Newly discovered vulnerabilities are a constant source of concern for the cybersecurity community, particularly when threat actors set their sights on them. In this ever-evolving landscape, threat actors remain vigilant, and they have honed in on vulnerabilities in VMware Aria Operations, Citrix NetScaler ADC, and Gateway.
As the cybersecurity community knows all too well, the moment a Proof-of-Concept (PoC) exploit becomes available for a vulnerability, threat actors are quick to seize the opportunity. Recent chatter in a Telegram chat group highlighted the availability of PoC exploits for vulnerabilities in VMware Aria Operations, Citrix NetScaler ADC, and Gateway.
 Threat actors forward the announcement across different Telegram channels
Threat actors forward the announcement across different Telegram channels
This is likely to attract the attention of additional threat actors, soon leading to an upsurge in exploitation activities.
What is the Vulnerability in VMware Aria Operations About? (CVE-2023-34051)
VMware recently issued a warning to its customers regarding a Proof-of-Concept (PoC) exploit for a security vulnerability that had previously been patched in Aria Operations for Logs (vRealize Log Insight).
The vulnerability, designated as CVE-2023-34051 and boasting a high severity CVSS score of 8.1, arises from an authentication bypass issue. It enables an unauthenticated malicious actor to inject files into the operating system of a vulnerable appliance, ultimately achieving remote code execution with root privileges.
It is crucial to highlight that CVE-2023-34051 serves as a patch bypass for several critical vulnerabilities that were previously addressed by VMware. The vulnerabilities in question include:
- CVE-2022-31706 – Directory Traversal Vulnerability
- CVE-2022-31704 – Broken Access Control Vulnerability
- CVE-2022-31711 – Information Disclosure Vulnerability
The three vulnerabilities in VMware Aria Operations for Logs could be chain-exploited by attackers to cause a Denial-of-Service (DoS) situation, as well as access sensitive information, and raise concerns about the potential exposure of users to remote code execution attacks.
Researchers report that, while these vulnerabilities were relatively simple to exploit, they required that the attacker already had the necessary infrastructure in place to deliver malicious payloads and had established a foothold within the network through other means. This is because the product is less likely to be directly exposed to the internet.
About the PoC
Horizon3.ai has shared the PoC for the CVE-2023-34051 vulnerability on GitHub. The provided PoC exploits IP address spoofing and various Thrift RPC endpoints to achieve arbitrary file write capabilities. Researchers emphasize that for this attack to succeed, the attacker must possess the same IP address as a master or worker node, which adds a layer of complexity.
Nevertheless, now that a PoC exploit is available, the likelihood of vulnerability’s exploitation in potential attacks is greatly amplified.
Researchers have also shared Indicators of Compromise (IoCs) related to exploitation of CVE-2023-34051, which you can find here.
Citrix NetScaler ADC/Gateway Appliances Are Also Under Risk (CVE-2023-4966)
In parallel, Citrix has recently released an advisory of its own, urgently advising its customers to apply fixes for CVE-2023-4966, which boasts a critical CVSS score of 9.4. This security vulnerability affects both NetScaler ADC and NetScaler Gateway appliances and is currently under active exploitation.
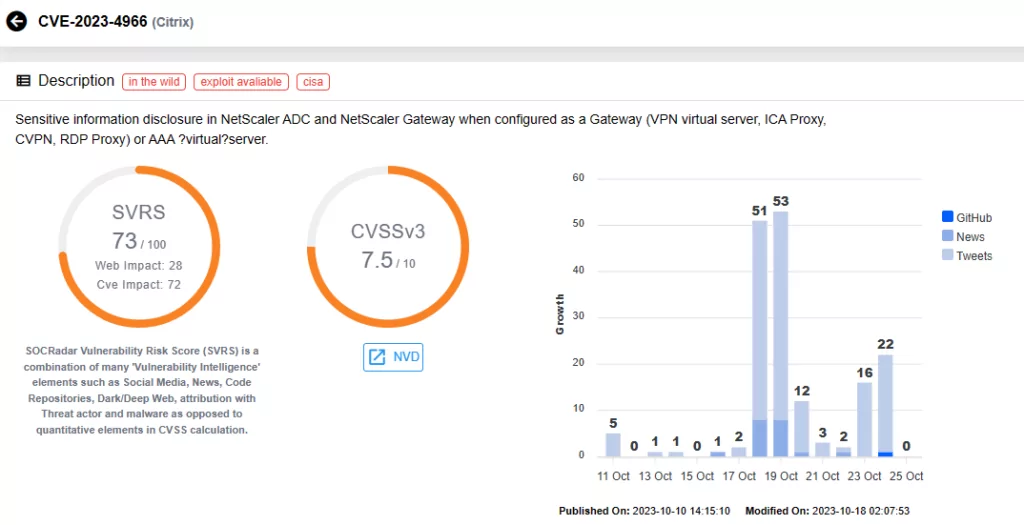 Vulnerability card for CVE-2023-4966 (SOCRadar Vulnerability Intelligence)
Vulnerability card for CVE-2023-4966 (SOCRadar Vulnerability Intelligence)
To further exacerbate the situation, a PoC exploit named Citrix Bleed has surfaced, raising concerns about the imminent surge in exploitation activities.
The gravity of the situation prompted CISA to include CVE-2023-4966 in the Known Exploited Vulnerabilities (KEV) catalog, mandating that U.S. federal agencies implement the latest patches by November 8, 2023.
For a more in-depth exploration of the vulnerabilities in Citrix NetScaler ADC/Gateway appliances, we encourage you to visit our other blog post:
Threat Actors Stay Watchful: The Okta Breach Has Not Gone Unnoticed
Threat actors have additionally circulated news about a breach in Okta’s support system. This breach had implications for prominent companies, including Cloudflare, 1Password, and BeyondTrust. While the affected vendors acted promptly to mitigate the issue, it serves as a stark reminder of how such incidents could potentially culminate in a severe supply chain compromise.
The knowledge and swift disclosure by threat actors underscore their unwavering vigilance and acute awareness of potential vulnerabilities within the cybersecurity landscape. This emphasizes the imperative need to maintain vigilance and proactivity, particularly as threat actors are always on the lookout for potential targets.
 Threat actors share about the Okta breach
Threat actors share about the Okta breach
Learn more about the Okta breach in our recent blog post:
Apply the Patches for VMware Aria Operations to Fix CVE-2023-34051
VMware has resolved the CVE-2023-34051 vulnerability as part of the KB95212 update. For further details, and to access update documentation and guides, refer to VMware’s official advisory.
Conclusion
According to researchers, the patch bypass (CVE-2023-34051) for VMware Aria Operations would not be very difficult for an attacker to find. The provided PoC exploit highlights the importance of defense-in-depth, rather than relying on a patch to solve all the problems.
Thereby, implementing further measures such as intrusion detection systems, network segmentation, and robust access controls can help; by adopting a holistic defense-in-depth strategy, organizations can fortify their cybersecurity posture and be better prepared to withstand unforeseen vulnerabilities and emerging threats.
With SOCRadar’s Vulnerability Intelligence, you can gain access to hacker trends, and details and updates on specific vulnerabilities, as well as their SVRS score (SOCRadar Vulnerability Risk Score). This score provides better insights into a vulnerability’s popularity and its likelihood of exploitation.
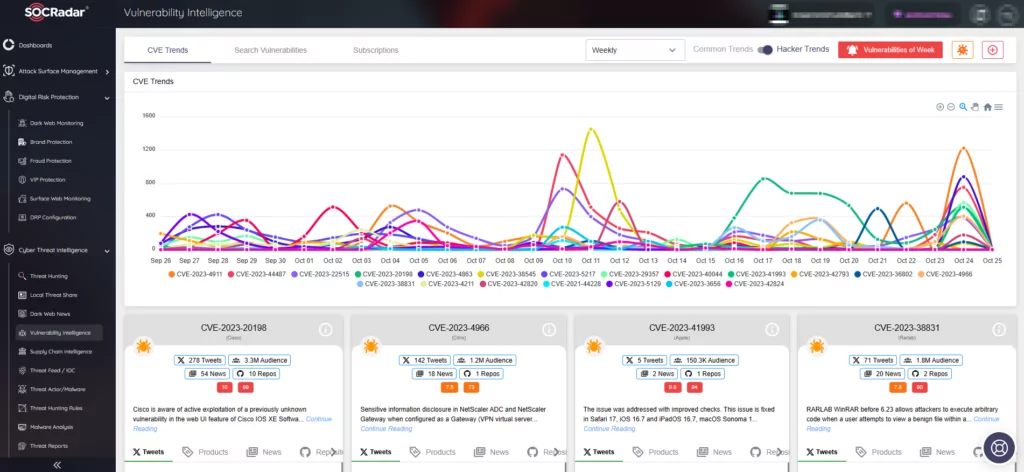 SOCRadar Vulnerability Intelligence
SOCRadar Vulnerability Intelligence
Leveraging the Attack Surface Management (ASM) module, you can proactively monitor emerging vulnerabilities across your digital assets, receive timely threat alerts, and efficiently manage patching efforts to mitigate their impact.
 SOCRadar Attack Surface Management
SOCRadar Attack Surface Management
The post On Threat Actors’ Radar: PoC Exploits for VMware Aria Operations Vulnerability (CVE-2023-34051), and More appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: On Threat Actors' Radar: PoC Exploits for VMware Aria Operations Vulnerability (CVE-2023-34051), and More
