Navigating the array of SOC automation tools and trends can be overwhelming, with new artificial intelligences technologies emerging at a rapid pace in 2024. This dynamic environment underscores the necessity for Security Operations Centers (SOCs) both understand and effectively implement AI-driven automation to triage alerts and incidents efficiently.
Let’s explore the current challenges, benefits, best practices, and key tools shaping SOC automation today — from autonomous SOC solutions, to new SOAR solutions, to AI co-pilots.
Current Challenges Driving New Strategies for SOC Automation
Cybersecurity Talent Shortages: There is a significant lack of skilled cybersecurity professionals, which hampers the ability of SOCs to manage and mitigate threats efficiently.
High Alert Volume: As the attack surface expands due to more devices and connections, SOCs face a higher volume of alerts, making it challenging to distinguish between false positives and genuine threats. This increases risk to organizations if their analysts are suffering from alert fatigue.
Challenges of Manual Monitoring and Response: Manual security processes are slow and prone to errors, making it difficult to respond effectively to incidents as they occur. (For example, think about the skills, time, and process required for traditional memory forensics using popular industry tools.)
Benefits of Enhancing Automation in Security Operations
Automation can enhance operational efficiency by streamlining threat detection and response, reducing the time and manual effort required. Maximizing automation also offers cost savings by minimizing the need for extensive personnel and reducing error-related expenses. Additionally, automation provides the scalability necessary to adapt to growing and changing security demands without significant additional resource investment.
Many security teams have automated some processes. But most of their alerts still require some kind of human intervention to triage and resolve. If a security team hasn’t fully implemented effective automation, they often have gaps that require them to rely more on outsourced SOC services for triage and response.
SOC Automation vs Outsourcing
Deciding between “fully” automating your SOC or outsourcing to a third-party provider like an MDR (Managed Detection and Response) service hinges on several key factors:
- Control and Customization: Automation within your SOC allows for greater control over security processes and tailored solutions specific to your organizational needs.
- Cost Implications: While initial setup for automation may be high, it can be more cost-effective in the long run compared to the recurring costs of outsourcing.
- Expertise and Resources: Outsourcing can provide access to top-tier expertise and advanced technologies without the in-house investment, which is beneficial for organizations lacking sufficient cybersecurity personnel or infrastructure.
- Security and Compliance: Keeping SOC operations in-house through automation ensures direct oversight and potentially tighter compliance with industry regulations, which can be more challenging to manage through a third-party provider.
Each option has its merits, and the right choice depends on the organization’s specific requirements, budget, and strategic goals. Some MDRs provide expert services, like strategic advice and planning for reducing risk, that go beyond 24/7 alert triage and management of SOC processes.
The Best Tools and Technologies for AI-Driven SOC Automation
Autonomous SOC
Autonomous SOC or AI-SOC platforms are the newest addition for SOC automation solutions, designed to mitigate the significant skill gaps in cybersecurity teams. These systems utilize artificial intelligence to mimic the decision-making and investigative skills of human analysts. Most Autonomous SOC products focus on the alert triage processes to automate Tier 1 or 2 tasks for different types of alerts (such as endpoint detections, reporting phishing emails, or SIEM alerts).
Autonomous SOCs can replace traditional managed services or automate basic internal team functions, allowing security professionals to focus more on critical threats by reducing repetitive tasks and alert fatigue. This not only boosts efficiency but also enhances the detailed analysis of security alerts, lowering overall risk.
Example vendors: Intezer, Dropzone, Radiant
Tip: When selecting an Autonomous SOC vendor, consider the maturity of the company. You’ll want to assess the accuracy of their escalations to build trust in their AI’s decision making and verify that their advertised capabilities reflect actual performance.
SOAR
SOAR (Security Orchestration, Automation, and Response) tools are integral to modern SOCs, primarily enhancing case management and automating responses. They excel in organizing and managing incident response activities, ensuring that each case is tracked systematically from detection to resolution. Additionally, SOAR tools allow teams to create and implement incident response playbooks that automate repetitive and straightforward tasks, improving response times and reducing the chance for human error.
New Autonomous SOC solutions have benefits that are distinct from SOAR tools, though they may complement and improve existing orchestration and automation workflows. Cybersecurity teams may choose to integrate these two types of automation products to leverage both AI decision-making along with their customized playbooks.
Example vendors: Tines, XSOAR, Splunk, Torq
Tip: Most SIEM or XDR tools contain a built-in playbook or workflow creation component, which can save you the need of purchasing an additional standalone SOAR tool. You may also want to verify or inquire about supported integrations for SOC automation.
AI Co-Pilots
AI Co-Pilots are new tools that promise to significantly enhance SOC operations by serving as AI analyst assistants, focusing particularly on complex security investigations. These tools utilize generative AI to interpret and manage vast amounts of data, providing context that aids in a deeper analysis of security incidents. While they do not fully automate the process of alert triage, their strength lies in supporting your analysts thorough investigations so security professionals can make informed decisions based on enhanced data insights.
Example vendors: Microsoft Security Co-Pilot, Crowdstrike Charlotte AI, SentinelOne Purple AI
Tip: Write an internal cheat sheet with examples of prompts for your team to use with the AI Co-Pilot. This will help fully leverage its capabilities, possibly uncovering new uses and tasks that were previously unrecognized.
Designing a Modern SOC Automation Strategy
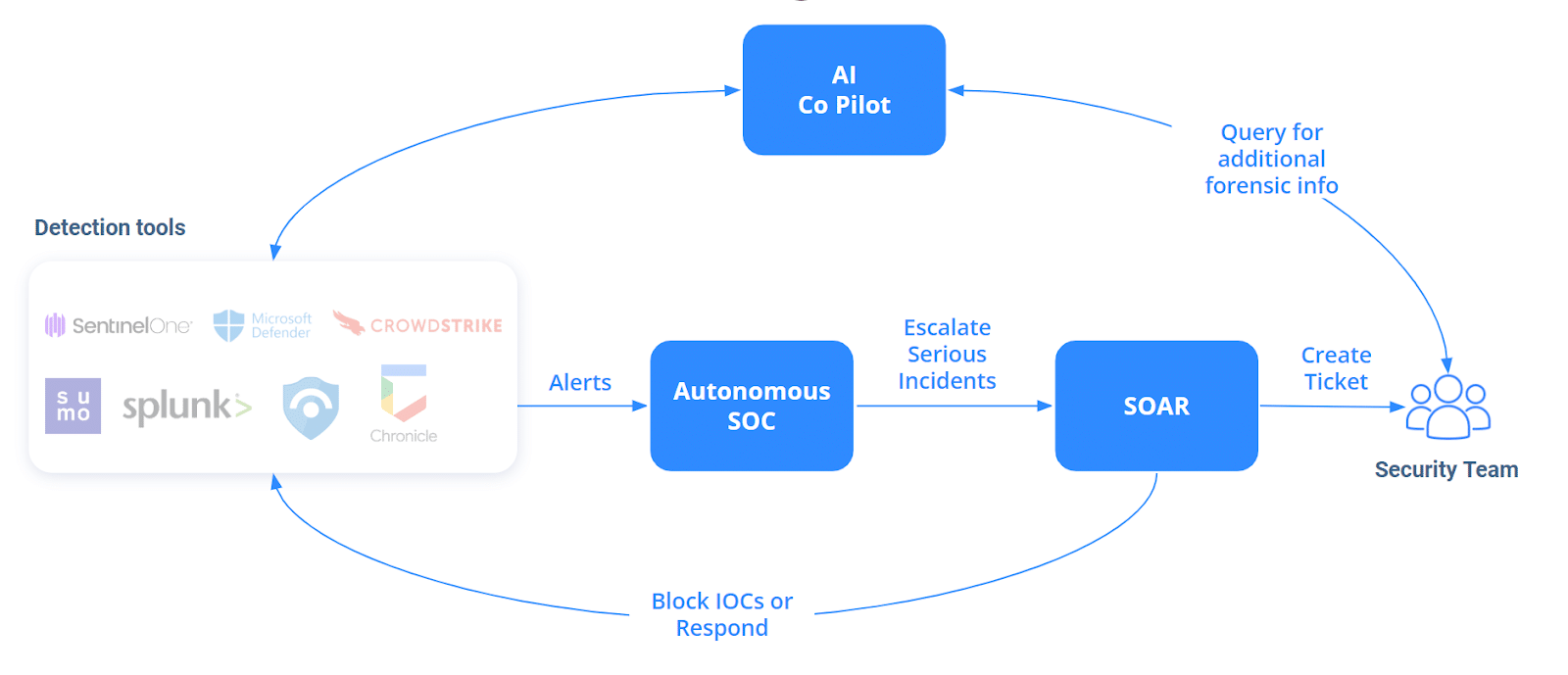 Illustration of enhanced SOC automation using AI-powered cybersecurity products.
Illustration of enhanced SOC automation using AI-powered cybersecurity products.
A well-rounded SOC automation strategy should leverage the strengths of specific tools for designated tasks:
- Automate Alert Triage: Use Autonomous SOC tools to sift through alerts, escalating only those that truly require human analysis. This helps effectively manage a high volume of alerts and drastically reduce time spent on false positives.
- Manage Cases and Automate Responses: Implement SOAR tools for case management and to automate responses based on input from Autonomous SOC tools. For example, automatically blocking a suspicious IP address that the Autonomous SOC identifies as a threat.
- Enhance Investigation of Escalated Alerts: Deploy AI Co-Pilots to assist analysts with further investigation of complex, escalated alerts. These tools can quickly provide detailed insights, such as specific network activities within a defined timeframe.
What should your security team focus on automating first? In deploying these tools, consider the specific needs of your SOC:
- If case management is a bottleneck, prioritize implementing SOAR.
- If alert volume is overwhelming, focus on integrating an Autonomous SOC.
- For enhancing detailed investigations, consider adding AI Co-Pilots.
The most effective strategy uses a layered approach with AI and automation tools, but should start with the most critical need allows for phased, manageable integration.
Best Practices for SOC Automation in 2024
SOC automation tools can sometimes be overwhelming, with a variety of AI features and options that challenge even the most experienced security teams. However understanding and deploying the right tools, such as Autonomous SOCs, SOAR platforms, and AI Co-Pilots, can profoundly transform your security operations. These solutions not only streamline processes, but also empower your team to prioritize and address critical threats more effectively.
Implementing the right mix of automation tools helps manage large volumes of alerts, automates routine tasks, and ensures that more complex threats undergo thorough investigation. This strategic approach enhances both efficiency and accuracy within your SOC.
You can learn more about how Intezer’s Autonomous SOC platform works and addresses the challenges of resource and talent scarcity in cybersecurity, helping you maximize your SOC’s performance without the need for constant human supervision.
Want to see it in action? Check out this interactive product tour or book a demo to learn more about our offerings to enhance your security posture with automation.
The post Mastering SOC Automation in 2024: Tips, Trends and Tools appeared first on Intezer.
Article Link: Mastering SOC Automation in 2024: Tips, Trends and Tools