Beginning this month, versions 5.6 and 7.0 of the server-side scripting language PHP will reach end-of-life and will no longer be supported. That means websites using these versions of PHP will run on a platform that no longer receives updates or patches, leaving them extremely vulnerable to hacks and data exposure.
Sites running PHP 5 should update to newer, supported versions of PHP 7.2 immediately, but many lack the visibility into their internet-exposed attack surface that helps these organizations identify assets running PHP and upgrade to the latest version if needed.
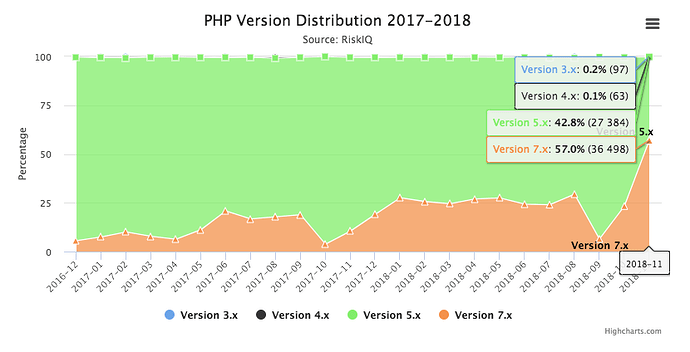
Just how prevalent is this now outdated version of PHP? Of the 78.9% of all the websites using PHP, 59.6% of them using Version 5. According to RiskIQ telemetry data, 55,714,034 of the sites we crawled all-time ran version 5, and 11,612,312 since the start of 2018.
However, sites are beginning to upgrade. In the graph below, you can see a spike in PHP version 7 adoption, likely in a last-ditch effort to upgrade before the end-of-life:
What are the consequences? There have been several vulnerabilities like this that led to high-profile compromises through the malicious modification of third-party hosted code. For example, jquery.com, the JavaScript provider, was compromised but the subsequent breach was identified before the JavaScript libraries were modified. Recently, a new Drupal vulnerability was disclosed prompting the need for patching on thousands of hosts.
Vulnerabilities in site dependencies can result in threat actors gaining access to thousands, and in the case of PHP version 5, potentially millions of sites at once. Recently, a group under the now-infamous Magecart umbrella skimmed payment information entered into forms on Ticketmaster’s various websites by hacking third-party components shared by many of the most frequented e-commerce sites in the world.
Unfortunately, many security teams have a blind spot comprised of unknown and unmanaged internet-facing assets that often act as inroads for cyber attacks and data breaches from outside the firewall. They need is a system which continuously monitors their web assets and with a scanning tool that can be automatically updated with the latest intelligence about new vulnerabilities as they’re discovered, such as outdated versions of PHP.
While organizations may not be able to patch these vulnerable platforms themselves, visibility into the scope of the impact on an enterprise allows an organization to make an informed risk decision, as well as help them manage and understand their overall risk. This visibility can enable them to establish a defense and mitigation strategy much faster than they’ll be able to execute on patching.
Sites that are still using PHP 5.6 should contact their hosting provider and push them to support a secure version of the language. For help identifying if you’re vulnerable following the PHP version 5 end-of-life, contact us today.
The post PHP Version 5 End of Life: Millions of Websites are About to Become Vulnerable appeared first on RiskIQ.
Article Link: https://www.riskiq.com/blog/external-threat-management/php-version-5-end-of-life/