Our sample today comes from Ahmet Payaslioglu AT_Computeus7 in This twitter thread.
I was tagged along with a few other people that may be interested in the sample.
The main file was run on AnyRun Here. This is where I downloaded that from.
I also downloaded the 2 pastebin files that were referenced before they have a chance disappear.
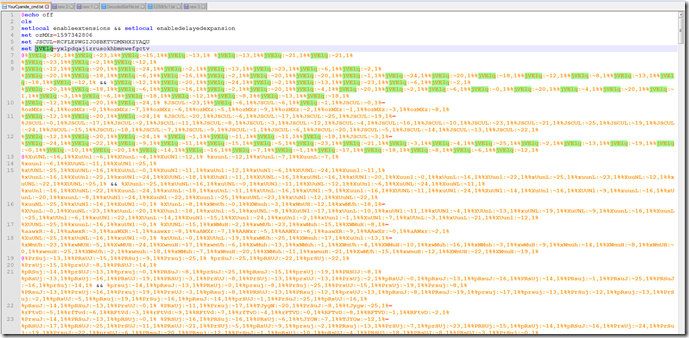
Let’s take a look at the main file downloaded.
There are several thing we see here. I’ve been calling these Environmental variable like like because of the values are surrounded by 2 “%” percent signs like this %jVElq:~20,1%. But I guess the technical term would be Delayed Expansion.
We can see where it is enabled here.
The next thing is the set values.
These are basically Alphabets that the numeric value will index from and return a char or string depending on the values.
Here we can see how each of those parts work to build a string.
Here we can see a couple of things. There are several “@” symbols showing on the left side spread out and the matches for the variable name seem to stop at the “@” symbol.
That can be an indication there are multiple levels of encoding/obfuscation at work here.
Here we can see the result of each layer getting decoded to produce the strings/ Alphabets to decode the next layer.
There were a total of 10 layers to get this to fully decode.
The tools I had were close but not close enough to decode these layers so I wrote a new one.
Experimenting with Reg-X to make it easier to find the the “Matching” values.
Here is what I used. %jVElq:~[0-9]+,[0-9]+%
In my decoder I had to allow for changing the name so that looks like this.
Dim Pattern As String = “%” & Name & “:~[0-9]+,[0-9]%”
Here we can see it did a pretty good job of finding and replacing the values.
This tool will only work on 1 name/ value at a time so you have to start at the top and work your way down on the name/Alphabet. You also have to copy the result from the output back to the input to get it fully decoded. Yes I got lazy and didn’t add a button to do that.
Once we get the first layer decoded we see the second and that is where my tool failed.
So what was going on?
Take a closer look. Now do you see it?
If you take a close look a the variable name of “xuunL” then look at the highlighted values they are using mixed case parameter names.
My Reg-X the way it was built would not pick up on the various different versions. I also could not find a way for it to “Ignore Case”
My next step was to build a function to “Normalize” the case to what it was originally set at. It searches 1 step at a time thru the input and matches the value then replaces it with the proper case.
So when it would find %XuUNL: it would replace it with %xuunL: throughout the input data.
This is still a lot of work if you have 10 rounds but you can control and work with the output.
After decoding the 10 layers we see where it is setting a file extension in different folders. But it does not appears to be encrypting anything. Unless I’ve missed it so far.
We can also see it is downloading 2 files from pastebin.
Here we see a note claiming the files were encrypted.
Looking at the renamed files on Anyrun suggest that it does only rename files and not encrypt them.
Although this does not appear to be encrypting anything (Right now) it is going thru and disabling Security product and dumping data.
Disabling taskmgr, exiting if a listed username is found ? Sandbox or developer username?
Looking at the decoded file from the “EZ88t5c1” pastebin link we can see links to telegram, Discord, Google Docs.
Looking at the cleaned up version of the pastebin link “bLnD8FWX” we can see that is is shutting down found security products.
There is a lot to process in this piece of malware.
That is it for this one.
Links:
Link to Twitter thread.
Link to Anyrun for the main script.
Link to my github for the tool used here. (password is “clean”0
Article Link: Pealing back the layers of a batch script ransomware | PC's Xcetra Support