We’re excited to share ANY.RUN‘s latest malware trends analysis for Q3 2024.
Our quarterly update provides insights into the most widely deployed malware families, types, and TTPs we saw during the last 3 months of the year.
Summary
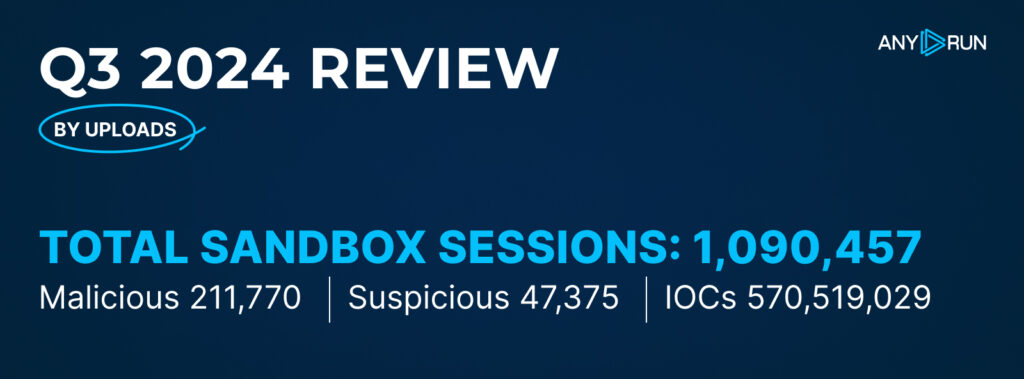 Users launched over 1M sandbox sessions in Q3 2024
Users launched over 1M sandbox sessions in Q3 2024In Q3 2024, ANY.RUN users ran 1,090,457 public interactive analysis sessions, which is a 23.7% increase from Q2 2024. Out of these, 211,770 (19.4%) were marked as malicious, and 47,375 (4.3%) as suspicious.
Compared to the previous quarter, the percentage of malicious sandbox sessions increased slightly from 18.4% in Q2 2024 to 19.4% in Q3 2024. The share of suspicious sessions saw a decline from 7.0% to 4.3%.
As for indicators of compromise, users collected a total of 570,519,029 IOCs this quarter.

Top Malware Types in Q3 2024
 Stealers dominated the threat landscape in Q3 2024
Stealers dominated the threat landscape in Q3 2024Let’s take a closer look at the most common malware types identified by ANY.RUN’s sandbox.
- Stealer: 16,511
- Loader: 8,197
- RAT: 7,191
- Ransomware: 5,967
- Miner: 3,880
- Keylogger: 3,172
- Backdoor: 811
- Installer: 640
- Trojan: 507
Compared to Q1 and Q2 of 2024, the ANY.RUN sandbox saw a significant increase in the detection of malware in Q3. A major reason for this is the growing number of public samples being uploaded by our 500,000-strong community of security analysts. Our team is also continuously improving the service’s capabilities, resulting in broader threat coverage.
Top malware types: highlights
In Q3, Stealers were the most common malware type detected, returning to the first spot since the start of the year after falling to the fourth place in Q2. They saw a serious rise in detections, reaching 16,511 in Q3.
Loaders maintained a strong presence, securing the second position for another quarter in a row. Their detections have seen a 49% rise from 5,492 to 8,197.
After leading in Q2, RATs dropped to the third spot, with 7,191 detections.
Trojan and Installer malware experienced a substantial decrease, shedding 3,704 and 2,466 detections correspondingly. Ransomware increased by 3,021, indicating a rise in this type of threat.
Top Malware Families in Q3 2024
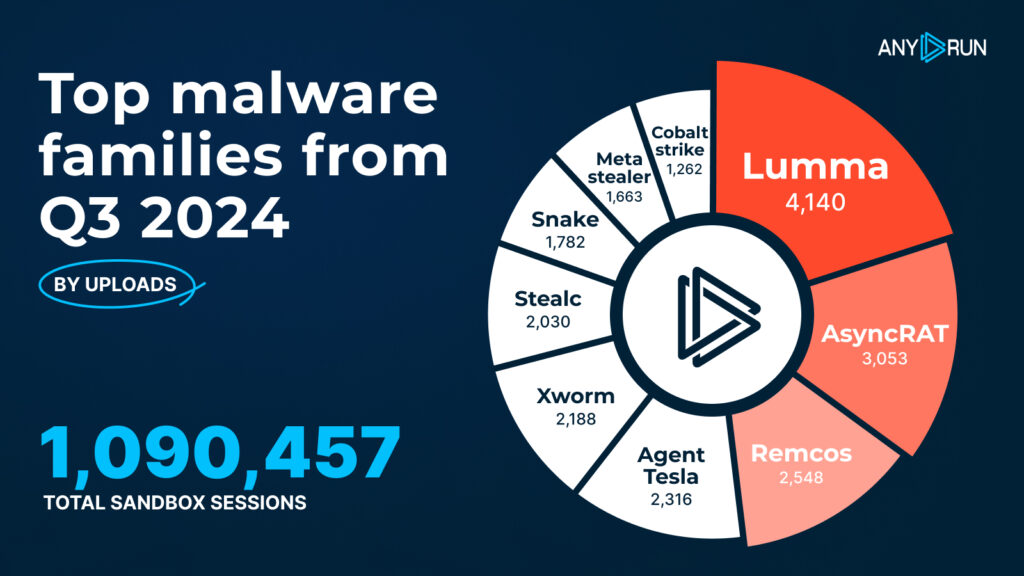 Lumma, AsyncRAT and Remcos became top threats in Q3 2024
Lumma, AsyncRAT and Remcos became top threats in Q3 2024- Lumma: 4,140
- AsyncRAT: 3,053
- Remcos: 2,548
- Agent Tesla: 2,316
- XWorm: 2,188
- Stealc: 2,030
- Snake: 1,782
- MetaStealer: 1,663
- Cobalt Strike: 1,262
Top malware families: highlights
In Q3 2024, the malware landscape saw notable shifts. Despite not being present on the Q2 ranking, Lumma emerged as the leading threat, recording 4,140 instances.
AsyncRAT went from 670 detections in Q2 to 3,053 in Q3, followed by Remcos whose detections almost doubled from 1,282 to 2,548.
Agent Tesla also showed an increase, jumping from 439 detections to 2,316, which is still more than its Q4 2023 result, when it topped the malware families chart.
Several new families made their debut in Q3, including XWorm with 2,188 detections and Stealc with 2,030.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup.
Top MITRE ATT&CK techniques in Q3 2024
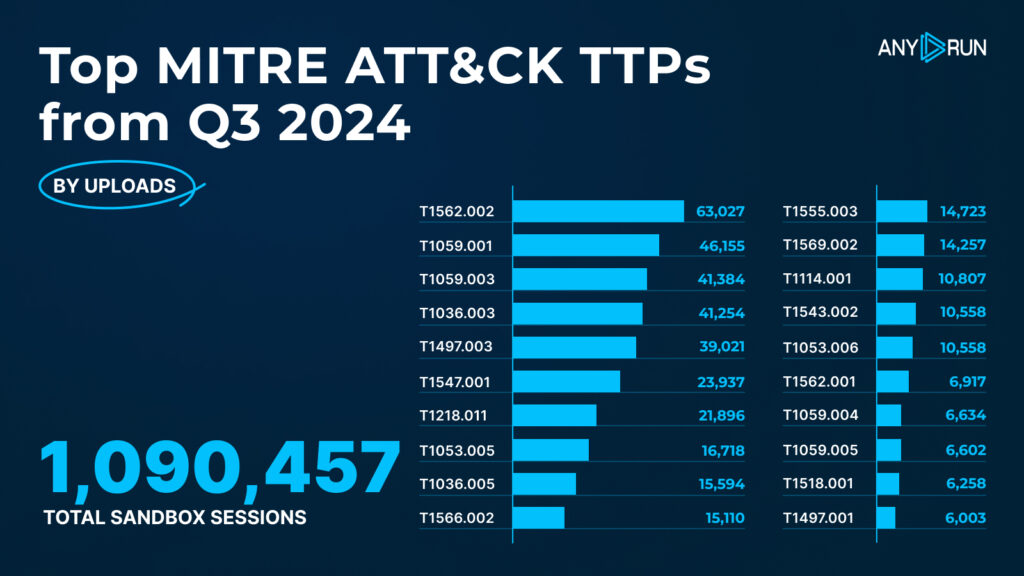 Disable Windows Event Logging became top TTP in Q3 2024
Disable Windows Event Logging became top TTP in Q3 2024The MITRE ATT&CK framework categorizes adversary behavior into tactics and techniques, helping malware analysts more efficiently identify, assess, and respond to threats.
Here are the top 20 techniques observed in Q3 2024:
<thead> <tr>
<th>
# </th>
<th>
MITRE ATT&CK Technique </th>
<th>
№ of detections </th>
</tr>
</thead><tbody> <tr>
<td>
1 </td>
<td>
Impair Defenses: Disable Windows Event Logging, T1562.002 </td>
<td>
63,027 </td>
</tr>
<tr>
<td>
2 </td>
<td>
Command and Scripting Interpreter: PowerShell, T1059.001 </td>
<td>
46,155 </td>
</tr>
<tr>
<td>
3 </td>
<td>
Command and Scripting Interpreter: Windows Command Shell, T1059.003 </td>
<td>
41,384 </td>
</tr>
<tr>
<td>
4 </td>
<td>
Masquerading: Rename System Utilities, T1036.003 </td>
<td>
41,254 </td>
</tr>
<tr>
<td>
5 </td>
<td>
Virtualization/Sandbox Evasion: Time Based Evasion, T1497.003 </td>
<td>
39,021 </td>
</tr>
<tr>
<td>
6 </td>
<td>
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder, T1547.001 </td>
<td>
23,937 </td>
</tr>
<tr>
<td>
7 </td>
<td>
System Binary Proxy Execution: Rundll32, T1218.011 </td>
<td>
21,896 </td>
</tr>
<tr>
<td>
8 </td>
<td>
Scheduled Task/Job: Scheduled Task, T1053.005 </td>
<td>
16,718 </td>
</tr>
<tr>
<td>
9 </td>
<td>
Masquerading: Match Legitimate Name or Location, T1036.005 </td>
<td>
15,594 </td>
</tr>
<tr>
<td>
10 </td>
<td>
Phishing: Spearphishing Link, T1566.002 </td>
<td>
15,110 </td>
</tr>
<tr>
<td>
11 </td>
<td>
Credentials from Password Stores: Credentials from Web Browsers, T1555.003 </td>
<td>
14,723 </td>
</tr>
<tr>
<td>
12 </td>
<td>
System Services: Service Execution, T1569.002 </td>
<td>
14,257 </td>
</tr>
<tr>
<td>
13 </td>
<td>
Email Collection: Local Email Collection, T1114.001 </td>
<td>
10,807 </td>
</tr>
<tr>
<td>
14 </td>
<td>
Create or Modify System Process: Systemd Service, T1543.002 </td>
<td>
10,558 </td>
</tr>
<tr>
<td>
15 </td>
<td>
Scheduled Task/Job: Systemd Timers, T1053.006 </td>
<td>
10,558 </td>
</tr>
<tr>
<td>
16 </td>
<td>
Impair Defenses: Disable or Modify Tools, T1562.001 </td>
<td>
6,917 </td>
</tr>
<tr>
<td>
17 </td>
<td>
Command and Scripting Interpreter: Unix Shell T1059.004 </td>
<td>
6,634 </td>
</tr>
<tr>
<td>
18 </td>
<td>
Command and Scripting Interpreter: Visual Basic T1059.005 </td>
<td>
6,602 </td>
</tr>
<tr>
<td>
19 </td>
<td>
Software Discovery: Security Software Discovery T1518.001 </td>
<td>
6,258 </td>
</tr>
<tr>
<td>
20 </td>
<td>
Virtualization/Sandbox Evasion: System Checks T1497.001 </td>
<td>
6,003 </td>
</tr>
</tbody></table>
Top TTPs: Q3 2024 vs Q2 2024
The first three spots were taken accordingly by:
- T1562.002, Impair Defenses: Disable Windows Event Logging — new entry.
- T1059.001: Command and Scripting Interpreter: PowerShell — up from the 7th spot in Q2.
- T1059.003, Command and Scripting Interpreter: Windows Command Shell — rose from the 6th spot, nearly doubling in detections.
The worthy mentions:
- T1114.001, Local Email Collection, was pushed down from the top spot in Q2 to the 13th position with 10,807 detections.
- T1036.003, Rename System Utilities, dropped from the 3d spot in the previous quarter to 4th, registering 41,254 instances.
- T1497.003, Time Based Evasion, despite falling to the 5th spot from 2nd in Q2, saw an increase in detections, bringing the figure to 39,021.
Report methodology
For our report, we looked at data from 1,090,457 interactive analysis sessions. This information comes from researchers in our community who contributed by running public analysis sessions in ANY.RUN.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Integrate ANY.RUN’s services in your organization →
The post Malware Trends Report: Q3, 2024 appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Malware Trends Report: Q3, 2024 - ANY.RUN's Cybersecurity Blog