Monthly Threat Actor Group Intelligence Report, December 2023 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 November 2023 to 20 December 2023.
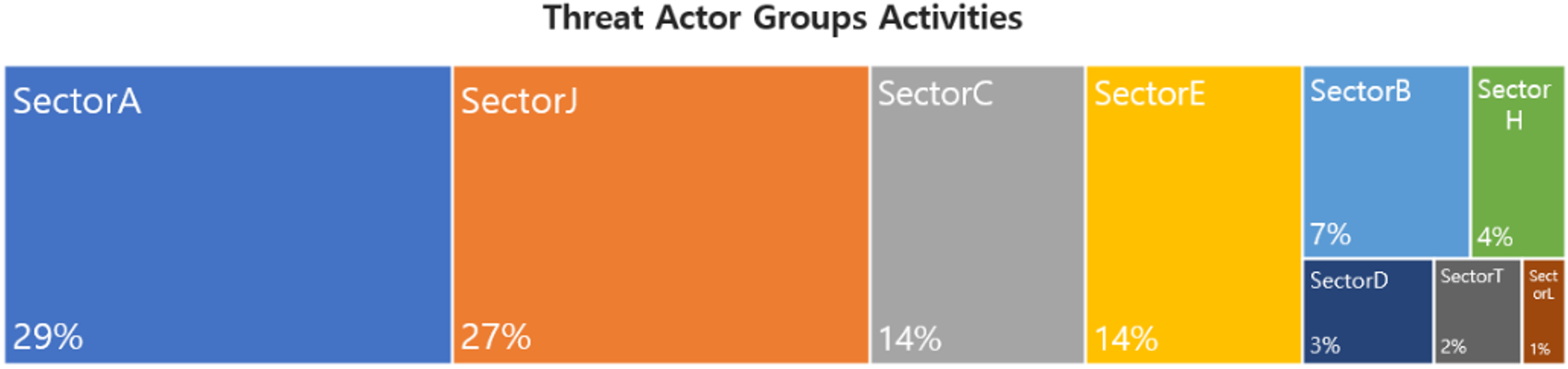
In December, activities by a total of 36 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 29%, followed by SectorJ and SectorC groups.
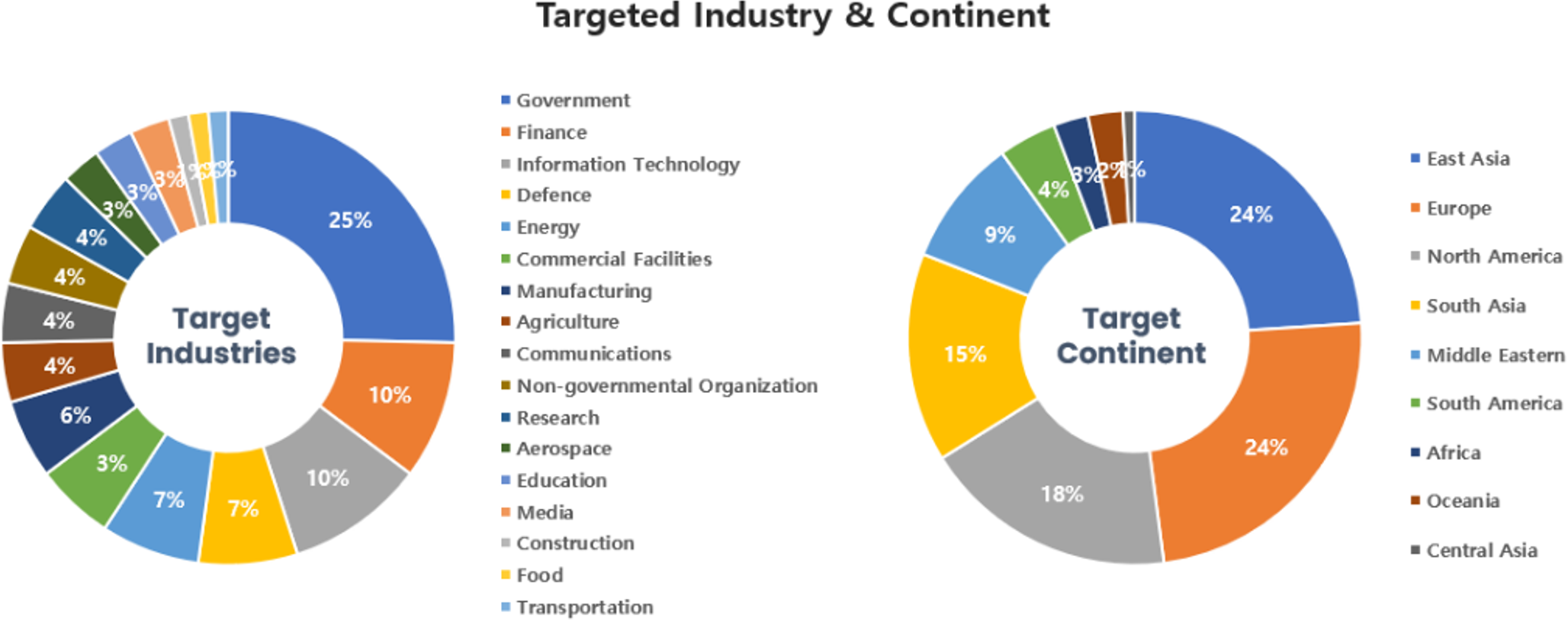
Threat Actors identified in December carried out the highest number of attacks on workers and systems in government agencies and commercial sectors. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In December 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, and SectorA07.
SectorA01 group was found to be active in the United Kingdom, Sweden, Belarus, Brazil, Japan, Taiwan, Canada, the United States, Singapore, the Netherlands, Colombia, Pakistan, Romania, Italy, Spain, Bulgaria, Morocco, Turkey, the Philippines, Ukraine, Vietnam, Cyprus, Chile, and South Korea. The group disguised themselves as hiring managers, targeting software developers who were actively seeking employment and lured them into a fake interview process, ultimately installing malware disguised as programs.
SectorA02 group was found to be active in Hong Kong, Italy, Uzbekistan, Japan, and South Korea. The group used malware in the form of window shortcuts (LNKs) disguised as documents requesting the submission of clarification data on the source of unreported funds, and finally used Visual Basic Script and Batch script files to collect system information.
SectorA05 group was found to be active in South Korea. The group used malicious JavaScript disguised as a test and research organism import declaration document for Korean research institutes, and malware in the final DLL format collects and transmitted system information and performed commands received from the C2 server.
SectorA06 group was found to be active in Luxembourg, Vietnam, China, Sweden, and the United States. The group used malicious Python scripts disguised as tools used in cryptocurrency transactions for macOS users and distributed them through the public channel of Discord, a Voice over Internet Protocol (VoIP) application software.
SectorA07 group was found to be active in the United States, South Korea, Thailand, and Hong Kong. The group used malware in the form of Windows Shortcut (LNK) disguised as an email account security check guide, and when the target ran the malware, the system information of the target was finally sent to the C2 server through the Obfuscated Visual Basic Script.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In December 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorB01, SectorB22, SectorB72, SectorB73, and SectorB85.
SectorB01 group was found to be active in Hong Kong and the United States. The group attempted initial access by exploiting Adobe ColdFusion’s arbitrary code execution vulnerability (CVE-2023-26360) on a government agency system and then distributed malware to engage in attack activities. Information for future attacks was collected by stealing existing process information, network connection status, local and domain administrator account information, network configuration, and user information through malware distributed to the target system.
SectorB22 group was found to be active in Taiwan. The group distributed malicious Windows installer (MSI) files to the Taiwanese government personals and diplomats and conducted various malicious activities such as system information collection, keylogging, and screen capture according to commands received from the C2 server through a remote-controlled malware known as PlugX distributed to the target system.
SectorB72 group was found to be active in France, China, Thailand, Egypt, Afghanistan, Australia, and Romania. The group distributed various malwares to organizations such as governments, education, retail, non-profit organizations, and telecommunications companies in the Middle East, Africa, and the United States. The group collected user credentials through various malwares distributed to the target system and executed commands, uploaded, and downloaded files according to commands received from the C2 server through malwares of the backdoor function.
SectorB73 group was found to be active in Guam, the United States, Ukraine, and South Korea. The group distributed malware to various router and firewall products used in government and energy organizations and engaged in attack activities.
SectorB85 group distributed malware written in the Lua programming language and engaged in attack activities, and the malware distributed to the target system used a cloud-based reverse proxy infrastructure as a C2 server. The group collected system and user information through malware distributed to the target system and transmitted it to the C2 server, and various malicious actions were performed according to the commands received from the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In December 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC08, SectorC13, and SectorC14.
SectorC01 group was found to be active in Japan, Turkey, the Netherlands, Indonesia, India, the United States, the United Arab Emirates, Ukraine, Slovakia, Romania, Poland, Luxembourg, Lithuania, Jordan, Italy, Bulgaria, Czech Republic, Australia, France, and Latvia. The group used MS Word bait documents using topics related to the Israel-Hamas War to induce the target to execute malware and attempted to download and execute additional malware using malicious DLL file execution and batch script malware using the DLL Side-Loading technique.
SectorC04 group was found to be active in the Philippines, Denmark, Poland, the United States, Canada, Thailand, the United Kingdom, India, South Africa, China, and Australia. The group used malware in the form of window shortcuts (LNK) files disguised as Adobe PDF documents related to vehicle sales prices, and eventually used Cobalt Strike, a penetration testing tool.
SectorC08 group was found to be active in the United States, Vietnam, Chile, Poland, Germany, Hong Kong, and Ukraine. The group used a malware in the form of Portable Executable (PE) disguised as an Adobe PDF document with award-related content in the national reward policy, and finally attempted to steal information using UltraVNC, a remote-control tool.
SectorC13 group was found to be active in Latvia and Russia. The group used MS Word malware disguised as documents on rail transportation, and when the target of the attack executed the MS Word malware, an MS Word template containing malware is downloaded and executed through a template injection technique.
SectorC14 group used various methods such as Server-Side Script and Domain Generation Algorithm (DGA) to hide their credential and infrastructure information stealing activities.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In December 2023, activities by a total of 2 hacking groups were identified, and the groups was SectorD02 and SectorD37.
SectorD02 group was found to be active in Egypt, Sudan, Tanzania, and the United Kingdom. The group used malware in the form of Portable Executable (PE) disguised as a Java-related file for telecommunication industry groups in African countries and executed malicious DLL files using a DLL side-loading technique.
SectorD37 group was found to be active in the United States, and Israel. The group carried out cyberattack activities targeting water and wastewater systems (WWS) industries connected to the external Internet with weak security settings.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In December 2023, activities by a total of 3 hacking groups were identified, and the groups was SectorE01, SectorE04, SectorE05.
SectorE01 group was found to be active in Afghanistan, Bangladesh, Norway, and Pakistan. The group distributed malware of the download function and performed attack activities, eventually installing malware of a remote-control function known as Remcos to perform various malicious actions according to commands received from the C2 server in the target system.
SectorE04 group was found to be active in Nepal, Germany, the Netherlands, and Pakistan. The group distributed MS Word documents disguised as travel itinerary documents and document containing negative press releases from foreign media companies, and transmitted data such as computer names and command prompt execution results to BASE64 through the malware installed on the target system and then transmitted to the C2 server.
SectorE05 group was found to be active in Sri Lanka, China, Nepal, Pakistan, and Singapore. The group distributed Windows Help (CHM) files disguised as Circular documents, operational data documents, and criminal record documents to conduct attacks. Through the malware distributed to the target system, the computer name and username were transmitted to the C2 server, and the malware was downloaded and executed to lay groundwork for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In December 2023, activities by a total of 2 hacking groups were identified, and the groups was SectorH01 and SectorH03.
SectorH01 group was found to be active in Italy. The group distributed malicious Adobe PDF documents disguised as Invoice, and through the code injection function, malware was distributed to the target system and inserted into memory for future attacks.
SectorH03 group was found to be active in India. The group distributed window shortcut (LNK) files disguised as retirement planning documents and engaged in attack activities and performed various malicious acts according to commands received from the C2 server. In addition, MS PowerPoint documents disguised as posting policy revision documents were distributed to perform further attack activities, with various malicious acts were performed according to commands received from the C2 server through malwares distributed to the target system.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorL Group Activities
In December 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorL03.
SectorL03 group was found to be active in China, Ukraine, Greece, the United States, and Italy. The group distributed reverse TCP Shell malware after initial access to various organizations such as NGOs, information technology (IT) and communication, and performed various malicious actions according to commands received from the C2 server.
Hacking activities of SectorL hacking groups that continue to date are seen to be aiming to collect advanced information regarding governmental activities such as political, diplomatic, military activities in nearby countries. However, considering that they have expanded their targets to other areas recently, the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology are analyzed to have been increased.
8. Characteristics of Cyber Crime Group Activities
In December 2023, activities by a total of 13 hacking groups were identified, and the groups were SectorJ03, SectorJ09, SectorJ10, SectorJ12, SectorJ25, SectorJ64, SectorJ85, SectorJ94, SectorJ110, SectorJ120, SectorJ131, SectorJ133, and SectorJ137.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ03 group was found to be active in Israel, Portugal, the United States, Palestine, and Spain. The group used bait MS Excel documents about political theme about Palestine and induced the target to execute malware in the form of Portable Executable (PE) with various functions such as sending screenshots, downloading, and executing additional malwares.
SectorJ09 group maintains the existing hacking method of collecting usernames, addresses, mails, phone numbers, and credit card payment information from the payment page by inserting obfuscated skimming scripts on the website.
SectorJ10 group used White Rabbit Ransomware to encrypt and paralyze the Active Directory Controller and VMware ESXi for monetary profit, leaving a Ransom Note to communicate to the target of the attack.
SectorJ12 group was found to be active in Malaysia, the United States, and Italy. The group used phishing mail disguised as invoice emails from Germany’s an international transportation business Deutsche Post AG DHL Group and used Message Queuing Telemetry Transport (MQTT), a lightweight Internet of Things (IoT) messaging protocol to hide the actual address of a C2 server.
SectorJ25 group was found to be active in the United States, China, Singapore, South Korea, and Poland. The group used Cryptojacker to mine cryptocurrencies for cloud and container environments, and the Bash malware used collected system information and changed system settings for cryptocurrency mining.
SectorJ64 group was also found to be active in Peru, Israel, China, the United States, and South Korea. The group distributed malware to vulnerable servers using Remote Code Execution vulnerabilities, and finally used Cryptojacking malware for financial gain.
SectorJ85 group attempted a typosquatting attack by building a phishing site like a cryptocurrency-related domain.
SectorJ94 group was found to be active in France, Italy, Canada, China, and the United States. The group established a phishing website disguised as a remote-control program called AnyDesk, and distributed malware through malicious advertisements (Malvertising attack), inducing targets to download malware disguised as an installation program.
SectorJ110 group was found to be active in Ukraine, the United Arab Emirates, Russia, Iran, and Turkey. The group compressed and distributed the Visual Basic Script (VBS) malware disguised as an invoice document in MS Excel format attached in the phishing mail, and eventually used the malware with download and execution function.
SectorJ120 group was found to be active in Israel, Brazil, Canada, France, and India. The group distributed Python script malware through the official Python Packages Index (PyPI) storage, and eventually used Portable Executable (PE) malware that collects credentials and cryptocurrency-related information stored in the system.
SectorJ131 group was found to be active in Canada. The group deployed cryptocurrency mining scripts by exploiting vulnerabilities in Apache ActiveMQ (CVE-2023-46604).
SectorJ133 group was found to be active in the United Kingdom and the United States. The group distributed Visual Basic Script malware in the form of downloader through a malware advertisement, and finally used a backdoor type of Portable Executable (PE) malware.
SectorJ137 group established a phishing website in various fields such as web portals, mail services, and cryptocurrency exchanges for the purpose of inducing visitors and collecting their account information.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact [email protected].
Article Link: Monthly Threat Actor Group Intelligence Report, December 2023 (ENG) – Red Alert