In the infostealer ecosystem, there are communities of malware operators spreading their malicious builds on a daily basis, working under a common organization, more commonly known as a team.
In this blog series, I will be exposing very briefly the activity of some of these “traffers teams”: what they did, what they are doing, and what they will do in the future. If possible, I’ll let them talk freely in a quick interview.
Today, an introduction to these guys…


What is a traffer team?
Traffers have been documented in the past:
Traffers: a deep dive into the information stealer ecosystem (sekoia.io)
Also please find an amazing talk by Jiho Kim on this matter:
<a href="https://medium.com/media/2df01c8db534431021b512458d5d9328/href">https://medium.com/media/2df01c8db534431021b512458d5d9328/href</a>FIRSTCON23-TLPCLEAR-Kim-Info-Stealer-Most-Bang-for-the-Buck-Malware.pdf
Teams functionality hasn’t changed over these years; please refer to the resources above for further insights on traffers teams.
These teams have been operating for a long time and are still active at the moment. But how does an actual traffer team work?
Summarizing,
A traffer team offers an attractive solution to those malware operators willing to make some money, under some kind of common organization that will guide you through all the processes. They provide you with everything you need to start working for free, as simple as that. Also, newcomers are welcomed, and because of this, this is usually the starting point for some of these new threat actors.
The vast majority of these traffers teams can be found in the Russian-speaking internet ecosystem. That should be a reason why most of these organizations follow the “not work with CIS countries victims” rule, although we can find some of them not following this statement.
They promote their services on forums, attracting users to join them because their user base is from forums. In fact, when applying to join a traffer team, it is usually mandatory to send a profile link to a forum, being the most used forum the “LOLZ guru” aka Zelenka. Forums also have their rules, and those teams that don’t follow these rules aren’t allowed to promote on these forums, although many of their users can be found there.
If we look at each one of these traffer teams promoting on forums, we can group them by the activities they are doing: working with infostealers, working with crypto drainers, and working with scams. Although most of the teams specialize in only one activity among these groups, some of them mix activities from other groups. In this blog series, I will focus on those teams working with infostealers, although I will try to expose some of the other groups working with crypto drainers and related.
Profits
Traffers are getting a lot of profits, both for the workers and the team staff.
Talking about infostealers, the main profit for team users is the amount of cryptocurrencies that a wallet stolen on a log can have. Other profit is made from custom requests on the same logs, for example:
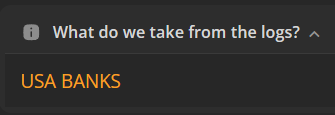
In fact, as you work for a team, you will be provided with the logs you have made, but these logs will never be private to you because the administration will have access to them too, and they will make their own profit with their own processing.
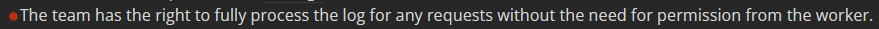
If we talk about crypto drainers, profits are shared on a % to both workers and staff.
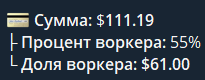 Example (55% payout to a worker)
Example (55% payout to a worker)So who is really making a huge profit on these teams? Indeed, the staff.
In the next releases, I will expose from where each traffer team is getting their own profit.
Traffickers teams digital infrastructure
Traffers rely on Telegram to develop their activities. The whole team is managed on Telegram via a bot and channels, where “workers” meet each other and “work”.
The Telegram Bot, operational brain
Everything starts with an application to a Telegram bot, where new people who want to join the team answer some prepared questions. Depending on the team, some of these applications will need further approval by an administrator, or you may be accepted directly into the team without prior checks. Questions in the application are almost always the same, asking “from where you found our team, “why you want to join”, and any prior experience in the activities done by the team.
Once approved, the newly accepted user on the team will have the right to use every resource provided by the team, including infostealers’ build generation, SEO tools, etc., for free.
These bots have the same functionality as those described by researchers in the past. I will describe individually the bots used by traffers teams once I talk about them in further releases.
The newly accepted worker will also have access to (almost usually) private channels related to the team, being the most common of these a chat and a ОТСТУК channel.
ОТСТУК channels — Mortality Census
“Отстук” is a Russian slang word that is translated to “knock time” or “successful execution rate”.
Despite the meaning, what you can see in a Отстук channel is supposed to be a full count of the victims of the builds generated from the Telegram bot and directly related to workers on a team.
I am talking about several dozens of thousands of records of the activity of these traffers teams available on these channels. Talking about infostealers, on a scale that can reach more than a million records of victims in a time stamp of ~2 years.
Indeed, traffers represents such a threat, and they are one of the main suppliers of the infostealers log market.
These records will be featured in the individual reports of each traffer team in further releases.
Other Resources — Educational Resources
Every traffer team promises to “train” you in the criminal activities they do so you can start working for them as a beginner. These trainings are given by some kind of manual or similar, written by the administration of these groups or by relevant workers on a team.
I will discuss the manuals provided of each traffer team in further releases.
Workers
Several dozens of thousands of records implies hundreds of users “working” on a team.
Profiling the total number of unique users that have participated in the activities of a team would be a very hard task, because some of these records hide the username of the user who “did the job” or because of changes in the username of an individual in a poor attempt to hide his activities.
Sometimes the staff can also be seen working for the team as another worker, but this is unusual. Hundreds of users working for the same guys and making them rich is the best “passive income”.
I will talk about the disclosed usernames and the total number of victims that these traffers have made for the sake of his traffer team in further releases of these blog series.
flip a coin, choose heads or tails

(Not) The end ;)
Expect more content, soon.
Best regards,
Article Link: Profiling Трафферы: An introduction to Traffers Teams | by g0njxa | Mar, 2024 | Medium