![]()
Recorded Future's Insikt Group has conducted an analysis of a prolonged cyber-espionage campaign known as TAG-74, which is attributed to Chinese state-sponsored actors. TAG-74 primarily focuses on infiltrating South Korean academic, political, and government organizations. This group has been linked to Chinese military intelligence and poses a significant threat to academic, aerospace and defense, government, military, and political entities in South Korea, Japan, and Russia. TAG-74s targeting of South Korean academic institutions aligns with China's broader espionage efforts aimed at intellectual property theft and expanding its influence within higher education worldwide.
The motivation behind Chinese state-sponsored actors collecting intelligence in South Korea is likely driven by regional proximity and South Korea's strategic role in China's competition with the United States and its regional allies in the Indo-Pacific. Recent tensions have emerged as China expressed concerns about South Korea's closer relations with the US and its perceived involvement in Taiwan and alignment with the US and Japan's containment of China. TAG-74's intelligence collection efforts, which include spoofed domains and decoy documents related to inter-Korean cooperation, are expected to intensify as China seeks information to shape its diplomatic and business engagements with South Korean entities.
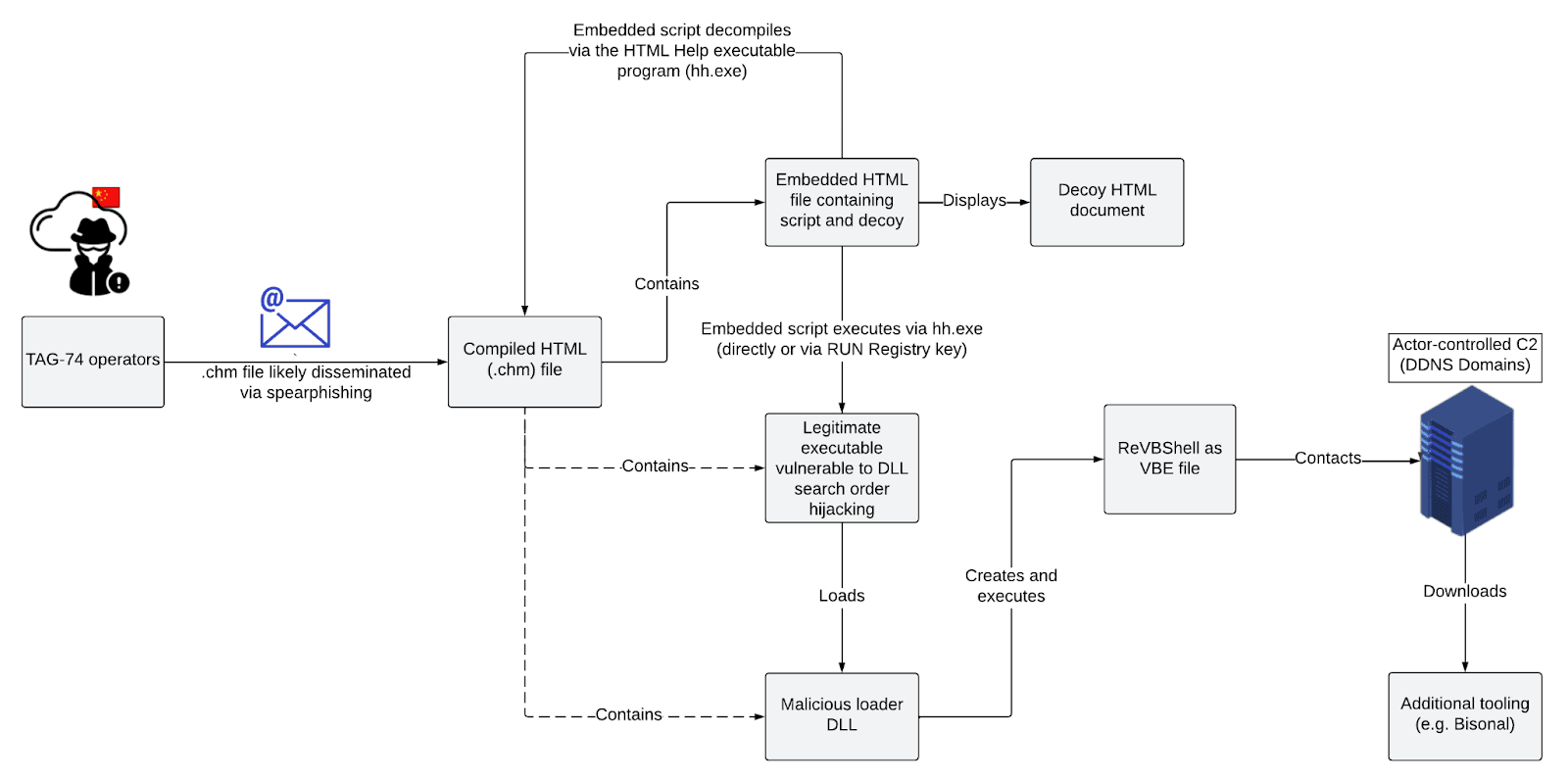 Typical infection chain observed in TAG-74 campaign targeting South Korea (Source: Recorded Future)
Typical infection chain observed in TAG-74 campaign targeting South Korea (Source: Recorded Future)
TAG-74 is a well-established Chinese state-sponsored threat activity group specializing in intelligence collection against South Korean, Japanese, and Russian organizations. Their tactics, techniques, and procedures (TTPs) include the use of .chm files that trigger a DLL search order hijacking execution chain to load a customized version of the VBScript backdoor ReVBShell. Additionally, a custom backdoor known as Bisonal is used to enhance capabilities once initial access through ReVBShell is established. This customized ReVBShell variant is likely shared between TAG-74 and another closely related threat activity group, Tick Group, indicating collaboration between these groups.
The persistence of TAG-74 in targeting South Korean organizations and its likely operational alignment with the Northern Theater Command suggests that the group will continue its active and long-term intelligence-gathering efforts in South Korea, Japan, and Russia. Notably, the use of .chm files by Chinese state-sponsored actors is not particularly common outside of South Korea. However, the use of this attack vector in activity targeting South Korea has been seen both in TAG-74 campaigns and, more widely, in activity attributed to North Korean state-sponsored threat activity groups such as Kimsuky and APT37. Organizations should monitor for the presence and use of .chm files, particularly if they are not commonly used within their environment, as this tactic has gained prevalence among threat actors in recent years.
To read the entire analysis, click here.
Article Link: Multi-year Chinese APT Campaign Targets South Korean Academic, Government, and Political Entities | Recorded Future