The landscape of botnet development has been transformed in recent years, thanks to the accessibility of open source code, particularly in the context of Mirai-based trojans. In September 2023, researchers closely monitored the appearance of new botnet variants originating from the Mirai. These botnets are spreading rapidly, presenting a significant cybersecurity threat. Of the latest botnet families that have surfaced, hailBot, kiraiBot, and catDDoS have emerged as some of the most actively deployed and concerning entities in this evolving landscape.
This blog post will provide an overview of the researchers’ findings regarding these new botnets and their potential implications for cybersecurity.
What Are the Capabilities of the New hailBot, kiraiBot, and catDDoS Botnets?
With these new variants, researchers have observed a strategic alteration of open-source botnet trojans. Attackers have enhanced the trojans’ stealthiness in file operations by incorporating encryption algorithms and manipulated communication methods to evade detection, employing tactics such as binding malicious IPs to benign domains, reportedly using services like ClouDNS or OpenNIC domains.
These developments raise concerns regarding their potential cybersecurity impact. In the following sections, we will delve into specific details about these new botnet variants and their activities.
hailBot Botnet
The name “hailBot” is coined from the output string “hail china mainland” that emerges during its operation. Researchers note that it raises suspicions of intentional manipulation. Based on the Mirai botnet, the bot has modified its original go-live data packet.
This botnet spreads by exploiting vulnerabilities, scanning for weak passwords, and employing brute force attacks. In its current iteration, hailBot includes a single embedded vulnerability, CVE-2017-17215 (remote code execution vulnerability in some customized versions of Huawei HG532).
hailBot encompasses four distinct DDoS attack methods, as detailed below:
 hailBot attack methods (NSFOCUS)
hailBot attack methods (NSFOCUS)
The hailBot controller has been highly active, establishing its own Mirai-based botnet in late 2022. Although it has issued fewer commands recently, researchers report an increase in its active Command and Control server (C2) count, indicative of a large-scale expansion.
Researchers further revealed C2 infrastructure with IP addresses 5.181.80.120 and 5.181.80.115, which distributed malicious documents. These documents, named with keywords like “invoice” and “product,” enticed victims into triggering the CVE-2017-11882 (Microsoft Office Memory Corruption) vulnerability. Successful lures resulted in the download and execution of banking trojans such as LokiBot and FormBook.
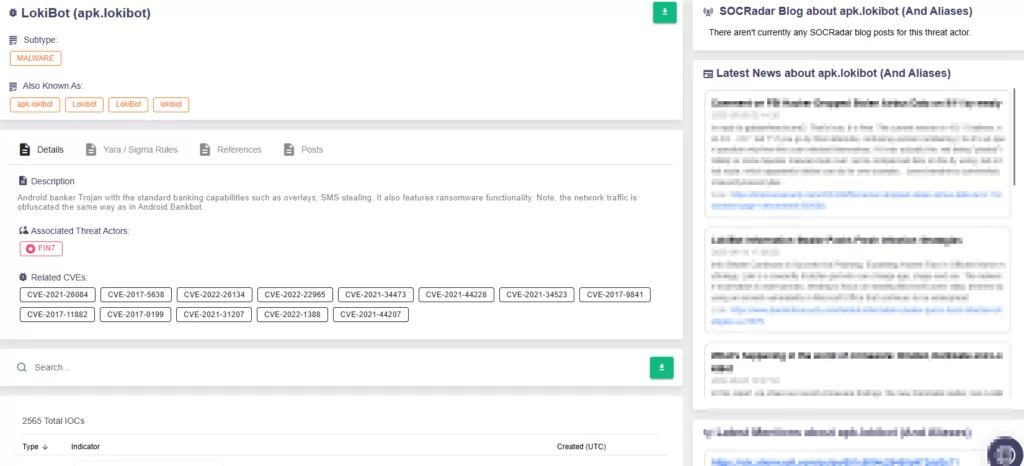 LokiBot (SOCRadar Threat Actors/Malware)
LokiBot (SOCRadar Threat Actors/Malware)
While hailBot initially concentrated on financial and trade institutions, it is stated that the botnet’s focus later shifted to IoT platforms.
Nonetheless, these findings suggest that the hailBot controller poses a significant threat to the targeted industries, which may continue to face challenges in the future.
kiraiBot Botnet
The kiraiBot takes inspiration from the Mirai source code while incorporating numerous unique design elements. Its name is derived from the “kirai” string found in the sample.
To ensure persistence, kiraiBot configures a self-starting script. The botnet primarily propagates by targeting port 23 (typically used by the Telnet protocol) through weak password scanning.
The “kirai” string is also visible in the scan traffic of the kiraiBot, and its report server for receiving breach results is modeled after Mirai, but the location of the kiraiBot propagation scripts differs from its C2.
The current version boasts support for six DDoS attack modes:
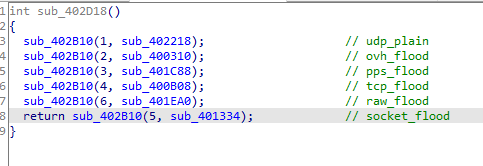 kiraiBot attack methods (NSFOCUS)
kiraiBot attack methods (NSFOCUS)
Unlike other Mirai variants, kiraiBot features significant code structure changes, including an adapted instruction parsing module from the original Mirai. Its activities were mainly concentrated in August and September 2023.
Despite issuing relatively few recent instructions, its extensive propagation volume renders it a substantial threat.
catDDoS Botnet
Researchers state that catDDoS has prioritized concealment, incorporating the ChaCha20 algorithm and introducing the OpenNIC domain name, resembling the Fodcha family’s tactics.
Using the ChaCha20 algorithm for encrypting and storing critical information, the catDDoS family enhanced the Mirai source code. This variant also adjusted the original Mirai’s go-live process, transmitting data to the server in multiple rounds, in both plaintext and ciphertext.
Researchers monitored that the catDDoS family is actively issuing commands, primarily between 8 AM. and 9 PM. Recent data reveals that 58% of its targets are in China, followed by the United States at 25%, with Japan, Singapore, France, and other countries also affected.
Furthermore, catDDoS includes various built-in DDoS attack methods:
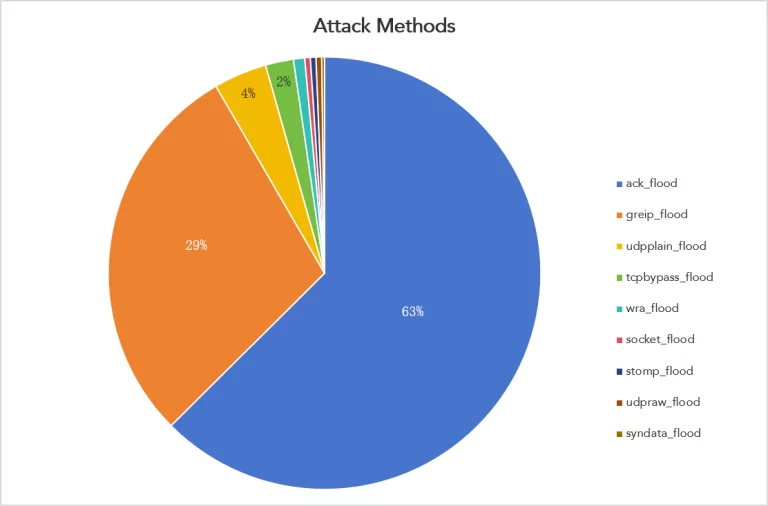 catDDoS attack methods (NSFOCUS)
catDDoS attack methods (NSFOCUS)
The Indicators of Compromise (IoCs) related to all three botnet families are available at the end of this blog. For further information about hailBot, kiraiBot, and catDDoS botnets, refer to the original research here.
Conclusion
In the ever-evolving world of cyber threats, the dangers posed by botnets and their potential for devastating Distributed Denial-of-Service (DDoS) attacks are all too real. The fact that there exist botnets comprising millions of enslaved computers, ready and waiting for malicious instructions, is a chilling testament to the scale of the threat we face.
Cybercriminals show no restraint when deploying legions of bot soldiers to execute crippling DDoS attacks, bringing down target servers and causing severe disruption. Moreover, some botnets target individual devices, aiming to plunder valuable information, pilfer passwords, or engage in cryptocurrency mining. It is also a stark reminder that the cybercriminal underground operates efficiently, and often rents out these botnets to other threat actors.
The dangers of botnets and the potential for devastating cyberattacks are ever-present. As we navigate this digital landscape, it is crucial to remain vigilant, adapt security measures, and stay informed about emerging threats. By doing so, we can collectively work towards a safer and more secure cyber environment.
How Can SOCRadar Help?
Stay ahead of malicious actors and safeguard your digital assets with SOCRadar. Our platform constantly monitors threat actor behavior and keeps an eye on the latest malware, offering you real-time information and indicators of compromise. Staying informed about potential risks empowers you to proactively detect and eliminate threats before they can inflict significant damage on your organization.
 Mirai botnet on SOCRadar Threat Actors/Malware
Mirai botnet on SOCRadar Threat Actors/Malware
Elevate your organization’s defense against Denial-of-Service (DoS) threats through SOCRadar Labs’ DoS Resilience module. DoS Resilience enables you to assess your domain’s or subnet’s capability to withstand DoS attacks.
 Check for your DoS Resilience on SOCRadar Labs
Check for your DoS Resilience on SOCRadar Labs
The post Origin of the Botnets: New Mirai-based Botnet Variants Emerge (hailBot, kiraiBot, and catDDoS) appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Origin of the Botnets: New Mirai-based Botnet Variants Emerge (hailBot, kiraiBot, and catDDoS)
