Polyfill Fuels Supply Chain Concerns with Malicious Redirects: +100,000 Websites Affected
Researchers have issued a warning about a new supply chain attack originating from the Polyfill[.]io service. Alarmingly, this attack has affected at least 100,000 websites.
Polyfill is an open-source library that ensures your website’s code remains functional even in outdated browsers. By using Polyfill, older browsers can support modern features, allowing users to access the same functionalities as they would on newer browsers.
What Caused the Polyfill Supply Chain Attack?
The supply chain attack linked to Polyfill[.]io began after a Chinese company, “Funnull,” took over its domain and altered the script to reroute users to malicious websites.
Sansec warned about this on June 25, 2024, reporting that Funnull acquired both Polyfill’s domain and its GitHub account in February 2024, using the compromised domain to spread malware to mobile devices via any site utilizing “cdn.polyfill.io.”
The Polyfill[.]io service was redirected to polyfill.io.bsclink.cn, which is controlled by Funnull. As a result, developers who embed cdn.polyfill.io scripts inadvertently pull code from Funnull’s site, causing visitors to be redirected to unwanted destinations.
Numerous complaints regarding the subject surfaced on GitHub, though they were swiftly removed. An archive of these comments is available here for further context.
Capabilities of the Malicious Script
In observed cases, the script directed users to scam sites by using a fake Google Analytics domain or other redirect URLs (see the IoCs section). Researchers mention that this script is resistant to reverse engineering, which makes it difficult to analyze.
Sansec researchers mention that the script is resistant to reverse engineering, which makes it difficult to analyze. It activates only on specific mobile devices, at certain times, and remains inactive when detecting an admin user, delaying execution if a web analytics service is found, in order to evade detection.
At this point, the cdn.polyfill.io domain redirects to a Cloudflare mirror. Yet since the DNS servers for the domain remain the same, the owners can revert to their original domains.
What Is the Scope of This Supply Chain Attack?
More than 100,000 websites currently embed Polyfill using the “cdn.polyfill.io” domain. Given that each of these sites could attract thousands of visitors daily, the risks are substantial, highlighting the extensive impact of this supply chain attack.
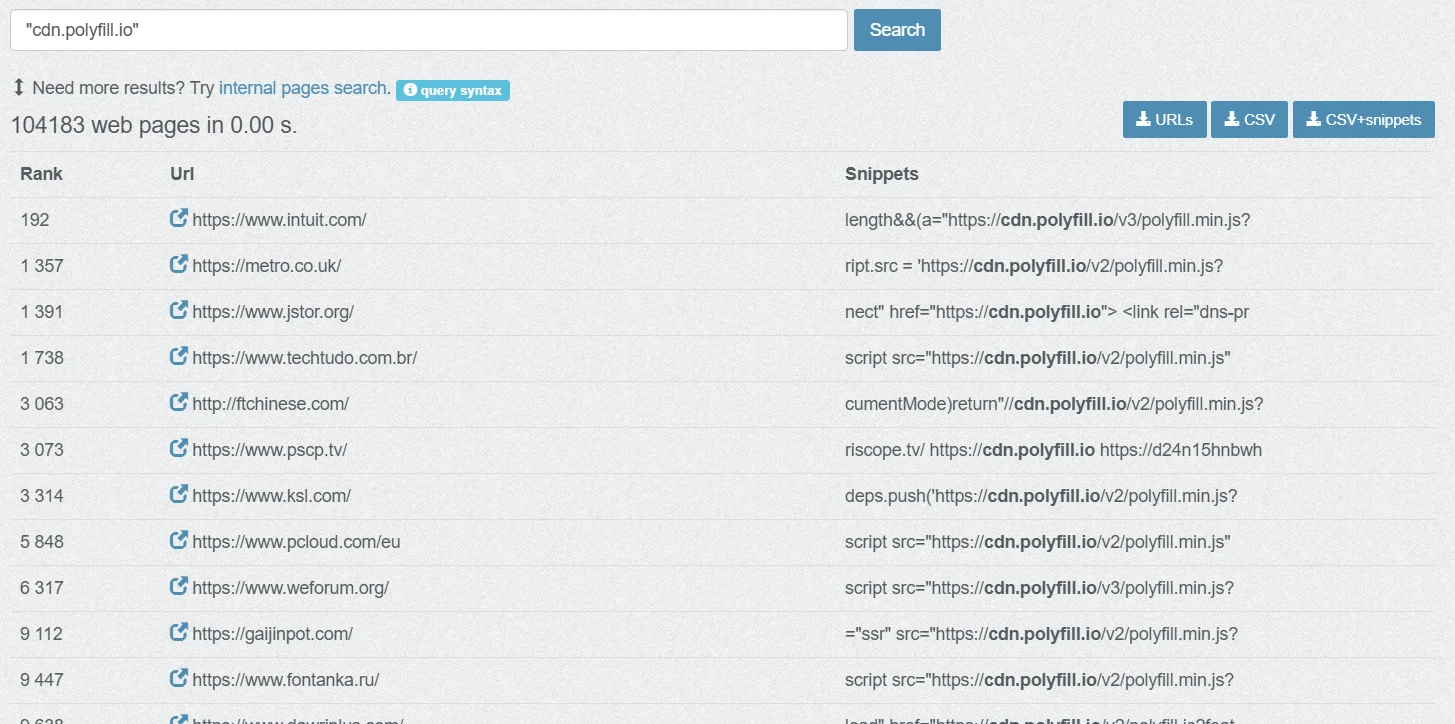
Results for websites using “cdn.polyfill.io” (PublicWWW)
Can’t Use Polyfill; Here’s What to Do
Due to the severity of the issue, Andrew Betts, the original author of Polyfill, advises against using Polyfill altogether, as modern browsers no longer need it. He emphasizes that it should be removed ‘immediately’.
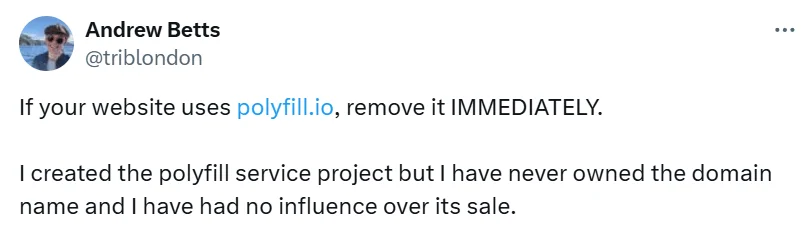
Tweet by the author (Source: X)
Betts further states, “No website today requires any of the polyfills in the polyfill[.]io library. Most new web platform features are quickly adopted by all major browsers. Exceptions, like Web Serial and Web Bluetooth, generally can’t be polyfilled anyway.”
With developers reporting that Polyfill is redirecting to specific wallet sites or delivering ambiguous eval code, its use is completely inadvisable.
For those needing similar services, Cloudflare and Fastly offer alternatives to Polyfill. It is recommended to use services from these trusted providers or to self-host the repository to minimize the risk of a supply chain attack.
Google’s Warning
Google has issued a warning that landing pages containing the malicious code can redirect visitors away from the intended site without the website owner’s knowledge or permission. Consequently, the Google Ads for e-commerce sites using Polyfill[.]io are now being blocked.
Additionally, Google reports that Bootcss[.]com, Bootcdn[.]net, and Staticfile[.]org have also been found causing unwanted redirects, potentially expanding the scope of the supply chain attacks.
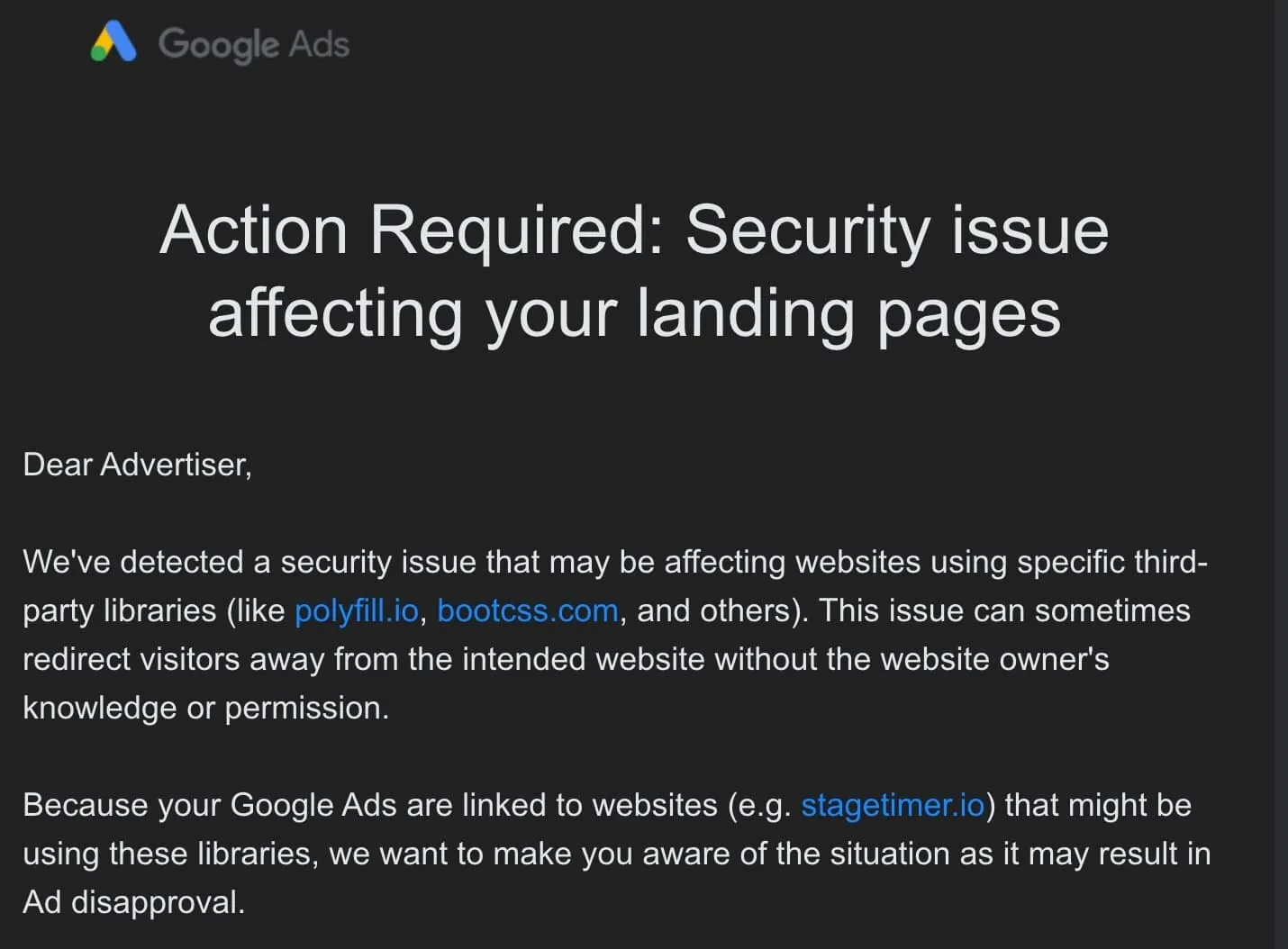
Google Ads alert (Source: X)
Nevertheless, the Polyfill[.]io service remains active, continuing to pose a significant threat.
Indicators of Compromise (IoCs) Related to Polyfill Supply Chain Attack
- hxxps://kuurza[.]com/redirect?from=bitget
- hxxps://www.googie-anaiytics[.]com/html/checkcachehw.js
- hxxps://www.googie-anaiytics[.]com/ga.js
Attackers often exploit third-party vendors, tools, and services in supply chain attacks to distribute malware. To prevent these threats and enhance your security posture, SOCRadar offers the Supply Chain Intelligence module.
This module alerts you on companies that have been targets of cyberattacks, provides actionable intelligence, and ensures you stay protected from weaknesses in your supply chain.
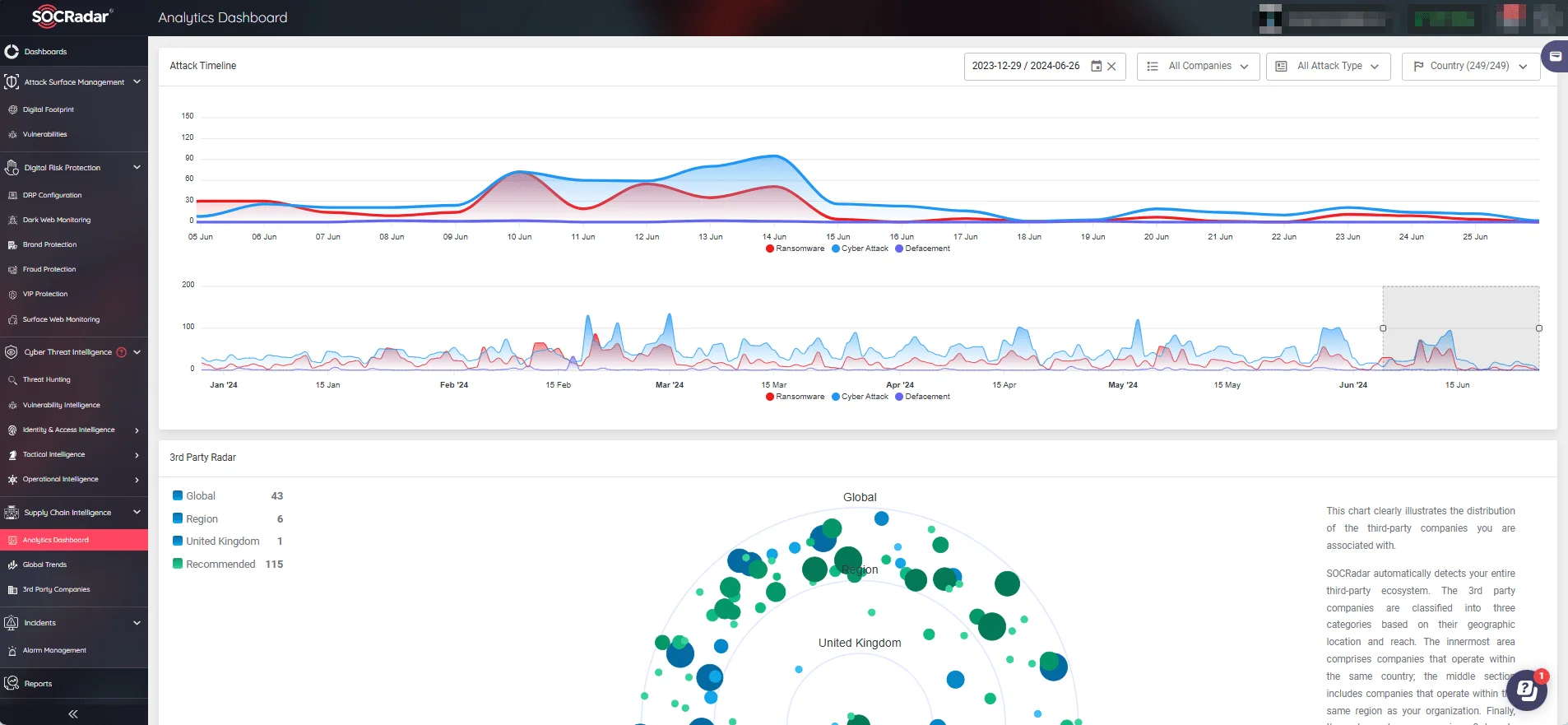
SOCRadar’s Supply Chain Intelligence module, Analytics Dashboard
Infected WordPress Plugins Raise Threat of Supply Chain Attacks
Numerous WordPress plugins have been injected with malicious PHP code, which exfiltrates database credentials and allows creating new unauthorized administrator accounts.
Reportedly, a malicious threat actor compromised the source code of these plugins, including those listed below:
- Social Warfare
- Affected versions: 4.4.6.4 to 4.4.7.1
- Fixed version: 4.4.7.3
- Blaze Widget
- Affected versions: 2.2.5 to 2.5.2
- Fixed version: 2.5.4
- Wrapper Link Element
- Affected versions: 1.0.2 to 1.0.3
- Fixed version: 1.0.5
- Contact Form 7 Multi-Step Addon
- Affected versions: 1.0.4 to 1.0.5
- Fixed version: 1.0.7
- Simply Show Hooks
- Affected versions: 1.2.1 to 1.2.2
- No available fixes
Wordfence advises users to uninstall the compromised plugins and perform a thorough malware scan. While one plugin still lacks a fix, current evidence indicates that the issue is confined to the five identified plugins, though other WordPress plugins could potentially be affected.
How Did the Threat Actor Infect WordPress Plugins?
The attack was discovered by Wordfence, and a CVE identifier was publicly assigned on June 24, 2024: CVE-2024-6297 (CVSS: 10/10). The injections took place between June 21 and June 22, however, how the threat actor accessed the source code of the plugins is still unclear.
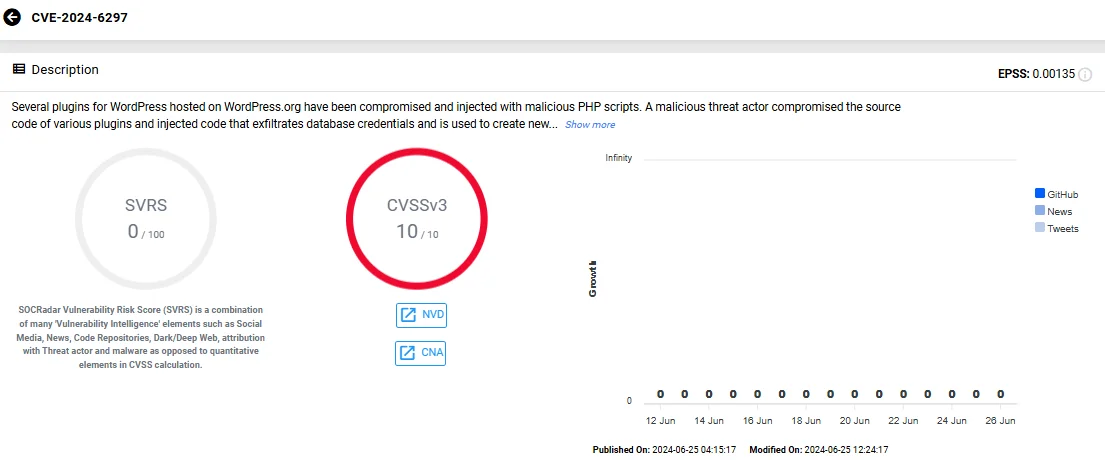
Vulnerability card of CVE-2024-6297 (SOCRadar Vulnerability Intelligence)
The injected malware attempts to create new administrative user accounts and sends those details back to an attacker-controlled server. Additionally, the threat actor injected malicious JavaScript into websites’ footers, adding SEO spam throughout the site. The data is transmitted to the IP address 94.156.79[.]8, with the arbitrarily created admin accounts named “Options” and “PluginAuth.”
Exploiting these plugins, malicious actors could create new administrative accounts on WordPress websites, compromise sensitive data, and serve malware to website users.
This development coincides with the release of WordPress 6.5.5, which provides urgent security updates related to several other vulnerabilities, exposing millions of WordPress-powered websites to Cross-site Scripting (XSS) and Path Traversal attacks.
Indicators of Compromise (IoCs) Related to Compromise of WordPress Plugins
Attacker-controlled server’s IP address:
- 94.156.79.8
Known usernames of attacker-generated administrative user accounts:
- Options
- PluginAuth
Monitor and Strengthen Your Supply Chain Security with SOCRadar
SOCRadar provides the much-needed Cyber Threat Intelligence (CTI) to empower your organization against cyber incidents, providing proactive insights into potential threats.
CTI solutions like SOCRadar enhance supply chain visibility by mapping the attack surface, offering early vulnerability detection, and assisting in implementing effective cybersecurity measures.
SOCRadar’s Supply Chain Intelligence module provides you with real-time cybersecurity updates, reports, and alarms, ensuring you remain informed about emerging threats targeting your organization’s supply chain.
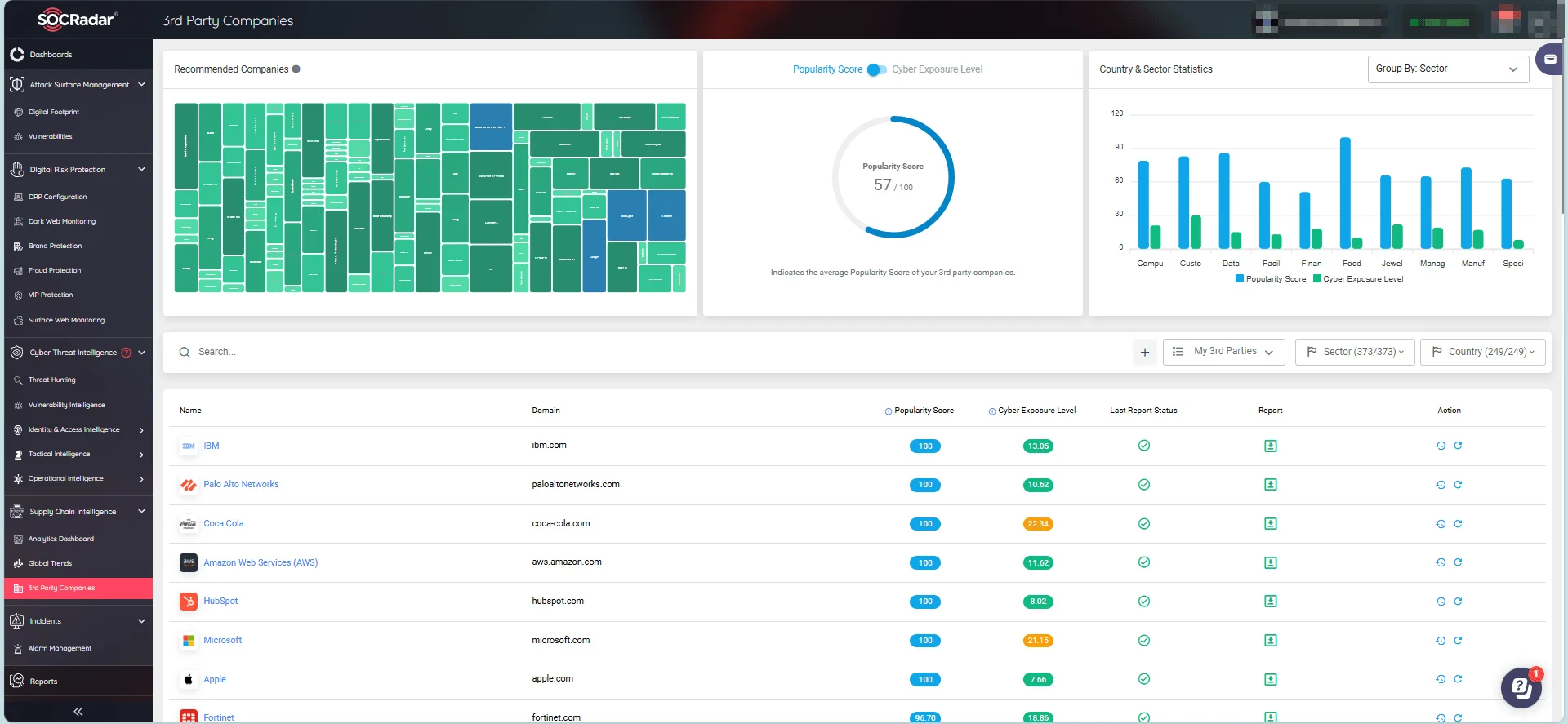
SOCRadar’s Supply Chain Intelligence module, 3rd Party Companies
Additionally, the platform provides insights into global trends for country and sector-specific attacks, enabling you to forecast and defend against supply chain threats.
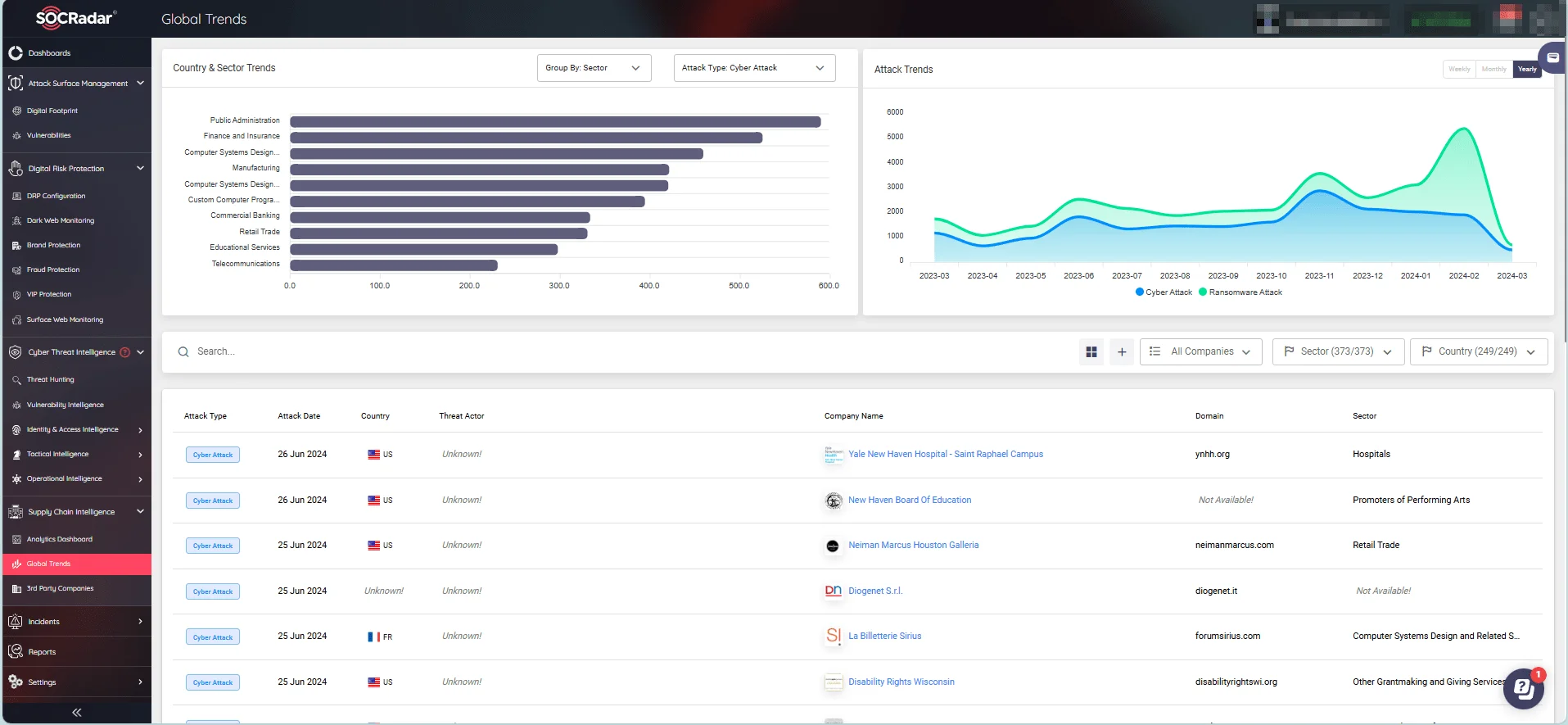
SOCRadar’s Supply Chain Intelligence module, Global Trends
Article Link: https://socradar.io/polyfill-fuels-supply-chain-concerns-with-malicious-redirects-100000-websites-affected/
