

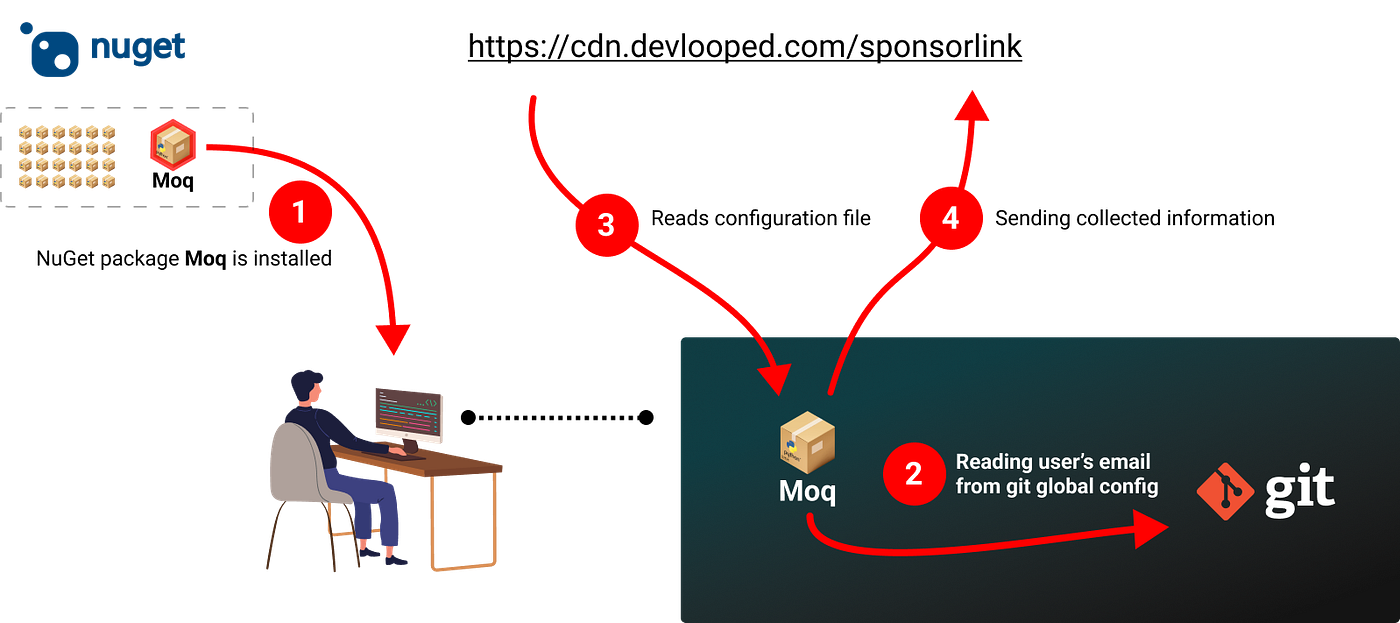
The highly popular NuGet package, Moq, with total downloads of 475M+, released a new versions 4.20.0 and 4.20.1 on August 8th with a new sub-dependency that has hidden executable code that reads the user’s local git config, extracting the developer’s email address, hashing it, and sending it to a cloud service.
This incident was reported yesterday by Reddit user u/DinglDanglBob and also reported on the project’s GitHub page as an issue.
About Moq
Moq is a highly popular open-source project to provide a mocking library for .NET applications. From the project’s GitHub page:
Moq (pronounced “Mock-you” or just “Mock”) is the only mocking library for .NET developed from scratch to take full advantage of .NET Linq expression trees and lambda expressions, which makes it the most productive, type-safe and refactoring-friendly mocking library available. And it supports mocking interfaces as well as classes. Its API is extremely simple and straightforward, and doesn’t require any prior knowledge or experience with mocking concepts.
Moq’s New Sub-Dependency – “SponsorLink”
Since version 4.20.0 of Moq, Devlooped.SponsorLink NuGet package has been added as a new dependency.
As it turned out, Devlooped.SponsorLink is a closed-source project, provided as a compiled dll with obfuscated code, which scans the git config and sends the hashed email of the current developer to a cloud service. This code is executed during the application build and if you are depends on Moq there is no option to disable this.

Obfuscated Code
User account d0pare commented and found that the library spawns an external git process to get the developer’s email from the command git config --get user.email , then does some hashing and sends the result to hxxps://cdn.devlooped[.]com/sponsorlink.
private static string \u00a0(string P_0) {
try {
Process process = Process.Start(new ProcessStartInfo(
// this is obfuscated value of "git"
6FA47342-3716-4274-AF01-7A37793E0E97.\u206f(),
// this is obfuscated value of "config --get user.email"
6FA47342-3716-4274-AF01-7A37793E0E97.\u3000()
) {
RedirectStandardOutput = true,
UseShellExecute = false,
CreateNoWindow = true,
WorkingDirectory = P_0
});
process.WaitForExit();
if (process.ExitCode != 0) {
return null;
}
return process.StandardOutput.ReadToEnd().Trim();
} catch {}
return null;
}
He later discovered that the library also loads settings from the URL hxxps://cdn.devlooped[.]com/sponsorlink/settings.ini and is evasive in case one of the following environment variable exists
CI
TF_BUILD
TRAVIS
BUDDY
TEAMCITY_VERSION
APPVEYOR
JENKINS_URL
Users Looking For Alternatives
And I don’t blame them. Many users seem concerned about GDPR compliance as their products are built using Moq. This user commented that he won’t be able to use this package any more:
This is a serious GDPR breach, and we won’t be able to continue using this lib.
Also, having an obfuscated package included means that we can’t (easily) know what is happening. It could harvest any other information from a developer’s machine without any user consent.
Another user, SefaOray also commented:
We are removing moq immediately due to this.
and many more similar comments in this GitHub thread..
The Maintainer’s Response
GitHub user account kzu, the author behind this, commented that it was simply part of testing, and he wonder “why so much anger over sponsoring which can be done with as little as $1”

After posting this message, kzu probably panicked and decided to revert and unpublish versions 4.20.0 and 4.20.1 while quickly publishing 4.20.2without the new dependency in Devlooped.SponsorLink NuGet package.
Summary
Yesterday the owner of the popular NuGet package Moq incorporated a new sub-dependency, which exfiltrates the user info without his consent to hxxps://cdn.devlooped[.]com — a domain owned by the author of the Moq.
This sparked a debate on Reddit and GitHub, leaving many concerned users accusing this action of GDPR violations and statements regarding the legitimacy of his action.
Many organizations that built software using those releases are exposed to GDPR compliance.
In my opinion, the author did not intend to cause any harm but ended up damaging the trust of his users. This could have been prevented if it had been open for discussion prior to publishing the new changes and accepting the content of his users.
We must understand that it’s our responsibility when we use open source. This is why we need to support open-source maintainers in order to have a healthy open-source ecosystem.
Timeline
2023–01–24: Author published a blogpost suggesting a new solution to open source sustainability using the SponsorLink service2023–02–04: Devlooped.SponsorLink first release to NuGet2023–08–08: Moq released new versions 4.20.0 and 4.20.1 with Devlooped.SponsorLink as a dependency2023–08–09: Moq released version 4.20.2 removing the Devlooped.SponsorLink dependency
IOC
hxxps://cdn.devlooped[.]com/sponsorlink
Packages
Other NuGet Packages using Devlooped.SponsorLink
devlooped.cloudstorageaccount.source
devlooped.tablestorage
devlooped.cloudstorageaccount
devlooped.sponsorlink
isbn
gitinfo
thisassembly.assemblyinfo
thisassembly.constants
thisassembly.project
thisassembly.git
thisassembly.strings
thisassembly.metadata
thisassembly.resources
nugetizer
devlooped.credentialmanager
websocketeer
websocketchannel
devlooped.web
packagereferencecleaner
mvp.xml
devlooped.dynamically
thisassembly
The post Popular NuGet Package “Moq” Silently Exfiltrates User Data to Cloud Service appeared first on Checkmarx.com.
Article Link: Popular NuGet Package “Moq” Silently Exfiltrates User Data to Cloud Service