The U.S. Securities and Exchange Commission (SEC), a regulatory body responsible for overseeing securities markets and protecting investors, has recently introduced new rules regarding the disclosure of cybersecurity incidents. As cybersecurity professionals, it is vital to grasp these changes, as they can significantly impact how companies approach incident response and reporting.
Background of the Change of Rules by SEC
The new rules by SEC mandate that companies promptly disclose any cybersecurity incidents that could have a material impact on their operations or financial condition. This change stems from a rising trend in cyber threats and their potential repercussions on the financial stability of businesses.
Considering the increasing significance of cybersecurity in the corporate world, SEC Chair Gary Gensler pointed out, “Whether a company loses a factory in a fire — or millions of files in a cybersecurity incident — it may be material to investors. Currently, many public companies provide cybersecurity disclosure to investors. I think companies and investors alike, however, would benefit if this disclosure were made in a more consistent, comparable, and decision-useful way. Through helping to ensure that companies disclose material cybersecurity information, today’s rules will benefit investors, companies, and the markets connecting them.” This emphasis on uniform and meaningful disclosures underscores the broader move towards transparency and informed decision-making in the financial markets.
What’s New in the SEC Rules?
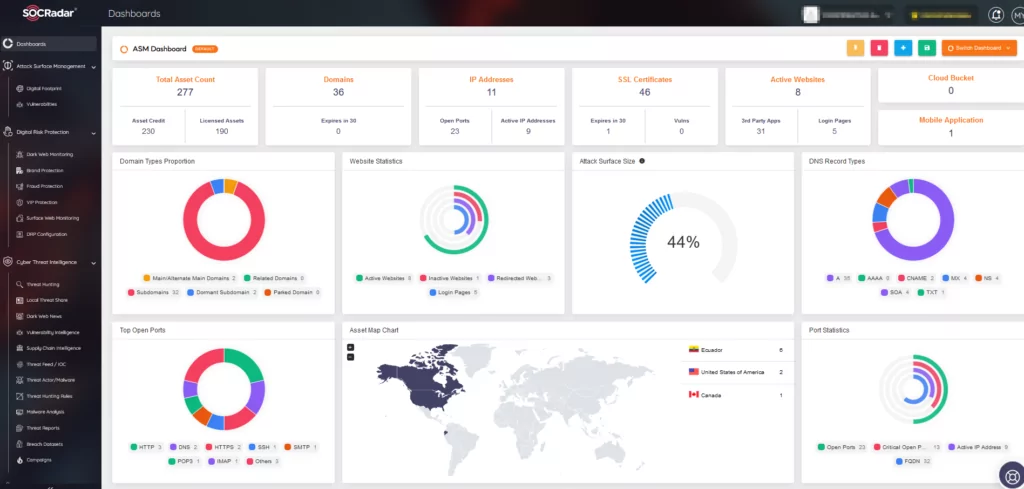 The new SEC rules emphasize prevention. Tools like SOCRadar’s Extended Attack Surface Management become essential for companies.
The new SEC rules emphasize prevention. Tools like SOCRadar’s Extended Attack Surface Management become essential for companies.
- Companies must now report material cybersecurity incidents within four business days via a Form 8-K.
The new regulation introduces an amendment to Form 8-K, introducing Item 1.05 titled “Material Cybersecurity Incidents.” This mandates that companies must report significant cybersecurity breaches within four business days once they recognize the event’s materiality. However, to make a comprehensive report, companies need critical details such as TTPs (Tactics, Techniques, and Procedures) and IOCs (Indicators of Compromise). These essential details can be readily provided by a Threat Intelligence Provider.
Essentially, Item 1.05 describes a cybersecurity event as any unauthorized action or a chain of such actions on a company’s information systems that potentially compromise the system’s security or the data contained within it.
- There is an emphasis on enhancing disclosures about companies’ cybersecurity risk management and governance in annual reports on Form 10-K and Form 20-F.
All companies are obligated to include the fresh details about cybersecurity risk management and governance as per Item 106 of Regulation S-K (or equivalent stipulations for FPIs in Form 20-F). This is mandatory starting from the annual reports of fiscal periods concluding on or post-December 15, 2023. Hence, companies that operate on a calendar year basis need to adhere to these updated regulations in their forthcoming annual statements.
- Companies must describe processes for assessing, identifying, and managing cybersecurity threats. This includes detailing how these processes integrate into the company’s overall risk management system, the involvement of third parties, and oversight of risks from third-party service providers.
New Item 106(b) of Regulation S-K mandates that companies include in their Form 10-K (or Form 20-F) details on:
The measures they’ve implemented for detecting, understanding, and handling significant risks from cyber threats. These details should be comprehensive enough for a well-informed investor to grasp, which encompasses:
- How these cyber-related measures fit into the company’s broader risk management strategies;
- If they collaborate with experts, consultants, auditors, or other external entities for these measures;
- The existence of systems in place to supervise and pinpoint prominent cyber risks when partnering with third-party service providers.
Discussing if any cyber threats or prior cybersecurity events have had or might have significant consequences on the company’s operational strategy, operational results, or financial standing and, if so, the nature of these effects.
The challenge is that it is not sufficient for just your systems to be secure. Your entire supply chain and all the vendors you engage with must also be safeguarded. As recent breaches with MOVEit have demonstrated, vulnerabilities in third-party systems can lead to compromises, even if your own network is fortified. To truly ensure security, it is imperative to monitor your entire ecosystem, especially your supply chain. A comprehensive threat intelligence service like SOCRadar can provide the insights you need about third-party risks.
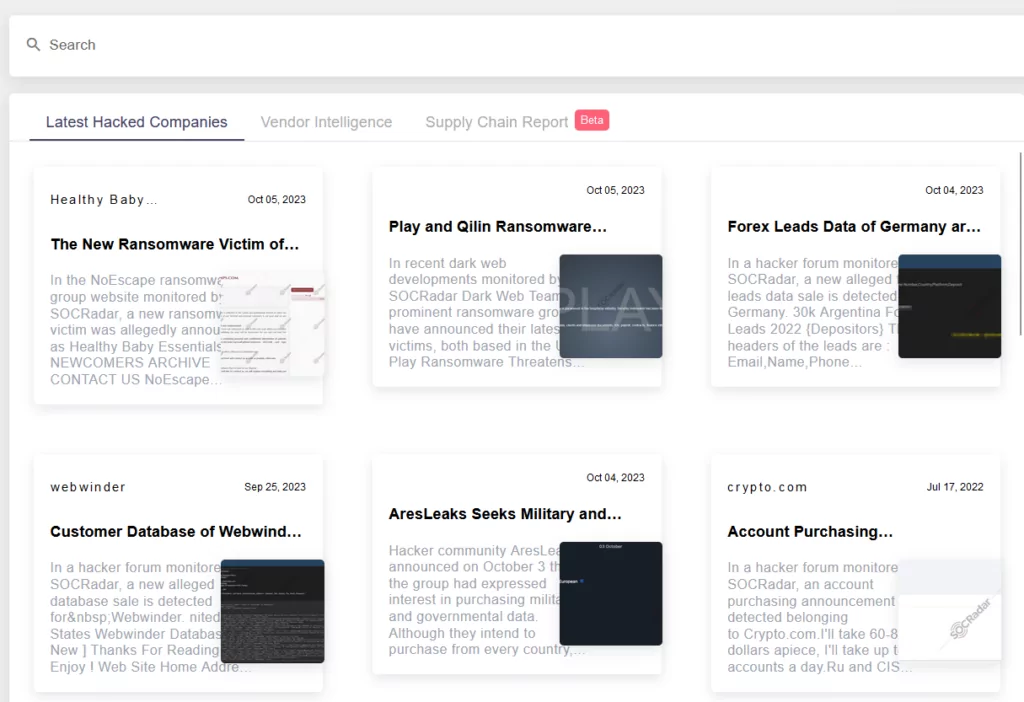 The Supply Chain Intelligence module of SOCRadar.
The Supply Chain Intelligence module of SOCRadar.
The scope of these disclosure mandates was refined and made more specific based on feedback. The finalized guidelines don’t necessitatein-depth disclosure about preventive actions, recovery strategies, or how past incidents have shaped policy or tech governance. Given wide-ranging worries about the initial rules being too directive, potentially impacting corporate risk management choices, it was expressly stated in the finalizing release that the main aim is to enlighten investors, rather than dictate how companies should tackle their cybersecurity threats.
- There’s also a focus on board oversight and management’s role in assessing cybersecurity threats. Companies need to detail which board committee is responsible for cybersecurity risk oversight and how frequently the board discusses these risks.
The updated Item 106(c) of Regulation S-K necessitates that companies outline in their Form 10-K (or Form 20-F):
The board’s supervision of cybersecurity risks, covering:
- Any specific board committee or subcommittee handling oversight.
- The method through which the board or committee stays informed about these risks.
The role of management in assessing and handling significant cyber risks, which includes:
- Identifying key management roles or committees in charge of such risks and elaborating on their expertise.
- The mechanisms by which these entities stay updated and monitor the handling of cybersecurity incidents.
- Reporting structures between these entities and the board or its committees.
The SEC decided against initially suggested changes that would have demanded more specific disclosures about the board’s role in embedding cybersecurity in business strategy and other areas. Yet, the SEC highlighted that some companies might need to discuss how often their board or committees engage in cyber risk discussions, depending on the context.
Companies Affected
The new rules apply to all companies registered with the SEC (basically all publicly traded companies or registrants). This encompasses both domestic firms and foreign private issuers. Even incidents originating on the systems of third-party service providers are within the scope of these rules, emphasizing the interconnectedness of today’s digital business ecosystem.
Effective Dates
All registrants, except for smaller reporting companies, need to adhere to the new incident disclosure norms outlined in Item 1.05 of Form 8-K and in Form 6-K beginning December 18, 2023. However, if the rules are published in the Federal Register after this date, they have an additional 90 days from the publication date. On the other hand, smaller reporting companies get an extended timeline and must start abiding by Form 8-K Item 1.05 from June 15, 2024, or 270 days post the rule’s publication date in the Federal Register if that’s later.
|
Effective date |
Entity Type (As defined by the SEC) |
|
|
Annual Disclosures |
December 15, 2023 |
All Public Companies |
|
“Material” Incident Disclosures |
December 18, 2023 |
Public Companies (not including “Smaller Reporting Companies”) |
|
“Material” Incident Disclosures |
December 18, 2023 |
Foreign Private Insurer filing on Domestic Forms |
|
“Material” Incident Disclosures |
June 15, 2024 |
“Smaller Reporting Companies” |
Recommendations for Companies
Review Current Systems: Given the upcoming disclosure requirements, companies should revisit their cybersecurity and risk management systems, emphasizing any recent tech infrastructure changes, shifts in the cybersecurity threat landscape, and insights from recent security incidents.
A threat intelligence provider can be incredibly beneficial in this context. This is because vital prevention measures such as Attack Surface Management and Supply Chain Intelligence often go overlooked by SOC teams who are typically overwhelmed with other tasks.
Enhance Communication Protocols: With third-party incidents also coming under the purview of these rules, companies should establish robust communication channels with their third-party providers to ensure timely assessment and disclosure.
Strengthen Governance Structures: Organizations must evaluate their existing cybersecurity risk oversight structures at both board and management levels, making necessary improvements to ensure compliance and to safeguard against potential risks.
Harnessing SOCRadar: Proactive Defense
In the face of ever-evolving cyber threats, especially in light of the SEC’s new rules on cybersecurity disclosure, companies are now under more pressure than ever to ensure they are protected. Enter Cyber Threat Intelligence (CTI). CTI acts as the eyes and ears of an organization in the vast digital universe, pre-emptively scouting for threats and ensuring that defenses are always one step ahead. Using platforms like SOCRadar can drastically improve a company’s defense against cyber threats. Let’s delve deeper into how.
- Know Your Internet-Facing Assets: The First Line of Defense
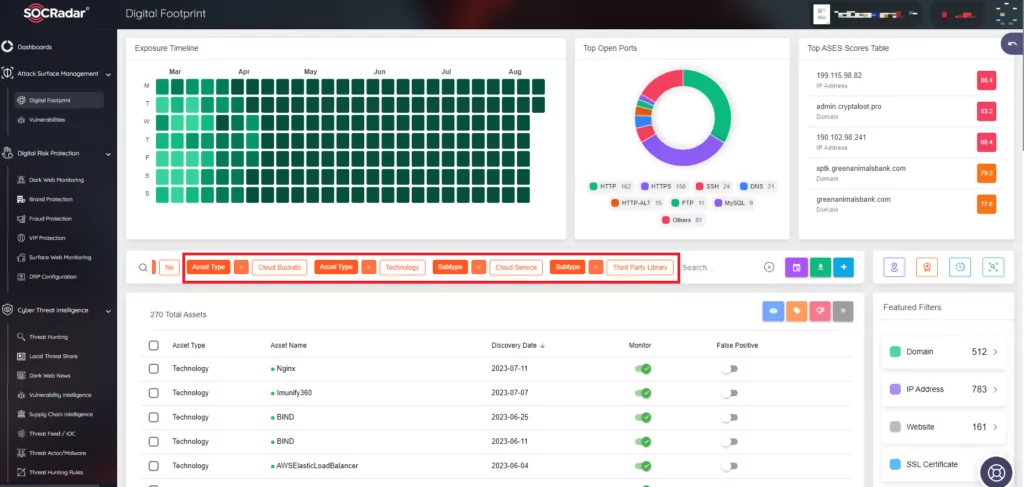 Monitoring your dynamic digital footprint is crucial for effective Attack Surface Management.
Monitoring your dynamic digital footprint is crucial for effective Attack Surface Management.
Prevention is undoubtedly the best strategy in cybersecurity. But to prevent potential cyber attacks, it’s crucial first to understand and have a comprehensive view of all your digital touchpoints exposed to the world. This is where SOCRadar’s External Attack Surface Management module steps in. It systematically identifies and maps out all internet-facing assets, giving companies clarity on potential vulnerability points and allowing for timely reinforcement before an attack happens.
- Peek into the Dark Web: Stay Updated on Potential Threats
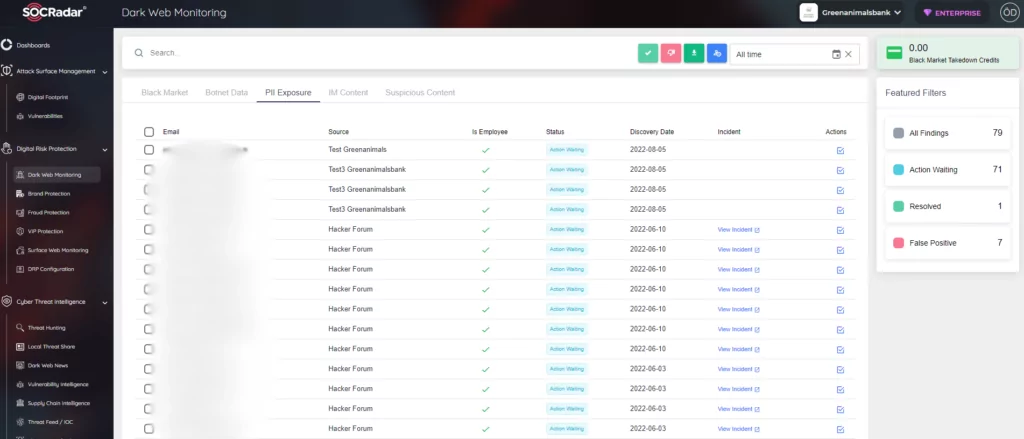 Being aware of conversations about your company on both the clear and dark web is a crucial prevention step. For instance, monitoring potential impersonation sites of your domain can prevent significant troubles and protect your reputation.
Being aware of conversations about your company on both the clear and dark web is a crucial prevention step. For instance, monitoring potential impersonation sites of your domain can prevent significant troubles and protect your reputation.
Information about a company or its assets can sometimes lurk in the dark corners of the web, often signaling an impending attack or a data breach. SOCRadar’s Digital Risk Protection module proactively scans the dark web to ensure that no unauthorized details about a company or its digital assets are floating around. This early warning system can be crucial in preventing potential cyber threats.
- Trend Monitoring & Proactive Threat Hunting: Staying Ahead in the Game
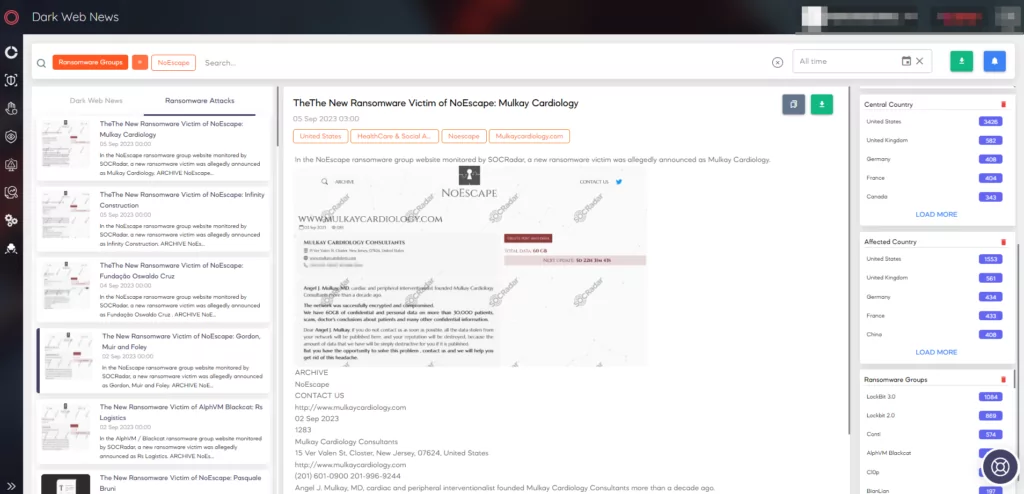 Monitoring the dark web for geolocal and industry trends has become an integral aspect of preventive threat intelligence.
Monitoring the dark web for geolocal and industry trends has become an integral aspect of preventive threat intelligence.
It’s not just about your company. In today’s interconnected world, trends affecting your region or industry can signal threats to your organization. SOCRadar’s Cyber Threat Intelligence module goes beyond company-centric scans. It monitors dark web trends specific to your geolocation and industry, giving a holistic view of potential threats. Additionally, instead of waiting for threats to be evident, proactive threat hunting identifies possible future threats, ensuring your defenses are always prepared.
Conclusion
In conclusion, as the regulatory environment becomes more stringent with requirements for timely disclosure of cybersecurity incidents, it is not just about reacting swiftly after an incident but being prepared before it occurs. Platforms like SOCRadar are not just tools but essential partners in this journey, offering a comprehensive, proactive, and strategic approach to cybersecurity. With them on your side, not only can you comply with regulations, but you can also ensure the integrity of your digital assets and, most importantly, the trust of your stakeholders.
The new rules of SEC are a testament to the rising significance of cybersecurity in today’s business environment. While they add layers of responsibility for companies, they also underline the importance of transparency and proactive risk management in protecting both businesses and investors. For cybersecurity professionals, understanding and aligning with these changes is not just about compliance; it’s about fostering a culture of robust cybersecurity awareness and preparedness.
The post New Cybersecurity Rules of SEC: What Businesses Need to Know appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: New Cybersecurity Rules of SEC: What Businesses Need to Know
