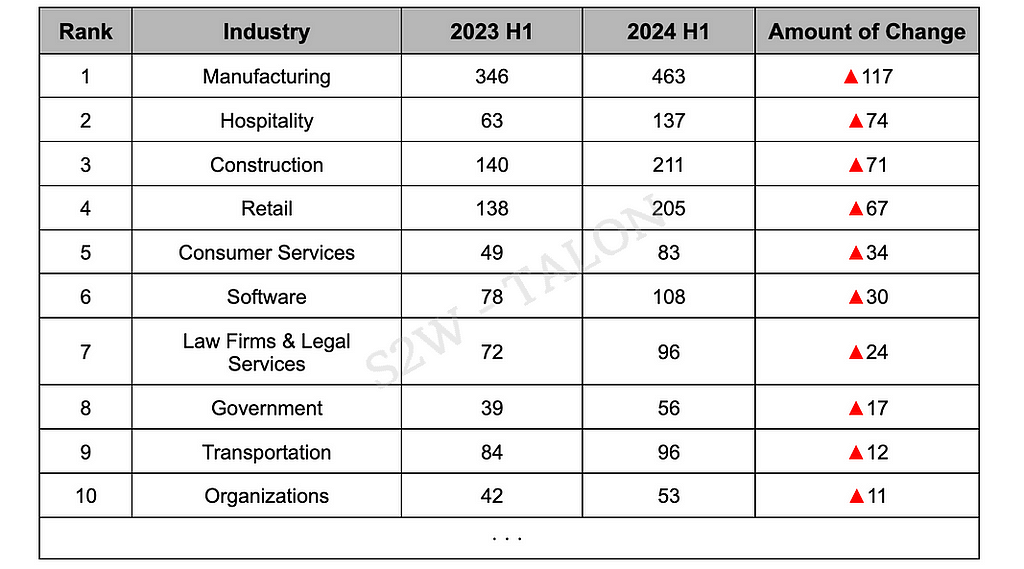 Table 10. Top 10 Industries with the Most Increased Ransomware Victims
Table 10. Top 10 Industries with the Most Increased Ransomware VictimsThe Education, Business Services, and Finance industries were among those that experienced a decline in ransomware victims in the first half of 2024, with Education seeing the most significant reduction, down by 31 incidents. The Education sector appears to be a less attractive target for ransomware groups due to its lower profitability, which has also contributed to the decline in activity by the Rhysida group during H1 2024. The Banking, Financial Services, and Insurance (BFSI) industry has also seen fewer ransomware attacks, likely due to enhanced cybersecurity infrastructure and stricter regulatory compliance. Similarly, the Insurance industry has experienced a decline in victimization, attributed to increased investments in cybersecurity.
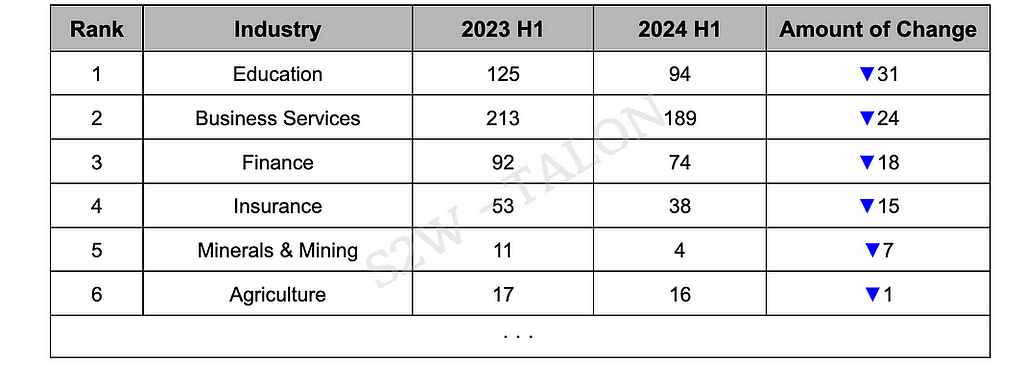 Table 11. Top 10 Industries with the Most Reduced Ransomware Victims
Table 11. Top 10 Industries with the Most Reduced Ransomware Victims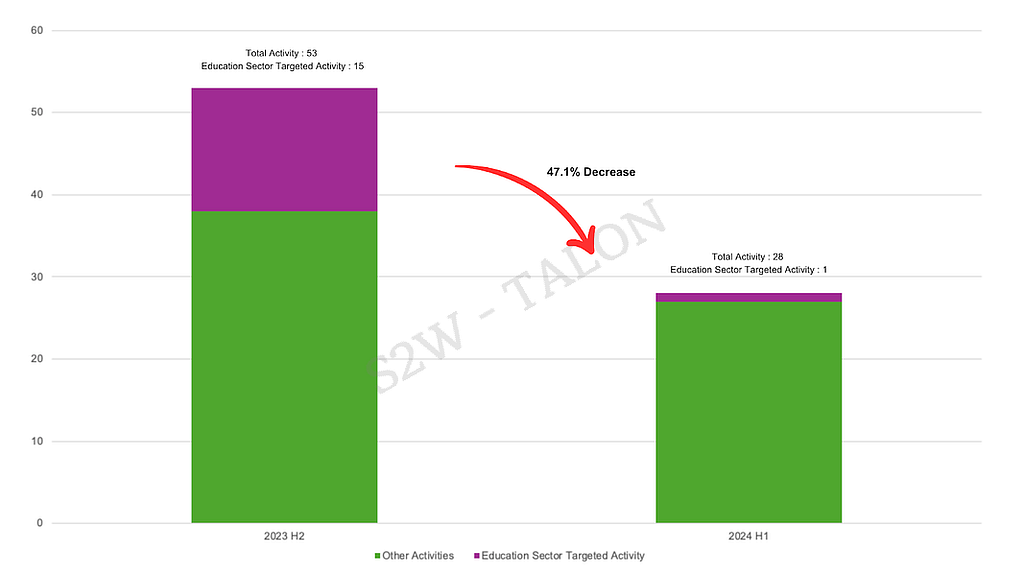 Figure 13. Comparison of Rhysida group activity in H2 2023 vs. H1 2024
Figure 13. Comparison of Rhysida group activity in H2 2023 vs. H1 20242.2 Key Issue
2.2.1. Version Control
Ransomware groups operating RaaS platforms continuously update their ransomware to evade detection and maintain their brand reputation. Additionally, they are expanding the range of operating systems they target. The changes observed in the first half of 2024 are as follows.
LockBit
In February 2024, Trend Micro discovered a ransomware variant identified as an updated version of LockBit ransomware, which they called LockBit-NG-Dev. Unlike its predecessors, LockBit-NG-Dev is written in C# and includes logic to check the current time to determine whether or not to execute. However, this sample is believed to be a test version, as its functionality must be completed.
In April 2024, LockBit mentioned in a conversation with vx-underground that they were developing a payload targeting Nutanix environments.
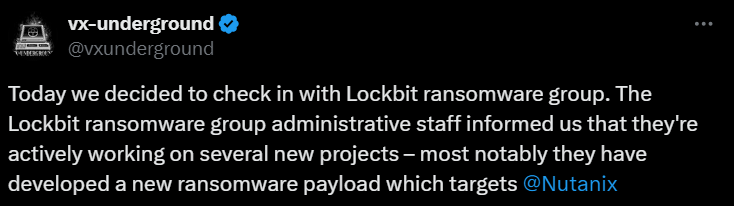 Figure 14. vx-underground and LockBit Interview (Source: vx-underground)
Figure 14. vx-underground and LockBit Interview (Source: vx-underground)Cerber
In April 2024, a campaign was identified that distributed Cerber ransomware through the Confluence vulnerability CVE-2023–22518. Additionally, a Linux version of Cerber was recently discovered. The Cerber Linux variant identified in this campaign was written in C++ and packed with UPX.
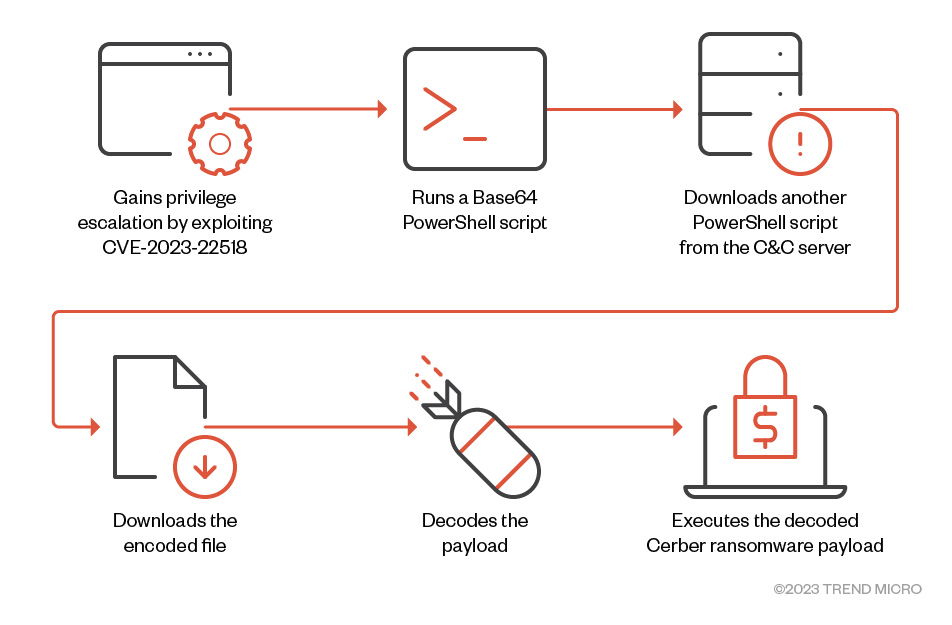 Figure 15. Cerber Ransomware Attack flow (Source:Trend Micro)
Figure 15. Cerber Ransomware Attack flow (Source:Trend Micro)TargetCompany
According to Trend Micro, in June 2024, a new ransomware targeting Linux environments, TargetCompany, was discovered. This ransomware is notable for encrypting disk image file extensions within VM mode, specifically in ESXi environments.
Trend Micro also identified an affiliate using the nickname “vampire” during the attack process. This affiliate was the same one observed in TargetCompany’s PureCrypter campaign in May 2024.
2.2.2. Revealed connections between ransomware groups
Ransomware groups are updating their binaries, modifying their attack strategies through inter-group collaborations, rebranding themselves to manage affiliates, and maintaining their reputation. Throughout the first half of 2024, several instances of collaboration and rebranding among ransomware groups have been observed. Below is a summary of the connections and affiliations confirmed during this period.
BlackCat — Trigona (Cooperation possible)
Between 2023 and 2024, BlackCat faced multiple infrastructure shutdowns, seemingly due to seizures by law enforcement. Meanwhile, several affiliates posted reports on the RAMP forum accusing BlackCat of running a scam. The RAMP forum administrator also confirmed that BlackCat was involved in a scam.
Although BlackCat has ceased operations, some affiliates, such as Scattered Spider, continue to carry out attacks using the BlackCat ransomware.
Recent incidents involving BlackCat and Trigona ransomware revealed the use of “rclone” in both incidents. The same Mega account was used during these attacks, suggesting that the two groups shared the same affiliate.
Embargo — MEOW (Cooperation possible)
“Embargo” is a ransomware group discovered in April 2024, and MEOW, identified in November 2023, is a group solely focused on data exfiltration without engaging in ransomware attacks.
Although MEOW does not engage in ransomware attacks, there is speculation of a link between the two groups, as both Embargo and MEOW share the same favicon on their sites and have matching hash values.
 Figure 16. MEOW, Embargo Favicon (Source: Dominic Alvieri)
Figure 16. MEOW, Embargo Favicon (Source: Dominic Alvieri)INC — Hunters International (Cooperation possible)
In May 2024, the INC group revamped its site and launched a new Data Leak Site (DLS). Numerous similarities between the new DLS and Hunter International’s DLS have raised suspicions of a possible connection between the two groups.
The similarities include a similar design for victim lists and using Flagsapi.com services to display images. Additionally, both groups’ DLS platforms are hosted on Onion domains using REACT and ExpressJS, and both employ nginx version 1.18.0.
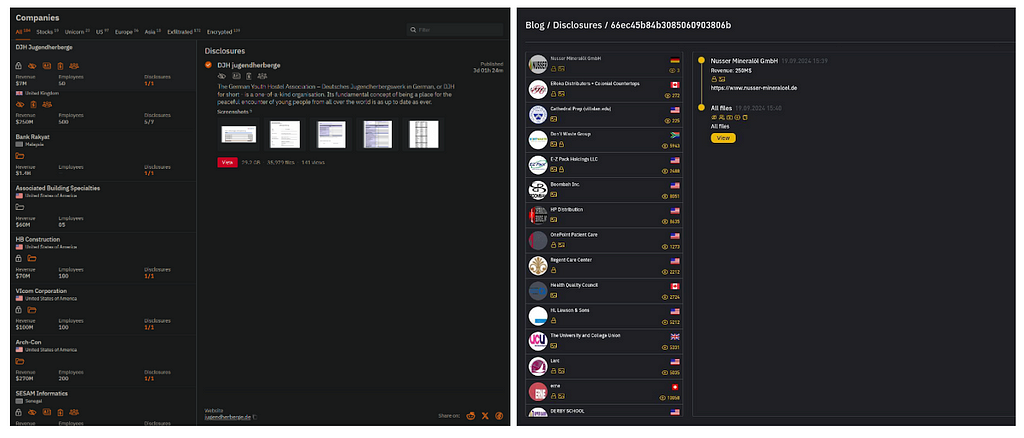 Figure 17. Hunters’s Leak site (Left) / INC’s Leak site(Right)
Figure 17. Hunters’s Leak site (Left) / INC’s Leak site(Right)BianLian — Makop (Cooperation possible)
BianLian has been active since 2022. Initially, they employed a double extortion strategy by conducting ransomware attacks alongside data theft. However, after Avast released a decryption tool in early 2023, BianLian shifted its focus solely to data exfiltration attacks.
According to Unit42, both the BianLian and Makop groups have been found using the same custom tool, indicating a possible connection between them. This tool, written in .NET, is designed to search registry and clipboard data.
Trinity — 2023Lock, Venus (Cooperation possible)
Trinity was first discovered in May 2024, and the ransomware they use shares multiple code similarities with the 2023Lock ransomware, which was recently identified in early 2024.
Additionally, Trinity ransomware shows significant code similarities with Venus ransomware, discovered around August 2022, as both use the same mutex and registry names.
ThreeAM — Conti, LockBit, BlackCat (Cooperation possible)
According to Symantec, ThreeAM is ransomware identified during attacks involving LockBit ransomware. It is suspected that the attackers switched to using ThreeAM when LockBit was blocked by security systems, suggesting a possible connection between the two variants.
An analysis of the ClearNet infrastructure used by ThreeAM revealed some similarities with the backend infrastructure associated with BlackCat. Additionally, there is a history of BlackCat ransomware and Quantum ransomware distribution being facilitated by Emotet, primarily used by the Conti group, further indicating potential links among these groups.
Alpha — NetWalker (Rebrand possible)
Alpha is a ransomware group that began its activities in February 2023. Because of overlapping ransomware payloads, there are concerns about a possible connection between Alpha and the NetWalker group, which ceased operations in January 2021. Notably, the two groups share similarities in the lists of encryption exclusion paths, file extensions, and targeted services and processes. Both ransomware variants also utilize batch files to delete files after completing the encryption process.
Additionally, the user interface of the victim negotiation pages for Alpha and NetWalker is similar, and both contain identical messages, further supporting claims of a connection between the two groups.
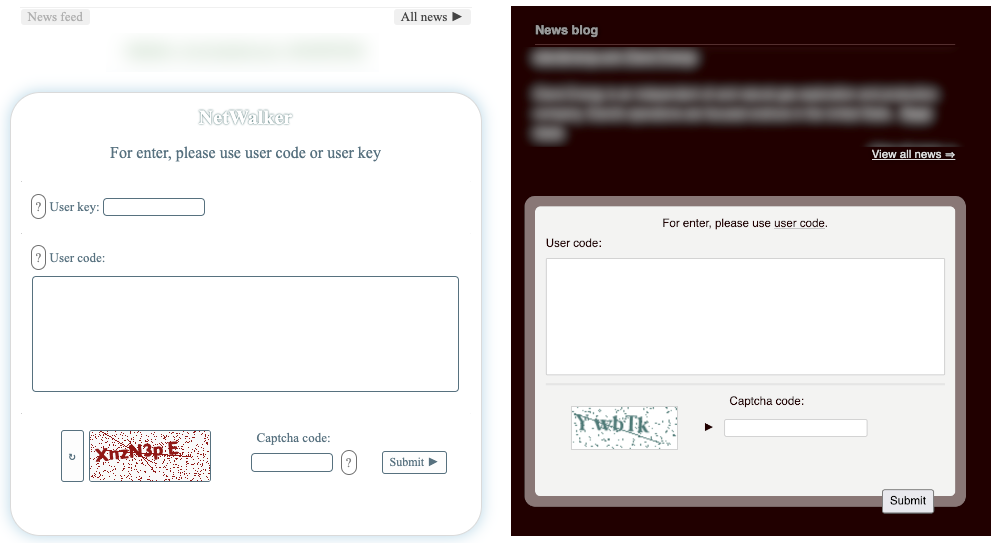 Figure 18. NetWalker’s Negotiation Site (Left) / Alpha’s Negotiation Site (Right) (Source:TrendMicro)
Figure 18. NetWalker’s Negotiation Site (Left) / Alpha’s Negotiation Site (Right) (Source:TrendMicro)Eldorado — LostTrust (Rebrand possible)
Eldorado is a ransomware group that emerged in March 2024 and operates a Ransomware as a Service (RaaS) platform that targets VMWare ESXi and Windows environments. It is active on the RAMP forum with the nickname “$$$,” and since March, it has actively recruited affiliates and pen-testers.
Researchers at SOCRadar have analyzed Eldorado ransomware and found that its ransom note is similar to the ransom notes previously used by the LostTrust group.
HelloGookie — HelloKitty (Rebrand)
HelloKitty is a ransomware first identified in early January 2021 and targets Windows operating systems. It is named after the mutex ‘HelloKittyMutex’ used within the ransomware. In April 2024, HelloKitty ransomware rebranded itself to HelloGookie upon launching a Data Leak Site (DLS) and published some decryption keys as its first post.
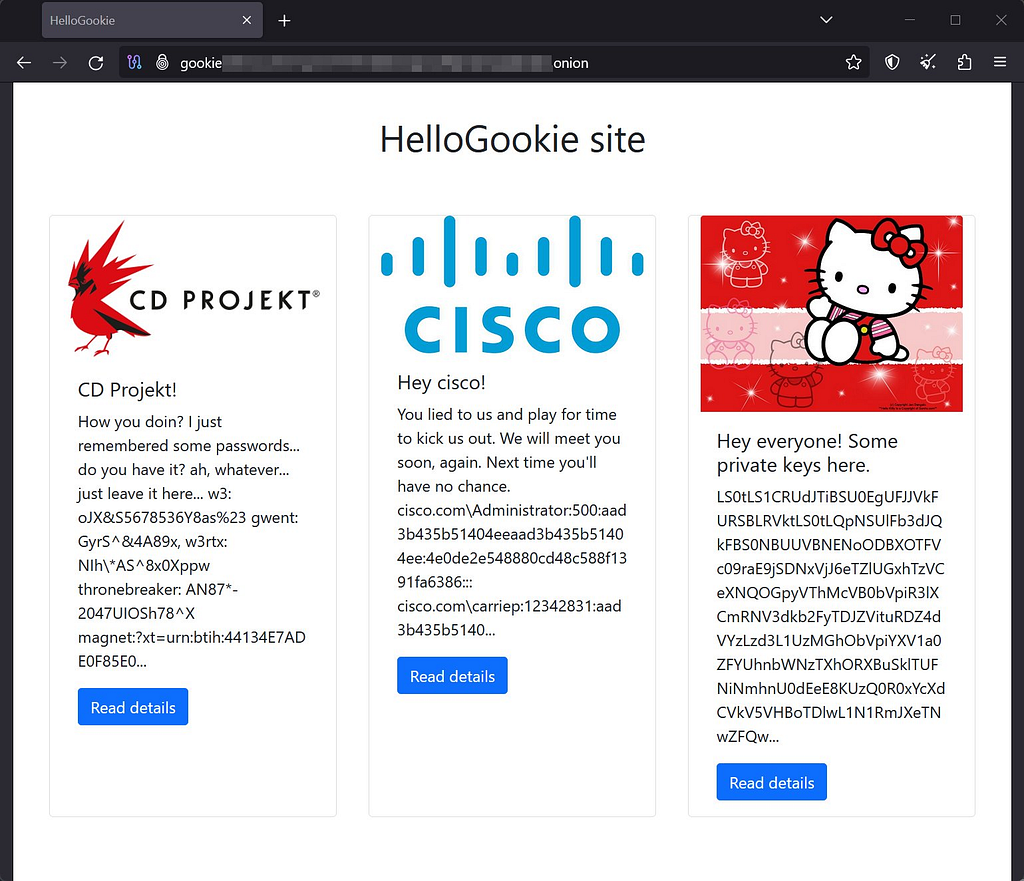 Figure 19. HelloGookie Leak Site
Figure 19. HelloGookie Leak Site2.2.3. Affiliate
An Affiliate refers to an individual or group that collaborates with RaaS Operators to perform initial infiltration, lateral movement within networks, data exfiltration, and ransomware deployment. In this report, the concept of an Affiliate has been expanded beyond its traditional meaning to include any user or group that assists in gaining Initial Access. Consequently, Affiliates are divided into two categories: Initial Access Brokers, who sell access to individuals or specific companies on the deep and dark web, and Pentesters, who are responsible for the initial infiltration to distribute ransomware payloads.
LockBit: PTI-269, PTI-43, PTI-130, PTI-236, PTI-253, PTI-254 and PTI-257 (Pentester)
On February 19, 2024, law enforcement agencies from 11 countries collaborated to take down part of LockBit’s infrastructure. Following this, the NCA, FBI, and Europol issued statements regarding Operation CRONOS and released information obtained from LockBit’s infrastructure.
On February 25, LockBit began restoring the taken-down infrastructure and issued a statement rebutting Operation CRONOS, signaling the resumption of their activities.
PRODAFT had previously identified more than 28 LockBit affiliates, and recent NCA statistics indicate that the number of LockBit affiliates has increased to 194 over the past three years. PRODAFT also identified seven clusters of affiliates through their unique TTPs and confirmed links to groups like EvilCorp, FIN7, BassterLord, and WizardSpider.
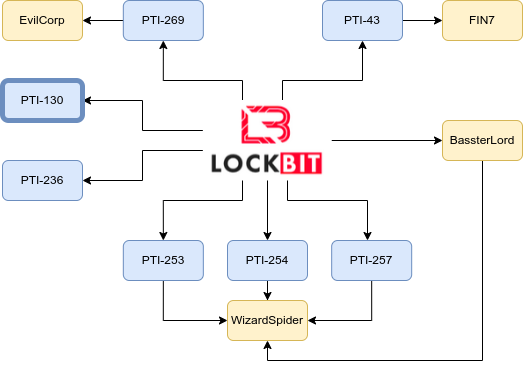 Figure 20. LockBit Affiliate (Source: PRODAFT)
Figure 20. LockBit Affiliate (Source: PRODAFT)Akira, LockBit, Conti, Ryuk: Zeon (Pentester)
Zeon (Conti Team 1) previously operated as a pentester for Conti and has been active as a pentester for Akira and LockBit since December 2023. It provides expertise in callback phishing (BazarCall) and call center operations.
After the FBI seized some of LockBit’s infrastructure, Zeon shifted focus to Akira’s activities and is reported to have exploited vulnerabilities such as CVE-2024–22252, CVE-2024–22253, CVE-2024–22254, and CVE-2024–22255.
Black Basta: Storm-1811 (Pentester)
Storm-1811 is a pentester group that carries out initial infiltration through phishing and vishing campaigns, maintains persistence using Remote Monitoring and Management (RMM) tools, and ultimately conducts Black Basta ransomware attacks.
In April 2024, Microsoft identified a Black Basta distribution campaign by Storm-1811, utilizing Quick Assist. The attackers performed vishing attacks via Microsoft Teams for initial infiltration, then requested device access through Quick Assist. They installed RMM software like ScreenConnect and NetSupport Manager, used PsExec for lateral movement, and finalized the attack with Black Basta ransomware.
2.2.4. Attack Technique
Ransomware attackers continuously evolve their TTPs, including the malware, tools, and vulnerabilities they use, to evade detection. Similarly, RaaS operators and affiliates constantly advance their methods to distribute ransomware and acquire financial gains from their targets. The following are the key ransomware distribution campaigns publicly disclosed in the first half of 2024.
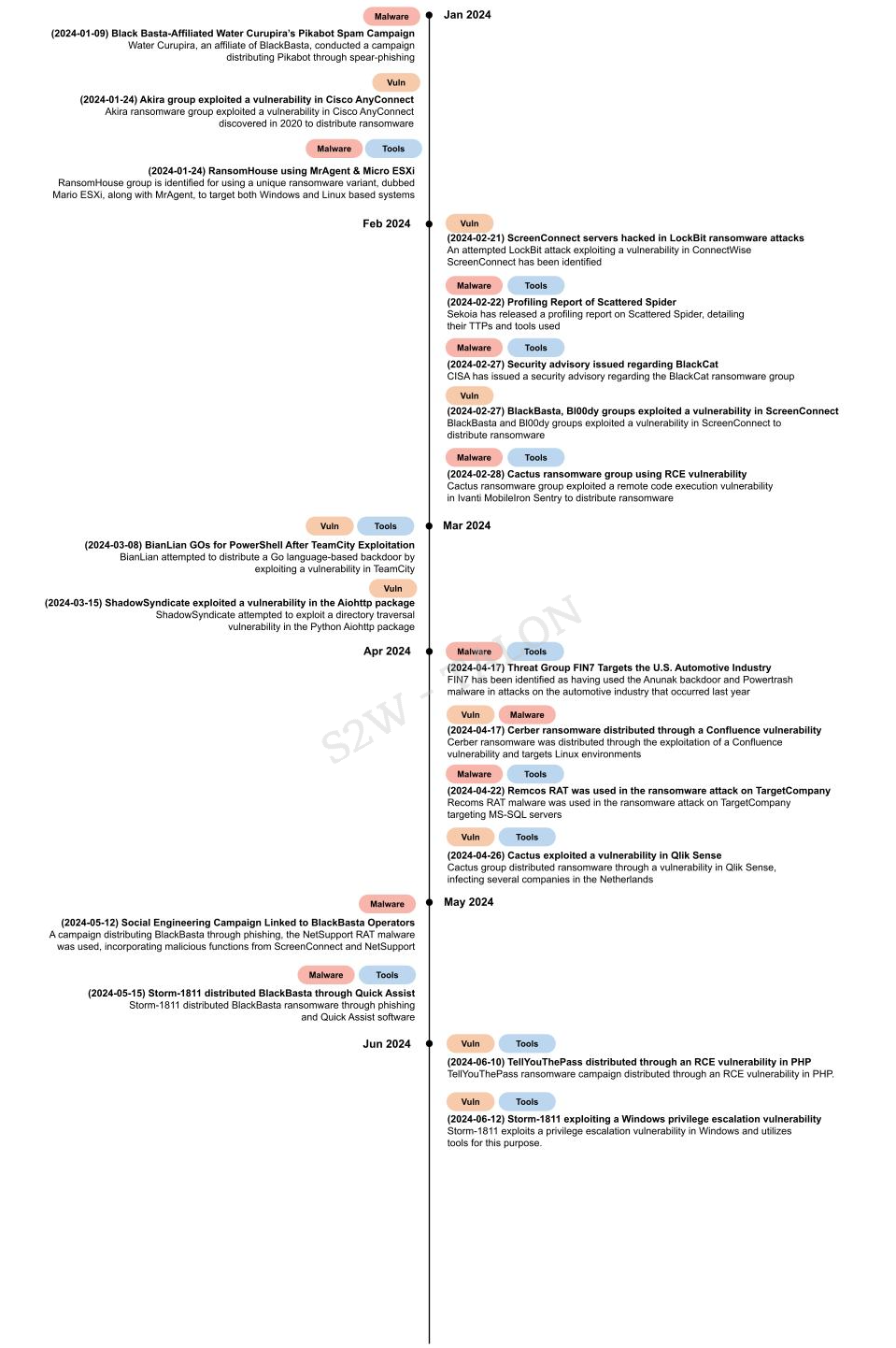 Figure 21. Campaign Timeline
Figure 21. Campaign TimelineThe following is a list of malware and custom tools identified by ransomware groups and affiliates during the first half of 2024.
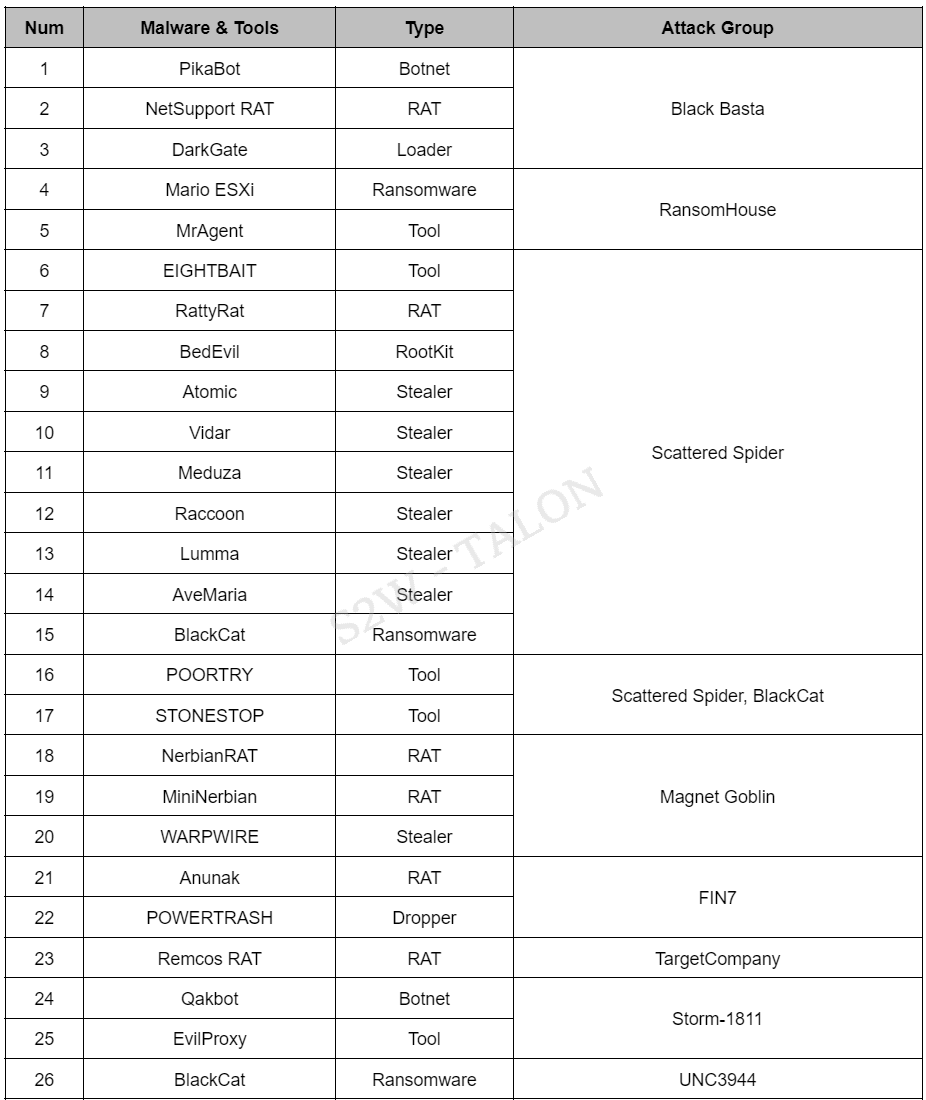 Table 12. List of Malware & Custom Tools Used in the Campaign
Table 12. List of Malware & Custom Tools Used in the CampaignDuring the first half of the year, 10 ransomware groups utilized 17 distinct vulnerabilities in their attacks. Of these, 16 were exploited using publicly disclosed vulnerabilities (1-day), while 1 was exploited using an undisclosed vulnerability (0-day). The following is a list of vulnerabilities ransomware groups used in their attacks during the year's first half.
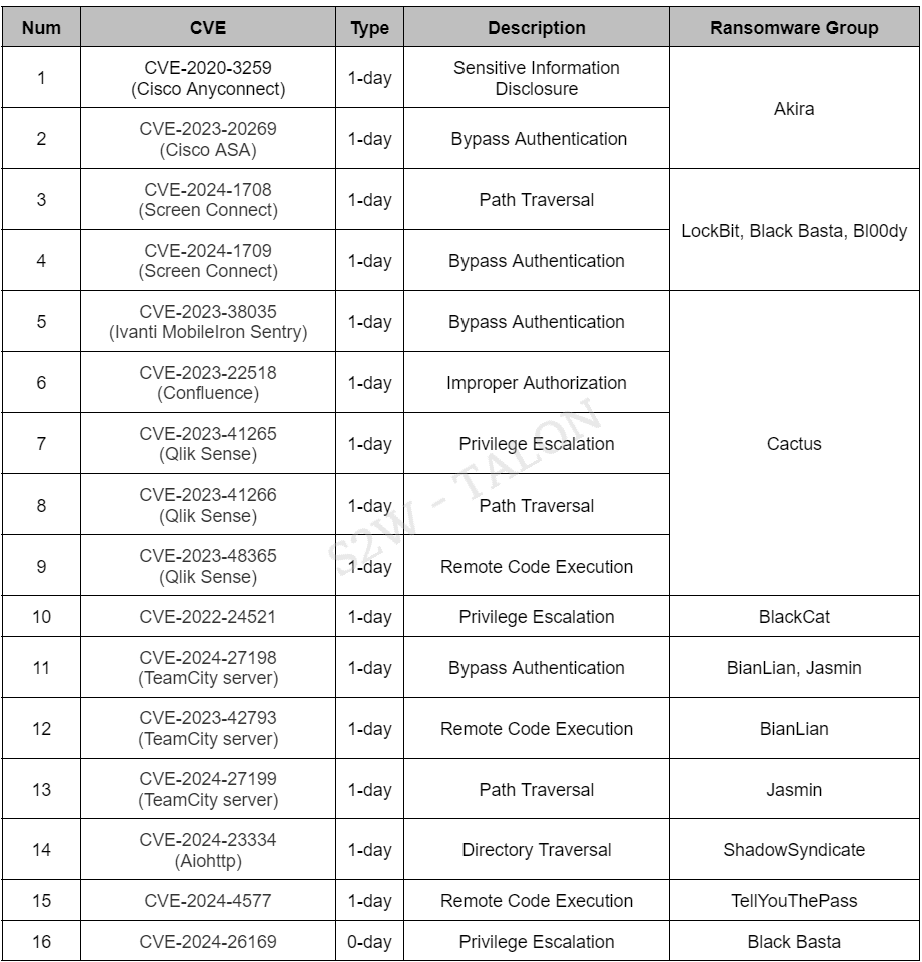 Table 13. List of Vulnerabilities Exploited in the Campaign
Table 13. List of Vulnerabilities Exploited in the Campaign2.2.5. Activities in DDW & Telegram
Ransomware groups actively recruit affiliates and promote RaaS, as well as purchase initial access rights from Initial Access Brokers (IABs), through various deep and dark web forums and Telegram. In the first half of 2024, ransomware-related posts were made on dark web forums and Telegram.
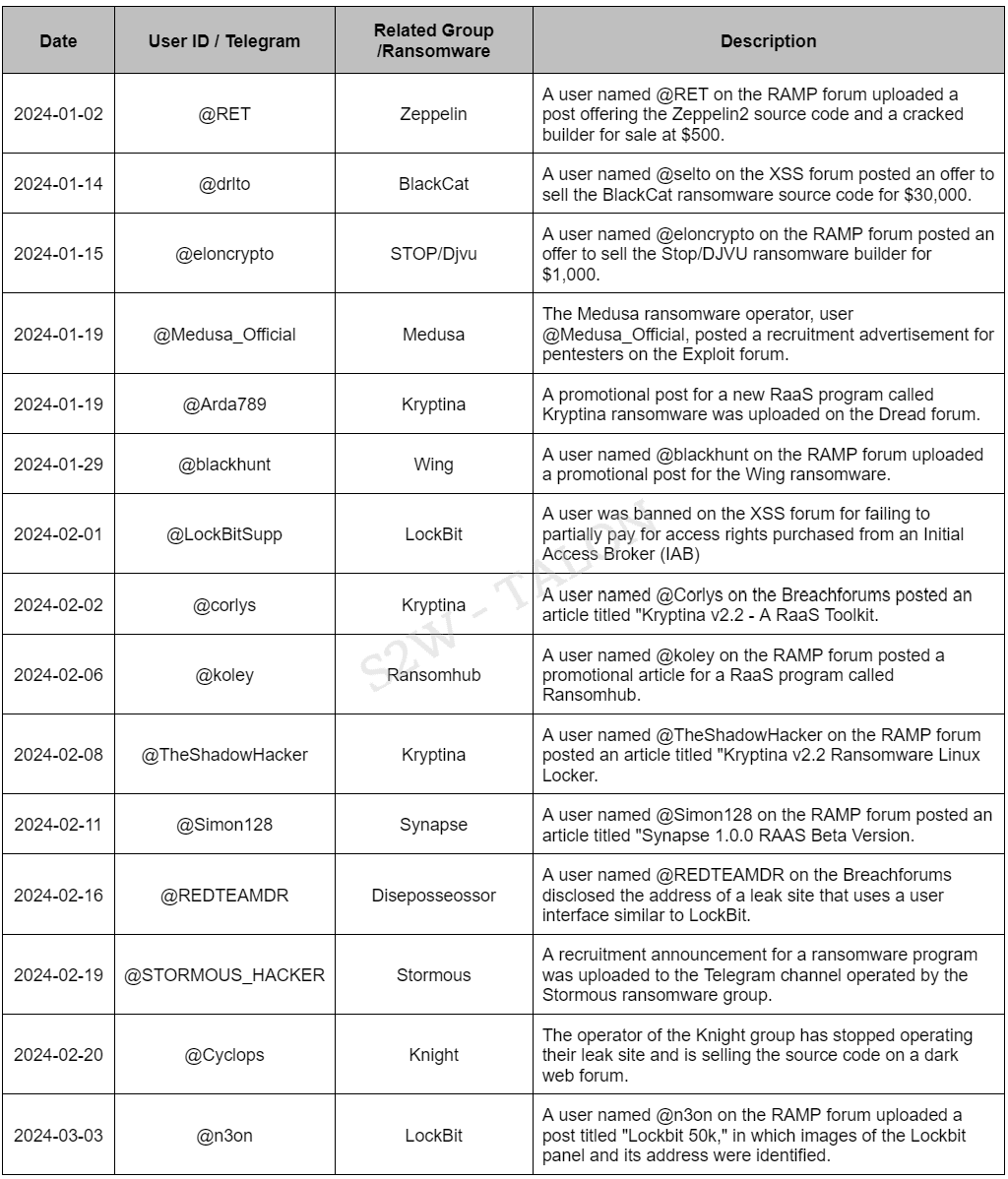
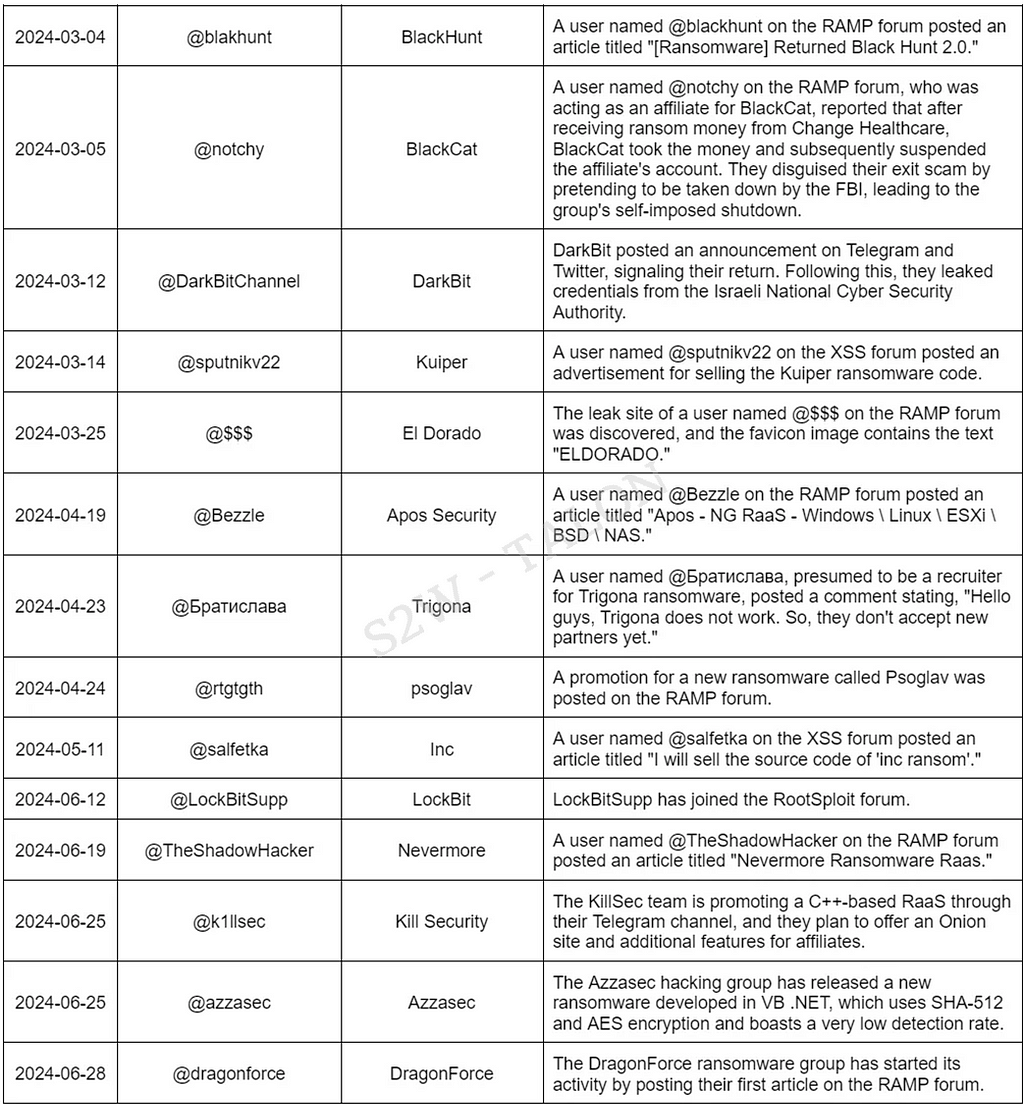 Table 14. Ransomware-Related Posts on DDW/Telegram in the First Half of the Year
Table 14. Ransomware-Related Posts on DDW/Telegram in the First Half of the Year2.2.6. Duplicated Victims
This report analyzed further to differentiate between ransomware groups that uploaded the same companies multiple times. In some cases, the same company’s breach information is disclosed on multiple Leak sites, presumed to be due to Initial Access Brokers (IABs) working with various ransomware groups.
During the first half of 2024, 54 duplicated victim companies were uploaded to Leak sites, and 30 ransomware groups were found to have disclosed the same companies. Among these groups, LockBit, PLAY, NoEscape, and BlackCat were identified as the ones that uploaded the duplicated companies earlier on multiple occasions. Conversely, LockBit, Hunters International, and PLAY were the groups that uploaded the same companies later in multiple instances.
- Each group has a 1:1 relationship with other groups. The group that uploaded the duplicated company first is placed on the left, and the group that uploaded it later is on the right.
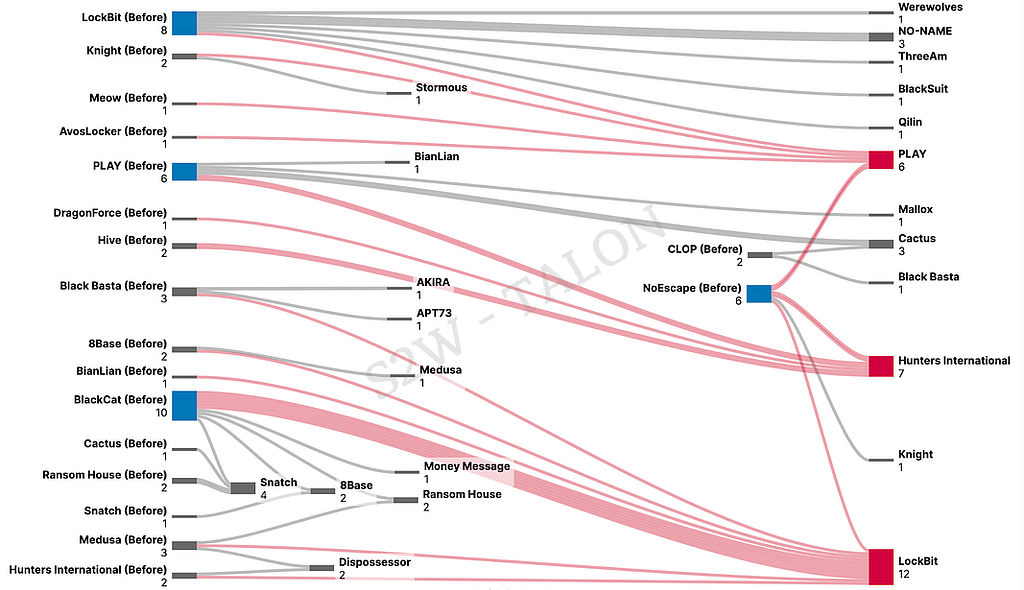 Figure 22. Diagram of Ransomware Groups that Uploaded Duplicated Victim Companies
Figure 22. Diagram of Ransomware Groups that Uploaded Duplicated Victim Companies3. Top 5 ransomware groups based on risk assessment
S2W Threat Intelligence Center has developed an evaluation metric to assess the risk of ransomware groups based on the criteria of Activity, Influence, Brand Continuity, Extensibility, and Vulnerability. This evaluation was conducted by focusing on ransomware groups with leak sites.
Detailed risk assessment metrics can be found below.
> Ransomware Resurgence: A Deep Dive into 2023’s Threatscape and Risk Assessment
This metric evaluated ransomware groups active in the first half of 2024. As a result, the top 5 high-risk groups were identified as Black Basta, BlackSuit, Qilin, Ransomhub, and PLAY. Before applying reduction metrics, LockBit, BlackCat, and BianLian were also ranked highly. Still, their risk scores dropped due to exposure of infrastructure caused by law enforcement operations such as Operation CRONOS.
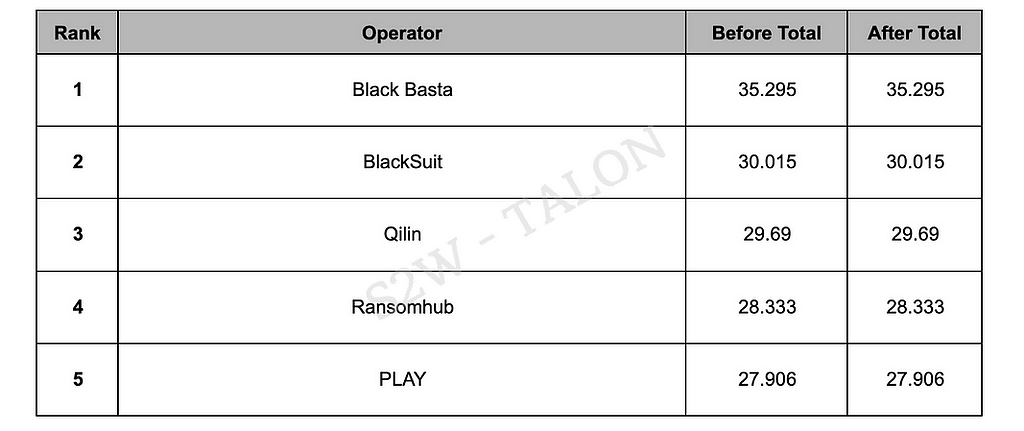 Table 15. Top 5 Ransomware Groups by Risk
Table 15. Top 5 Ransomware Groups by RiskBlack Basta
Black Basta initially ranked second in risk before applying the reduction metrics, but it moved to the first position after LockBit’s score dropped. In the first half of 2024, Black Basta had an exceptionally high score in the Vulnerability category due to the discovery of vulnerabilities in ScreenConnect (CVE-2024–1708, CVE-2024–1709), and an affiliate of Black Basta, Storm-1811, was found to have used the privilege escalation vulnerability CVE-2024–26169. However, because Black Basta does not actively participate in forums, its score for Extensibility was relatively low.
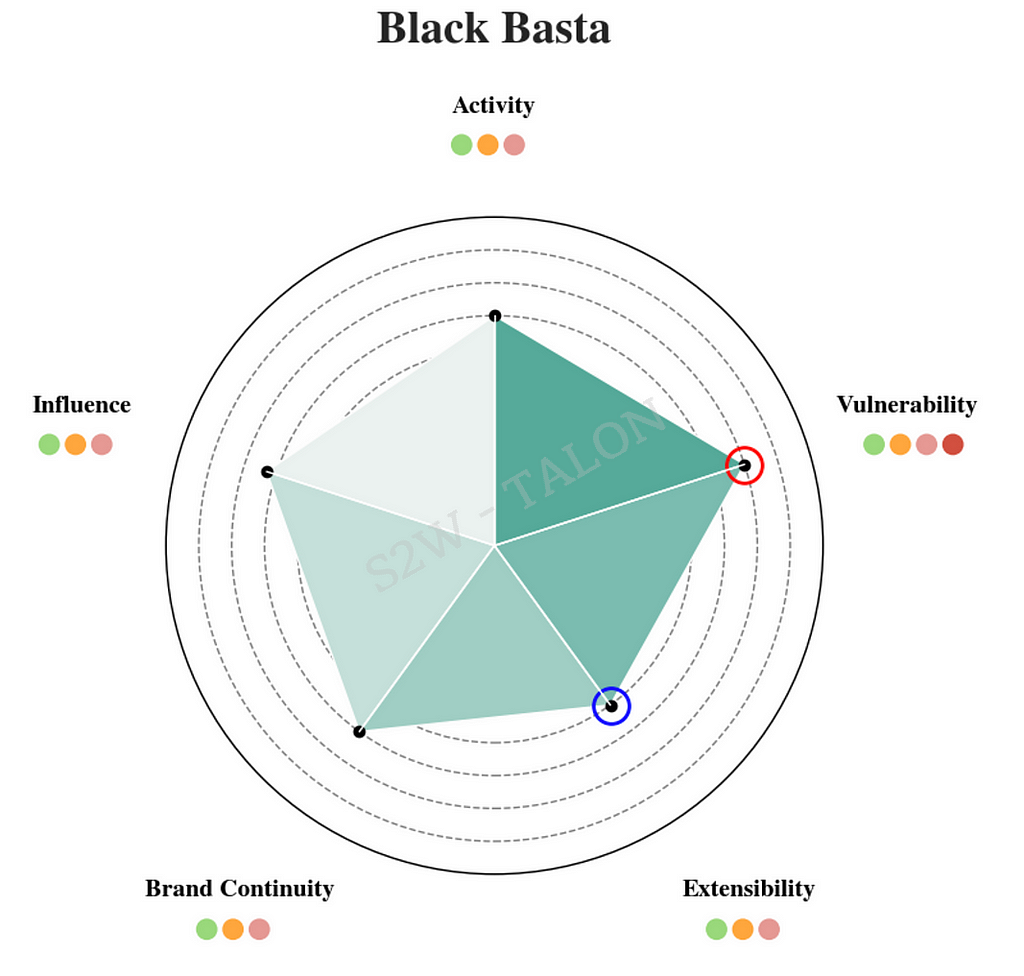 Figure 23. Black Basta Risk Metrics
Figure 23. Black Basta Risk MetricsBlackSuit
BlackSuit was initially ranked 5th in risk before applying the reduction metrics, but after applying them, it rose to 2nd place. BlackSuit is a rebranded group from Royal that operates ransomware for both Windows and Linux. It has been active for over a year, contributing to its high score in Brand Continuity. However, since there were no recorded incidents of exploiting vulnerabilities in the first half of 2024, it was rated lower than other groups in that area.
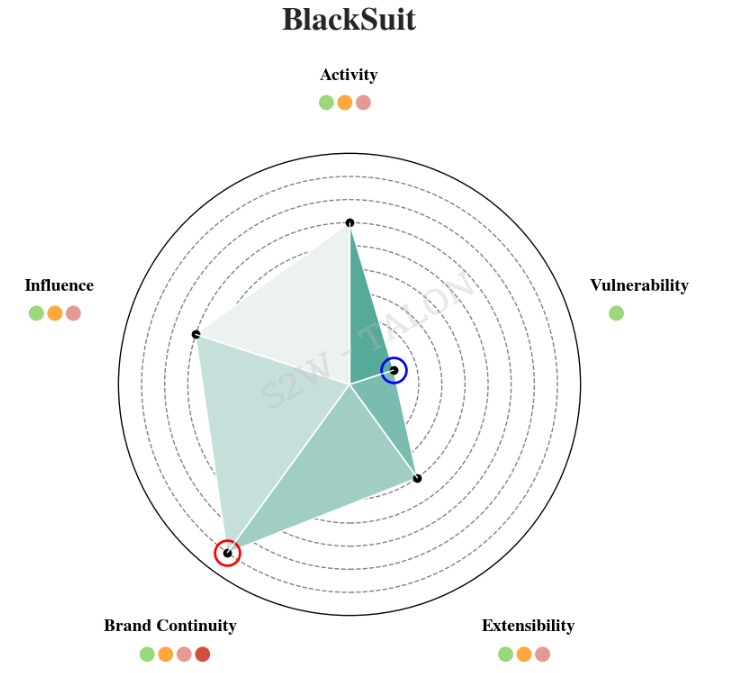 Figure 24. BlackSuit Risk Metrics
Figure 24. BlackSuit Risk MetricsQilin
Qilin was initially ranked 6th in risk before applying the reduction metrics but rose to 3rd after application. Qilin actively promotes its RaaS and recruits affiliates on dark web forums, resulting in a high score for Extensibility. Additionally, the group continuously updates and announces new versions of its ransomware for Windows and Linux, contributing to a high Brand Continuity score. However, due to the absence of vulnerability exploitation during the first half of 2024, it scored lower compared to other categories.
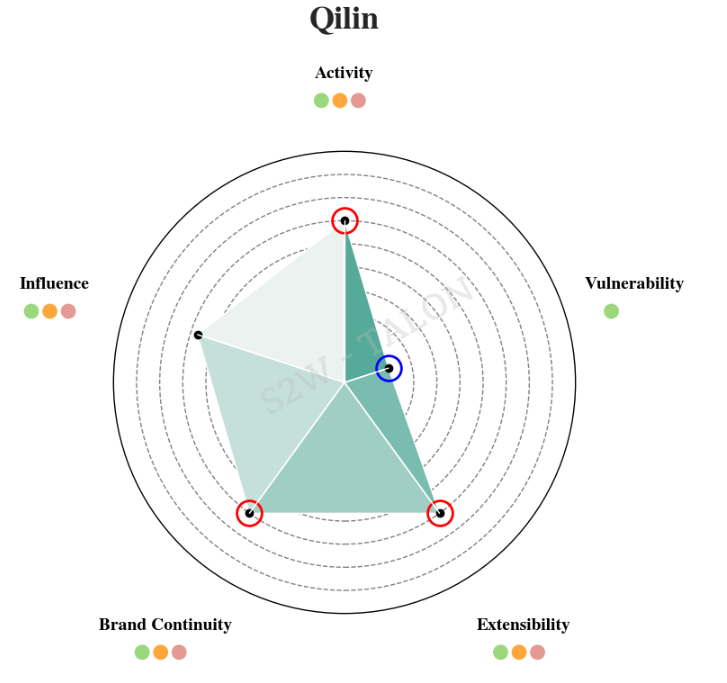 Figure 25. Qilin Risk Metrics
Figure 25. Qilin Risk MetricsRansomhub
Ransomhub initially ranked 7th in risk before applying the reduction metrics, but after application, it climbed to 4th place. Although Ransomhub first appeared in February 2024, it aggressively promoted its RaaS on dark web forums and recruited affiliates such as Scattered Spider, resulting in a relatively high score for Activity. The group was also suspected of rebranding from fallen ransomware groups like Knight and Alphv, contributing to its growing notoriety. However, similar to other groups, there was no record of vulnerability exploitation in the first half of 2024, leading to a lower score in that category.
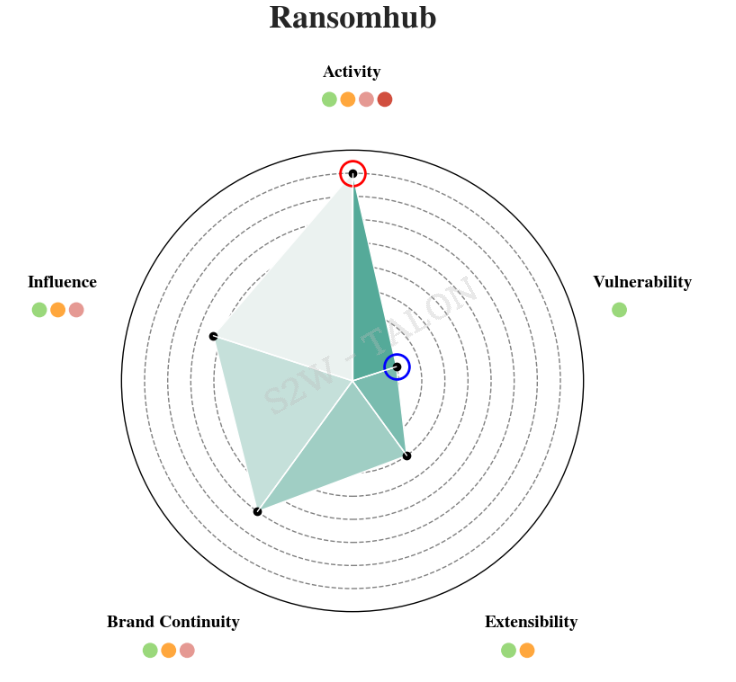 Figure 26. Ransomhub Risk Metrics
Figure 26. Ransomhub Risk MetricsPLAY
PLAY was initially ranked 9th in risk before applying the reduction metrics but moved to 5th place after application. PLAY recorded the second-highest activity level in the first half of 2024, following LockBit. Despite being a relatively new group, appearing in June 2022, PLAY operates closed without promoting itself on dark web forums, resulting in lower scores for Brand Continuity and Extensibility. Furthermore, there was no evidence of vulnerability exploitation in the first half of 2024, which lowered its score compared to other metrics.
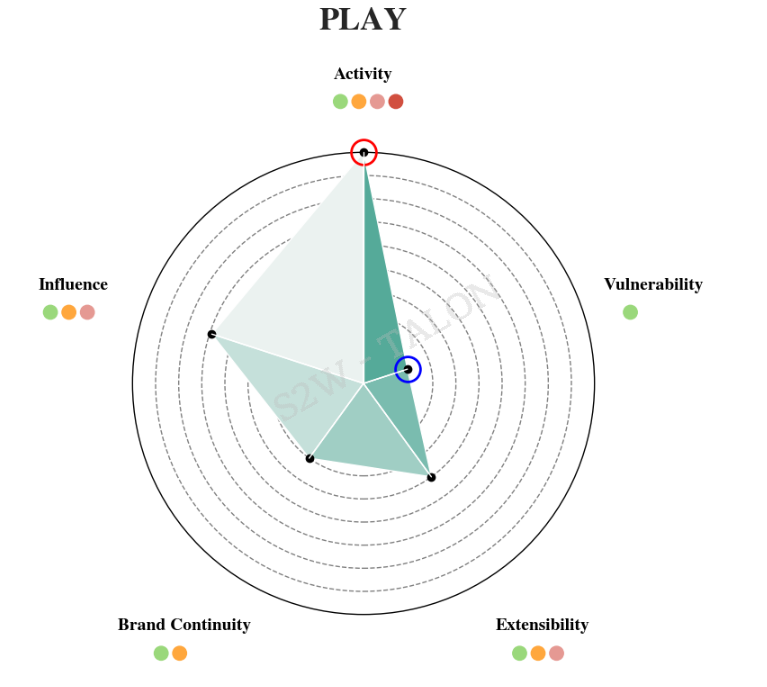 Figure 27. PLAY Risk Metrics
Figure 27. PLAY Risk MetricsConclusion
- Ransomware activity in the first half of 2024 increased by 445 compared to the first half of last year, with an overall increase in ransomware attacks attributed to the following factors.
- A decrease in the volume of ransomware against large enterprises, but an almost 80% increase in the volume against small businesses compared to H1 2023.
- A total of 51 new groups emerged in H1 2024, including new groups Ransomhub and Dark Vault, with Ransomhub being the most active of all new ransomware groups, ranking seventh among all ransomware groups. - Similar to the second half of 2023, ransomware groups in 2024 continued to target highly profitable industries and countries with high GDP.
- Two of the top 10 countries with the most significant increases in ransomware victims are the Middle East and Asia, likely due to the recent wars in the region and the steady growth in GDP since 2022.
- The “RaaS” and “Freelance” boards in the RAMP forum, where job postings for ransomware groups are uploaded, saw a 41.7% increase in posts and comments in the first half of 2024 compared to the second half of 2023.
- In particular, the months of March and June 2024, when we observed a high level of activity on these boards, coincided with a decrease in the number of ransomware attacks compared to the first half of 2023, suggesting that fewer members in ransomware groups may have contributed to the reduction of the number of ransomware attacks in March and June 2024.
- Ransomware mentions are approximately 91% higher in Telegram than in DDW, indicating the need for continued monitoring of ransomware activity within Telegram. - Ransomware groups rebrand to evade law enforcement and market themselves. H1 saw the HelloKitty ransomware rebrand to HelloGookie and possible rebranding between the Eldorado and LostTrust groups.
- Analysis of significant ransomware campaigns in the first half of 2024 shows that ransomware groups and affiliates are using 1-day vulnerabilities to target unpatched environments, with some instances of privilege escalation using vulnerable drivers.
- Using S2W’s proprietary criteria to measure the risk of ransomware groups, the top five most dangerous ransomware groups in the first half of 2024 are Black Basta, BlackSuit, Qilin, Ransomhub, and PLAY.
- Ransomhub is a new ransomware group that emerged in the first half of 2024. Still, its inclusion in the top five highest-risk ransomware groups highlights the need to continue monitoring its future activity.
Ransomware Landscape in H1 2024: Statistics and Key Issues was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Ransomware Landscape in H1 2024: Statistics and Key Issues | by S2W | S2W BLOG | Oct, 2024 | Medium