Mastodon recently addressed two vulnerabilities, namely CVE-2023-42451 and CVE-2023-42452. In addition, a zero-day vulnerability, identified as CVE-2023-41179, was promptly resolved in TrendMicro’s Endpoint Security product, Apex One.
Critical Zero-Day in TrendMicro Apex One: CVE-2023-41179
The CVE-2023-41179 vulnerability carries a critical severity rating with a CVSS score of 9.1. Reports indicate that attackers have actively exploited the vulnerability to achieve remote code execution.
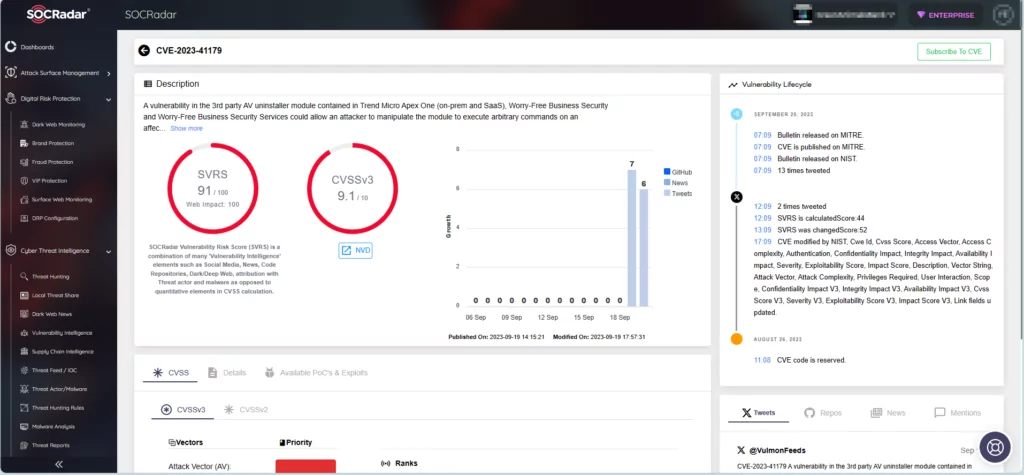 CVE-2023-41179 on SOCRadar Vulnerability Intelligence
CVE-2023-41179 on SOCRadar Vulnerability Intelligence
The CVE-2023-41179 vulnerability affects the following products::
- Trend Micro Apex One 2019
- Trend Micro Apex One SaaS 2019
- Worry-Free Business Security 10.0 SP1
- Worry-Free Business Security Services 10.0 SP1
CVE-2023-41179 resides in a third-party uninstaller module included with TrendMicro Apex One (both on-premises and SaaS). The Worry-Free Business Security and Worry-Free Business Security Services could allow an attacker to manipulate the module to achieve remote code execution.
An attacker must first gain administrative console access on the target system – either by stealing credentials or physically gaining access to a vulnerable machine – in order to exploit CVE-2023-41179.
If you are unable to apply the updates immediately, it is recommended that you restrict access to the administration console. You can prevent unauthorized access by whitelisting trusted networks.
For information on the available updates, refer to the official security bulletin for CVE-2023-41179.
Vulnerabilities in Mastodon: CVE-2023-42451, CVE-2023-42452
Mastodon is an open-source social network with independent servers/communities. The platform’s posts work similarly to Twitter (X), and it has earned recognition as the new Twitter within the security community.
Two significant vulnerabilities in Mastodon have recently been addressed, mitigating the risks of domain spoofing and XSS (Cross-Site Scripting) attacks. The vulnerabilities, CVE-2023-42451 and CVE-2023-42452, are detailed below:
CVE-2023-42451 (CVSS: 7.4, High Severity):
The vulnerability affects versions preceding 3.5.14, 4.0.10, 4.1.8, and 4.2.0-rc2 and allows attackers to exploit a domain name normalization issue under specific conditions. Exploiting the vulnerability, an attacker can spoof domains they do not own.
CVE-2023-42452 (CVSS: 6.1, Medium Severity):
The vulnerability affects 4.x branch versions before 4.0.10, 4.2.8, and 4.2.0-rc2 and allows attackers to abuse the translation feature. This enables them to circumvent server-side HTML sanitization, potentially allowing unescaped HTML execution in the browser. For successful exploitation, a user must click the “Translate” button on a malicious post.
The vulnerability description on NVD (National Vulnerability Database) states that the Content Security Policy (CSP) of Mastodon blocks inline scripts, thereby mitigating the impact. However, it is important to note that CSP cannot prevent DOM-based XSS attacks, and the particular vulnerability, CVE-2023-42452, is a DOM-based XSS issue.
You can update to version 4.1.8 to be safe from exploitation of CVE-2023-42451 and CVE-2023-42452. For more details on the updates, see the changelog on GitHub.
Get Instant Vulnerability Alerts with SOCRadar
SOCRadar continuously tracks the latest emerging security vulnerabilities. Subsequently, the platform is updated with essential details about the vulnerabilities, their mentions, available PoC exploits, lifecycle information, and specifically generated SOCRadar Vulnerability Risk Score (SVRS). You can access comprehensive information about the latest vulnerabilities by searching in the Vulnerability Intelligence tab within the Cyber Threat Intelligence module.
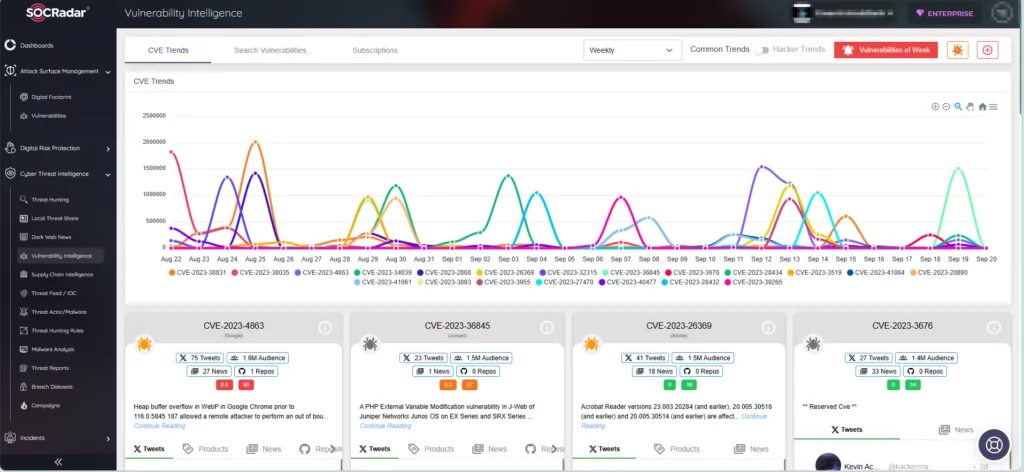 SOCRadar Vulnerability Intelligence
SOCRadar Vulnerability Intelligence
Additionally, SOCRadar, using the Attack Surface Management (ASM) module, monitors your organization’s digital footprint, tracks your assets, and sends alarms in case of emerging threats. In the ASM module, you can visit the Vulnerabilities tab to see which vulnerabilities have been identified among your assets and take proactive measures to prioritize and apply patches more effectively.
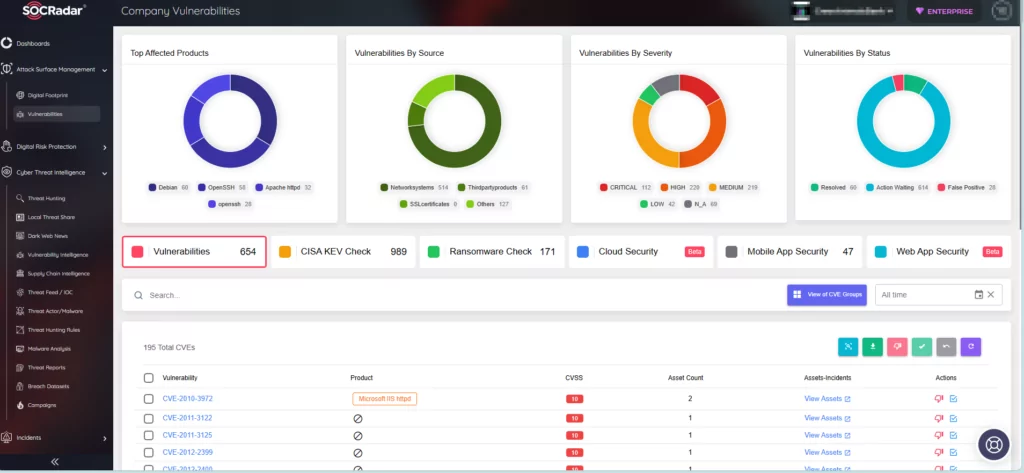 SOCRadar Company Vulnerabilities
SOCRadar Company Vulnerabilities
The post Mastodon Vulnerabilities and Critical Zero-Day in TrendMicro’s Apex One, Fixed: CVE-2023-41179, CVE-2023-42451, CVE-2023-42452 appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Mastodon Vulnerabilities and Critical Zero-Day in TrendMicro’s Apex One, Fixed: CVE-2023-41179, CVE-2023-42451, CVE-2023-42452
