New Security Vulnerability “regreSSHion” Exposes Millions of Linux OpenSSH Servers to RCE Attacks (CVE-2024-6387)
A newly discovered security vulnerability, dubbed “regreSSHion” (CVE-2024-6387), puts millions of OpenSSH server instances at risk of exploitation. This vulnerability enables attackers to perform Remote Code Execution (RCE), potentially leading to complete system control.

OpenSSH Server is used for secure remote system management, encrypted traffic, and secure tunneling.
What is CVE-2024-6387? (regreSSHion)
CVE-2024-6387 impacts the OpenSSH server (sshd) on glibc-based Linux systems, which handles connections from client applications.
Notably, this vulnerability reintroduces a previously patched issue, tracked as CVE-2006-5051.
It stems from a signal handler race condition in OpenSSH’s sshd and affects the default configuration. Moreover, it does not require user interaction, making it particularly dangerous.
Researchers highlight that this is the first unauthenticated RCE in OpenSSH in nearly two decades. It allows attackers to perform RCE as root and possibly obtain complete control over compromised systems.
Regression of Old Vulnerability in OpenSSH Leads to New Exploitation Risk (CVE-2006-5051)
CVE-2024-6387 was identified as a regression of CVE-2006-5051, a vulnerability first reported in 2006.
CVE-2006-5051 is a signal handler race condition in OpenSSH versions prior to 4.4, which allowed remote attackers to cause a Denial-of-Service (DoS) and potentially execute arbitrary code.
In this context, a ‘regression’ means that a previously fixed security vulnerability has reappeared in a later release, often due to updates or changes that inadvertently reintroduce the issue. Hence, researchers have dubbed CVE-2024-6387 as “regreSSHion.”
According to its advisory, CVE-2024-6387 was introduced with the release of OpenSSH 8.5p1 in October 2020.
What is the scope of the vulnerability?
Reportedly, searches on Shodan and Censys have revealed over 14 million OpenSSH instances potentially exposed to exploitation on the internet.
Within its own customer base, Qualys discovered about 700,000 systems exposed to the internet that seem vulnerable, making up 31% of all internet-facing OpenSSH instances. Additionally, over 0.14% of these vulnerable systems are running outdated, unsupported versions of OpenSSH.
In parallel, a ZoomEye search brings up almost 127 million OpenSSH instances, mainly located in the U.S. and China, showcasing the extensive attack surface for this vulnerability.
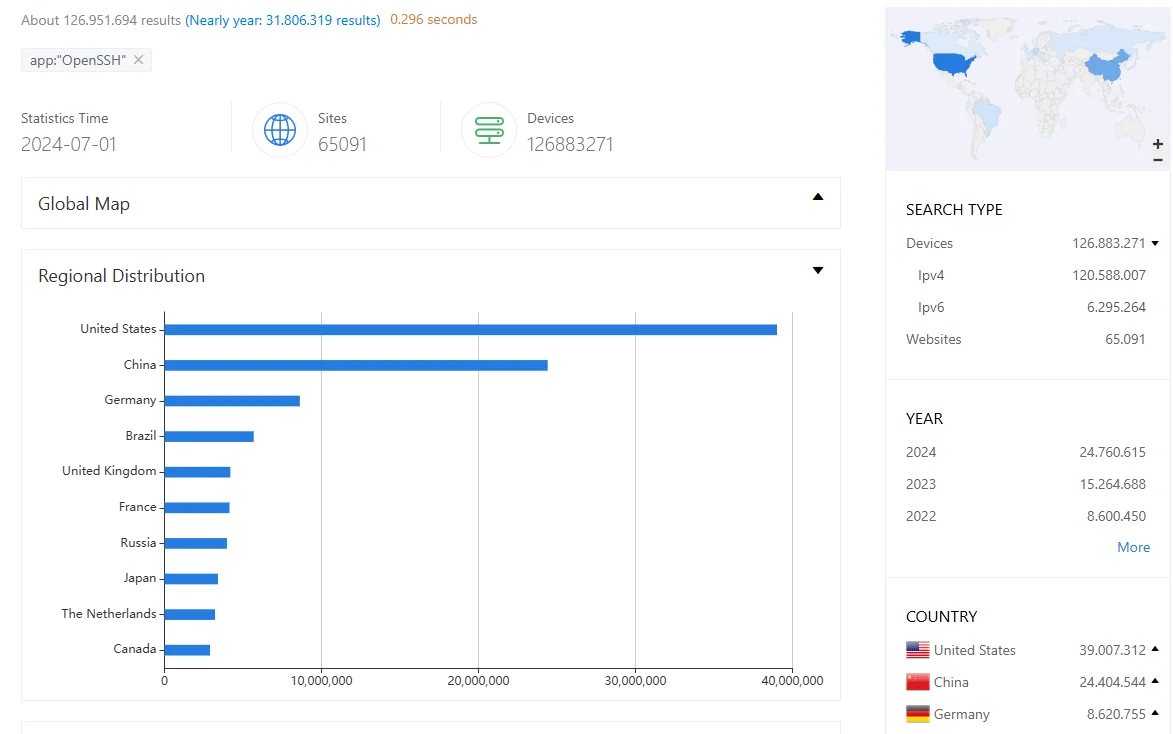
ZoomEye search results for OpenSSH
Researchers also highlight that while the vulnerability might exist on both macOS and Windows platforms, further analysis is needed to confirm its exploitability on these systems.
Receive the Latest Vulnerability Updates with SOCRadar
For the effective management of security vulnerabilities, organizations can rely on SOCRadar’s Vulnerability Intelligence.
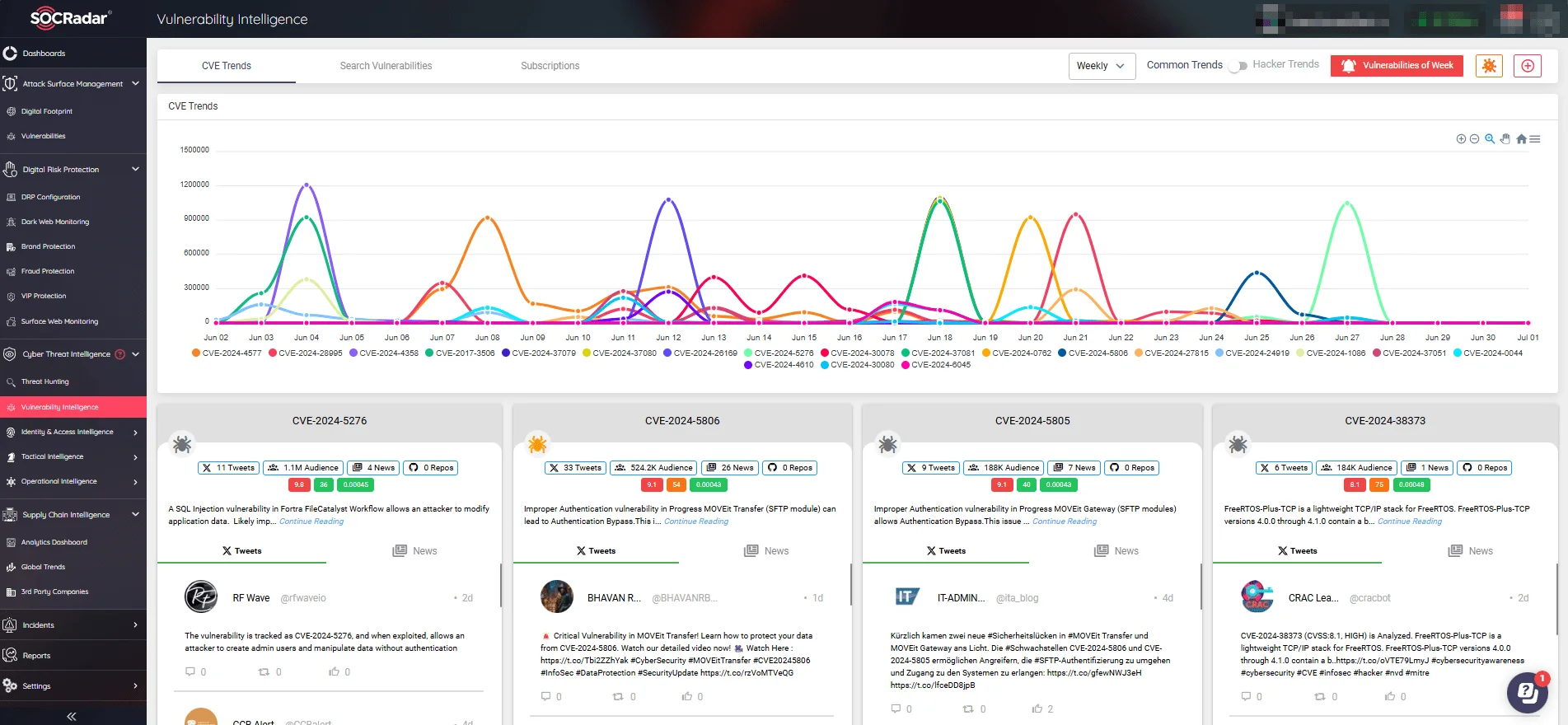
With SOCRadar’s Vulnerability Intelligence, users can ensure they are always up-to-date with the latest threats and vulnerabilities, helping them to secure their systems more effectively.
This powerful module enables you to:
- Access details on identified CVEs, including new exploits, mentions, related threat actors, and more.
- Stay updated on the latest exploitation trends and emerging CVEs to protect your systems against potential attacks
- Filter and search for vulnerabilities by product, vendor, and other tags for targeted and efficient vulnerability management.
Which OpenSSH versions are affected by CVE-2024-6387?
CVE-2024-6387 affects OpenSSH versions from 8.5p1 up to, but not including, 9.8p1.
Indicators of Compromise (IoCs)
You can identify exploitation attempts for this vulnerability by checking the logs for numerous “Timeout before authentication” lines.
Are there any reports of exploitation regarding the regreSSHion vulnerability (CVE-2024-6387)?
Currently, there are no reports of the regreSSHion vulnerability (CVE-2024-6387) being exploited.
OpenSSH’s release note for version 9.8/9.8p1 indicates that successful exploitation has been demonstrated on 32-bit Linux/glibc systems with ASLR enabled. They identified that the attack typically requires 6-8 hours of continuous connections to the server.
While exploitation on 64-bit systems is considered possible, it has not yet been demonstrated. The advisory notes that these attacks will likely be improved upon.
Patch the regreSSHion vulnerability (CVE-2024-6387)
To address this critical vulnerability, ensure you install the latest updates from OpenSSH’s official site.
Is there a workaround?
If sshd can’t be updated or recompiled, set LoginGraceTime to 0 in the config file. This exposes sshd to a denial of service by using up all MaxStartups connections, but it prevents the remote code execution risk.
If updating or recompiling sshd isn’t possible, researchers advise setting ‘LoginGraceTime’ to 0 in the configuration file. They note that while this workaround mitigates the RCE risk, it exposes sshd to a DoS by using up all MaxStartups connections.
To further protect your systems:
- Limit SSH access from network-based controls to minimize attack risks.
- Segment your networks to restrict unauthorized access and lateral movement within critical environments.
- Deploy systems to monitor and alert on unusual activities indicative of exploitation attempts.
With SOCRadar’s Attack Surface Management (ASM) module’s continuous monitoring of digital assets, you can keep up with security incidents and respond quickly to new vulnerabilities.
With SOCRadar’s Attack Surface Management (ASM) module, you can continuously monitor your digital assets and quickly respond to new vulnerabilities. The ASM module provides real-time threat alerts with actionable insights, enabling effective preemptive actions to improve your cybersecurity posture.
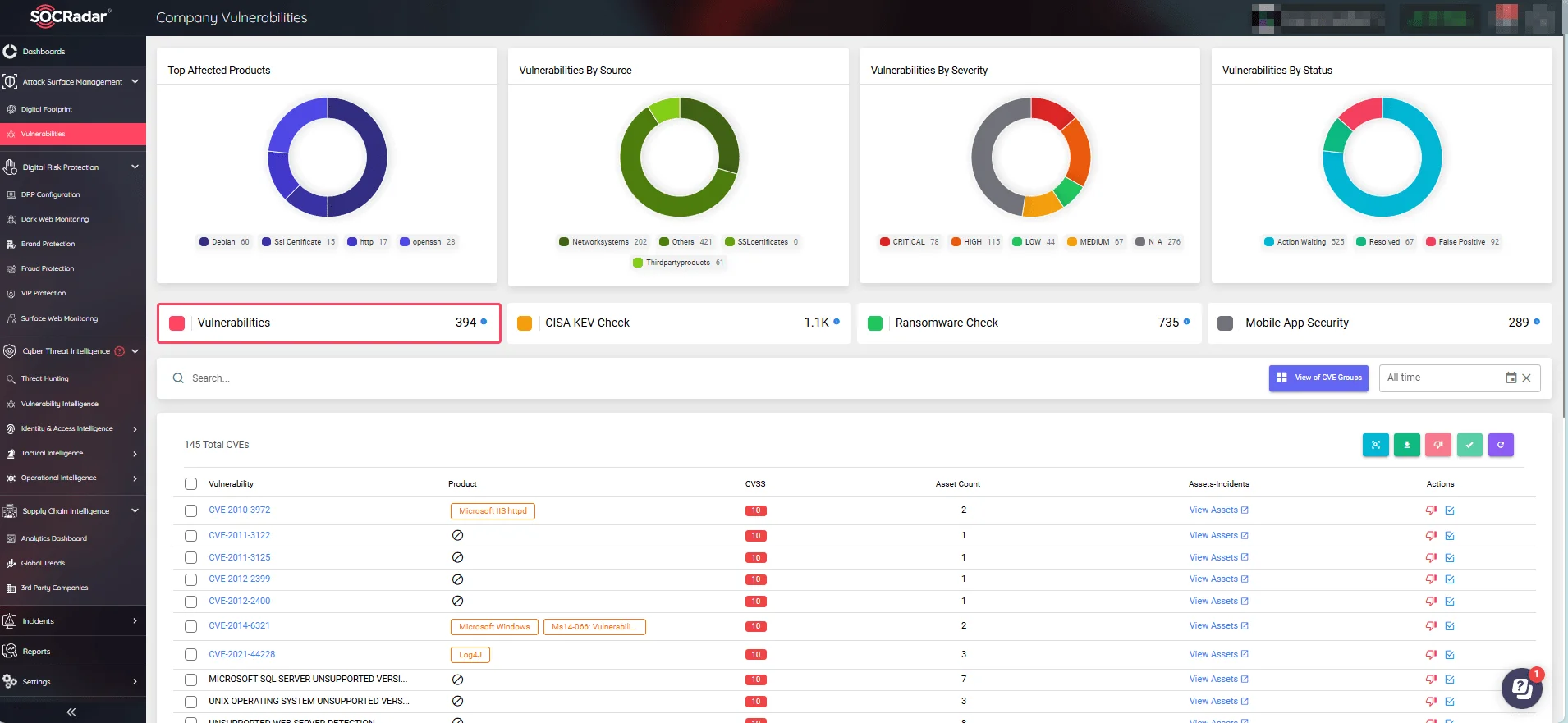
By leveraging SOCRadar’s ASM, you can stay ahead of potential threats, ensuring your digital environments remain secure and resilient against evolving cyber threats.

