Monthly Threat Actor Group Intelligence Report, September 2023 (ENG)
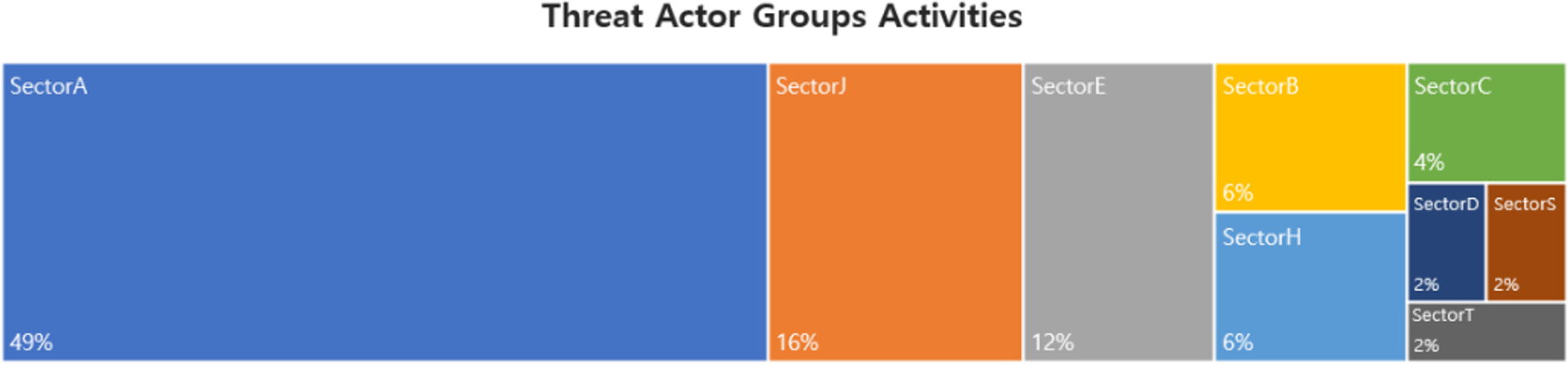
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 August 2023 to 20 September 2023. In September, activities by a total of 26 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 49%, followed by SectorJ and SectorE groups.
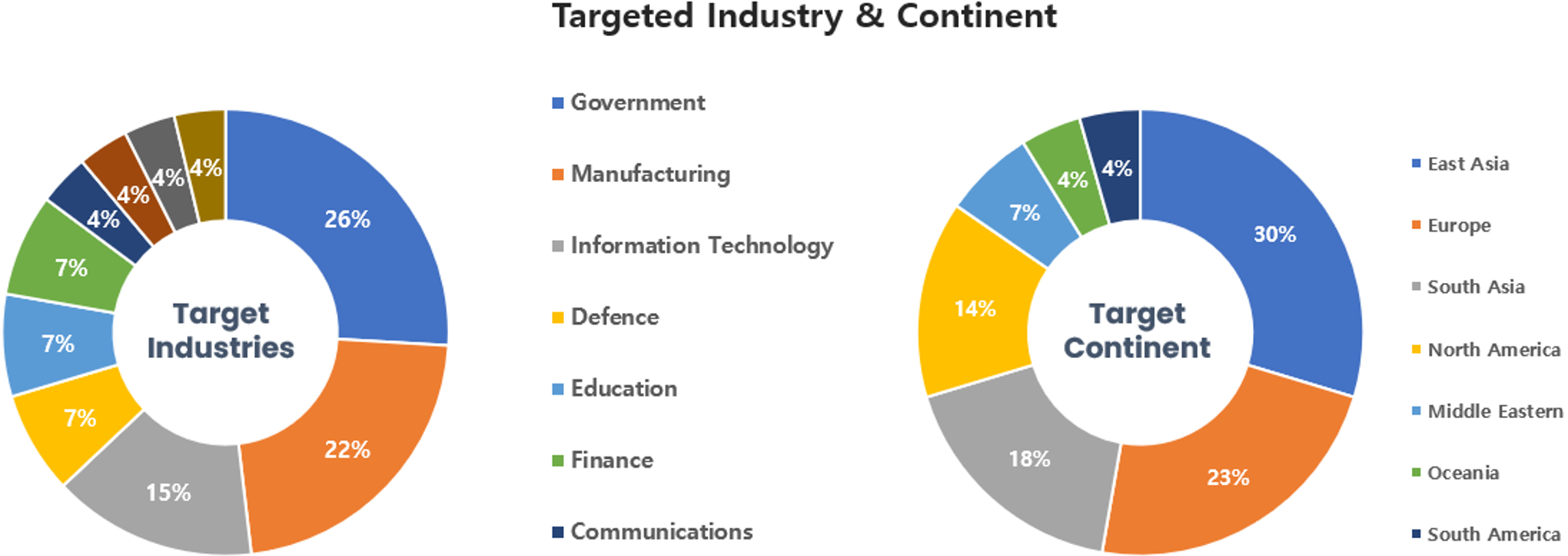
Threat Actors identified in April carried out the highest number of attacks on workers and systems in government agencies and manufacturing sectors. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In September 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA02, SectorA04, SectorA05, SectorA06 and SectorA07 groups.
SectorA02 group was found to be active in South Korea, the United States, China, and Romania. The group used malicious code in the form of Windows Help (CHM, Compiled HTML Help) files disguised as financial topics such as credit cards, securities, and insurance fees, and ultimately downloaded and executed additional malware through PowerShell commands.
SectorA04 group was found to be active in South Korea and Poland. The group conducted cyberattacks targeting the education industry including universities and the manufacturing industry, and used malicious code disguised as Microsoft Internet Explorer web browser.
SectorA05 group was found to be active in South Korea, Malaysia, Netherlands and Qatar. The group used a malicious code in the form of a Windows shortcut (LNK) disguised as a kidnapping-related news article and ran bait news article web pages to deceive the attack target.
SectorA06 group was found to be active in the United States, Malaysia and South Korea. When the target of the attack executed the malicious code, additional malicious code was downloaded and executed to collect information and perform malicious behavior according to the attacker’s commands.
SectorA07 group was found to be active in South Korea and Hong Kong. The group used malicious code in the form of a Windows shortcut (LNK) disguised as a consolidated income tax return, and ultimately used Visual Basic Script to collect system information, as well as batch (Batch) script files.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In September 2023, activities by a total of 3 hacking groups were identified, and the groups was SectorB01, SectorB21, and SectorB78.
SectorB01 was found to be active in India. The group distributed malicious code and keyloggers targeting important infrastructure facilities and performed attack activities according to commands received from C2 server on the target systems.
SectorB21 was found to be active in Spain, Ukraine, Yemen, the Democratic Republic of the Congo, Australia, Brazil, Denmark, Germany, Hong Kong, Hungary, Lithuania, the Netherlands, Poland, Portugal, Singapore, and the United States. The group distributed Android malware disguised as Signal and Telegram apps to carry out attack activities, and stole sensitive information such as call logs, contact lists, Google account lists, and device locations according to the commands of the C2 servers on the targeted devices.
SectorB78 was found to be active in Hong Kong, Nepal, India, Taiwan, and South Korea. The group distributed Spear Phishing emails containing discussions on maritime-related issues between Taiwan and the US targeting government institutions and performed attack activities. According to the commands received from the C2 server, various commands were executed on the targeted systems.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In September 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorC01 and SectorC13.
SectorC01 was found to be active in Austria, Poland, and Belgium. This group used malicious code in the form of Windows shortcuts (LNK) that can only be accessed by service subscribers and attempted to steal hash values used in NTLMv2 (NT LAN Manager) authentication protocol with a Geo-fencing strategy.
SectorC13 was found to be active in Russia. The group used a MS Word malicious code disguised as a resume, and when the target of the attack executed the MS Word malicious code, malicious code-containing MS Word (Word) template was downloaded and executed through the Template Injection technique.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In September 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorD01.
SectorD01 was found to be active in Israel and Australia. This group used a MS Word (Word) malware disguised as marketing service promotional materials, and the malware ultimately executed would collect the username, computer name, and local domain name and perform various functions according to the attacker server command.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In September 2023, activities by a total of 4 hacking groups were identified, and the groups was SectorE01, SectorE02, SectorE03, and SectorE05.
SectorE01 was found to be active in China, Taiwan, Japan, and Malaysia. The group distributed disguised Windows shortcut files (LNK) through investment documents and conducted attack activities. They downloaded malicious codes from the attack system and executed them to prepare a foothold for future attacks.
SectorE02 was found to be active in China, South Korea, the United States, Pakistan, Taiwan, Ecuador, Germany and Malaysia. The group distributed spear phishing emails as a target for IT and manufacturing, and ultimately installed a remote control malware known as Agent Tesla to steal sensitive information such as credentials, keylogging information, and screenshots from the target system according to the commands received from the C2 server.
SectorE03 was found to be active in India. The group disguised itself as Google Update and deployed Android malware to launch attacks, and it stole sensitive information such as call records, SMS messages, camera recordings, recordings, and screenshots from the targeted devices according to the commands of the C2 server.
SectorE05 was found to be active in China. The group disguised itself as an invitation to attend Reporting Guidelines and Cryptocurrency recognition seminars, and distributed a Windows Help file (CHM) to carry out attack activities, and downloaded additional malware to run on the target system to prepare for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In September 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 was found to be active in Austria, Australia, India, Netherlands, and Canada. The group distributed ZIP archives containing malicious Windows shortcuts (LNK) for attacking, and the finally installed malware collected system information including the computer name, OS version, and anti-virus information to prepare for future attacks.
The group also distributed malicious code and Penetration Testing tools targeting Windows and Linux operating systems to conduct attack activities, and performed various commands according to commands received from C2 servers, such as file download and upload, and execution. In addition, the group distributed Android malware through the YouTube app to carry out attack activities, and stolen sensitive information such as call records, contact lists, camera recordings, and recordings according to the commands of the C2 server from the target terminal.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorS Group Activities
In September 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorS01.
SectorS01 was found to be active in Bulgaria, the United States, Japan, and Taiwan. The group carried out attack activities by distributing malicious MS Excel documents through Spear Phishing emails targeting the manufacturing industry, and ultimately installed the remote-control malicious code known as Agent Tesla on the targeted system to steal sensitive information such as credentials, keylogging information, and screenshots.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
8. Characteristics of SectorT Group Activities
In September 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorT01.
SectorT01 was found to be active in Ukraine, Austria, and Thailand. The group used malware disguised as defense strategy documents, exploiting a vulnerability (CVE-2023-38831) in the compression software WinRAR. Subsequently, they attempted malicious acts in accordance with the attacker’s commands by using the remote-control tool Cobalt Strike to download additional malware.
SectorT hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of Cyber Crime Group Activities
In September 2023, activities by a total of 7 hacking groups were identified, and the groups were SectorJ25, SectorJ37, SectorJ39, SectorJ49, SectorJ73, SectorJ121, and SectorJ124.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ25 was found to be active in Mongolia, the United Kingdom and Indonesia. The group used Cryptojacker, which mines Cryptocurrency in Cloud and Container environment, and the Bash malware used by this group collects system information and changes system settings for Cryptocurrency mining.
SectorJ37 was found to be active in Spain, Brazil, France, Morocco, Slovakia, Estonia, Italy, the United Kingdom, Germany, the United States, the Netherlands, Canada, and the Arab Emirates. The group used malicious code disguised as an OTT (Over The Top) service program based on a Set-Top Box, and induced the target of attack to execute MS Word malware.
SectorJ39 was found to be active in the United States, Canada, India, Iran, Israel, the United Kingdom, Azerbaijan, Italy, and Sweden. The group exploited a Windows search file remote code execution vulnerability (CVE-2023-36884) targeting businesses in Europe and North America, and used topics related to Ukraine and NATO to induce the targets to run malicious code.
SectorJ49 was found to be active in Estonia, Russia, and India. The group distributed compressed files containing PE file format malicious code disguised as military conscription orders via phishing mail, and ultimately attempted to install malicious code with remote control capabilities to collect system information, commands, and control systems.
SectorJ73 was found to be active in Colombia. The group used Rhysida Ransomware to target government, IT and manufacturing industries for financial gain.
SectorJ121 was found to be active in Poland and Ukraine. The group utilized a zipped file containing a batch script disguised as a government agency document, and eventually used remote control malware that performed various functions according to the attacker’s server commands.
SectorJ124 was found to be active in Netherlands, Israel, Ukraine, the United States, and India. The group used the Python Package Index (PyPl) to distribute malware to steal cryptocurrency wallet related data and used Telegram channels or file sharing services to avoid detection.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact [email protected].
Article Link: Monthly Threat Actor Group Intelligence Report, September 2023 (ENG) – Red Alert