The cyber security landscape has recently been abuzz with discussions about Operation Triangulation, a sophisticated and multi-faceted cyber attack campaign. This operation stands out for its targeting of Apple’s iPhones, exploiting zero-day vulnerabilities and making use of undocumented hardware features in Apple’s SoCs.
This post delves deep into the attack chain of Operation Triangulation, its global impact, and strategies for mitigating such advanced threats.
 An illustration of the campaign
An illustration of the campaign
Operation Triangulation: Revealing the Mysteries of Advanced iPhone Hacking Mechanisms
Operation Triangulation distinguishes itself through its complexity and layered approach. Primarily targeting iPhones, the campaign facilitates the surreptitious installation of malware and theft of sensitive information. This campaign has been observed to affect various sectors globally.
The Attack Mechanism
The attack chain of Operation Triangulation is a testament to the advanced tactics employed by cybercriminals. The attack commences with a zero-click iMessage exploit, leveraging four zero-day vulnerabilities effective up to iOS 16.2.
A malicious iMessage attachment is used to exploit a Remote Code Execution (RCE) vulnerability in an undocumented TrueType font instruction, a sophisticated approach showcasing the depth of the attackers’ capabilities.
The Enigma of CVE-2023-38606
One of the most intriguing aspects of Operation Triangulation is its exploitation of the CVE-2023-38606 vulnerability. This involves bypassing hardware-based security protections in recent iPhone models, using a hardware feature likely intended for debugging or testing purposes. The discovery and utilization of this undocumented feature by attackers underscore the sophistication and depth of their skillset.
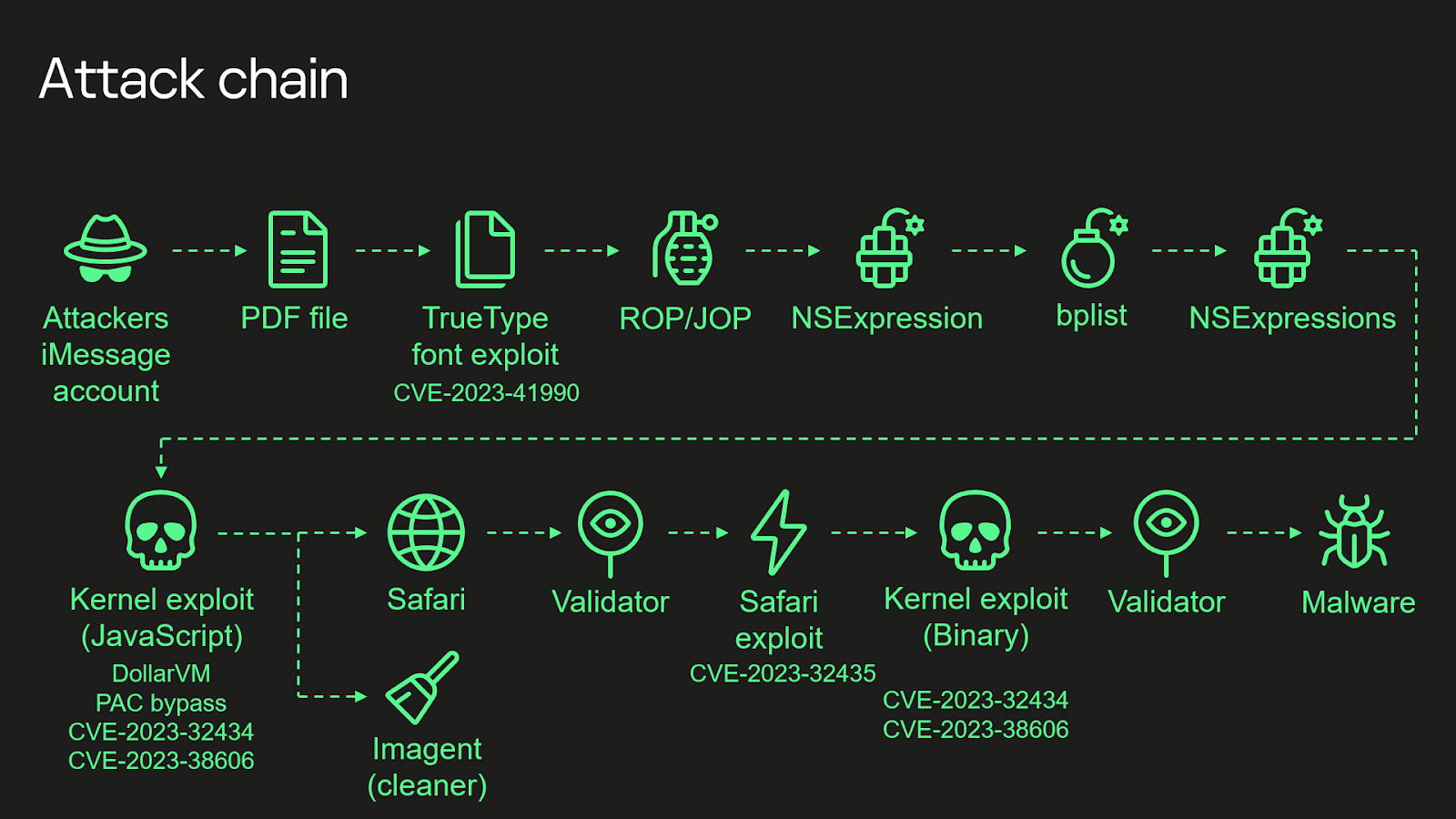 Exploitation of CVE-2023-38606
Exploitation of CVE-2023-38606
Mitigation Strategies
To counter threats like Operation Triangulation, robust security measures are essential, such as:
- Stay Updated: Regularly install the latest iOS updates to patch known vulnerabilities.
- App Caution: Only download apps from the App Store and review permissions carefully.
- Avoid Jailbreaking: The practice of jailbreaking, which involves removing software restrictions imposed by the manufacturer, can make your device more vulnerable to cyber attacks.
- Strong Authentication: Employ strong, unique passwords and enable Two-Factor Authentication (2FA).
- Network Security: Use secure Wi-Fi networks and consider VPNs, especially on public networks.
- Phishing Awareness: Be cautious about clicking on suspicious links and opening email attachments from unknown sources.
- Use Security Tools: Deploy tools to detect malware and other threats.
- Developer Vigilance: App developers should adhere to security best practices, including regular security testing.
- User Education: Security awareness training is crucial, particularly in corporate settings.
- Regular Data Backups: Consistently back up important data to facilitate recovery in case of data loss.
SOCRadar’s Proactive Measures Against Operation Triangulation
In response to the complexities and dangers posed by Operation Triangulation, SOCRadar, a leading cybersecurity firm, has implemented a range of proactive measures to safeguard its clients.
Leveraging its advanced threat intelligence capabilities, SOCRadar actively monitors for Indicators of Compromise (IoCs) associated with Operation Triangulation. This includes tracking known malicious domains, IP addresses, and unique malware signatures linked to the attack campaign.
Additionally, SOCRadar employs cutting-edge anomaly detection systems to identify unusual activities that could signify an attempted intrusion, ensuring that their clients are promptly alerted to potential threats. SOCRadar also prioritizes client education, providing detailed information and best practices to enhance their clients’ internal security protocols against such sophisticated attacks.
Through these concerted efforts, SOCRadar not only strengthens its clients’ defenses against Operation Triangulation but also bolsters their overall cybersecurity posture in the face of evolving digital threats.
Conclusion
Operation Triangulation highlights the sophisticated threats present in our digital world. It is imperative for both individuals and organizations to be informed and vigilant against such high-tech cyber espionage tactics.
By taking strong security measures and being informed, we can increase our resistance to such sophisticated threats. You can find detailed information about Operation Triangulation in our Journal under the Campaigns heading on our SOCRadar Labs page.
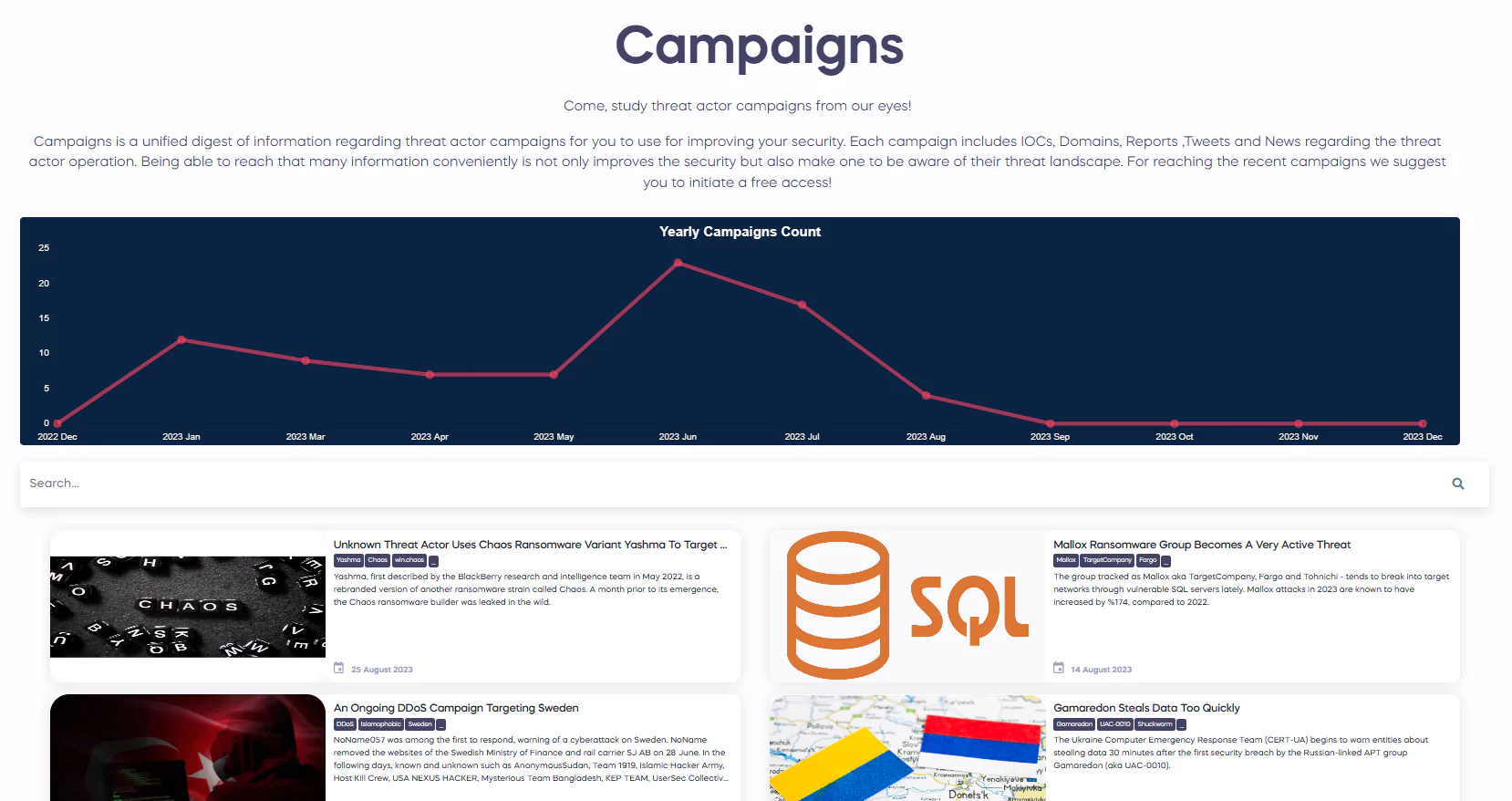 SOCRadar Campaigns Page
SOCRadar Campaigns Page
You can also get information about the CVE-2023-38606 vulnerability in our Vulnerability Intelligence module.
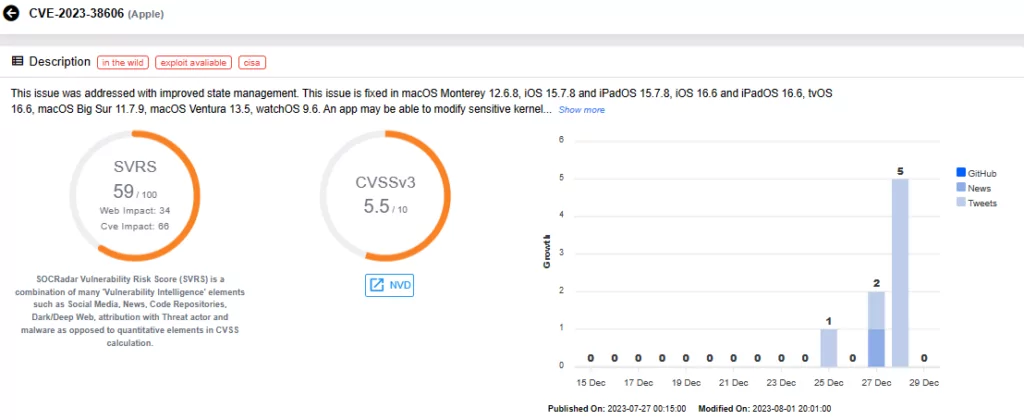 Details of the CVE-2023-38606 Vulnerability (SOCRadar Vulnerability Intelligence)
Details of the CVE-2023-38606 Vulnerability (SOCRadar Vulnerability Intelligence)
Further Reading and Resources:
For more detailed technical insights into Operation Triangulation, the following reports are highly recommended:
The post Operation Triangulation: ‘’Most Sophisticated Attack Chain Ever Seen” appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Operation Triangulation: ‘’Most Sophisticated Attack Chain Ever Seen"
