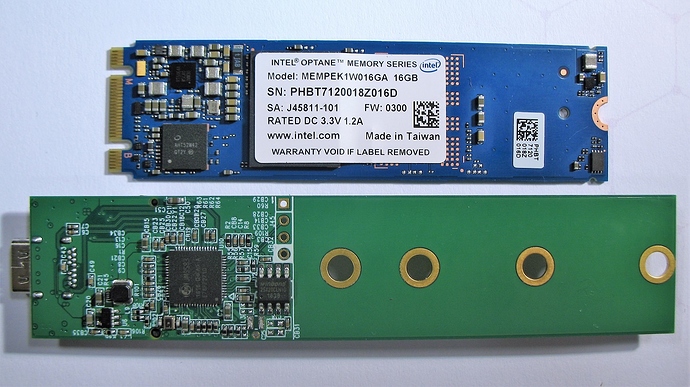
In a recent article about computer storage formats, I mentioned that USB enclosures for NVMe M.2 hard drives were not widely available. We have since been able to to obtain a demo board for the JMS583 USB 3.1 gen 2 to PCIe bridge from the fine folk at JMicron. We have been using this adapter to do some testing with an NVMe SSD over a USB 3.1 connection.
To recap, NVMe is a protocol for high speed storage media that are attached to computers via the PCIe bus. NVMe/PCIe SSDs are increasingly common and are on their way to replacing SATA drives in many applications. Some manufacturers have also begun to use newer memory technologies such as 3D XPoint to enable more speed and longevity than storage media based on NAND flash. In the digital forensics world, various hardware write-blocking solutions are available for PCIe storage devices.
But what about the quick and dirty method of using a Windows registry setting to block write operations? The following policy, which was introduced in Windows XP SP2, provides the facility to make USB block storage devices operate in read-only mode:
| Location | HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies |
| Setting | WriteProtect |
| Values | 0: disabled, 1: enabled |
When I connected an SSD using the JMS583 adapter to a legacy operating system (Windows 7 SP1), the WriteProtect setting worked as expected. But on my main test computer which has Windows 10 (1803), it did not. The reason turns out to be UASP.
Drivers
Let’s take a closer look at how the device is treated by the host operating system. Firstly, it would seem that Windows 7 uses its USB storage port driver:
C:\>wmic diskdrive where "Caption like '%USB%'" get Caption,PNPDeviceID
Caption PNPDeviceID
JMicron Generic USB Device USBSTOR\DISK&VEN_JMICRON&PROD_GENERIC&REV_0203\0123456789ABCDEF&0
When the same device is connected to a Windows 10 computer, with a USB 3.1 gen 1 connection, it is recognised as a SCSI device. Despite the WriteProtect policy being enabled, the drive is not in read-only mode, as illustrated below.
PS D:\> Get-Disk 7 | select FriendlyName,Path,IsReadOnly | Format-List
FriendlyName : JMicron Generic
Path : \?\scsi#disk&ven_jmicron&prod_generic#000000#{53f56307-b6bf-11d0-94f2-00a0c91efb8b}
IsReadOnly : False
PS D:> Get-Item HKLM:\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies\
Hive: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control
Name Property
StorageDevicePolicies WriteProtect : 1
The following output from lsusb on a relatively recent version of Linux (4.15) shows the uas driver being used with the same device. (An old USB 2.0 flash drive would have caused the usb-storage driver to be loaded instead.)
ccl@r930 ~ % lsusb | grep JMicron
Bus 006 Device 003: ID 152d:0583 JMicron Technology Corp. / JMicron USA Technology Corp.
ccl@r930 ~ % lsusb -t | grep 06 -A 1
/: Bus 06.Port 1: Dev 1, Class=root_hub, Driver=xhci_hcd/2p, 5000M
|__ Port 1: Dev 3, If 0, Class=Mass Storage, Driver=uas, 5000M
UASP
The USB Attached SCSI (UAS) specification and Protocol (UASP) were introduced as part of the USB 3.0 specification. UASP brings the SCSI command set to USB, replacing the slower Bulk Only Transport (BOT) protocol. If the necessary hardware is present, UASP can also be used with USB 2.0.
If copying and transferring large amounts of data is part of your workflow, UASP can provide some significant performance improvements. But if you rely on the StorageDevicePolicies registry key to control the usage of USB drives on your IT systems, or in order to prevent write operations from being sent to exhibits, be aware that UASP-capable devices are not affected by that Windows policy. It will be evident from just taking a glance at the websites of a few electronics retailers that many new flash drives, external hard drives, drive enclosures and adapters support UASP.
Solution
Fortunately there is another Windows policy which can be used to prevent write access to all removeable storage devices. In Windows 7 or 10:
- Open the Local Group Policy Editor (
gpedit.msc) - Open Computer Configuration → Administrator Templates → System → Removable Storage Access
- Double click Removable Disks: Deny write access and select Enable
Another interesting setting in the same section is WPD Devices: Deny write access. WPD stands for Windows Portable Devices. This setting can be used to prevent write access to devices such as mobile phones, cameras and portable music players, which use protocols such as MTP to communicate. The StorageDevicePolicies registry key does not affect those devices either!
Arun Prasannan
Principal Analyst (Research & Development)
The post NVMe, UASP and write-blocking using the Windows registry appeared first on CCL Group.
Article Link: https://cclgroupltd.com/nvme-uasp-and-write-blocking-using-the-windows-registry/