Since its release in 2014, the NIST Cybersecurity Framework (CSF) has been adopted by organizations worldwide and across industries. But a lot has changed in that period. NIST gathered input about how the CSF should evolve, and this month released the draft version of CSF 2.0.
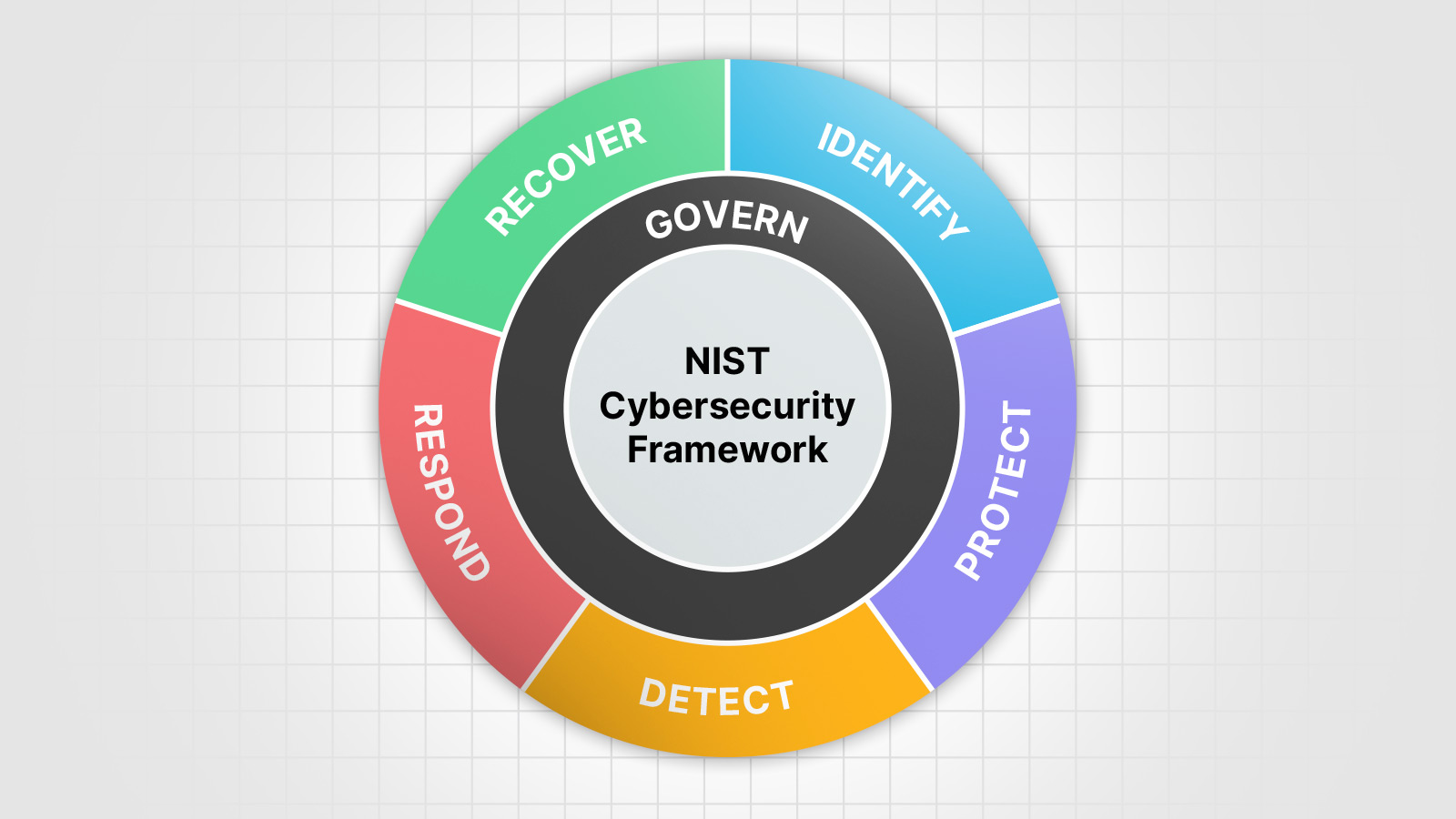
One of the most significant changes in CSF 2.0 is the inclusion of a Govern function and an emphasis on cybersecurity supply chain risk management (C-SCRM) and secure software development.
Addressing Increasing Supply Chain Risk
Incidents in recent years having to do with the OpenSSL library, Log4j, and SolarWinds products (to name just a few) have emphasized the need to better understand and manage the risk that we are taking on when we use a particular technology, whether it be an open source software library or piece of network gear.
Part of the solution lies with vendors: requiring SBOMs, attestation that they are following secure software development practices, and in general asking that products be secure by design.
But the other part of the solution lies with customers: Verifying that you are using libraries and repositories that are free from malware or backdoors, verifying that your devices contain authentic components that have not been tampered with, and then understanding and mitigating the risk that you knowingly accept.
The latter part is what CSF 2.0 addresses with new C-SCRM controls. See the table at the bottom of this blog for a quick overview of the proposed Functions and Categories.
Cybersecurity Supply Chain Risk Management in the CSF 2.0
The CSF 2.0 includes six functions: Govern, Identify, Protect, Detect, Respond, and Recover. The Govern function is new and includes a category for C-SCRM (GV.SC) that provides guidance on how to integrate supply chain risk management throughout your cybersecurity program.
Here are the subcategories within C-SCRM:
- GV.SC-01: A cybersecurity supply chain risk management program, strategy, objectives, policies, and processes are established and agreed to by organizational stakeholders (formerly ID.SC-01)
- GV.SC-02: Cybersecurity roles and responsibilities for suppliers, customers, and partners are established, communicated, and coordinated internally and externally (formerly ID.AM-06)
- GV.SC-03: Cybersecurity supply chain risk management is integrated into cybersecurity and enterprise risk management, risk assessment, and improvement processes (formerly ID.SC-02)
- GV.SC-04: Suppliers are known and prioritized by criticality
- GV.SC-05: Requirements to address cybersecurity risks in supply chains are established, prioritized, and integrated into contracts and other types of agreements with suppliers and other relevant third parties (formerly ID.SC-03)
- GV.SC-06: Planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships
- GV.SC-07: The risks posed by a supplier, their products and services, and other third parties are identified, recorded, prioritized, assessed, responded to, and monitored over the course of the relationship (formerly ID.SC-02, ID.SC-04)
- GV.SC-08: Relevant suppliers and other third parties are included in incident planning, response, and recovery activities (formerly ID.SC-05)
- GV.SC-09: Supply chain security practices are integrated into cybersecurity and enterprise risk management programs, and their performance is monitored throughout the technology product and service life cycle
- GV.SC-10: Cybersecurity supply chain risk management plans include provisions for activities that occur after the conclusion of a partnership or service agreement
How Eclypsium Helps with C-SCRM
A lot of the industry is focusing on software supply chain security for custom-developed applications, but they’re not paying much attention to the infrastructure those applications run on. That’s the gap that Eclypsium fills. Eclypsium’s supply chain security platform protects the hardware, firmware, and software components of your IT infrastructure. Eclypsium previously collaborated with the NIST National Cybersecurity Center of Excellence (NCCoE) on SP 1800-34 demonstrating how C-SCRM should include IT infrastructure.
Eclypsium provides you with intelligence about your supply chain risk for IT products: laptops, desktops, servers, network gear, IoT devices, and software. You can inventory the hardware, firmware, and software components of your IT infrastructure products, prioritize risk—vulnerabilities and misconfigurations—and detect threats such as malicious binaries. We can even help you automate firmware updates.
Eclypsium can help with other CSF 2.0 functions and categories as well, specifically:
- Identify, Asset Management (ID.AM) – Providing you with inventories of hardware, firmware, and software assets, with the ability to generate associated SBOMs.
- Identify, Risk Assessment (ID.RA) – Helping you to measure risk from newly announced vulnerabilities and supply chain incidents and misconfigurations. You can also use Eclypsium to verify the authenticity and integrity of hardware and software prior to acquisition and use.
- Protect, Platform Security (PR.PS) – Automating firmware updates for endpoints and servers, and providing guidance for other types of risk mitigations. We can also help you to harden this attack surface by highlighting misconfigurations that allow attackers to bypass system protections such as Secure Boot.
- Protect, Technology Infrastructure Resilience (PR.IR) – Protecting against unauthorized logical access and usage at the foundational firmware layer of your IT infrastructure devices.
- Detect, Continuous Monitoring (DE.CM) – Detecting known and unknown threats at the hardware and firmware layers that can evade traditional endpoint security such as EDR. Eclypsium has the unique ability to monitor the integrity of firmware binaries for particular assets and groups of assets to detect indicators of compromise. Threat actors have persisted in environments for upwards of 18 months by hiding out in the firmware level, according to Mandiant.
To learn more about the CSF 2.0 draft and specifically the new Govern function, join Eclypsium for our August 30 webinar: Tackling Supply Chain Security with NIST CSF 2.0 featuring Paul Asadoorian, John Loucaides and special guest speaker Rob Efrus.
| Function | Category |
| Govern | Organizational Context |
| Risk Management Strategy | |
| Cybersecurity Supply Chain Risk Management | |
| Roles, Responsibilities, and Authorities | |
| Policies, Processes, and Procedures | |
| Oversight | |
| Identify | Asset Management |
| Risk Assessment | |
| Improvement | |
| Protect | Identity Management, Authentication, and Access Control |
| Awareness and Training | |
| Data Security | |
| Platform Security | |
| Technology Infrastructure Resilience | |
| Detect | Continuous Monitoring |
| Adverse Event Analysis | |
| Respond | Incident Management |
| Incident Analysis | |
| Incident Response Reporting and Communication | |
| Incident Mitigation | |
| Recover | Incident Recovery Plan Execution |
| Incident Recovery Communication |
The post NIST Cybersecurity Framework 2.0 Highlights Supply Chain Security appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.