Monthly Threat Actor Group Intelligence Report, May 2023 (ENG)
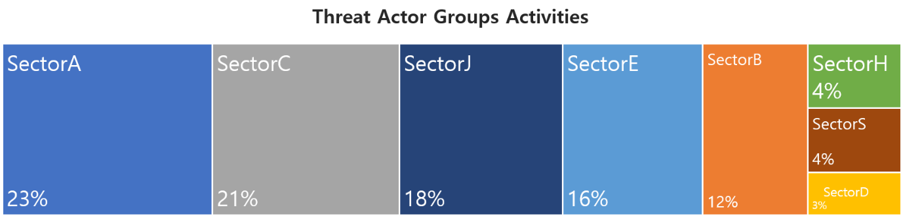
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 April 2023 to 20 May 2023. In May, activities by a total of 34 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 23%, followed by SectorC groups.
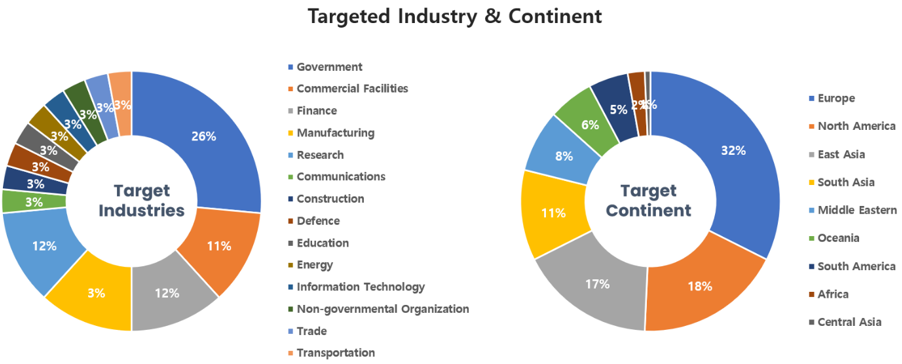
Threat Actors identified in May carried out the highest number of attacks on workers and systems in government agencies and commercial sectors. Regionally, Europe and North America were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
Among the SectorA hacking groups receiving support from the North Korean government, activities by a total of 5 hacking groups were identified in May. The groups were SectorA01, SectorA02, SectorA04, SectorA05 and SectorA06 groups.
SectorA01 group was found to be active in the United States. The group targeted on Windows IIS web servers of vulnerable versions to distribute malware with downloader functions, which could download and execute additional malware.
SectorA02 group was found to be active in South Korea, Australia, Hong Kong, the United States, and India. The group used compressed files containing malware in the form of Windows shortcut (LNK) files. These compressed files were disguised with various topics, including seminars by the Korean Public Administration Society and the North Korean economic crisis, to deceive the targets into executing the malicious code.
SectorA04 group was found to be active in the United States, Germany, and the United Kingdom. The group used malware disguised as Microsoft Defender to carry out their activities.
SectorA05 group was found to be active in South Korea, the United States, Japan, and Italy. The group utilized malware disguised as purchase payment invoices in the form of CHM (Compiled HTML Help) files. This malware had the function of downloading and executing HTA(HTML Application) malware through an internal script.
SectorA06 group was found to be active in Canada. Argentina, Italy, Turkey, United Arab Emirates, Germany, Spain, the United Kingdom, the United States, Japan, and Russia. The group impersonated a Venture Capital company and targeted on users of macOS to distribute malware disguised as a PDF viewer. In the final stage, the malware collected system information and transmitted it to a C2 server, and the group utilized a malware written in the Rust programming language, which had additional command execution capabilities.
SectorA hacking groups continue to carry the aim of collecting advanced information on political and diplomatic activities of the South Korean government, and at the same time launching hacking activities worldwide to secure financial resources. Hacking activities with these purposes have continued over a long period of time and is expected to continue without change for the time being.
2. Characteristics of SectorB Group Activities
Among the SectorB hacking groups receiving support from the Chinese government, activities by a total of 5 hacking groups were identified in May, and the groups were SectorB01, SectorB04, SectorB22, SectorB42 and SectorB53.
SectorB01 group was found to be active in Australia, France, and Hong Kong. The group distributed ZIP compressed files containing Windows shortcut (LNK) format malware as part of their attack campaign. Ultimately, they infiltrated the target systems and installed Cobalt Strike, a penetration testing tool, to carry out information exfiltration activities.
SectorB04 group was found to be active in Japan. The group conducted their attack activities targeting hotels and hospitality businesses in Japan. They distributed MS Word documents disguised as content related to the impact of the Russia-Ukraine war on Japan. These documents contained a downloader function that installed malicious code, laying the groundwork for future attacks.
SectorB22 group was found to be active in the United Kingdom, Vietnam, Ukraine, Australia, Myanmar, Thailand, Slovakia, Hungary, and Israel. The group conducted their attack activities by distributing HTML files containing malicious ZIP archives. Ultimately, they installed a remote access Trojan (RAT) known as PlugX on the targeted systems, enabling them to carry out information theft.
SectorB42 group was found to be active in Hong Kong, South Korea, and Lithuania. The group targeted on government and financial institutions and conducted their attack activities by distributing various backdoors, ultimately engaging in information theft.
SectorB53 group was found to be active in Taiwan. The group targeted government agencies, education, logistics, and telecommunications sectors by distributing malware with reverse shell configuration capabilities, engaging in their attack activities.
SectorB hacking groups continue to carry the aim of collecting advanced information on worldwide governmental activities such as political and diplomatic activities.
3. Characteristics of SectorC Group Activities
Among the SectorC hacking groups receiving support from the Russian government, activities by a total of 4 groups were identified in May, and the groups were SectorC01, SectorC04, SectorC08 and SectorC13.
SectorC01 group was found to be active in Ukraine, Israel, Canada, and Austria. The group utilized phishing sites disguised as portal sites providing news, media, and search engine services with the objective of stealing account information.
SectorC04 group was found to be active in the Dominican Republic. The group utilized compressed files containing DLL-format malicious code and Windows shortcut (LNK) files. They disguised the files as documentation to trick the victims into executing the Windows shortcut (LNK) files, which, upon execution, would run the malicious code in the form of DLL files located in the same path.
SectorC08 group was found to be active in Australia, Ukraine, the United States, Slovenian and Romania. The group utilized compressed files disguised as criminal lawsuit legal documents and attempted to download additional malicious files through Microsoft HTML Application (MSHTA), which allows the execution of HTA (HTML Application) files.
SectorC13 group was found to be active in Russia. The group employed MS Word (Word) malicious code disguised as instructions for evacuation in the event of an attack. If the target executes the MS Word (Word) malicious code, it downloads and executes an MS Word (Word) template containing malicious code through the technique of template injection.
SectorC hacking groups continue to carry the aim of collecting advanced information on Russia and its adjacent countries, and worldwide governmental activities such as political and diplomatic activities.
4. Characteristics of SectorD Group Activities
Among the SectorD hacking groups receiving support from the Iranian government, activities by a total of 2 hacking groups were identified in May, and the groups were SectorD05 and SectorD36.
SectorD05 group was found to be active in Austria, Spain, and Israel. The group utilized ASPX (Active Server Pages Extended) web shells, which are files in the form of web shells with upload, download, and command execution capabilities, to target vulnerable servers.
SectorD36 group was found to be active in Israel. The group distributed compressed files disguised as Iraq-related topics to their targets. They employed malicious code that disguised itself as a folder by changing its icon to match the folder icon, enticing the victim to open it. Ultimately, they utilized PowerShell scripts in the form of malicious code, which possessed various functionalities such as system information gathering and command control.
SectorD hacking groups usually carry out hacking activities on countries under diplomatic dispute with the Iranian government, and their recent purpose in hacking is seen to be to collect advanced political and diplomatic activity information of individuals and countries against the Iranian government.
5. Characteristics of SectorE Group Activities
Among the SectorE hacking groups receiving support from the Indian government, activities by a total of 5 hacking groups were identified this May, and the groups were SectorE01, SectorE02, SectorE04, SectorE05 and SectorE06.
SectorE01 group was found to be active in Singapore, Romanian, Canada, and Japan.
The group deployed malicious code disguised as overseas vessel deployment plans to carry out their attack. Ultimately, they installed a botnet malware known as Amadey, which was used to exfiltrate information.
SectorE02 group was found to be active in Nepal, Israel, Australia, the United States, the United Kingdom, Pakistan, Austria, Turkey, and Sri Lanka. The group distributed malicious code disguised as a cybersecurity advisory document in Adobe PDF format to carry out their attack. Ultimately, they installed malware to exfiltrate information.
SectorE04 group was found to be active in Sri Lanka, Pakistan, and Turkey. The group targeted government institutions in South Asia by distributing MS Word documents as part of their attack campaign. Ultimately, they installed malware to establish a foothold for future attacks.
SectorE06 group was found to be active in the United Kingdom, India, Pakistan, and Netherlands.
The group distributed malicious Android code disguised as a secure chat application to carry out their attack activities. They engaged in activities to steal sensitive information such as call logs, contacts, SMS messages, and location data.
SectorE hacking groups continue to carry the aim of collecting advanced information on Pakistan governmental activities such as political and diplomatic activities. However, considering that they have been expanding their attacks to East Asian countries such as China and other regions, the proportion of activities carried out with the purpose of collecting political, diplomatic, and technical information are seen to have increased.
6. Characteristics of SectorH Group Activities
Among the SectorH hacking groups receiving support from the Pakistani government, activities by a total of 1 hacking group was identified this May, and the group was SectorH03.
SectorH03 group was found to be active in India, the United States and Japan. The group distributed a ZIP compressed file disguised as “Saudi Delegation” and conducted attack activities to steal information.
SectorH hacking group carries out cybercrime hacking and hacking activities for governmental support at the same time. Due to the continued diplomatic dispute with the neighboring country India, they are analyzed to continue their attacks on the Indian government to collect advanced military and political information in the future as well.
7. Characteristics of SectorS Group Activities
Among the SectorS groups receiving support from the Venezuelan government, activities by a total of 1 hacking group was identified in May. The group was SectorS01.
SectorS01 group was found to be active in Germany, Ukraine, the United States, Czech Republic, Chile, the United Kingdom, Netherlands, Romanian, Columbia, and Mexico. The group conducted attack activities by distributing spear phishing emails to manufacturing and IT companies, aiming to steal information.
SectorS hacking groups continue to carry the aim of collecting advanced information on activities of governments bordering Venezuela and in the South American region, such as political, diplomatic, and military activities.
8. Characteristics of Cyber Crime Group Activities
Among the cybercrime groups found to be active in online spaces, activities by a total of 11 hacking groups were identified in April. The groups were SectorJ04, SectorJ05, SectorJ06, SectorJ09, SectorJ64, SectorJ72, SectorJ74, SectorJ110, SectorJ111, SectorJ112 and SectorJ113.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ04 group was found to be active in the United States, India, Spain, Romanian and Taiwan. The group targeted systems exposed to the PaPerCut vulnerabilities (CVE-2023-27350, CVE-2023-27351) to steal data or distribute ransomware.
SectorJ05 group was found to be active in Malaysia, Sweden. Turkey and the United States. The malicious code used by the group has the capability to download and execute additional
malware, indicating the potential for stealing sensitive information or attempting ransomware attacks in the future.
SectorJ06 group was found to be active in Russia. The group utilized the Gazprom Ransomware to secure financial gains and employed a ransom note containing a text graphic reminiscent of Russian President Vladimir Putin.
SectorJ09 group maintains the traditional hacking method by inserting obfuscated skimming scripts into websites. These scripts collect user information such as usernames, addresses, email addresses, phone numbers, and credit card payment details on payment pages.
SectorJ64 group was found to be active in the United States and India. The SectorJ09 group attempted cryptocurrency mining on servers exposed to the Oracle WebLogic Server vulnerability (CVE-2017-3506).
SectorJ72 group was found to be active in Netherlands, Hong Kong. Indonesia, Canada, Mexico, Armenia, Servia, Hungary, Bolivia, Spain, Tunisia, Ecuador, Malaysia, Italy, Poland, Croatia, Bulgaria, Lithuania, Argentina, and the United States. The group is propagating malware through removable media, and if the target executes the malicious Windows shortcut (LNK) files present on the infected removable media, additional malware is downloaded and executed.
SectorJ74 group was found to be active in Italy, Ireland, Germany, the United States and Finland. The SectorJ09 group used spear phishing emails disguised as reservation details, attaching MS Word (Word) malicious code using the template injection technique to lure the target into executing it. Ultimately, they attempted to collect system information and gain control by using malware with remote control capabilities.
SectorJ110 group was found to be active in Russia, the United States, Spain, and Ukraine. The SectorJ09 group distributed phishing emails by attaching compressed files containing malicious JavaScript files disguised as invoices. Ultimately, they used malware with the ability to download and execute additional malicious code.
SectorJ111 group was found to be active in Saudi Arabia, the United States, Iran, Mexico, Czech Republic, Serbia, Hungary, Bangladesh, Sweden, South Korea, Finland, Vietnam, Canada, India, Chile, Romanian, Algeria, the United Kingdom, Venezuela, Italy, Kenya, Germany, Brazil, Austria, Philippines, Singapore, Qatar, France, Spain, Thailand, Japan, Palestine, Hong Kong, and China. The group distributed malware with the ability to download and execute additional malicious code through a phishing site disguised as a free software provider. If the target executes the malware, they are redirected to a phishing site impersonating Microsoft, where they are prompted to enter their credit card information.
SectorJ112 group was found to be active in the United States, Mexico, Indonesia, Thailand, Russia, North Africa, India, Angola, Philippines, Argentina, and Taiwan. The group utilized Android malware to acquire data for big data utilization and generate revenue through ad execution. They also compromised sensitive information with the intention of selling it to other hacking groups.
SectorJ113 group was found to be active in Dominican Republic, the United Kingdom, Saint Lucia, Israel, Canada, Bosnia Herzegovina, Barbados, Italy, Peru, Netherlands, Belarus, Singapore, Turkey, Costa Rica, Uzbekistan, Venezuela, Taiwan, India, Hong Kong, Egypt, Latvia, France, South Korea, Germany, China, Bahrain, Russia, and the United States. The group employed the use of Babuk Ransomware to secure financial gain. They utilized a double-extortion attack by threatening to disclose the stolen data to increase the likelihood of the victims paying the ransom.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact [email protected].
Article Link: Monthly Threat Actor Group Intelligence Report, May 2023 (ENG) – Red Alert