
By Lakshya Mathur & Yashvi Shah
Phishing attackers aim to deceive individuals into revealing sensitive information for financial gain, credential theft, corporate network access, and spreading malware. This method often involves social engineering tactics, exploiting psychological factors to manipulate victims into compromising actions that can have profound consequences for personal and organizational security.
Over the last four months, McAfee Labs has observed a rising trend in the utilization of PDF documents for conducting a succession of phishing campaigns. These PDFs were delivered as email attachments.
Attackers favor using PDFs for phishing due to the file format’s widespread trustworthiness. PDFs, commonly seen as legitimate documents, provide a versatile platform for embedding malicious links, content, or exploits. By leveraging social engineering and exploiting the familiarity users have with PDF attachments, attackers increase the likelihood of successful phishing campaigns. Additionally, PDFs offer a means to bypass email filters that may focus on detecting threats in other file formats.
The observed phishing campaigns using PDFs were diverse, abusing various brands such as Amazon and Apple. Attackers often impersonate well-known and trusted entities, increasing the chances of luring users into interacting with the malicious content. Additionally, we will delve into distinct types of URLs utilized by attackers. By understanding the themes and URL patterns, readers can enhance their awareness and better recognize potential phishing attempts.
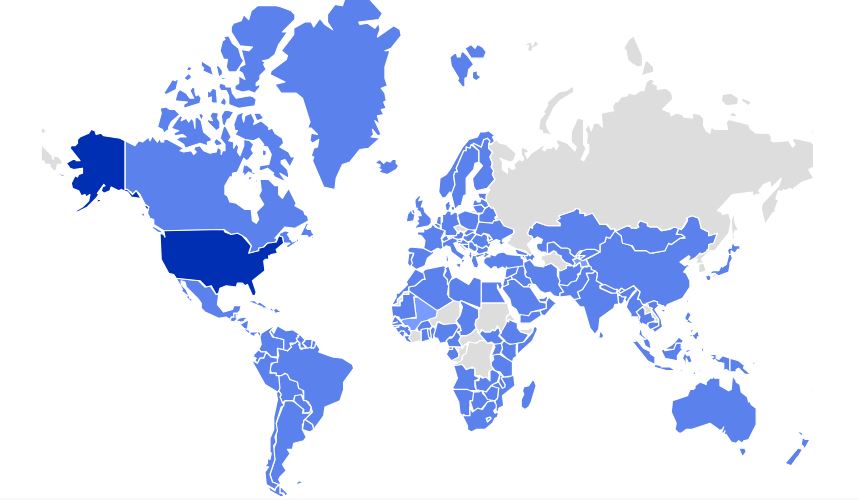
Figure 1 – PDF Phishing Geo Heatmap showing McAfee customers targeted in last 1 month
Different Themes of Phishing
Attackers employ a range of corporate themes in their social engineering tactics to entice victims into clicking on phishing links. Notable brands such as Amazon, Apple, Netflix, and PayPal, among others, are often mimicked. The PDFs are carefully crafted to induce a sense of urgency in the victim’s mind, utilizing phrases like “your account needs to be updated” or “your ID has expired.” These tactics aim to manipulate individuals into taking prompt action, contributing to the success of the phishing campaigns.
Below are some of the examples:
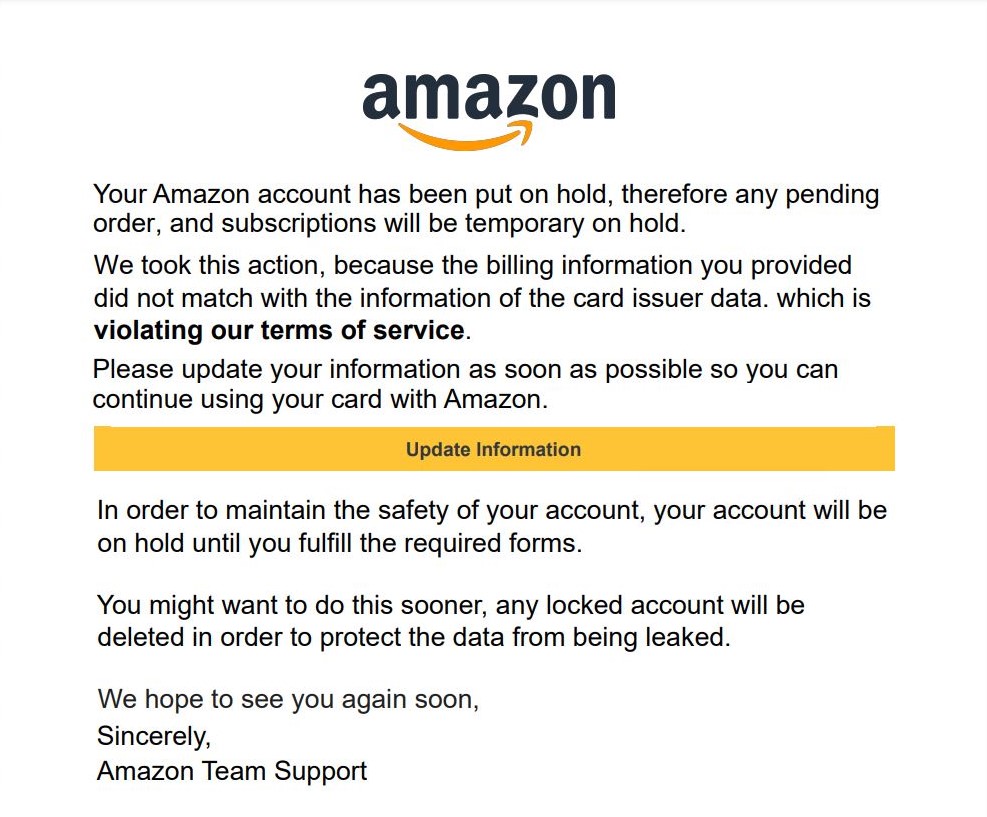
Figure 2 – Fake Amazon PDF Phish
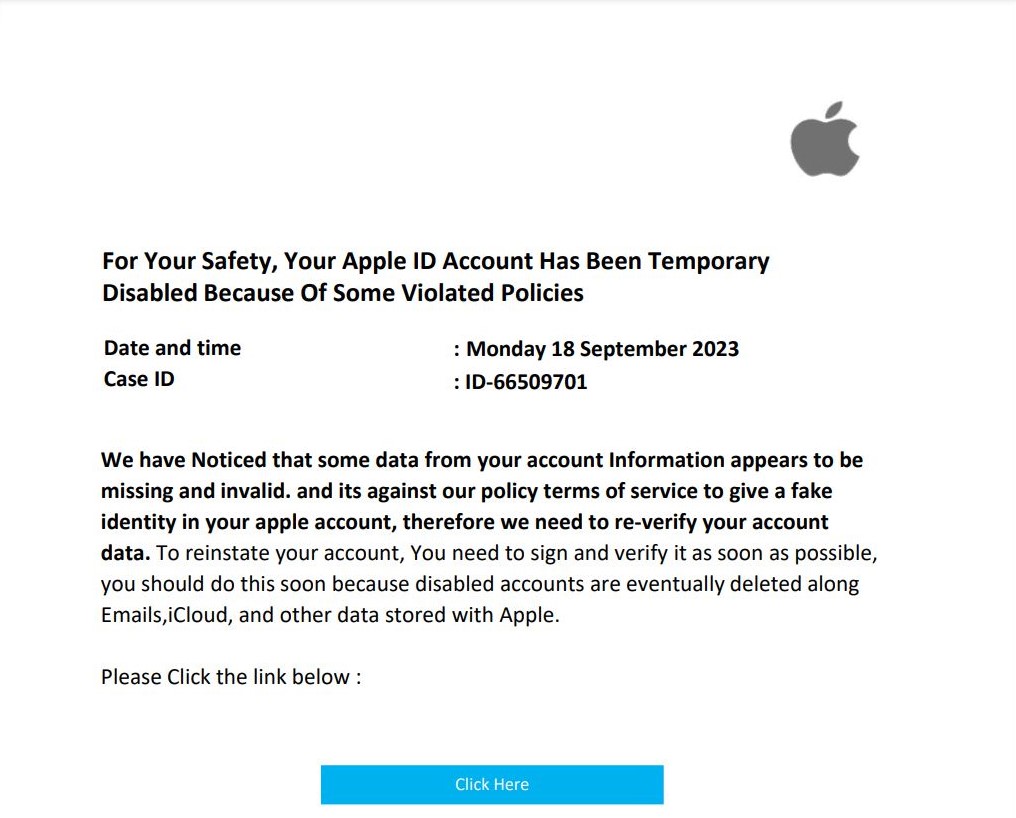
Figure 3 – Fake Apple PDF Phish
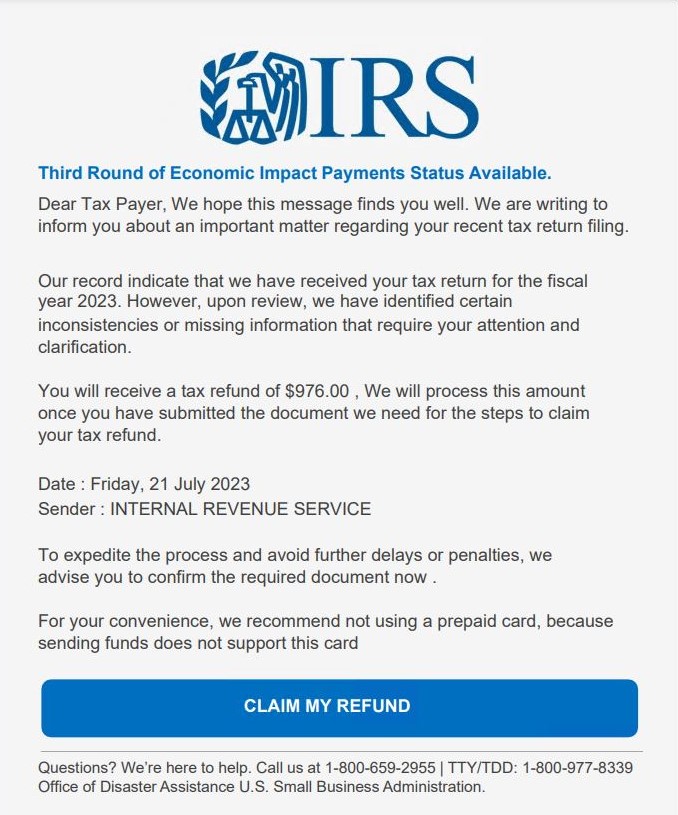
Figure 4 – Fake Internal Revenue Service PDF Phish
Figure 5 – Fake Adobe PDF Phish
Below are the stats on the volume of various themes we have seen in these phishing campaigns.
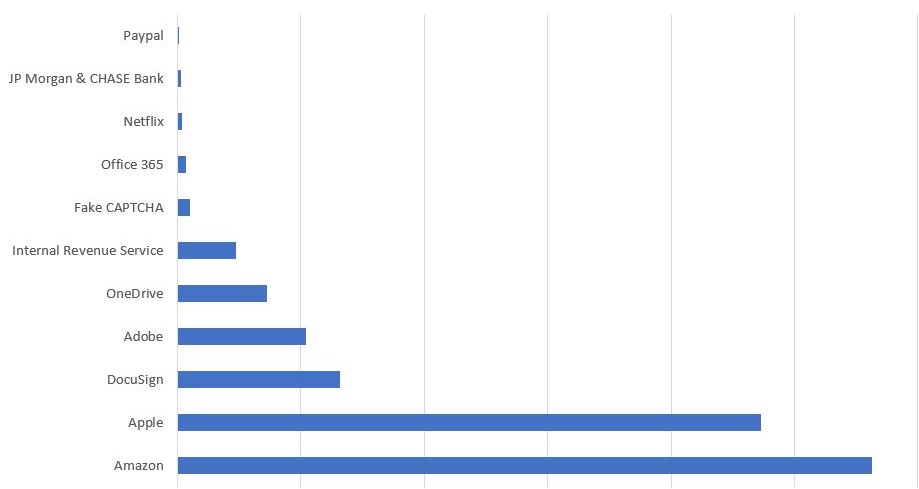
Figure 6 – Different themed campaign stats based on McAfee customers hits in last 1 month
Abuse of LinkedIn and Google links
Cyber attackers are exploiting the popular professional networking platform LinkedIn and leveraging Google Apps Script to redirect users to phishing websites. Let us examine each method of abuse individually.
In the case of LinkedIn, attackers are utilizing smart links to circumvent Anti-Virus and other security measures. Smart links are integral to the LinkedIn Sales Navigator service, designed for tracking and marketing business accounts.


Figure 7 – LinkedIn Smart link redirecting to an external website
By employing these smart links, attackers redirect their victims to phishing pages. This strategic approach allows them to bypass traditional protection measures, as the use of LinkedIn as a referrer adds an element of legitimacy, making it more challenging for security systems to detect and block malicious activity.
In addition to exploiting LinkedIn, attackers are leveraging the functionality of Google Apps Script to redirect users to phishing pages. Google Apps Script serves as a JavaScript-based development platform used for creating web applications and various other functionalities. Attackers embed malicious or phishing code within this platform, and when victims access the associated URLs, it triggers the display of phishing or malicious pages.
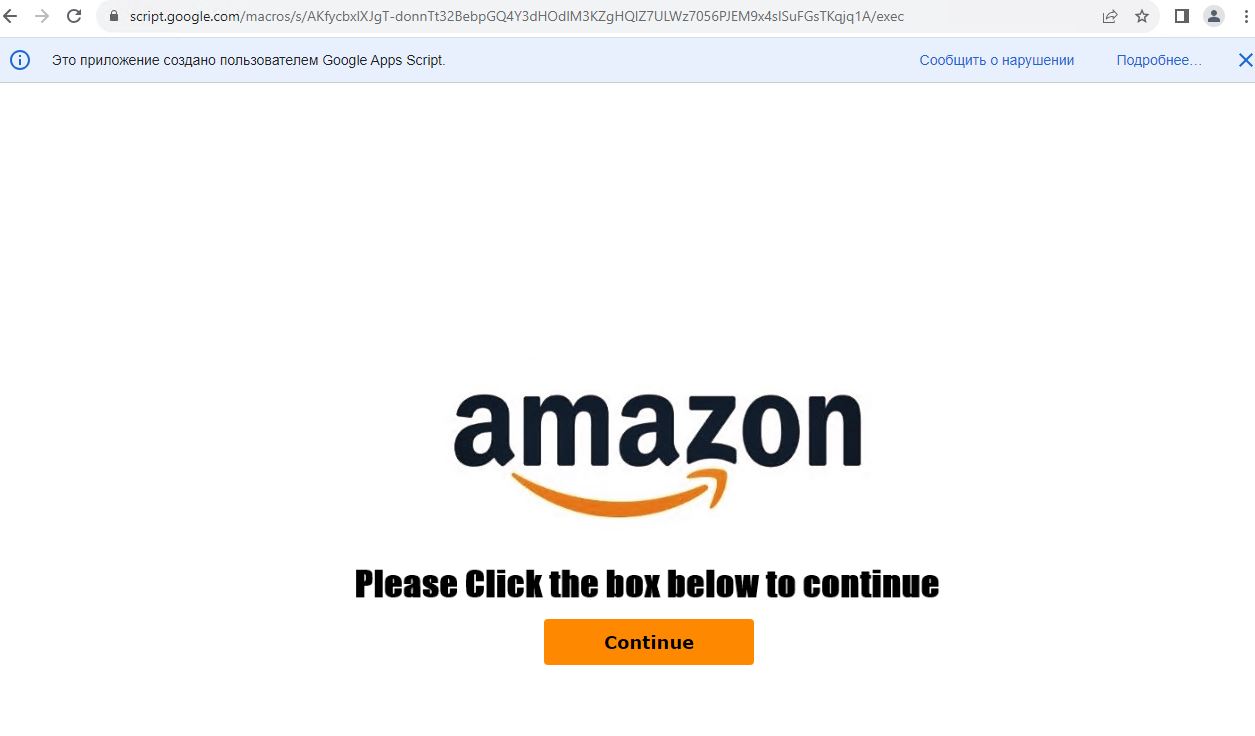
Figure 8 – Amazon fake page displayed on accessing Google script URL
As shown in Figure 8, when victims click on the “Continue” button, they are subsequently redirected to a phishing website.
Summary
Crafting highly convincing PDFs mimicking legitimate companies has become effortlessly achievable for attackers. These meticulously engineered PDFs create a sense of urgency through skillful social engineering, prompting unsuspecting customers to click on embedded phishing links. Upon taking the bait, individuals are redirected to deceptive phishing websites, where attackers request sensitive information. This sophisticated tactic is deployed on a global scale, with these convincing PDFs distributed to thousands of customers worldwide. Specifically, we highlighted the increasing use of PDFs in phishing campaigns over the past four months, with attackers adopting diverse themes such as Amazon and Apple to exploit user trust. Notably, phishing tactics extend to popular platforms like LinkedIn, where attackers leverage smart links to redirect victims to phishing pages, evading traditional security measures. Additionally, Google Apps Script is exploited for its JavaScript-based functionality, allowing attackers to embed malicious code and direct users to deceptive websites.
Remediation
Protecting oneself from phishing requires a combination of awareness, caution, and security practices. Here are some key steps to help safeguard against phishing:
- Be Skeptical: Exercise caution when receiving unsolicited emails, messages, or social media requests, especially those with urgent or alarming content.
- Verify Sender Identity: Before clicking on any links or providing information, verify the legitimacy of the sender. Check email addresses, domain names, and contact details for any inconsistencies.
- Avoid Clicking on Suspicious Links: Hover over links to preview the actual URL before clicking. Be wary of shortened URLs, and if in doubt, verify the link’s authenticity directly with the sender or through official channels.
- Use Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device.
McAfee provides coverage against a broad spectrum of active phishing campaigns, offering protection through features such as real-time scanning and URL filtering. While it enhances security against various phishing attempts, users must remain vigilant and adopt responsible online practices along with using McAfee.
The post PDF Phishing: Beyond the Bait appeared first on McAfee Blog.
Article Link: PDF Phishing: Beyond the Bait | McAfee Blog