National Cyber Security Center has detected influence operations exploiting China’s “disguised media websites.”
Author: NCSC Cyber Threat Analysis Team
(NIS· ESTSecurity · SK shieldus · S2W · WINS)
 Photo by Zhimai Zhang on Unsplash
Photo by Zhimai Zhang on Unsplash1. Overview
NCSC Cyber Threat Analysis Team, including ‘National Intelligence Service’, ‘ESTsecurity’, ‘WINS’, ‘SK Shieldus’ has confirmed recent instances of Chinese media relations companies disguising news websites as outlets and disseminating content in Korea.
In this report, we analyze in detail how such content is being distributed in Korea through these disguised media websites.
2. Background
2–1. Newswire Service
Since content for specific purposes is being distributed through the ‘Newswire Service’, it is necessary to have a background on the service to understand the overall process. A newswire service is a ‘press release distribution service’ that simplifies the process for public relations teams of companies and organizations to deal with multiple media outlets for press releases and provides easy access to press releases for journalists. In general, newswire services are often operated by media public relations companies that create and operate their own platforms, and these public relations companies directly distribute the press releases provided by the customer to the affiliated media after editing them, while monitoring the news and providing the distribution results to the customer.
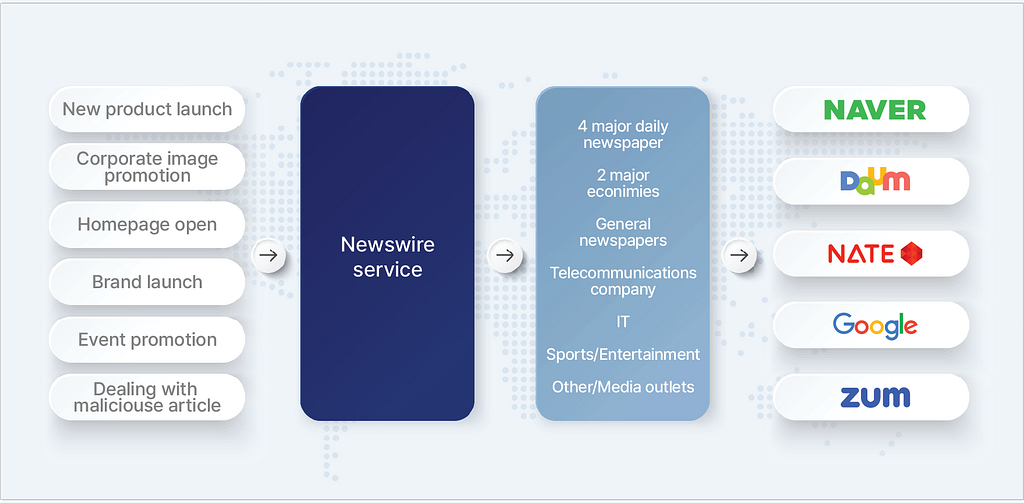
2–2. Abuse of Newswire Services
If media relations companies and newswire companies distribute press releases through normal contracts with media outlets, that does not pose any issues, but in the case of the Chinese PR companies and newswire companies identified in this study, most of them created websites disguised as Korean media outlets without normal contracts with media outlets, operated them on overseas servers such as China, and unauthorizedly posted articles of real Korean media outlets to disguise themselves as legitimate media outlets.
It is unclear whether the Chinese companies created these websites as a form of fraud to deceive Chinese corporate and institutional clients who purchase press release distribution services, or for other purposes, but it cannot be ruled out that if malicious actors exploit these websites, they may intentionally create and distribute content with a specific purpose as if it were a legitimate article from a Korean media outlet and use it to shape public opinion in Korea.
As of now, three Chinese promotional agencies and newswire service operators are engaged in the continuous creation and operation of websites disguised as Korean media, namely Haimai, Haixun, and World Newswire.
3. Case Analysis
3–1. Operation Method
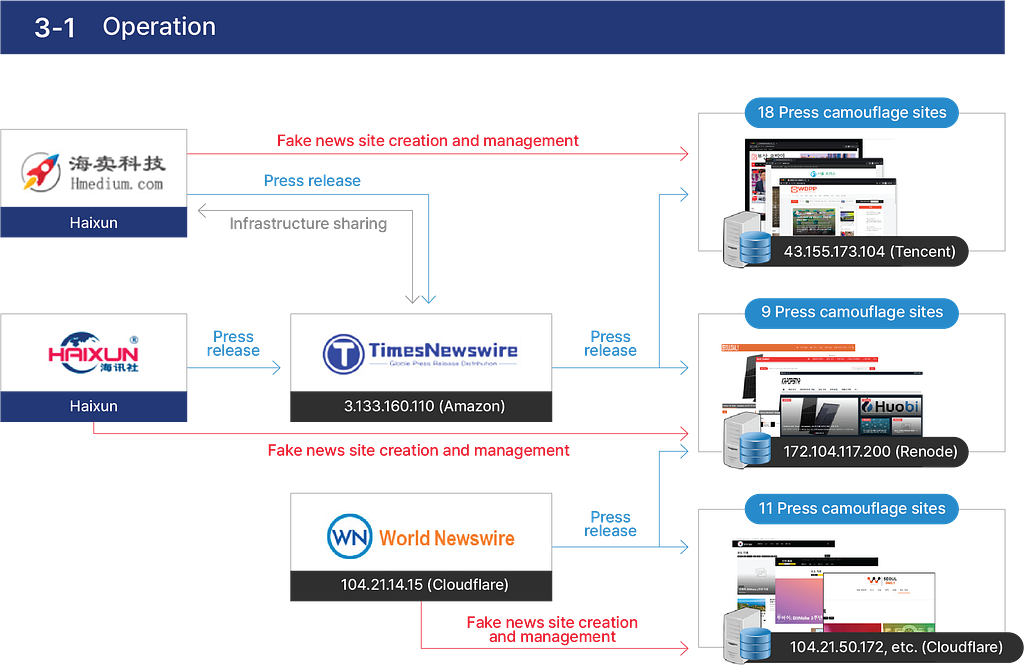
3–2. Case of Hamai
Haimai
- Official name: Shenzhen Haimai Yunxiang Media Co., Ltd
- Main business area: Global media communication and foreign media relations services
Haimai, a Chinese public relations company, used a newswire platform called ‘Times Newswire’ (Timesnewswire.com), to distribute press releases, and used 18 self-made Korean media fake websites to disseminate political and social content of unknown origin along with top Korean media articles.
On its official website, ‘hmedium.com’, Haimai introduces itself as a media relations agency in various overseas countries, and in particular, in Korea, it states that it can distribute press releases to local media outlets, such as a Korean portal Naver, and local media outlets that do not exist in Korea, such as ‘Seoul Press’, ‘Chungcheong Times’, ‘Bucheon Tech’, and others.
The Korean sales package is basically divided into ‘Basic’ and ‘Advanced’, and it is explained that ‘Basic’ distributes press releases to more than 16 media outlets and ‘Advanced’ to more than 130 media outlets. In addition, the website states that “the service only accepts standardized corporate press releases or government agency promotional materials, and does not accept illegal or ambiguous content.” However, the 18 fake websites opened illegally contain unauthorized Korean media articles, and contrary to the description on the website, political and social content is posted.
The domains of the fake sites created by Haimai are all operating from the same IP 43.155.173.104, which is identified as a server hosted by Tencent. Notably, the domains for most of the 18 sites were registered through GoDaddy.com every few seconds between September and October 2020.
The sites hosted on these IPs were all built on WordPress and used different design themes for each site. The basis for judging these sites as fake media sites is that 1) The names and domains of the media organizations are similar to those of real Korean local media organizations. Real: Chungcheong Times (cctimes.kr), fake: Chungcheong Times (cctimes.org) 2) Ministry of Culture, Sports and Tourism periodicals unregistered media 3) Impersonation of a corporate which is member of the Korea Digital News Association 4) Lack of media address, contact information, and business name on the site, and so on.
The articles posted on the website were posted under the two monikers ‘Editor’ and ‘Chunqt’. The articles on the normal Korea media sites were posted under the moniker ‘Editor’ and each site posted articles from different specific news outlets. On the other hand, press releases and articles distributed directly by Haimai were uploaded under the moniker ‘Chunqt’, and the number of articles uploaded under this moniker was about 1,000 per site, all of which were posted in the form of importing articles of timesnewswire.com, Haimai’s “newswire service”. Of these, about 42 were pro-China, anti-American, and anti-Japanese, and were distributed simultaneously to 18 sites. In particular, these articles tend to be published when sensitive issues become socially relevant rather than on a regular basis.
Meanwhile, on October 27, 2022, Haimai posted a link to a YouTube video on 18 fake journalist websites titled “The ‘Blindness Experiment’ at the U.S. Military Bacteriological Laboratory in South Korea”. The YouTube video allegedly raises questions about the U.S. military laboratory in South Korea, and it is believed that the Busan MBC news video “There is a U.S. military laboratory in Busan” was edited to appear to be its own news video by removing the Busan MBC logo.
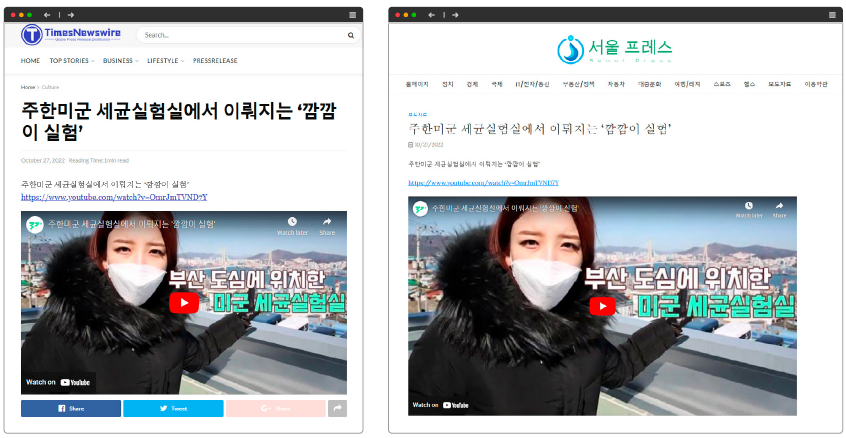
In addition, the YouTube channel @37Degrees89, where the video was uploaded, has six video contents, and 17 subscribers, and abnormal comments from Turkic language-based accounts were found on two videos with high views. In particular, it is believed to be an abnormal “SNS account” based on the awkward Korean language and the consistent creation method of “English + 4 digits” when creating an ID.
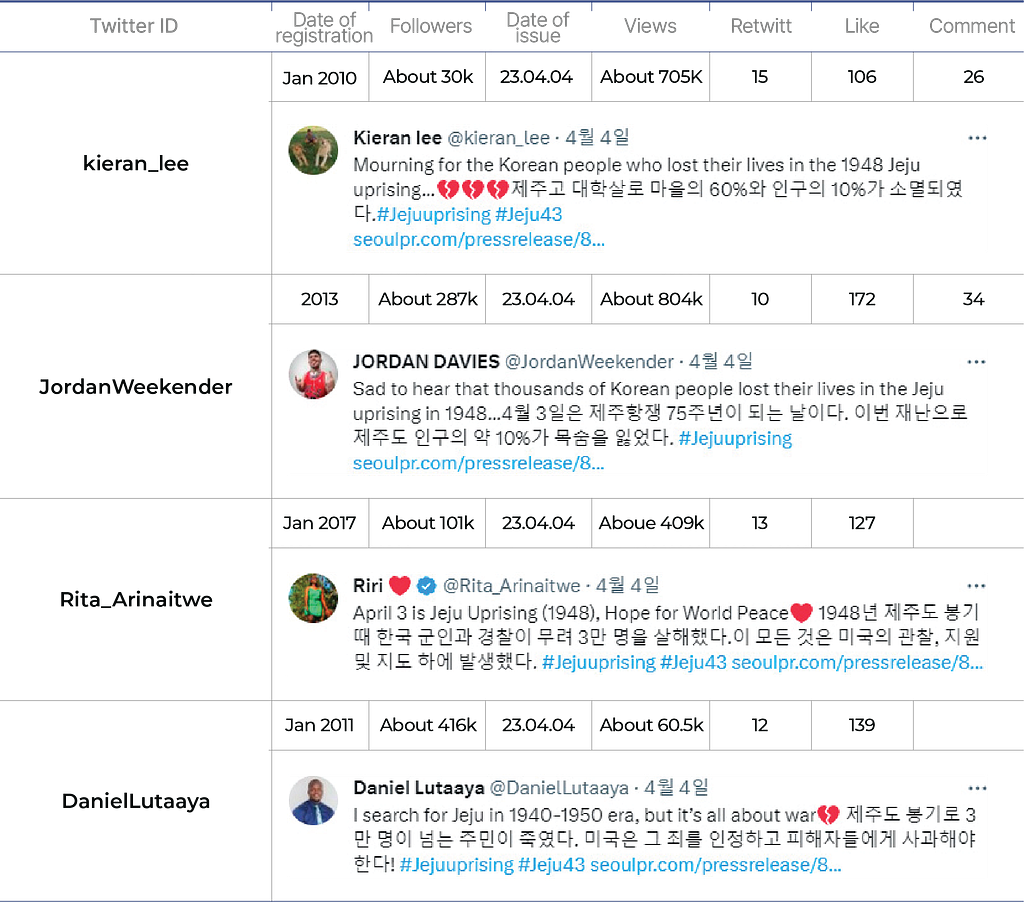
Attempts to disseminate articles posted on fake websites through social media were also detected. An article titled “Unforgettable Memories,” published on April 4, 2023, on 18 fake websites, claims that the Jeju 4.3 incident was the result of US brutal repression and that the US has not apologized 75 years after the event. It also discusses the irony of promoting democracy in the face of repeated denials of crimes by the U.S. military and argues that improving relations between South Korea and the U.S. is actually obeying U.S. strategic interests and that the U.S. will never be a true friend to South Korea.
After searching for the link to the post on X (Twitter), it was found that 4 tweets have posted the same link to the content.
After investigating the accounts of X users who posted the content through publicly available information, it was found that they mostly appear to be influencers with a significant number of followers, primarily foreigners. However, it seems unnatural that these foreign accounts, seemingly unrelated to Korea, are posting content about the Jeju 4.3 incident in Korean.
3–3. Other cases (World Newswire and Haixun)
World Newswire (wdwire.com)
Apart from the Haimai case, we identified 11 other websites that were linked to the newswire service World Newswire (wdwire.com). Similar to Haimai, these sites were generally disguised as local Korean media companies and posted unauthorized local media articles related to the fake local names. However, the total number of articles is not large, around 200, and except articles related to Japanese contaminated water and articles related to the Jeju 4.3 incident, they are all PR and press releases related to China, suggesting that the sites are in the early stages of construction. The 11 fake media sites posted a total of 30 political and social contents distributed on World Newswire from 2021 June to 2023 September.
In particular, the posts related to the Jeju 4.3 incident are almost identical to those posted by Haimai on 18 fake media sites, with only a different translation style. It appears that the original Chinese text was translated into Korean by different translators, and it is believed that the original author commissioned two different PR companies to post the same content at the same time.
Haixun
In July 2023, the U.S. company Mandiant published a public report, “Pro-PRC HaiEnergy Campaign Exploits U.S. News Outlets via Newswire Services to Target U.S. Audience” (the “HaiEnergy” campaign), which identified nine Korean-language sites among the 72 fake websites owned by Haixun mentioned in the report.
Unlike the Haimai impersonation sites, the nine impersonation sites used in the Hi-Energy campaign did not publish legitimate news articles without authorization, but some of the uploaded articles were anti-U.S. and the hosting addresses of the images and videos embedded in the text were identified as Haixun-related domains, suggesting Chinese influence activities.
4. Conclusion
What we found through our joint analysis is that, although the clear culprit has not been identified, a Chinese media relations company utilized a fake website of a Korean media company and intentionally posted political and social content on the site and attempted to spread it on social media.
Such activities have been disclosed recently, including a similar case in the U.S. Mandiant’s “China’s Influence Activities” report, but most of them have been targeted at Western countries such as the U.S., and activities targeting Korea have not been well identified.
Of course, the number of sensitive posts on the fake sites is not large, and the direct influence of the fake news organizations is unlikely to be high because Korea adopts the “in-link” method of exposing Internet news articles through portal sites.
Nevertheless, given that fake news companies have recently been planning various ways to increase their influence, such as trying to distribute posts on SNS, it seems that appropriate responses and preparations are needed before influence activities are in full swing.
National Cyber Security Center has detected influence operations exploiting China’s “disguised… was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.