A new packed Redline version was found in the wild and it has new tricks that may make it challenging to detect.
What’s new?
McAfee Labs recently discovered a new Redline Stealer variant that uses Lua bytecode to hide its malicious code. This is the first time we’ve seen this technique used in Redline Stealer.
The malware was also found on GitHub, inside Microsoft’s official vcpkg repository: https[:]//github[.]com/microsoft/vcpkg/files/14125503/Cheat.Lab.2.7.2.zip.
The attackers uploaded a malicious zip file named Cheat.Lab.2.7.2.zip to the repository. The zip file contains an MSI installer with two executable files:
- compiler.exe.
- lua51.dll.
As well as a text file readme.txt that holds the Lua bytecode.
Easily detect malware with ANY.RUN interactive sandbox
Register for freeWhat are the implications?
Using Lua bytecode makes it harder for security software to detect the malware. Lua is a less common programming language, so many security tools might not be equipped to properly analyze it. The bytecode allows the attackers to obfuscate malicious strings and evade detection by traditional means.
Distributing the malware through GitHub is also concerning. Recently, we wrote about a phishing campaign deploying STRAAT and VCURMS via Github. In all of these cases, the commercial protection of this platform makes it harder to detect the malicious nature of the files, and because GitHub is so widely used to share code, many people don’t think twice before downloading the file hosted there.
Is this a new trend and will we see more malware using GitHub for distribution?
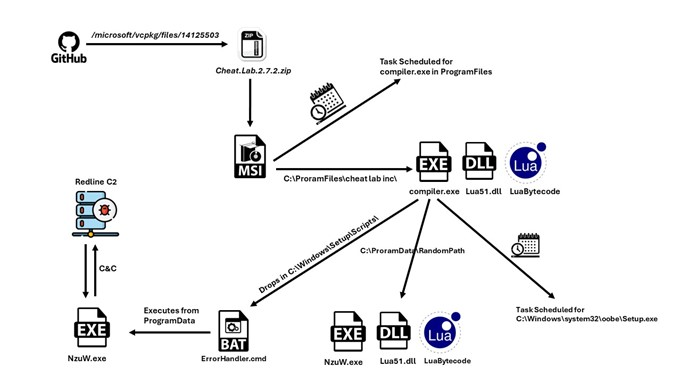 New Redline version infection chain. Source: McAffee
New Redline version infection chain. Source: McAffeeHow does the new Redline version work?
When someone runs the MSI installer, it creates a scheduled task to execute compiler.exe with readme.txt (the Lua bytecode) as an argument.
The malware also sets up a second persistence method by copying itself to a hidden folder and creating a file called ErrorHandler.cmd at C:\Windows\Setup\Scripts\.
The malware communicates with its C2 over HTTP. It can take screenshots and gather information about the infected computer, including:
- Its IP address.
- Machine ID.
- Username.
Analyzing the Lua bytecode is tricky because it’s hard to decompile back into readable code. The script contains obfuscated data and a complex decryption loop.
The malware uses Lua’s foreign function interface (FFI) to call Windows API functions directly, making it harder to detect still.
Normally, when malware wants to interact with the Windows operating system (for example, to connect to C2), it has to use the standard Windows API functions, which are well-known and monitored by security software.
By using Lua’s FFI, the malware can directly call the low-level Windows API functions, without going through the standard channels, effectively hiding in plain sight.
Sandbox analysis in ANY.RUN
Let’s replicate the execution chain in ANY.RUN interactive malware sandbox. We will run this sample, and see how it would behave in a real system.
We can see that the Malware was hosted on GitHub’s repository. The download, Cheat.Lab.2.7.2.zip, contained an MSI that installs modified Lua binaries to enhance stealth by evading detection.
Easily analyze malware in ANY.RUN cloud sandbox
Register for freeThe installation process writes three files, prompts users to spread the malware, and creates tasks for execution using system vulnerabilities. It communicates with a command server via HTTP, sending data and receiving tasks.
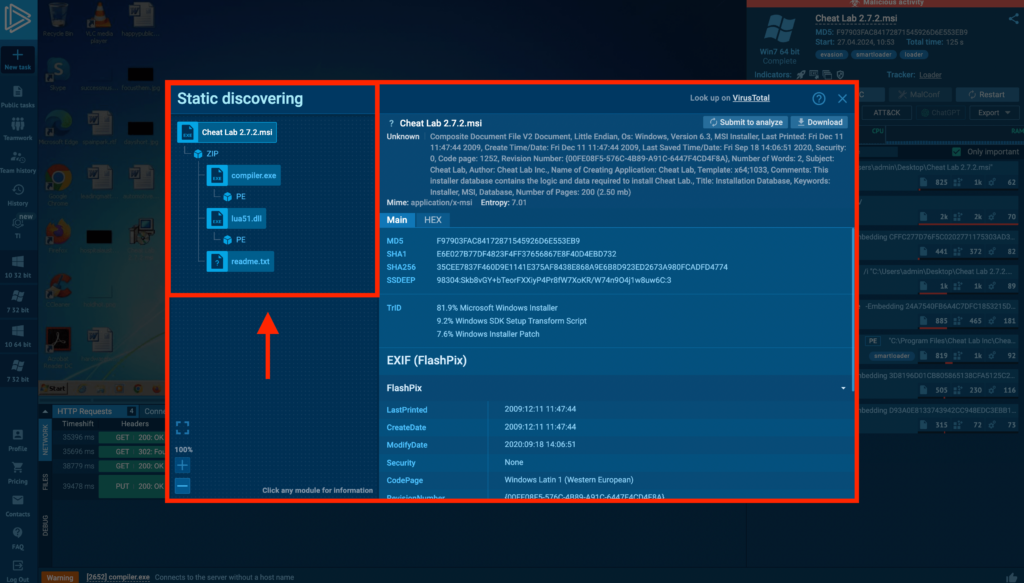 Static analysis of the Cheat.Lab.2.7.2.msi in ANY.RUN
Static analysis of the Cheat.Lab.2.7.2.msi in ANY.RUNThe MSI in the archive includes 2 PE files and a binary file with a .txt extension. Upon execution, msiexec runs Cheat.Lab.2.7.2.msi which triggers the PE file compiler.exe.
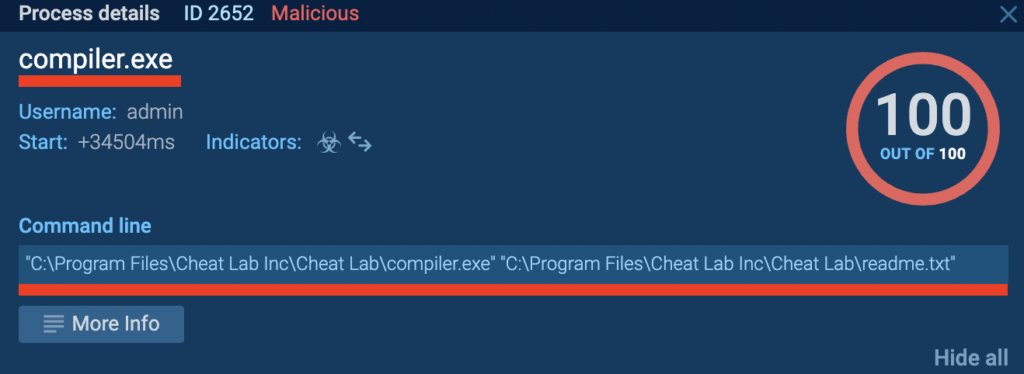 The binary file readme.txt is used as an argument
The binary file readme.txt is used as an argumentThis PE file loads lua51.dll and uses the binary file readme.txt as an argument. Subsequently, compiler.exe retrieves IP addresses from pastebin.com and attempts to connect to them. It sends an HTTP PUT request to the server with /loader/screen/ as part of the URL and uses the user agent Winter (shown below).
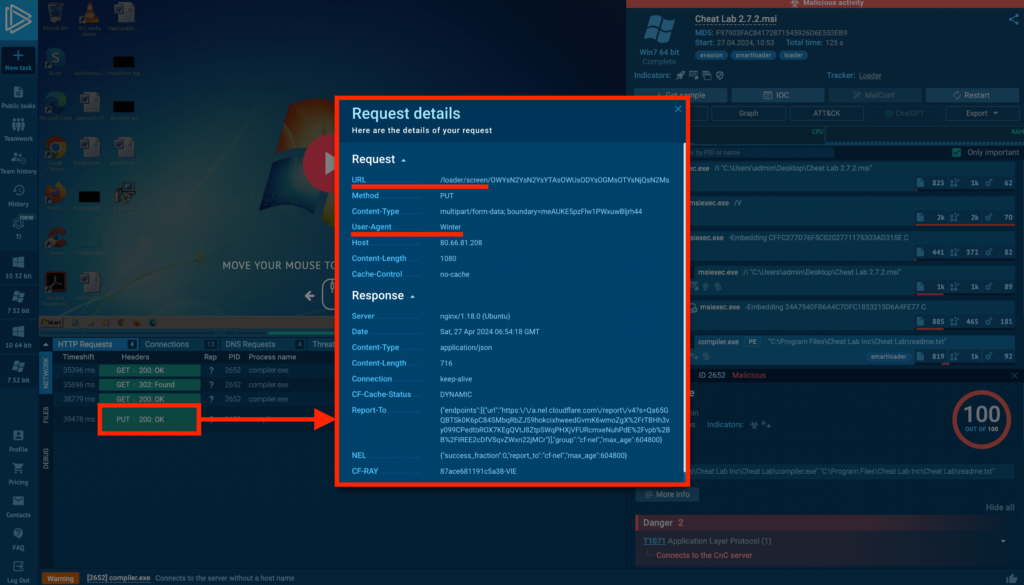 Easily analyze details of HTTP requests in ANY.RUN’s network tab
Easily analyze details of HTTP requests in ANY.RUN’s network tabDuring our analysis, the complete execution chain could not be fully detailed because the C2 server was already inactive.
Wrapping up
Redline Stealer is a very popular malware. In fact, in ANY.RUN’s Q1 Malware Trends report, it was the 5th most frequently detected family in all public tasks uploaded to ANY.RUN’s sandbox. McAfee’s data also shows that this strain is widespread: they have seen it in North America, South America, Europe, Asia and Australia.
This story is a good reminder that we need to be extra careful about the files we download — granted, in this case the file was masquerading as a cheat, which is never a good idea to download, but the same strategy can be applied to mimic a productivity application or script.
When in doubt, you can always throw any suspicious files into a sandbox such as ANY.RUN, which will detect and highlight malicious activity through YARA, Suricata or Signatures.
Analyze malware in the ANY.RUN sandbox
Sign up for freeAbout ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
Let us give you an interactive presentation of ANY.RUN and show you how it can help your security team.
The post New Redline Version: Uses Lua Bytecode, Propagates Through GitHub appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: New Redline Version: Uses Lua Bytecode, spreads via GitHub