You don’t always need an in-depth investigation to tell if a file or URL is malicious. In ANY.RUN, the process tree helps you quickly gather essential analytical information.
In this article, we’ll explain what the process tree is, how to use it effectively, and what insights you can gain from a superficial analysis of a sample. By the end, you’ll be able to determine if a file or URL is malicious without having to dive too deep.
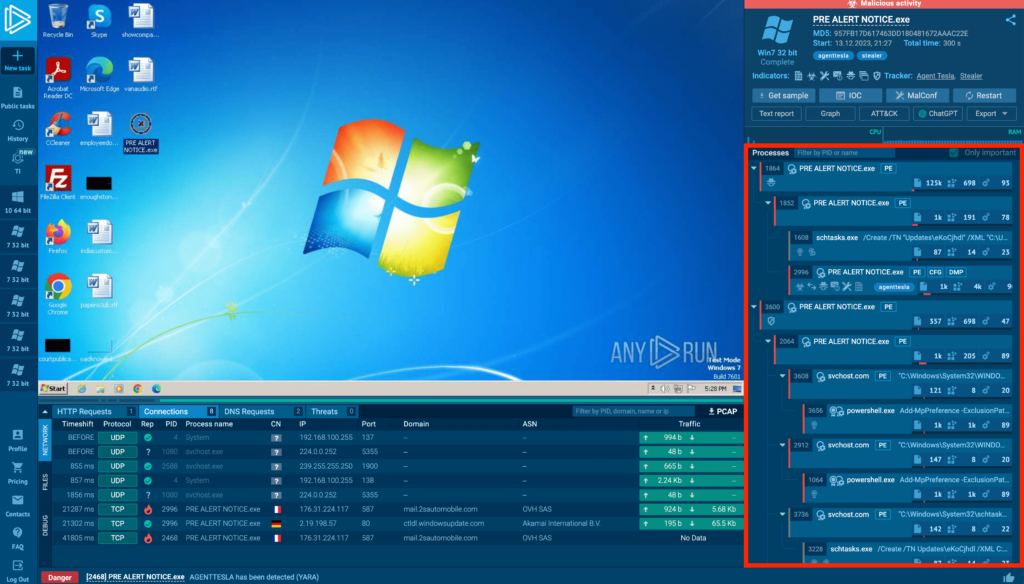 Process Tree in ANY.RUN interactive malware sandbox
Process Tree in ANY.RUN interactive malware sandbox What does ANY.RUN Process Tree do?
It shows a visual representation of all the processes spawned when a file or URL is executed in the ANY.RUN sandbox, as well as how these processes relate to each other.
When you run a sample in the sandbox, ANY.RUN records not only the processes directly created by the sample but also any additional processes those initial ones spawn. This gives you a complete picture of how the sample behaves and interacts with the system.
 The Process Tree helps:
The Process Tree helps:- Understand the sample’s behavior at a glance.
- Quickly identify parent-child relationships.
- Trace the origins of any suspicious activities.
Main features of the Process Tree
The Process Tree doesn’t just show parent-child relationships, but also contains useful tools for analyzing information on the fly. Let’s cover the ones you’re likely to use often:
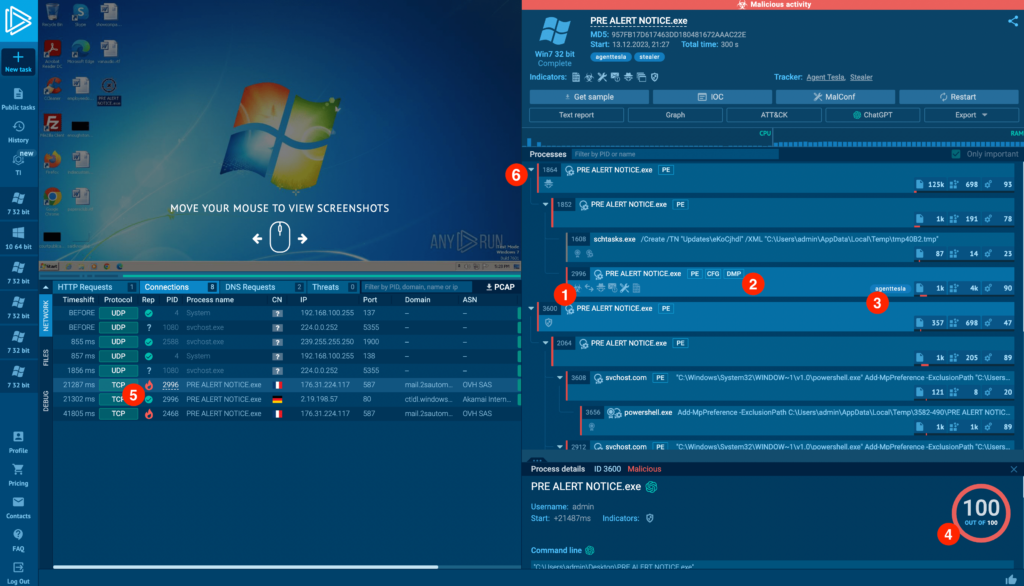 Breaking down features of the process tree
Breaking down features of the process tree - Indicators. Icons that highlight malicious activity that stands out, like credential stealing, schedule task creation, config extraction and so on. Next to them are process signatures.
- Static information. PE information and decrypted memory dumps (DMP) and malware configuration files (CFG) are available by clicking on the corresponding icons.
- Tags. Identify malware families and other threats, such as phishing.
- Score. Calculated based on events created by that process
- Process highlighting. Works across the interface. Hover over PIDs of processes in other tabs, and the corresponding process will be highlighted in the tree.
- Collapsing. Click on the triangle icons to collapse or expand groups of processes.
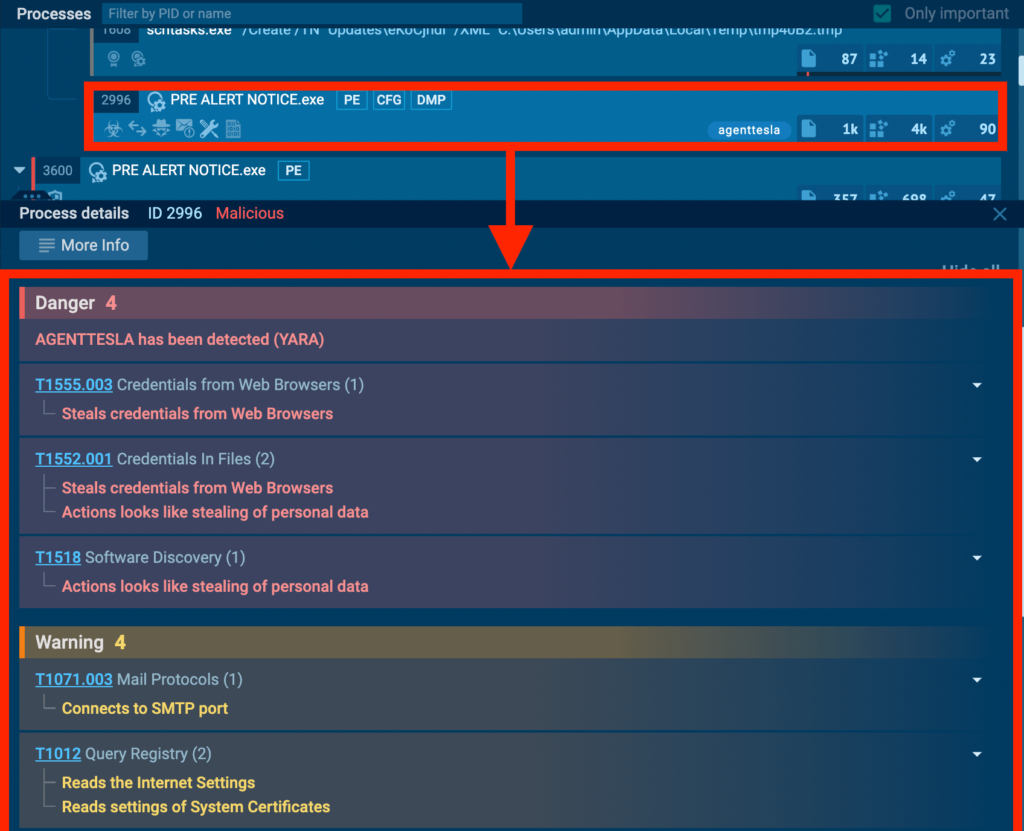 Descriptive actions in the process tree
Descriptive actions in the process tree Clicking on a process opens the Process Details tab, where you can view descriptions and classifications (Dagner, Warning and Other) of events that the process created within the system. We automatically map events to known MITRE TTPs and categorize them into groups ranging from most to least critical. This categorization also drives the malicious score, which we highlighted above.
Identify malicious activity in less than 40s with ANY.RUN
Get started freeWhen is the Analysis of the Process Tree Sufficient on its own?
Let’s say an employee in the SOC department is tasked with checking a sample, like an image in an email, and we’re sure there’s no infection. We just need to figure out if it is safe to open it.
Their first step is to determine whether the object they’re examining is malicious. If you submitted an image for analysis and a binary file executed instead within the virtual machine, then it is clearly a malicious file attempting to mimic an image file by changing its icon and extension.. Even if the malware isn’t detected by YARA or other signature-based tools, process activity will indicate that the object is likely malicious. All you have to do is report it and delete it.
What can we learn from taking a quick look at the Process Tree?
Let’s examine how the Process Tree functions and the information it provides, using this task as an example.
In this case, we’ll focus on analyzing the executable file named PRE ALERT NOTICE. Upon loading the file into ANY.RUN, the following process tree is displayed:
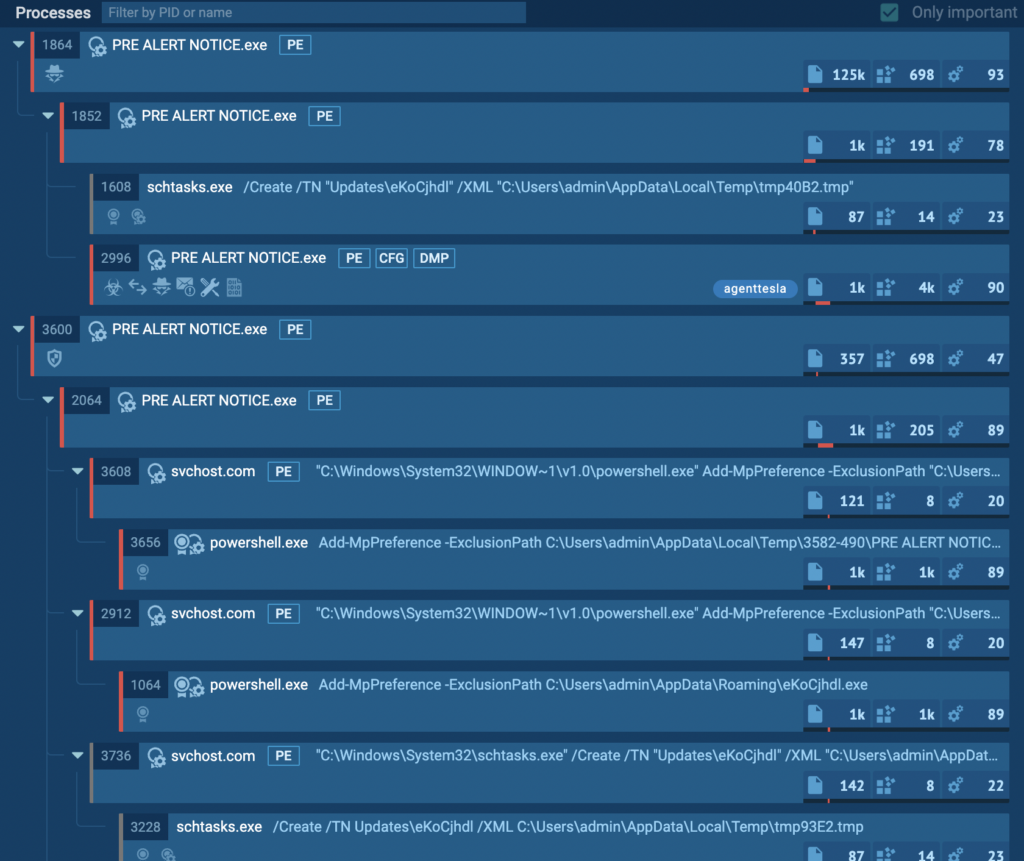 The Process Tree shows what a sample does in the system
The Process Tree shows what a sample does in the system That’s a lot of processes! But there’s no need to be overwhelmed. Let’s start breaking it down bit by bit. First, we’ll identify the process that stands out the most in terms of indicating malicious activity. Let’s focus on this one:
The agenttesla tag immediately stands out, attached to the process with PID 2996 in the screenshot above. This alone is sufficient to determine the malicious process. But for now, let’s continue working down the tree from the top. Two processes in particular warrant a closer look:
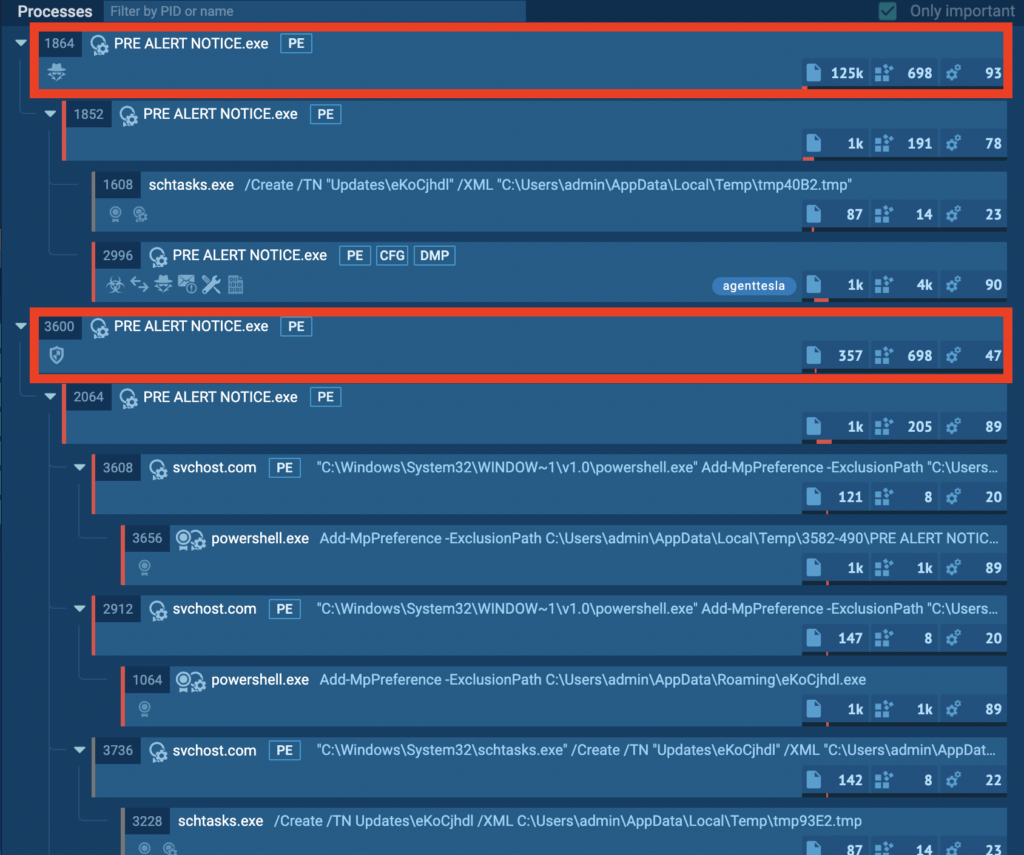
Two separate instances of PRE ALERT NOTICE.exe catch our attention, with PIDs 1864 and 3600 respectively. Each instance appears to be performing distinct actions within the system. Let’s first examine the group of processes spawned by PID 1864:
PID 1864 and its children
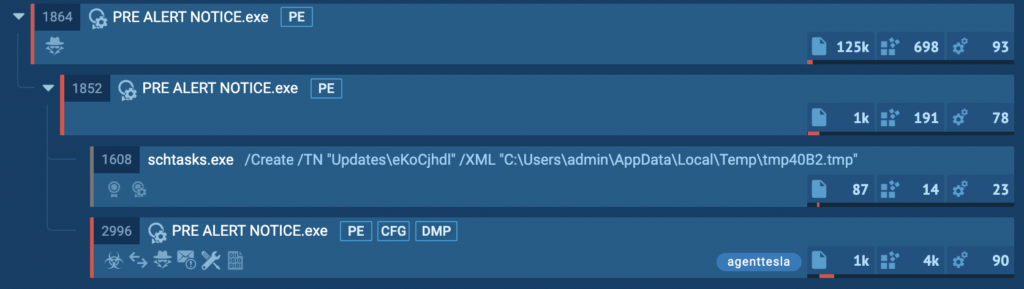
The initial “PRE ALERT NOTICE.exe” process with PID 1864 spawns a child process with the same name.

This child then creates two processes of its own:
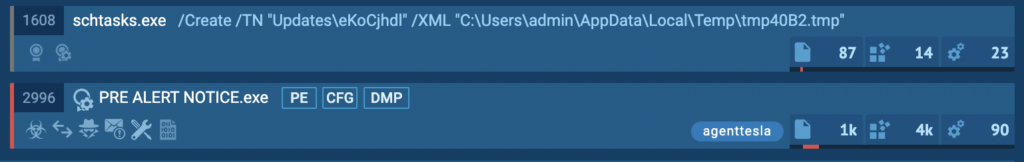
- A scheduled task via shtasks.exe, to achieve persistence or upload the payload into the system.
- One more instance of the PRE ALERT NOTICE.exe process where agenttesla was detected by a tag.
Selecting any of these processes will reveal more detailed information. Let’s take a closer look at shtasks.exe:
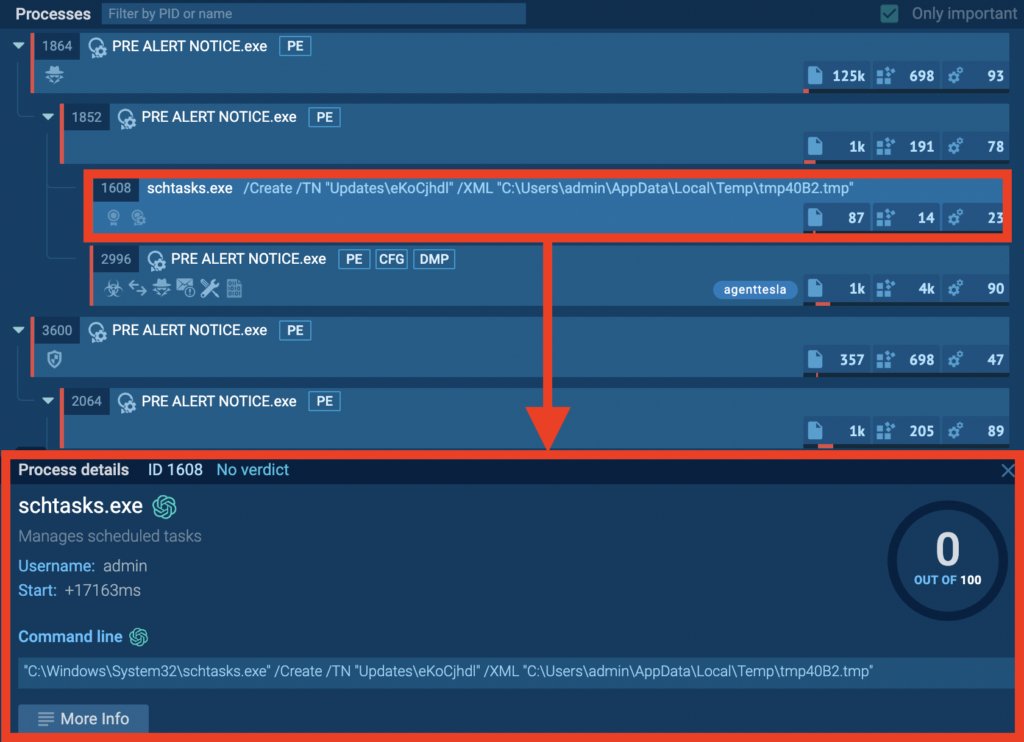
In the tab that appears, we find some useful information. For example, the start time of the process is often valuable. This allows us to see how long a malicious process may have been dormant before it began execution. In this particular case, we can see the time it took for the task launched via schatsk.exe to be created, which was 17163 milliseconds.
We also see a command line that created a new scheduled task named Updates\eKoCjhdl. This task used the definition provided in an XML file located at C:\Users\admin\AppData\Local\Temp\tmp40B2.tmp.
A couple of red flags to note here:
- The task name Updates\eKoCjhdl appears to be randomly generated, which is suspicious.
- The XML definition file is located in the admin user’s temporary files directory (AppData\Local\Temp), rather than a standard system location.
PID 3600 and its children
Also interesting is the group of child processes that PID 3600 creates.
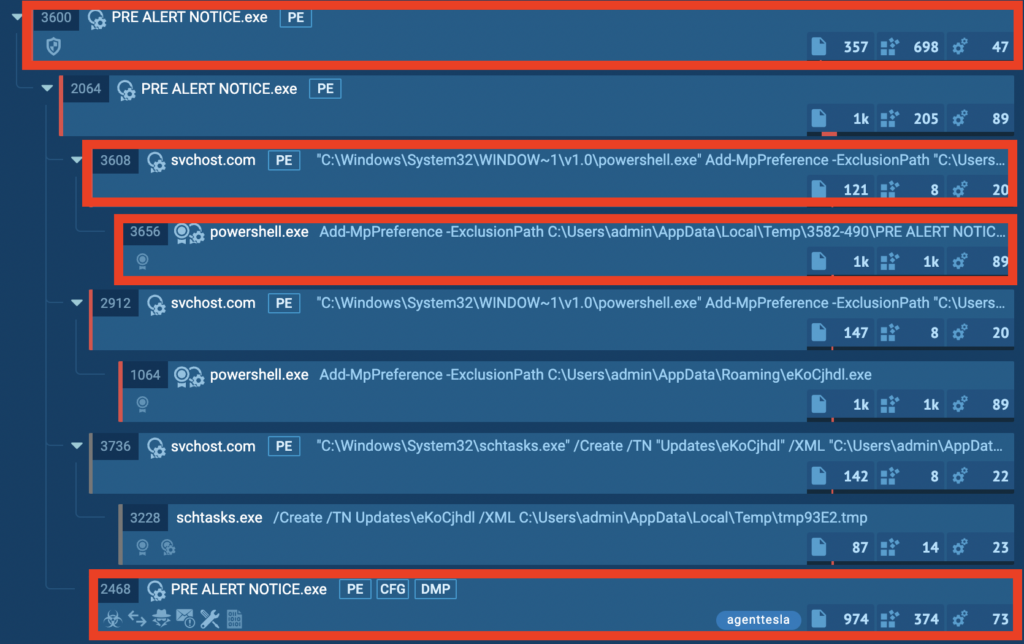
Let’s highlight the noteworthy aspects of the screenshot above.
- The processes named svchost.com mimic the legitimate svchost.exe. The .com extension serves as a red flag.
- These processes spawn powershell.exe instances, which an attacker could potentially utilize to download additional payloads.
- The parent process creates its own instance of the main PRE ALERT NOTICE.exe, effectively infecting the system with an additional copy of the malware.
Alternative view: Process Graph
You may have thought that if the malware launches hundreds of dummy processes to conceal itself and complicate analysis, isolating the primary malicious object in the tree would be challenging. While this holds some truth, ANY.RUN offers an alternative method to visualize the same information — the Process Graph.
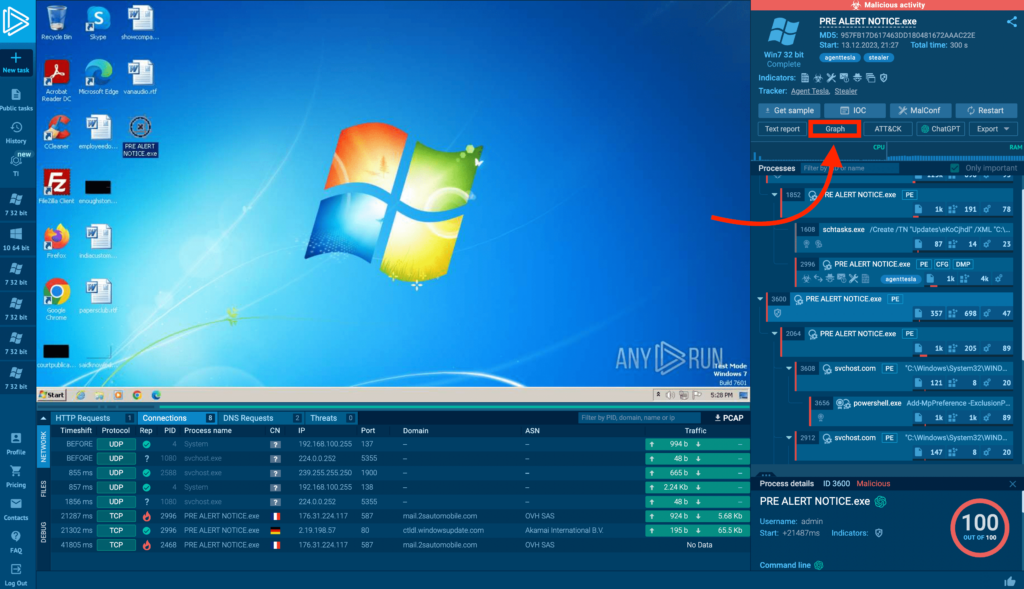
To access the Process Graph, click on the Graph button on the main task page. The report appears as follows:
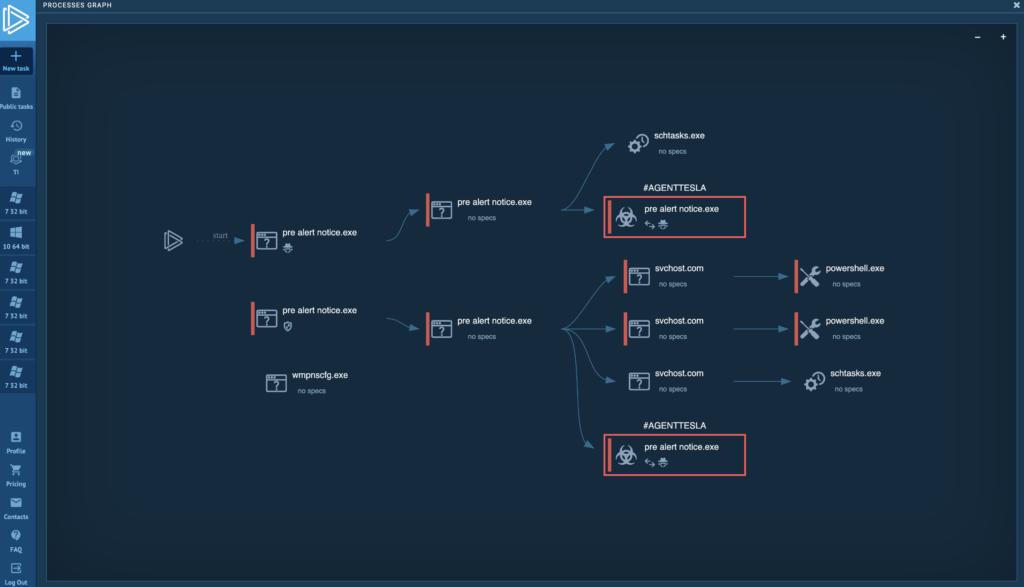
The Process Graph provides a convenient way to visualize the relationships between processes. The canvas can be zoomed in and out, which is particularly useful when dealing with hundreds or even thousands of processes. The color highlighting makes it easy to identify the malicious process.
This report also contains all the same information as the Process Tree — to view the details of a process, simply click on the one of interest. Let’s examine the process flagged with the AGENTTESLA tag:
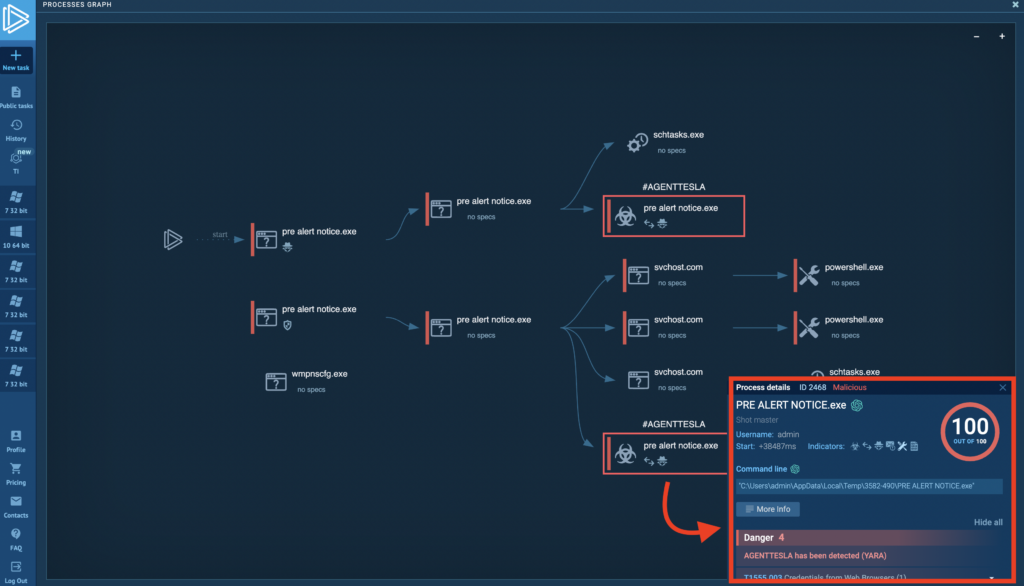
Detailed information will be displayed in the window located in the lower right corner.
About ANY.RUN
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware.
Every day, a community of 400,000 analysts and 3000 corporate clients use our cloud-based platform to analyze Windows and Linux threats.
Integrate ANY.RUN Threat Intelligence in your organization
Contact SalesKey advantages of ANY.RUN for businesses:
- Interactive analysis: Analysts can “play with the sample” in a VM to learn more about its behavior.
- Fast and easy configuration. Launch VMs with different configurations in a matter of seconds.
- Fast detection: Detects malware within roughly 40 seconds of uploading a file.
- Cloud-based solution eliminates setup and maintenance costs.
- Intuitive interface: Enables even junior SOC analysts to conduct malware analysis.
Learn how ANY.RUN can benefit you or your security team. Schedule a free demo with one of our sales representatives, and we’ll walk you through real-world examples.
The post Quickly Check if a Sample is Malicious with ANY.RUN’s Process Tree appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Quickly Check if a File is Malicious with ANY.RUN's Process Tree